- T-Mobile launches high-speed home internet service - see if you can get it
- Sponsor or Exhibit at a 2025 PCI SSC Event
- My favorite 3-in-1 travel MagSafe charger is smaller than a cookie (and it's $20 off)
- Workday unveils new AI tools and agents for developers - here's how to access
- Enterprises face data center power design challenges
Wells Fargo and Chase now among most imitated brands in phishing attacks
The banks are being exploited in attacks targeting people filing taxes, getting stimulus checks and ordering home deliveries, says Check Point.
Image: Getty Images/iStockphoto
Phishing campaigns typically try to arouse interest among potential victims through two strategies. They’ll impersonate popular brands and products potentially used by the recipients. And they’ll reference events and items that are timely. If a campaign can do both, so much the better, at least for the criminals.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
For the first time, Wells Fargo and Chase joined Check Point’s list of the top 10 most exploited brands in phishing attacks, according to a Thursday report. Wells Fargo made the No. 6 spot, used in 4% of all phishing attacks analyzed in the first quarter of 2021. Fellow bank Chase was right behind in seventh place, accounting for 2% of all phishing campaigns last quarter.
Check Point attributed the appearance of the banks on its list to a few factors. With the tax deadline now set for May 17, taxpayers are naturally relying more on online banking. The COVID-19 stimulus checks are being sent to households, prompting recipients to deposit or cash in those funds. And with the ongoing coronavirus lockdown, people continue to purchase groceries and other items online for which they pay by credit card or mobile app.
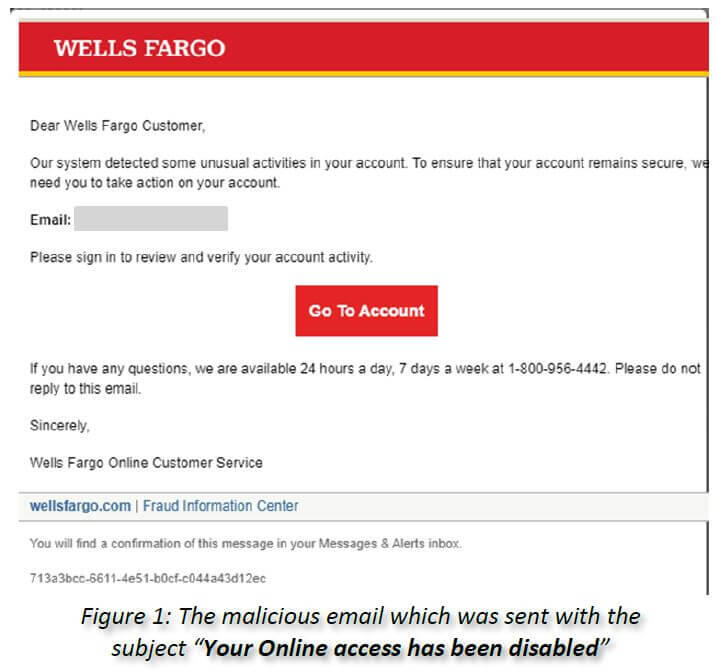
In one example, a phishing attack was caught spoofing Wells Fargo in an attempt to steal the banking account details of recipients. Using a spoofed sender address of noreply@cc.wellsfargo.com, the message included a subject line of “Your Online access has been disabled.” Clicking on the link in the message redirects the user to a malicious webpage that resembles the actual Wells Fargo site. That page then prompts the person to enter the username and password for their bank account.
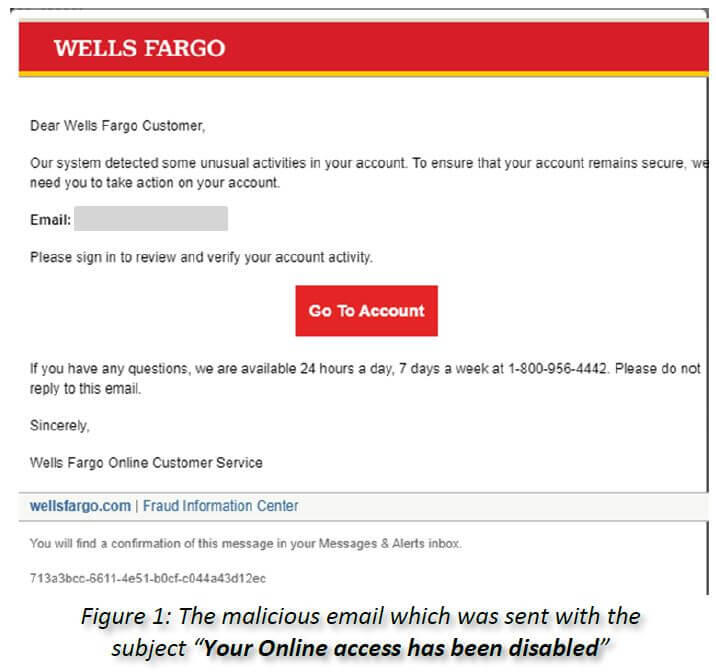
Image: Check Point Research
Among other spoofed brands, Microsoft remained at the top of Check Point’s list for the first quarter, used in 39% of all phishing campaigns. Other companies rounding out the top ten included DHL, Google, Roblox, Amazon, LinkedIn, Apple and Dropbox.
To help organizations and individuals avoid phishing attacks, Check Point serves up the following tips:
- Check for misspellings. Legitimate messages typically don’t have spelling errors or poor grammar. Read each email carefully and report any suspicious messages to your organization’s support staff or to an email provider like Microsoft.
- Don’t open file attachments. Don’t open file attachments from unknown sources or from unexpected messages. Phishing attacks often include attachments with viruses or other malware.
- Review the contact details. Legitimate businesses always provide contact information. A lack of direction on how to contact the sender strongly indicates a phishing message.
- Beware of urgent or threatening language in the subject line. Watch out for subject lines that claim your “account has been suspended” or that ask you to respond to an “urgent payment request.” Conveying a sense of urgency or fear is a popular ploy in phishing emails.
- Share the least amount of information. Don’t give up personal or company information that’s consider confidential or sensitive. Most companies will never ask for personal credentials by email, and that’s especially true for banks.


