- The iPad I recommend to most users is only $299 right now
- One of the most versatile action cameras I've tested isn't from GoPro - and it's on sale
- Small Manufacturers, Big Target: The Growing Cyber Threat and How to Defend Against It
- Why I pick this JBL speaker over competing models for outdoor listening
- Testing a smart cooler proved I can never go back to toting ice (and it's on sale)
How a malicious bot tries to evade detection by morphing

Targeting Windows and Linux systems, the Necro Python bot changes its code to evade traditional security detection, says Cisco Talos.
Image: Cisco Talos
Cybercriminals often use automated bots to deploy malware infections, take control of remote computers and carry out other cyberattacks. Though a bot sounds like it might be limited in intelligence and flexibility, a sophisticated bot can do a lot of damage on behalf of the attacker. A report published Thursday by threat intelligence provider Cisco Talos looks at one bot that includes code morphing as part of its repertoire.
SEE: Security Awareness and Training policy (TechRepublic Premium)
Dubbed Necro Python, this bot goes after computers that run Windows or Linux by exploiting security vulnerabilities in the operating system or an installed application.
To carry out the initial infection, Necro uses a Java-based downloader. The malware is deployed through a Python interpreter and a malicious script along with executable files created using the Python app program pyinstaller.
Though Necro first surfaced earlier this year, the latest iteration reveals a variety of changes and new powers. The activity spotted by Talos shows different command and control (C2) communications and new exploits to help it spread. In particular, the bot takes advantage of vulnerabilities in VMWare vSphere, SCO OpenServer, and Vesta Control Panel as well as Windows SMB-based flaws, none of which was seen in earlier versions of the code.
One of the more alarming capabilities uncovered in Necro’s latest flavor is code morphing. Talos found that the script code can morph into a different form after every iteration. This skill turns Necro into a polymorphic worm that can spread by abusing a growing number of web-based interfaces and SMB exploits.
Beyond the morphing ability, Necro installs a user mode rootkit to hide its malicious files, processes and registry entries. The overall goal is to make the bot harder to detect. These tactics could help Necro evade traditional and basic security protection, but Talos said that that it would be caught by more modern detection tools, including Extended Detection and Response products.
SEE: Apple supplier Quanta hit with $50 million ransomware attack from REvil (TechRepublic)
The bot has another trick up its sleeve in the form of Monero mining, a popular type of cryptocurrency mining. To set this up, Necro installs a variant of xmrig, which is an open-source program that uses a system’s CPU for Monero mining. The bot also injects malicious code into HTML and script files to add a JavaScript-based miner and more ways to control and hijack information from different browsers. If the user opens an infected application, the JavaScript Monero miner then runs via the browser.
Necro specifically tries to exploit server-side software to spread throughout a network. Like other bots such as Mirai, Necro targets small and home office routers. But it uses Python to hit different operating systems instead of downloading code compiled for each platform.
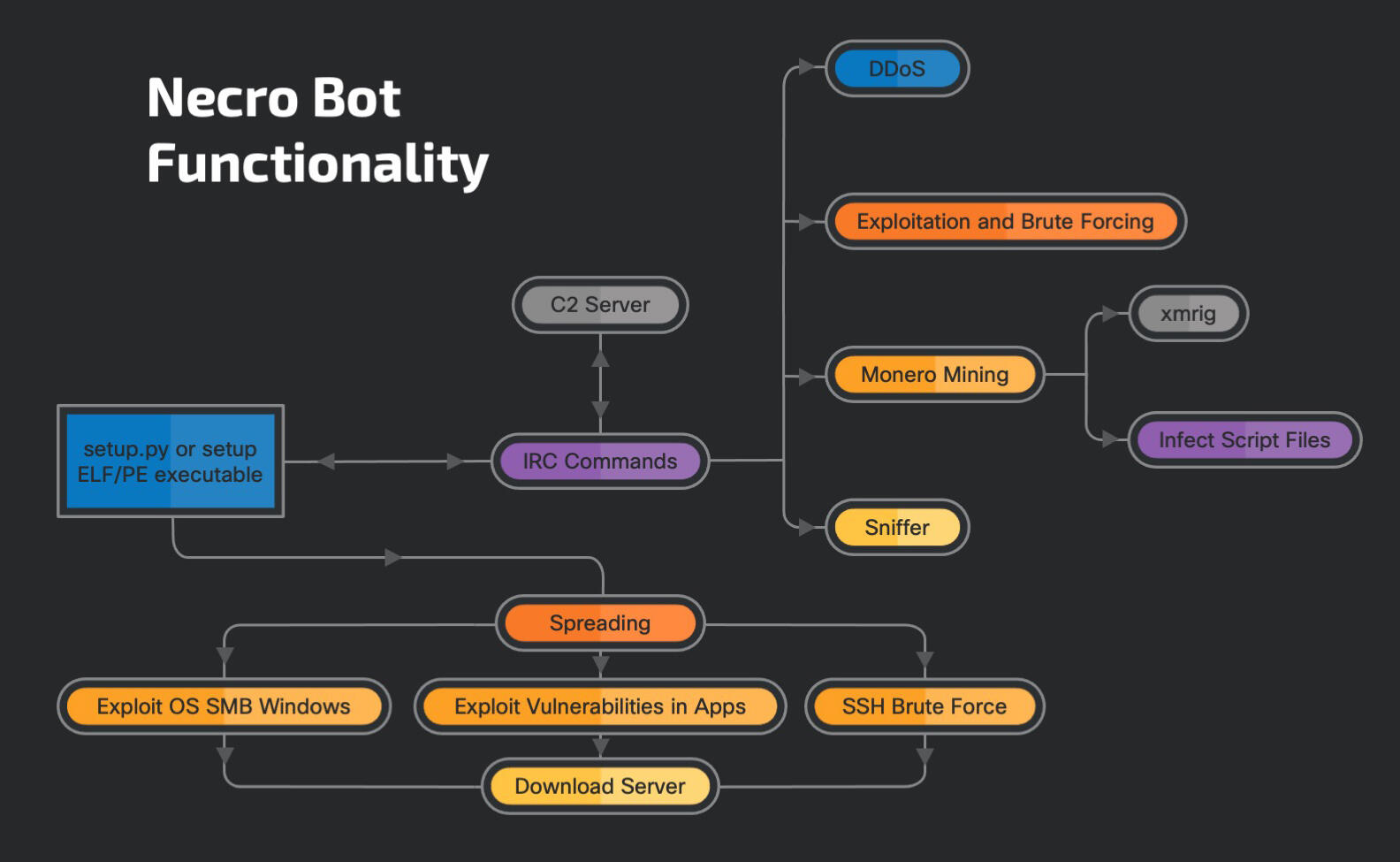
High-level overview of the Necro bot and its functionality.
Image: Cisco Talos
“Necro Python bot shows an actor that follows the latest development in remote command execution exploits on various web applications and includes the new exploits into the bot,” Talos said in its report. “This increases its chances of spreading and infecting systems. Users need to make sure to regularly apply the latest security updates to all of the applications, not just operating systems.”
To help organizations protect themselves against malicious bots like Necro, Cisco Talos threat researcher Vanja Svajcer offers the following advice:
Apply the latest security patches, especially on servers. The most important way to defend against bots and worms like Necro is to install the latest security patches for your applications and operating systems. With Necro, the targeted applications are server-side, so you need to make sure your servers are updated with the right patches.
Implement a strong password policy. Necro has a list of default credentials that it uses to try to authenticate access over Secure Shell. For that reason, organizations need to set a strong password policy combined with multi-factor authentication. Also, be sure to change the default credentials on any internet-facing hardware or software.
Use solid endpoint detection and prevention tools. Relying on a reputable endpoint protection product and keeping it properly configured and updated can help stop Necro and similar threats.


