- Best early Prime Day robot vacuum deals: My 20 favorite sales live now
- How to Create Smarter Networks
- Publisher's Spotlight: NAKIVO Backup & Replication v11
- This high-tech eye massager is the only thing that helps my migraines, and it's 48% off
- NordPass lets you store passports and other IDs now - but is this safe?
How phishing attacks spoofing Microsoft are evading security detection

The phishing emails use a Microsoft logo within an HTML table, which is not analyzed by security programs, says Inky.
Image: Getty Images/iStockphoto
Cybercriminals who specialize in phishing campaigns are always inventing new tactics to sneak past traditional security tools. In a recent campaign discovered by email security provider Inky, attackers impersonating Microsoft are using a devious method to spoof the software giant’s latest logo. Released on Wednesday, Inky’s report “The Microsoft Table Logo Impersonation Scam” describes how this method plays out.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
The scam takes advantage of HTML code by incorporating an embedded table that contains a spoofed version of the Microsoft logo. This works because email security programs don’t analyze tables because they haven’t traditionally been used in phishing emails. The spoofed logo looks just like Microsoft’s actual logo, so the content is able to pass through security filters and appears legitimate to potential victims.
Ironically, Microsoft itself inadvertently contributed to this scheme. The company’s old logo image displayed the familiar four colors in a contoured, three-dimensional style. In 2012, Microsoft changed and simplified its logo using the same colors but in a flat, two-dimensional layout. Because of its simplicity, the new logo is easier to spoof as anyone can create four cells in a table, each with one of the four colors as the background.

Images: Microsoft
In its report, Inky cited three phishing campaigns in which the fake logo played a role.
Fake SharePoint email
In this instance, the customized HTML logo appears in a phony fax notification. Displaying the logo with SharePoint branding, the email contains a link for the alleged notification that says: “Preview or Download Here.” Clicking the link briefly takes the user to the China UNICEF site and then redirects to a legitimate web development tool site called CodeSandbox where malware is installed on the computer. The fake table and logo combined with redirects to legitimate sites can trick people into taking the bait.
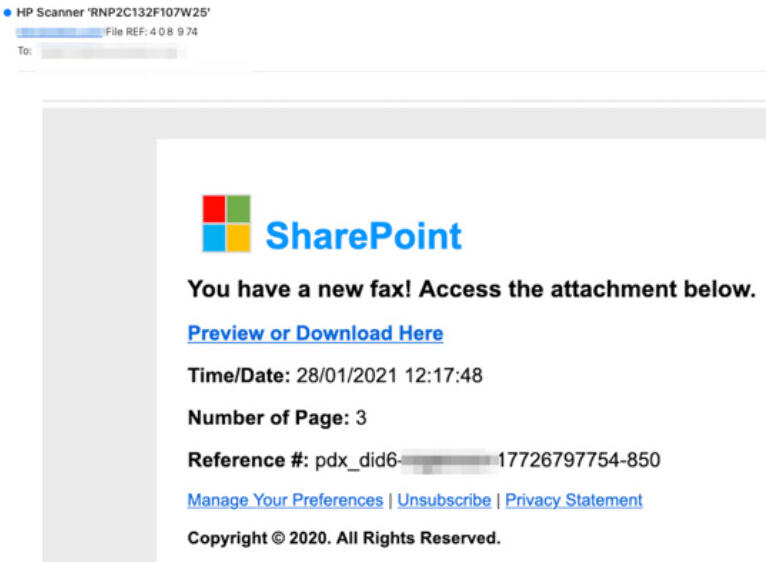
Image: Inky
Office 365 spoof
Using Office 365 with the spoofed Microsoft logo, this campaign warns recipients that their password has expired. The email contains a link that says: “Keep My Current Password.” Clicking the link takes the users to a hijacked but legitimate marketing email platform and then redirects to the CodeSandbox site to install malware. Again, the attacker uses the phony logo, the embedded table, and open redirects to fool potential victims.
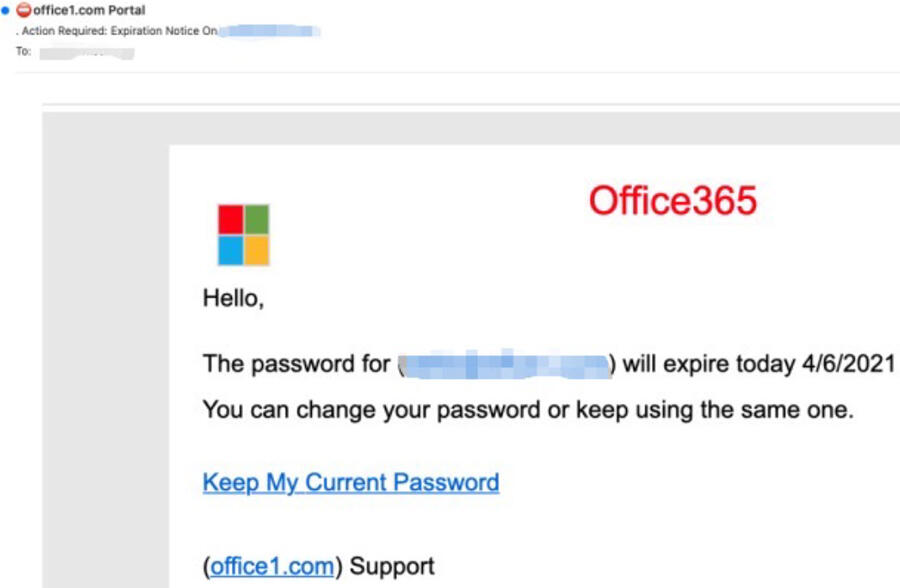
Image: Inky
Bogus voicemail notification
In this campaign, the phony HTML table logo is placed in a bogus voicemail notification. The malicious link is hidden in an HTML attachment encoded in hexadecimal to sneak past traditional security detection. By using the Microsoft logo, a hidden malicious link, and hexadecimal strings, the email is better able to escape security detection and fool the recipient.
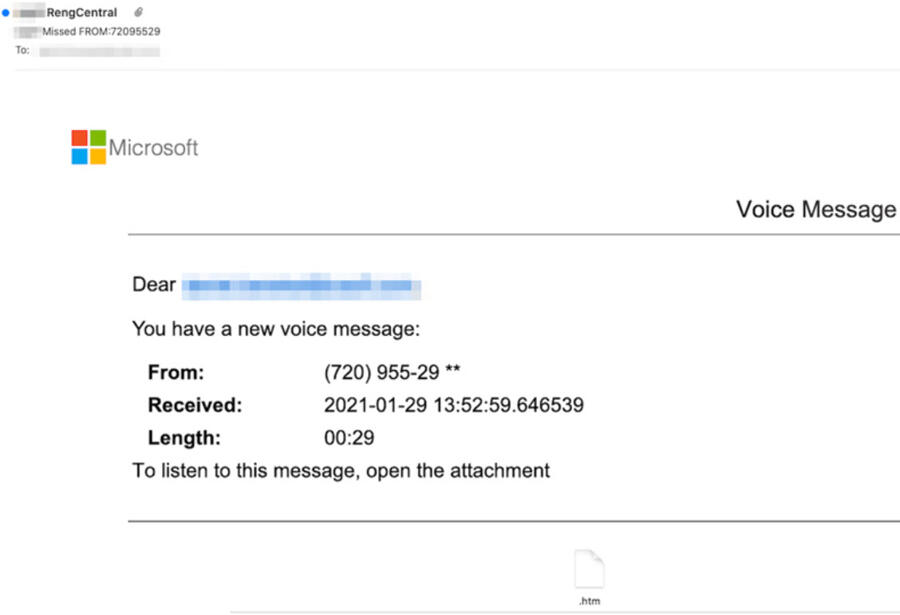
Image: Inky
Recommendations
These kinds of sophisticated phishing emails are difficult to discern. They look legitimate to the human eye. And they escape the kind of detection and protection offered by traditional email filtering and security products, including those from Microsoft itself.
The best way to analyze these types of attacks is to use both human and machine and compare the results. Even if the email is so expertly designed that it looks legitimate to the recipient, a good anti-phishing tool can tell whether it actually came from an actual Microsoft domain. Such a tool would use computer vision and artificial intelligence to see that the HTML table is trying to use a Microsoft logo. The system would then determine whether the sender truly is Microsoft.


