- Prime members can save $10 on any $20 or more Grubhub+ order for a limited time - here's how
- Get a Galaxy S25 phone, Watch, and Tab free from Verizon - here's how
- Best early Prime Day laptop deals: My 12 favorite sales live now
- From Innovation to Action: Seizing the $43B Networking Refresh Opportunity with Cisco
- Best early Prime Day phone deals: My 17 favorite sales live now
How to use Docker Bench for Security to audit your container deployments

Docker Bench for Security is a simple way of checking for common best practices around your Docker deployments in production. Jack Wallen shows you how to use this tool.
Image: Docker
One of the biggest issues surrounding container deployments is security. This is such an issue because there are so many moving parts to be checked. You might have your container manifests perfectly secure, but what about your host? Or maybe your host is sound, but your YAML files are riddled with security holes.
What do you do? Spend hours (or days) combing through everything to ensure those deployments are secure? You could do that. Or you could make use of the tools available to you. One such tool is a pre-built container, called Docker Bench for Security–it does a great job of auditing your container host and the currently running deployments. Unlike many such tools, Docker Bench for Security is incredibly easy to use.
Docker Bench for Security audits the following:
-
General configuration
-
Linux HostAs Specific configuration
-
Docker daemon configuration
-
Docker daemon configuration files
-
Container images and Build File
-
Container Runtime
-
Docker Security Operations
-
Docker Swarm Configuration
-
Docker Enterprise Configuration
-
Docker Trusted Registry Configuration
Let me show you how this is done.
SEE: Kubernetes security guide (free PDF) (TechRepublic)
What you’ll need
The only things you’ll need to make this work are a running instance of Docker on your server and a user associated with the docker group who can run Docker commands.
I’ll be demonstrating on Ubuntu Server 20.04, but the tool will work on any platform that supports Docker.
How to get Docker Bench
The first thing we need to do is clone the tool from GitHub. If you don’t already have git installed, do so with a command like:
sudo apt-get install git -y
Clone Docker Bench with the command:
git clone https://github.com/docker/docker-bench-security.git
Change into the newly-created directory with the command:
cd docker-bench-security
How to configure the Docker daemon
Before we run the audit, we need to create a Docker daemon configuration file. Create the file with the command:
sudo nano /etc/docker/daemon.json
In that file, paste the following:
{
"icc": false,
"userns-remap": "default",
"live-restore": true,
"userland-proxy": false,
"no-new-privileges": true
}
Save and close the file.
How to install and configure auditd
We now need to install auditd with the command:
sudo apt-get install auditd -y
When the installation completes, open the auditd rules file with the command:
sudo nano /etc/audit/audit.rules
At the bottom of the file, paste the following:
-w /usr/bin/docker -p wa -w /var/lib/docker -p wa -w /etc/docker -p wa -w /lib/systemd/system/docker.service -p wa -w /lib/systemd/system/docker.socket -p wa -w /etc/default/docker -p wa -w /etc/docker/daemon.json -p wa -w /usr/bin/docker-containerd -p wa -w /usr/bin/docker-runc -p wa
Save and close the file.
Restart auditd with the command:
sudo systemctl restart auditd
Finally, restart the Docker daemon with the command:
sudo systemctl restart docker
How to run the audit
While in the docker-bench-security directory, launch the audit with the command:
./docker-bench-security.sh
The above command will run the audit and start listing out details with either:
When the audit completes, you must comb through the output and address everything listed as a Warning–at minimum (Figure A). There might even be some Info or Note messages that you’ll need to take care of.
Figure A
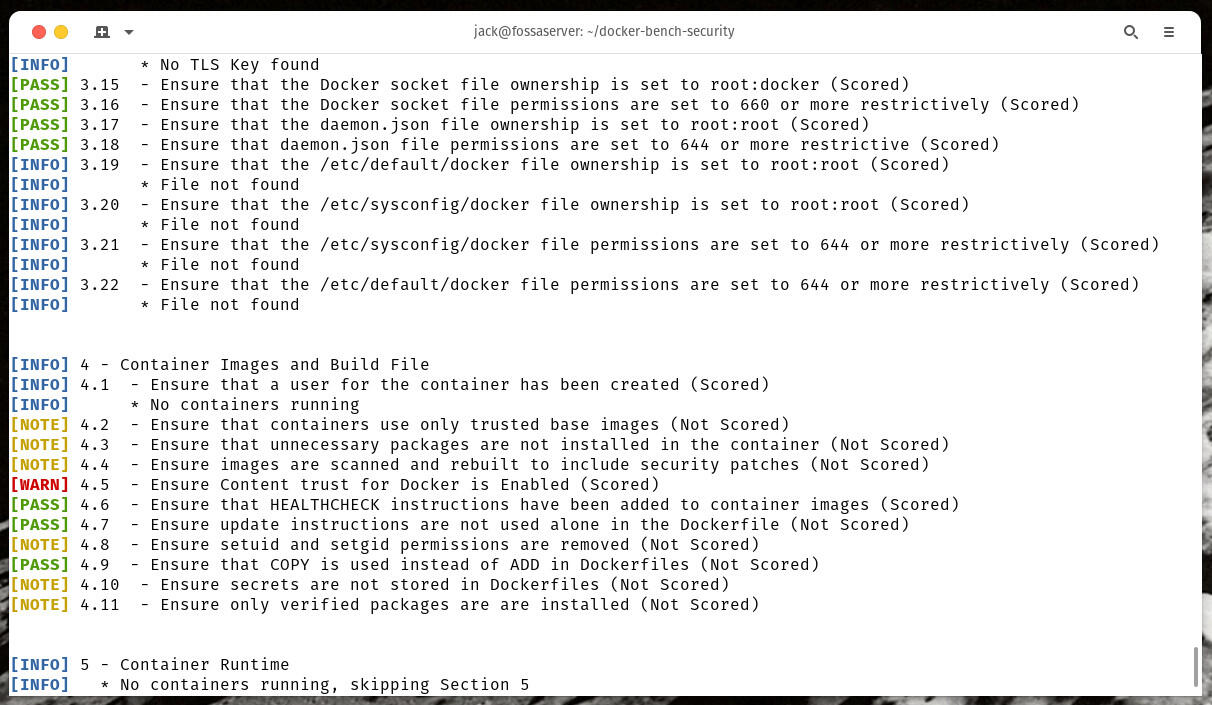
The output of Docker Bench makes it very clear what you need to fix.
The output you receive will depend on the configuration of your host and the containers you’ve deployed. However, it should be your goal to fix every Warning, at a minimum. After you address these issues, make sure to re-run the audit. Do this until you no longer see any Warning labels listed.
And that’s all there is to using Docker Bench for Security to audit your host and containers.
Subscribe to TechRepublic’s How To Make Tech Work on YouTube for all the latest tech advice for business pros from Jack Wallen.


