- I ditched my daily driver Bose headphones for the XM6 - and I'm hesitant to go back
- This Lenovo ThinkPad is my top pick for remote work - and it's nearly 50% off now
- I invested in this 3-in-1 robot vacuum, and it's paying off for my home
- I've tested the Meta Ray-Bans for months, and these 5 features still amaze me
- My new favorite iPhone portable charger has a magnetic superpower - and it's cheap
61% of Hackers Use New Exploit Code Within 48 Hours of Attack

In 2024, cyber-criminals have launched attacks within 48 hours of discovering a vulnerability, with 61% of hackers using new exploit code in this short timeframe.
Companies faced an average of 68 days of critical cyber-attacks, while ransomware remained the most significant threat. The healthcare industry was particularly affected, with ransomware responsible for 95% of all breaches and impacting more than 198 million US patients.
These figures come from SonicWall’s Annual Cyber Threat Report, which also suggested that attackers are leveraging AI-driven automation and advanced evasion techniques, making it increasingly difficult for SMBs to defend themselves.
Key Cyber Threat Trends
These were some of the key cyber threat identified by SonicWall in 2024:
-
Ransomware Surge: North America saw an 8% rise, while Latin America experienced a 259% spike
-
IoT Attacks: Increased 124% year-over-year, with hackers targeting unprotected devices
-
Business Email Compromise (BEC): Accounted for 33% of reported cyber insurance events, up from 9% in 2023
-
Malware Variants: SonicWall identified 210,258 never-before-seen malware variants, averaging 637 new threats daily
-
Living Off the Land Binaries (LOLBins): Attackers increasingly use native system tools to evade detection
AI-enabled and File-based Attacks
According to the report, AI-driven tools are making cyber-attacks more accessible and complex. Server-side request forgery (SSRF) attacks rose by 452% as AI enhances obfuscation techniques and automates exploit chaining.
Business Email Compromise (BEC) attacks are also evolving, with generative AI enabling cybercriminals to craft highly convincing phishing emails.
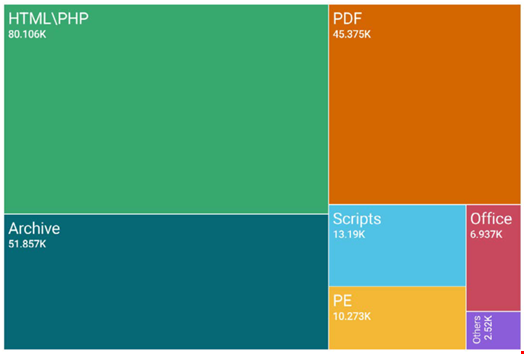
File-based attacks, particularly involving malicious PDFs and HTML phishing files, also experienced a significant increase.
According to SonicWall data, 38% of detected malicious files were HTML-based, while PDFs followed closely at 22%.
Strengthening Cyber Defenses
To counter these threats, businesses must adopt a multi-layered cybersecurity strategy.
Key recommendations from SonicWall include:
-
Real-Time Patch Management: Apply security patches within 48 hours of disclosure
-
Zero Trust Security Models: Restrict access and validate all network traffic
-
24/7 Threat Monitoring: Partner with MSSPs for continuous security oversight
-
Enhanced Ransomware Defenses: Implement network segmentation and endpoint detection & response (EDR)
-
IoT Security: Secure connected devices by changing default credentials and updating firmware
With cyber-criminals accelerating their tactics, SMBs must act promptly to strengthen their defenses and mitigate financial and reputational damage.

