- Network problems delay flights at two oneworld Alliance airlines
- Leveraging Avaya Experience Platform to accelerate your digital banking transformation
- The best iRobot vacuums of 2024: Expert tested and reviewed
- This simple Gmail trick gave me another 15GB of storage for free - and I didn't lose any files
- Why Oura Ring 4 is ZDNET's product of the year - besting Samsung, Apple, and others in 2024
Microsoft’s April 2021 Patch Tuesday Addresses 108 CVEs (CVE-2021-28310)

Microsoft addresses 108 CVEs, including CVE-2021-28310 — which has reportedly been exploited in the wild — as well as four new remote code execution vulnerabilities in Microsoft Exchange.
- 19Critical
- 88Important
- 1Moderate
- 0Low
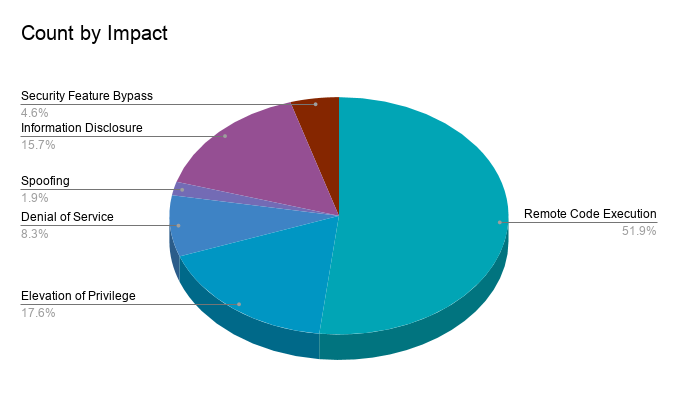
Microsoft patched 108 CVEs in the April 2021 Patch Tuesday release, including 19 CVEs rated as critical, 88 rated as important and 1 rated as moderate.
This month’s Patch Tuesday release includes fixes for
- Azure AD Web Sign-in
- Azure DevOps
- Azure Sphere
- Microsoft Edge (Chromium-based)
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Internet Messaging API
- Microsoft NTFS
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Windows Codecs Library
- Microsoft Windows Speech
- Open Source Software
- DNS Server
- Hyper-V
- Visual Studio
- Visual Studio Code
- Visual Studio Code – GitHub Pull Requests and Issues Extension
- Visual Studio Code – Kubernetes Tools
- Visual Studio Code – Maven for Java Extension
- Windows Application Compatibility Cache
- Windows AppX Deployment Extensions
- Windows Console Driver
- Windows Diagnostic Hub
- Windows Early Launch Antimalware Driver
- Windows ELAM
- Windows Event Tracing
- Windows Installer
- Windows Kernel
- Windows Media Player
- Windows Network File System
- Windows Overlay Filter
- Windows Portmapping
- Windows Registry
- Windows Remote Procedure Call Runtime
- Windows Resource Manager
- Windows Secure Kernel Mode
- Windows Services and Controller App
- Windows SMB Server
- Windows TCP/IP
- Windows Win32K
- Windows WLAN Auto Config Service.
Remote code execution (RCE) vulnerabilities accounted for nearly 52% of the vulnerabilities patched this month, followed by Elevation of Privilege (EoP) at 17.6%.
CVE-2021-28480, CVE-2021-28481, CVE-2021-28482 and CVE-2021-28483 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2021-28480, CVE-2021-28481, CVE-2021-28482 and CVE-2021-28483 are four RCE vulnerabilities in Microsoft Exchange Server. Discovery of these four flaws is credited to the National Security Agency (NSA). Two of the four flaws, CVE-2021-28480 and CVE-2021-28481, are pre-authentication vulnerabilities, which means they can be exploited by remote, unauthenticated attackers without the need for any user interaction.
While no public proof-of-concept (PoC) or in the wild exploitation of these vulnerabilities has been reported, these patches follow the disclosure of four zero-day vulnerabilities in Exchange that were widely exploited following their release in an out-of-band (OOB) update in March, just a week prior to the March 2021 Patch Tuesday release. Microsoft Exchange is undoubtedly a popular target for attackers and security researchers alike with several teams demonstrating successful exploit attempts against Exchange at the Zero Day Initiative’s annual Pwn2Own competition. Considering the widespread exploitation of the last batch of Exchange Server vulnerabilities and the severity of these newly disclosed flaws, administrators should place these at the top of their patching priority list.
CVE-2021-28310 | Win32k Elevation of Privilege Vulnerability
CVE-2021-28310 is an EoP vulnerability in the Desktop Window Manager or dwm.exe. The vulnerability has been exploited in the wild as a zero-day according to researchers at Kaspersky, who shared details about the flaw in a blog post. Kaspersky says this EoP vulnerability has likely been exploited by “several threat actors” and chained together with other browser-based exploits in order to escape sandboxes.
It remains unclear whether this particular zero-day was used in conjunction with a separate browser-based zero-day or unpatched browser-based vulnerabilities. It wouldn’t surprise us to see threat actors leveraging this vulnerability with a browser-based zero-day, as a majority of zero-day vulnerabilities disclosed last year were in browsers, according to findings from our 2020 Threat Landscape Retrospective report.
CVE-2021-28329, CVE-2021-28330, CVE-2021-28331, CVE-2021-28332, CVE-2021-28333, CVE-2021-28334, CVE-2021-28335, CVE-2021-28336, CVE-2021-28337, CVE-2021-28338, CVE-2021-28339 and CVE-2021-28343 | Remote Procedure Call Runtime Remote Code Execution Vulnerability
CVE-2021-28329, CVE-2021-28330, CVE-2021-28331, CVE-2021-28332, CVE-2021-28333, CVE-2021-28334, CVE-2021-28335, CVE-2021-28336, CVE-2021-28337, CVE-2021-28338, CVE-2021-28339 and CVE-2021-28343 are twelve RCE vulnerabilities in the remote procedure call (RPC) runtime in Microsoft Windows. These critically rated CVEs were reported to Microsoft by Yuki Chen, head of the 360 Vulnerability Research Group and 360 Vulcan Team. Chen is responsible for reporting all of the 27 RPC vulnerabilities in Microsoft’s April 2021 Patch Tuesday (table below) and was also responsible for the disclosure of 9 RPC vulnerabilities addressed in Microsoft’s January 2021 Patch Tuesday. All 27 vulnerabilities were assigned a CVSSv3 score of 8.8 and highlighted by Microsoft as “Exploitation Less Likely.” Exploitation of these vulnerabilities would require network access and a low privileged account based on Microsoft’s assigned CVSSv3 scores.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains April 2021.
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from March 2019 using Tenable.io:
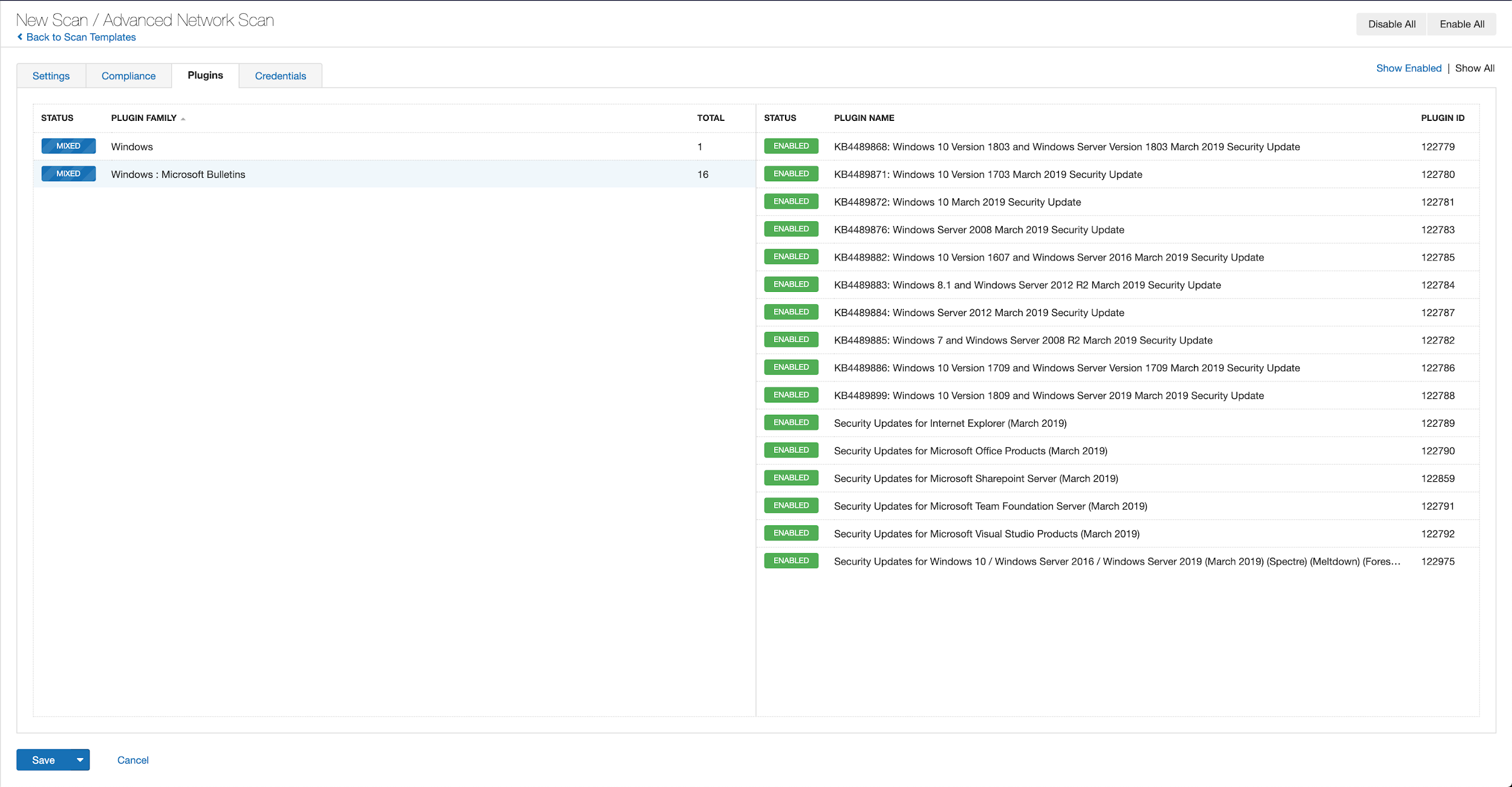
A list of all the plugins released for Tenable’s April 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.

