- NordPass lets you store passports and other IDs now - but is this safe?
- 8 AI features coming to iOS 26 that actually excite me (and how to try them now)
- Preorder the Hisense M2 Pro projector and get a free Anker battery - here's how
- Docker State of App Dev: Security | Docker
- Leadership Through Giving: How the Americas Partner Organization is giving Back
Malware Evasion Techniques

By Stas Gaivoronskii, Malware Analyst at ANY.RUN
Cybercriminals create new ways to make malware invisible for detection. They hide malicious indicators and behavior during analysis. Researchers need to know about different approaches to improve security. I have investigated evasion techniques that ANY.RUN service faces every day, and I would like to share my insights.
Malware evasion
Defense evasion is the way to bypass detection, cover what malware is doing, and determine its activity to a specific family or authors. There are different techniques used by threat actors like injection, data encryption, and obfuscating. The tactics often induce payloads and scripts.
Сyber specialists and detection dodging
Let’s imagine a researcher who deals with Ursnif malware. He knows that usually, this program injects itself into Internet Explorer processes. But some versions of Ursnif use time-based evasion and delay execution for quite a long time. Our investigator is impatient and doesn’t give the analyzed sample enough time to start its activity. But some versions of Ursnif acquire user execution. The researcher hasn’t checked this part and misses the attack. As a result, the threat remains undefined and it’s unclear what steps the security team will take to get rid of the infection.
If the specialist had taken extra time to check all possible variants of attacks, he could have found malicious files and URLs and got more IOCs. Being an expert means to block any malicious activity and improve security. Cybersecurity experts should get relevant information, adopt advanced evasion techniques and know its new features to prevent attacks. Most importantly, understand the ways malware uses to defeat it.
Malicious programs evade detection by a wide range of tactics. Moreover, attackers use them in different combinations, not just solo. Let’s explore the most typical ways of detection dodging.
Common defense evasion techniques
- BITS Jobs
System administrators who work with Windows OSs, use utilities to perform tasks. One of these utilities is the Background Intelligent Transfer Service (BITS). It transfers files between users and HTTP while running in the background.
Attackers take advantage of this feature to load malware, execute it or clean up: Cobalt strike downloads its agent to the infected machine with the help of BITS Jobs. Don’t forget to check the activity of this feature in the Events log and BITSAdmin to detect the BITS Jobs technique.
- Deobfuscate files or information
A malicious program can hide artifacts by decoding files or data. Agent Tesla decrypts strings enciphered with the Rijndael symmetric encryption algorithm. Analyze the scripts and monitor certutil, so you won’t miss deobfuscation.
- Hide Artifacts
Artifacts reveal malicious activity such as files, directories, file attributes, users, etc. Malware tries to hide or isolate them to bypass detection. The best way to find them is by monitoring for any actions that will point to the artifacts. Check files and process arguments or shell commands.
- Modify Registry
Change of registry allows the malicious software to conceal data about configuration. For example, Nanocore modifies registry keys to conceal payloads used to maintain persistence. If you turn on registry auditing, you may notice malware actions.
- Process Injection
Code injection is the way to avoid detection. Attackers get access to the target’s systems by injecting into the system’s processes using different techniques. Pay attention to DLL activity, it may load not as usual. If you suspect this tactic, the attentive analysis of process behavior will show you questionable network connection or file reading.
- Signed Binary Proxy Execution
Malware takes advantage of Microsoft signed binaries. It uses proxy execution of files and bypasses security based on signatures. Keep an eye on processes and command-line to reveal this technique.
- Trusted Developer Utilities Proxy Execution
Developers use various programs to help in their daily work routine. However, certificates of these utilities let them run in any system, including proxy execution of malware. Any unfamiliar arguments or activity can be a sign of potential malicious work.
- Virtualization/Sandbox Evasion
Sandboxes are a real challenge for a malicious program. But it knows how to avoid a standard sandbox and recognize the virtual environment from a real one. First, malware checks what software set is there, then focuses on user activity. Some malicious programs have delayed time of execution to help them to avoid detection inside virtual machines.
- Evasion and interactivity
These techniques are basic. However, attacks tend to evolve. And so does defense strategies and tools. The virtualization evasion tactic is complicated and requires extra tools for detection. Unfortunately, automated services provide kinds of analysis that often are not enough as they are lacking user interaction.
Here are some of the advanced evasion techniques that demand interaction from the user side:
- Malware exploits user activity based on checks. It can remain invisible. The program waits for a victim to drag a mouse or clicks, keyboard input, or launching of a specific program. If you want to see it in action, check this task.
- Banking Trojan can wait for an internet browser to launch and redirect to a bank’s website. After that program wakes up and applies one of the credential APIs hooking sub-techniques for user input capture.
- In some cases, Microsoft Office files include macros that focus on user activity. For example, when a file opens, a message appears. And further macros work starts after a user clicks on a button of that window or closes it. Have a look at the following example.
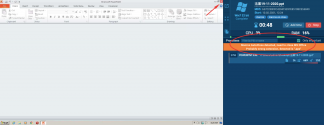
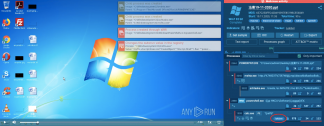
- Office files may contain macros on close that execute only after a user shuts down the active window or Excel sheet. You can investigate the sample that demonstrates the case.
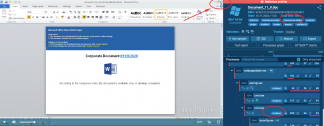
- Some malicious documents are encrypted. They require a user to insert the password mentioned in malspam to open them. That way, maldocs avoid both detonations in basic sandbox solutions and scanning of its contents because of the encryption. Automatic utilities can’t keep up with these features.
- Several samples add themselves into autorun and quit execution. They wait for system reboot where they have been executed. The task with the system restart is a great illustration. However, it can be a challenge for sandboxes that lack interactive access.

- Microsoft Office files also may require interactive scenarios. After a file is opened, it adds itself to the Microsoft Office’s startup folder. So, to execute the malware a user needs to open the Office file one more time. You can try it yourself in the following example.
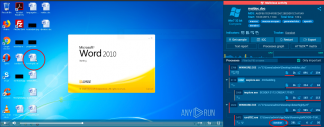
Thankfully, there is a way to detect these sly types of malware. The interactive approach of ANY.RUN service allows performing actions as a user does. And unlike automatic services, it allows overstepping evasion techniques. The most precious point, it saves time for analysis. You get the first results within seconds.
Malware will continue to evolve. The more defense approaches appear against them, the more complicated evasion techniques crooks will design. Cyber specialists must update their knowledge of modern and advanced ways to defeat malware. The same applies to detection tools that can save time and produce results.
About the Author
 Stas Gaivoronskii is a malware analyst at ANY.RUN, the first interactive online malware analysis sandbox. He has more than 9 years of experience in the digital forensics field and 2 years in malware analysis.
Stas Gaivoronskii is a malware analyst at ANY.RUN, the first interactive online malware analysis sandbox. He has more than 9 years of experience in the digital forensics field and 2 years in malware analysis.
Stas can be reached out online at s.gaivoronsky@any.run and at our company website https://any.run

