- Yes, your internet provider can throttle your speed. Here's how to stop it (or at least try to)
- Half of Firms Suffer Two Supply Chain Incidents in Past Year
- Data strategy e qualità del dato: come gettare le basi per implementare l’AI
- INE Security Alert: $16.6 Billion in Cyber Losses Underscore Critical Need for Advanced Security Training
- From help desk to AI harmony: Redefining IT support in the age of intelligent automation
7 Cyber Attack Vectors & How to Protect Them

Risk Management
The quicker a cyberattack is identified, the less it costs. Jon Clay, VP of Threat Intelligence, reviews 7 key initial attack vendors and provides proactive security tips to help you reduce cyber risk across the attack surface.
Read time: ( words)
Digital transformation and remote work have rapidly expanded the attack surface. As the collection of applications, websites, accounts, devices, cloud infrastructure, servers, and operational technology (OT) continue to increase, attack surface management becomes more challenging as well. Unsurprisingly, 73% of IT and business leaders polled in a Trend Micro global study said they’re concerned with the size of their digital attack surface.
Effective attack surface risk management (ASRM) starts with proactive defense of initial attack vectors instead of reactive defense after the malicious actors have breached your network. According to IBM, attack vectors with longer mean times to identify and contain were among the most expensive types of breaches. In this blog, I review the seven key initial attack vectors to help CISOs and security leaders strengthen their ASRM security strategy and reduce cyber risk.
Seven initial attack vectors
Read ahead:
1. Email
The risks: Email remains the most common initial attack vector for cybercriminals due to the ease in nature. In 2021, 74.1% (33.6 million) of the total threats blocked by Trend Micro were email threats — a 101% increase from 2020. And the cost of these attacks is growing as well; according to Ponemon’s 2021 Cost of Phishing Study, phishing attacks cost enterprises nearly $15 million annually, or more than $1,500 per employee.
What enterprises can do: Go beyond native email security by choosing a vendor with layered defense:
1. Email gateway leveraging AI, ML, behavioral analysis, and authorship analysis
2. Cloud application security broker (CASB) analyzes emails in the inbox by scanning links/attachments and emails between peers to prevent compromised accounts from phishing other employees
3. Secure web gateway (SWG) provides additional protection if a malicious link is clicked by inspecting traffic inline, performing image analysis, and using ML to analyze branded elements, login forms, and other site content to recognize fake websites
4. Educate users using built-in security awareness simulations and training. Ideally, the vendor will offer phishing tests based on templates extracted from recent, real phishing scams
2. Web and web applications
The risks: Cross-site scripting (XSS) attacks take advantage of coding flaws on websites or web applications to generate input from users. It’s no wonder XSS remains a mainstay on the OWASP Top 10 Web Application Security Risks—a severe XSS vulnerability in Ivory Search, a WordPress search plugin, left 60,000 websites open to malicious code injection. With remote work and the shift to cloud services resulting in a boom of websites and applications, enterprises need to strengthen their defense for this initial attack vector.
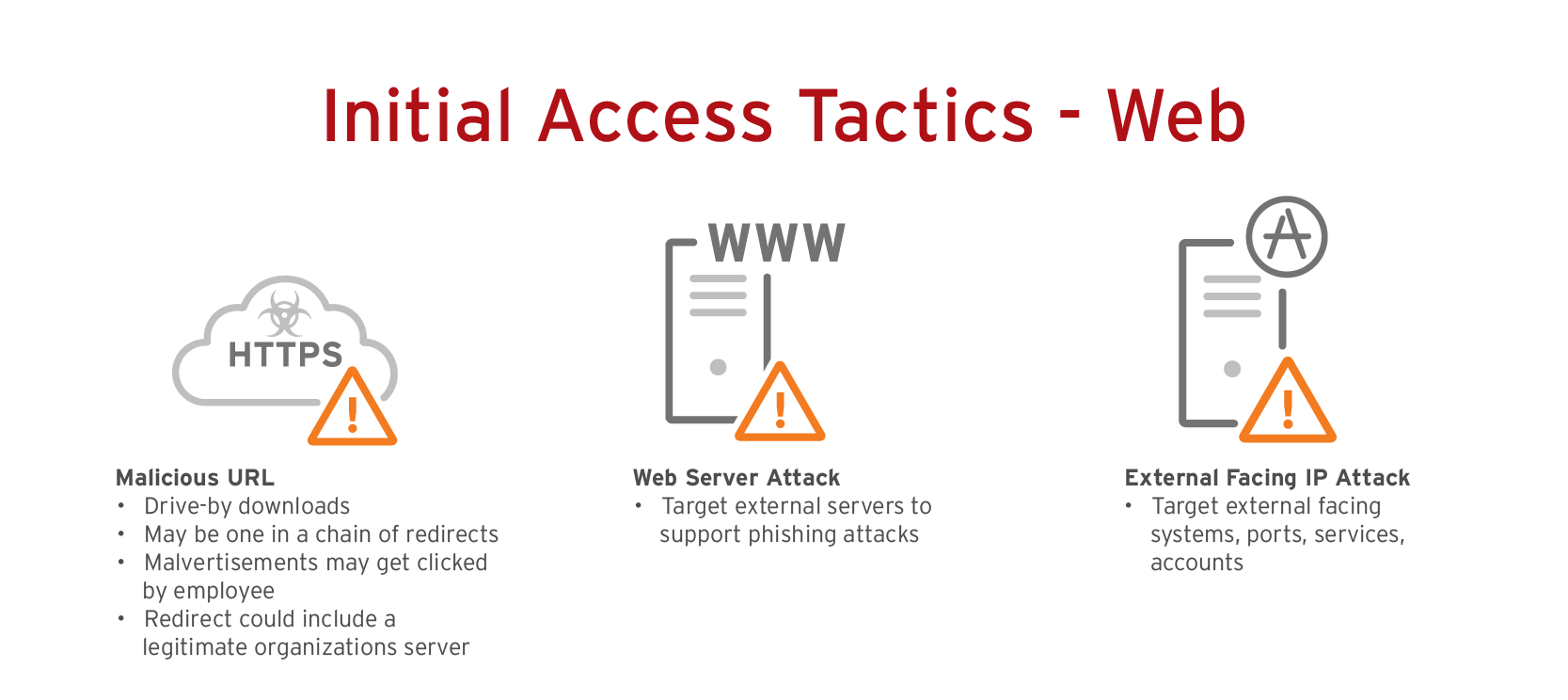
What enterprises can do: CASB can help reduce the risks of using SaaS apps without impacting the user experience. It counters shadow IT, secures cloud account compromise, and addresses security gaps for third-party services (like Ivory Search). Furthermore, CASB complements the threat-blocking capabilities of SWG solutions and benefits from integration with the analytical power of extended detection and response (XDR). The disparate logs of these once discrete solutions combine to offer a more holistic view of your environment, allowing for the creation of a more thorough risk profile.
3. Vulnerabilities

The risks: Vulnerabilities can disrupt business operations by causing system blackouts or closures. Take Swedish grocery chain Coop for example; it was forced to shut down 800 stores after malicious actors leveraged multiple zero-day vulnerabilities in Kaseya’s Virtual System/Server Administrator (VSA) product to launch a ransomware attack. Zero days, n-days, and forever days continue to increase. Trend Micro Research reported a 23% increase in the number of critical- and high-severity vulnerabilities during the first half of 2022 submitted to our Zero Day Initiative bug bounty program.
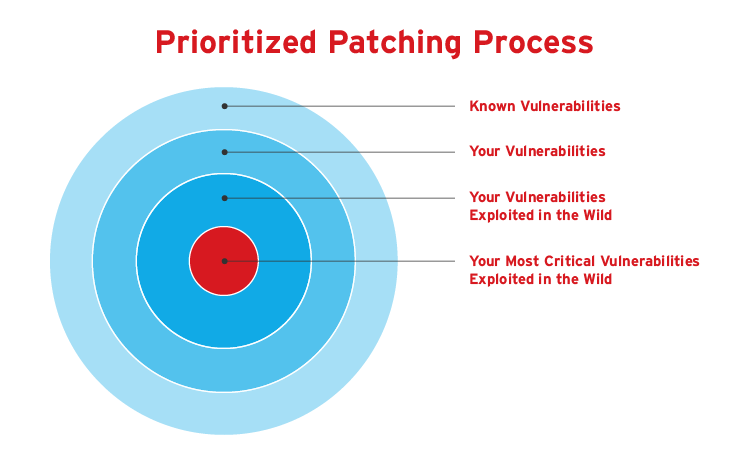
What enterprises can do: These five risk-based patch management best practices can help organizations create a strong defense program against vulnerability exploitation:
1. Identify which patches are most relevant using a prioritized patching process and checking the CISO Known Exploited Vulnerability catalog.
2. Make a zero-day plan for when, not if by consistently monitoring networks for suspicious activity and staying up to date with bug bounty programs that leverage global threat intelligence, such as the Trend Micro™ Zero Day Initiative™
3. Communicate with vendors about the possibility of rollbacks to previous versions of software
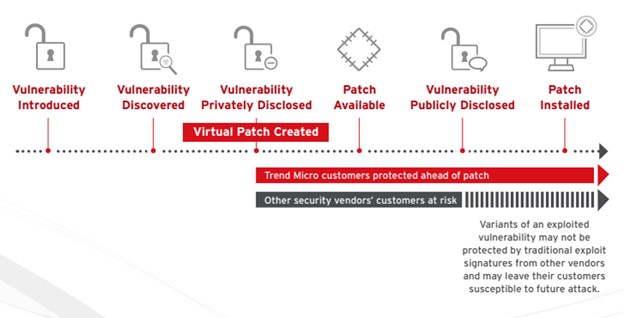
4. Utilize virtual patching to protect vulnerable systems while waiting for a vendor patch to be released
5. Share benefits with stakeholders to encourage a culture of security within the organization as well as demonstrate the ROI of cybersecurity to the board
4. Devices
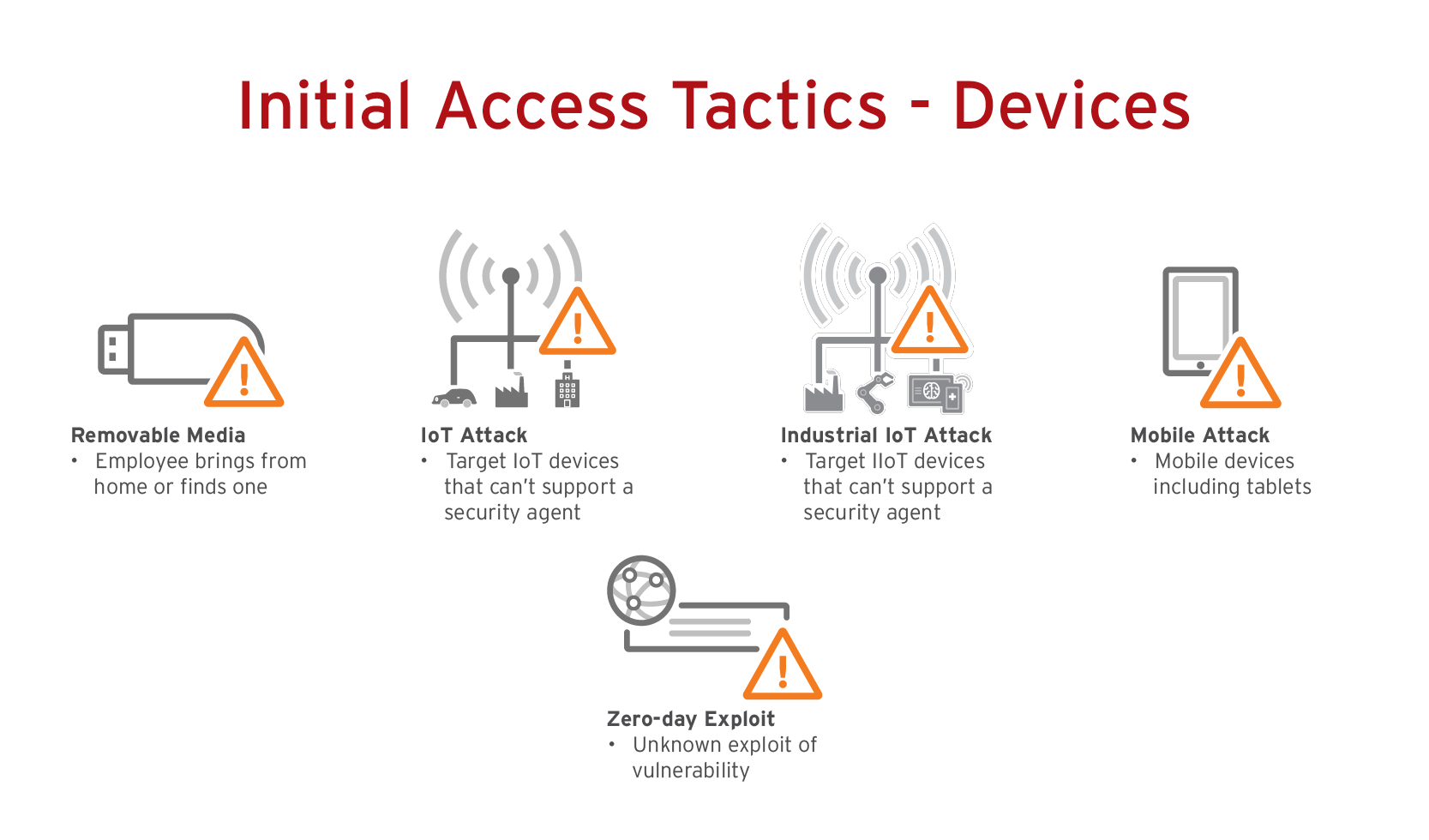
The risks: The shift to remote work exposed the dangers of VPNs — an initial attack vector which grants access to the entire network. While a remote worker may only access legitimate work apps, other devices in the household could spread malware through an unsecured machine connected to the VPN. And considering that 82% of data breaches involved a human element, the more devices with access to an organization’s entire network, the higher the cyber risk.
What enterprises can do: 63% of organizations are making the move from VPN to Zero Trust Network Access (ZTNA) to reduce cyber risk across the attack surface as part of a broader zero trust strategy. ZTNA continuously verifies the trust of users and devices, and only grants access to the web-portal frontend, which stops a compromised device from leapfrogging their attack across the attack surface. Furthermore, ZTNA provides the scalability needed to support evolving business operations. The specific application-to-user connection doesn’t require the bandwidth VPNs do, enabling high-performance availability and consistent delivery without negatively impacting the user experience.
5. Island hopping
The risks: Island hopping is used to pivot from an external environment into your network. Software supply chain attacks are increasing due to the success of Kaseya, Log4j, and SolarWinds. Think of this like a Russian nesting doll — within this initial attack vector lies many others: data distribution services (DDS), open source code, system management tools, and purchased applications. A Trend Micro global survey reported that 52% of organizations have a supply chain partner that has been hit by ransomware, meaning their systems were at risk as well.
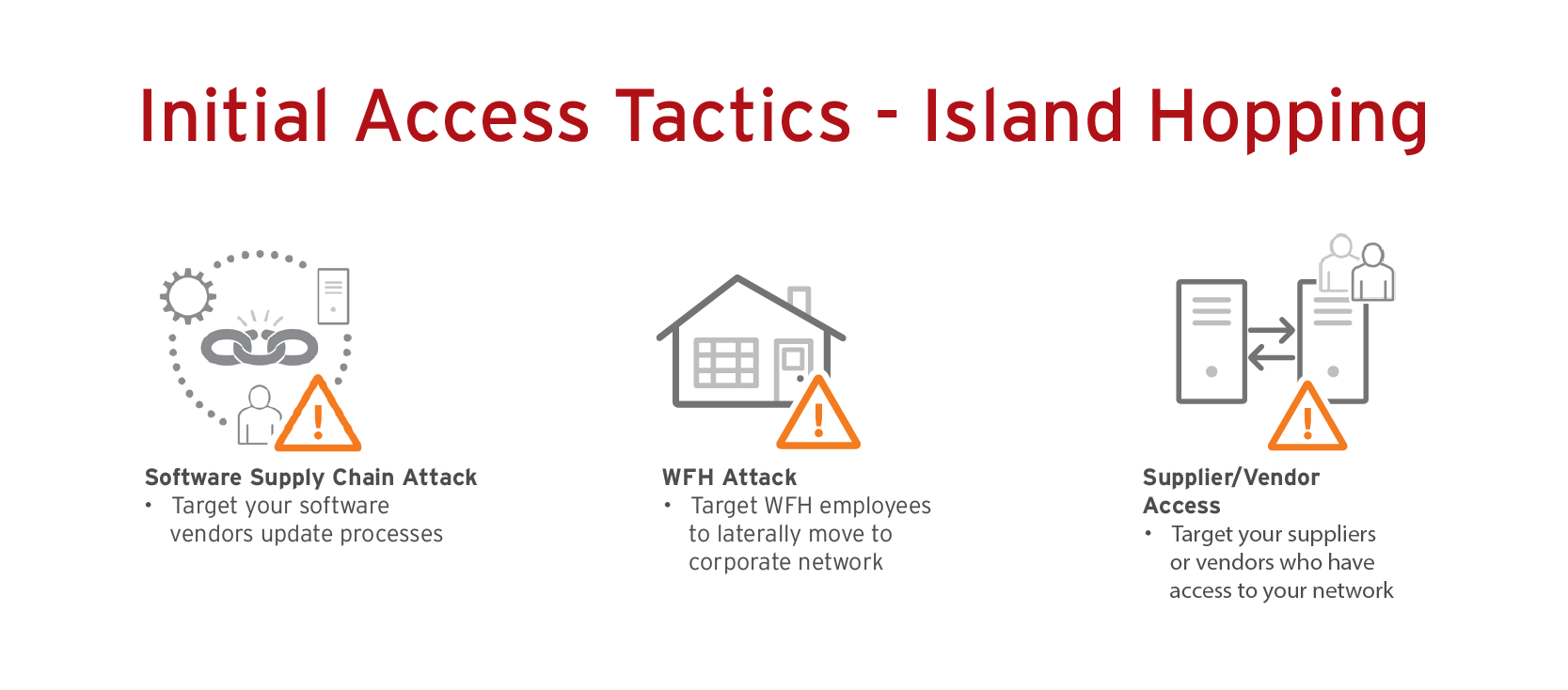
What enterprises can do: CISA published ICT SCRM Essentials which recommends six key steps to building effective software supply chain security:
1. Identify: Determine who needs to be involved
2. Manage: Develop your supply chain security policies and procedures based on industry standards and best practices, such as those published by NIST
3. Assess: Understand your hardware, software, and services that you procure
4. Know: Map your supply chain to better understand what component you procure
5. Verify: Determine how your organization will assess the security culture of suppliers
6. Evaluate: Establish timeframes and systems for checking supply chain practices against guidelines
6. Insider
The risks: A 2022 Ponemon global report found that the time to contain an insider threat increased from 77 to 85 days, causing organizations to spend the most on containment. Furthermore, incidents that took more than 90 days to contain cost an overage of $17.19 million on an annualized basis. Whether the insider is simply accidental, negligent, or malicious, the price to pay remains high.
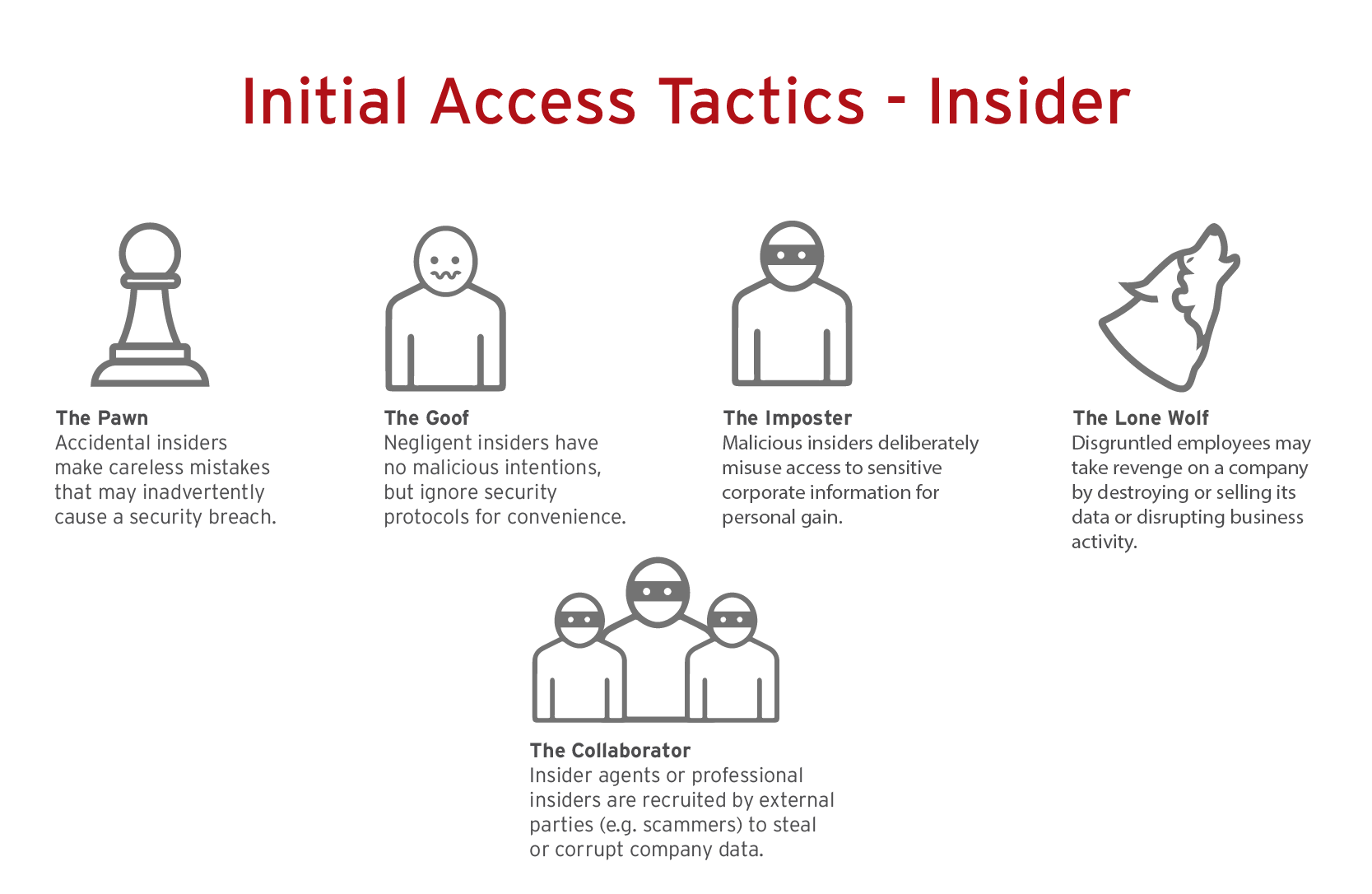
What enterprise can do: Improving cyber hygiene through security awareness training can help businesses avoid the accidental or negligent insiders. To address the other types of insiders, continuous monitoring of ingress and egress traffic is essential. And if this initial attack vector is exploited, having an incident response plan in place will help contain the threat quickly to limit the spread and financial impact.
7. Cloud
The risks: Digital transformation has accelerated cloud adoption, which presents new cybersecurity risk. The Trend Micro 2022 Midyear Cybersecurity Report identified three growing trends that post financial, operational, and reputation risks to enterprises: cryptocurrency mining, cloud tunnel exploits, and cloud software misconfigurations. The latter of which costs businesses an average of $4.14 million according to IBM.
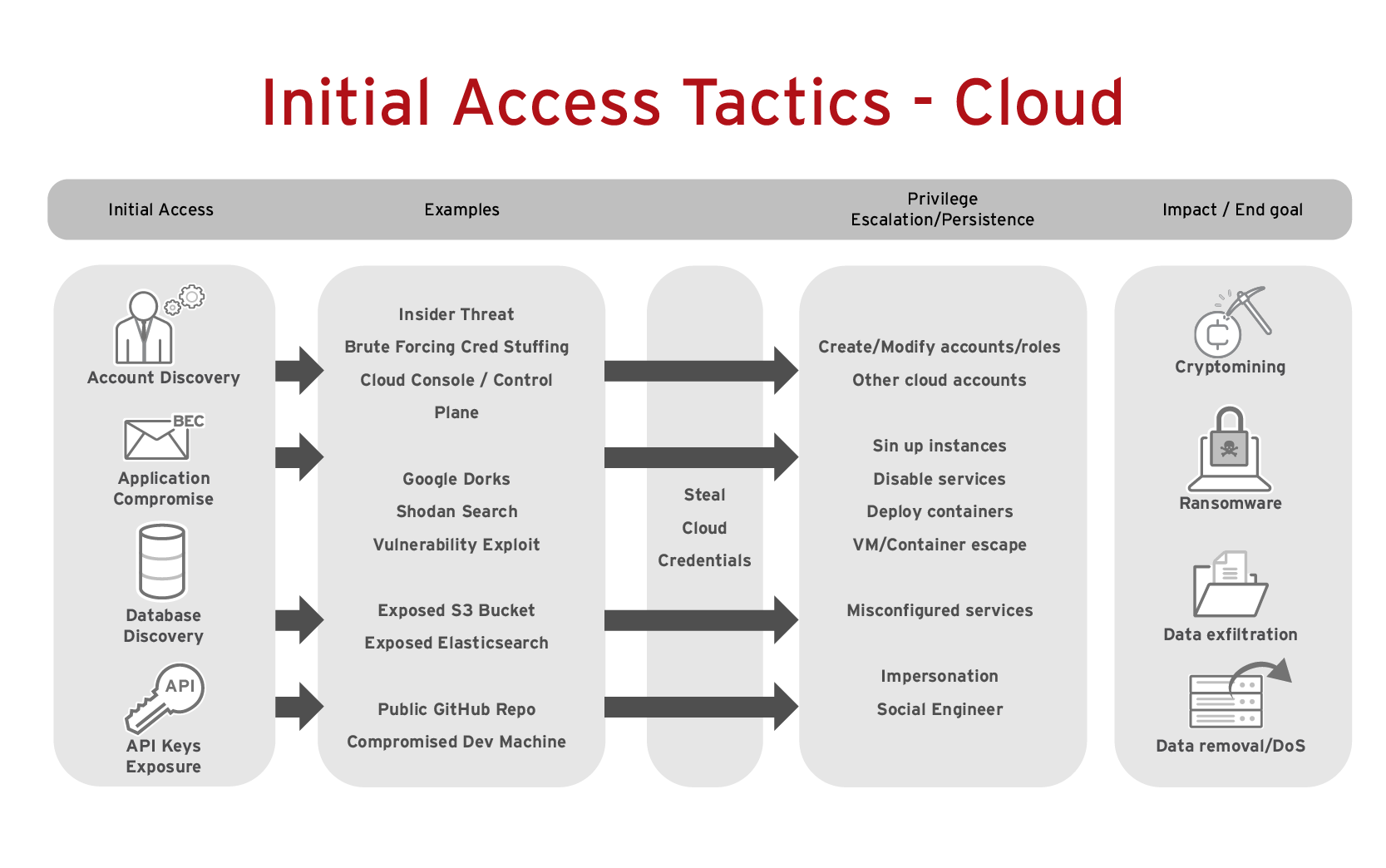
What enterprises can do: Leveraging a cloud-native security platform that supports multi- and hybrid-cloud environments is critical. Look for a platform that can automate as many things as possible, from scanning infrastructure as code (IaC), open source code, containers, and cloud workloads, to setting clear security policies and performing compliance checks.
A unified cybersecurity approach to protecting attack vectors
You might get to the end of this and be overwhelmed with the number of new security products you need. Truthfully, deploying and maintaining disparate security tools at each layer is simply unmanageable, especially with the skills gap and turnover. Consider a unified cybersecurity platform to reduce complexity and augment existing resources, while ensuring security maturity.
Using a unified platform across multiple environments that supports broad third-party integrations ensures comprehensive visibility from a single dashboard. Security capabilities such as automation, continuous monitoring, and XDR are critical to ASRM. Visibility and deep data correlation enable security teams to discover, assess, and mitigate threats across the attack surface risk lifecycle.
To learn more about ASRM, check out the following resources:
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

