- The 11th Gen Apple iPad just reached its lowest price yet
- What is 'Technical Debt'? How the U.S. Congress Can Tackle This Silent IT Challenge
- Microsoft sees AI agents shaking up org charts, eliminating traditional functions
- Run out of Gmail storage? How I got another 15GB for free and without losing any files
- Your Google TV is getting a free feature upgrade - smart home users will love it
Uyghur Diaspora Group Targeted with Remote Surveillance Malware

Several representatives of exiled Uyghurs have been targeted by a pervasive spear phishing campaign aimed at deploying surveillance malware, researchers at the Citizen Lab have found.
In March 2025, senior World Uyghur Congress (WUC) members received Google notifications warning that their accounts had been the subject of government-backed attacks.
The WUC is an international organization headquartered in Munich. Its mission is to represent the collective interests of the Uyghur people both inside and outside of Xinjiang, the Uyghur autonomous region in China.
Forensic analysis by The Citizen Lab revealed the spear phishing campaign was distributed through a trojanized version of a legitimate open-source word processing and spell-check tool designed for the Uyghur language. Ultimately the campaign would deliver Windows-based malware that enabled remote surveillance.
While the malware itself was not particularly sophisticated, the attackers demonstrated a high level of understanding of the targeted community and invested significant effort into making the malicious delivery appear legitimate.
Notably, the malware was initially developed by a trusted member of the community known to members of WUC, making the malware delivery highly customized and targeted.
The technical artifacts also indicated that the attackers began preparing the campaign as early as May 2024, suggesting a well-planned and executed operation.
The Citizen Lab researchers assessed that the attackers align with the Chinese government.
Kill Chain: Spear Phishing Emails and Malicious Backdoor
The malicious email messages sent to senior members of the WUC impersonated a trusted contact at a partner organization and contained Google Drive links that, if clicked, would download a password protected .rar archive file.
The archive contained a trojanized version of a legitimate open-source Uyghur language text editor called UyghurEditPP.
Once executed, the trojanized UyghurEditPP application contains a backdoor that profiles the system, sends information to a remote command-and-control (C2) server and has the potential to load additional malicious plugins.
Specifically, the backdoor collects the following information from a target’s device:
- Machine name
- Username
- IP address
- Operating system version
- The MD5 hash of the machine name, username and hard disk serial number
In response to this information, the malware’s operator can send a reply from the server, likely after verifying that the infected system legitimately belongs to a target of interest. To conduct several tasks, such as:
- Download files from the target device
- Upload additional files to the target device
- Run commands against plugins uploaded to the target device
Infrastructure: Two Command-and-Control Clusters
The campaign’s C2 infrastructure was divided into two distinct clusters.
The first cluster consisted of adversary-registered domains (gheyret[.]com, gheyret[.]net, and uheyret[.]com) that impersonated the developer of the UyghurEditPP tool. It was likely used from June to February 2024.
The second cluster, used to target the WUC, comprised subdomains registered through Dynu Services, a dynamic DNS service provider based in Arizona, with Uyghur words in the domain names but without referencing the tool or developer directly. It was likely used between December 2024 and March 2025.
Despite the differing domain names, both clusters shared the same Microsoft certificate and IPs belonging to AS20473, managed by Choopa LLC, a hosting provider frequently used by cyber threat actors.
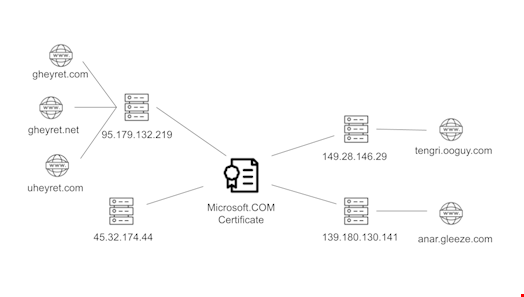
The existence of these two clusters raises questions about whether the shift represented a change in approach or two separate campaigns targeting different groups within the Uyghur community.
Attribution: Evidence Points to Chinese State Affiliation
The malicious campaign targeting the WUC members “was not notable for its technical sophistication and did not involve zero-day exploits or mercenary spyware,” The Citizen Lab researchers said.
However, the malware delivery showed “a high level of social engineering, revealing the attackers’ deep understanding of the target community,” they added.
The report also notes that although the researchers could not identify who was behind the attacks, the threat actors’ techniques and targeting suggest they align with the Chinese government.
Members of the WUC have been targeted by cyber-attacks in the past decade, including distributed denial-of-service (DDoS) attacks on their website, Facebook page and YouTube channel, as well as phishing attempts using sophisticated social engineering tactics to infect devices and steal data.
The authors of The Citizen Lab report recommended that states hosting exiled community members share information with them about the risks they face and provide assistance to help them mitigate the risks and impacts of transnational repression.
“The growing industry practice led by companies like Google and Apple of issuing notifications when individuals are targeted by state actors is one that needs to be standardized and replicated across all companies that provide digital services to vulnerable communities,” the researchers concluded.

