- Nvidia aims to bring AI to wireless
- Anthropic's new AI models for classified info are already in use by US gov
- My cat loves this automatic wet food feeder, and it's on sale
- Certified and Unstoppable: Recertify with Rev Up
- Walmart's drone delivery spreads its wings to 100 more stores - is yours one?
Microsoft’s June 2021 Patch Tuesday Addresses 49 CVEs (CVE-2021-31955, CVE-2021-31956 and CVE-2021-33742)

CVE-2021-33739 | Microsoft Desktop Window Manager Core Library Elevation of Privilege Vulnerability
CVE-2021-33739 is an EoP vulnerability in the Microsoft Desktop Window Manager (DWM) core library, dwmcore.dll. It was discovered and reported to Microsoft by researchers at DBAPPSecurity Threat Intelligence Center. In February, DBAPPSecurity Threat Intelligence Center disclosed another zero-day vulnerability, CVE-2021-1732, an elevation of privilege vulnerability in Win32k linked to a threat actor known as BITTER APT. In April, researchers at Kaspersky disclosed CVE-2021-28310, an elevation of privilege zero-day vulnerability in Microsoft DWM Core Library that they connected to multiple threat actors including BITTER APT. While it has not yet been confirmed, it is possible this is another zero-day leveraged by BITTER APT in the wild.
CVE-2021-31983, CVE-2021-31946, CVE-2021-31945 | Multiple Vulnerabilities in Paint 3D
CVE-2021-31983, CVE-2021-31946 and CVE-2021-31945 are RCE vulnerabilities in Microsoft’s Paint 3D, which replaced the original MS Paint. All three received a CVSSv3 score of 7.8 and a severity of Important with an “Exploitation Less Likely” designation. These vulnerabilities are more interesting than concerning. They all require user interaction and the application will automatically update in most cases. However, all three vulnerabilities were discovered by several different researchers including Mat Powell from Trend Micro Zero Day Initiative, Li Qiao of Baidu Security Lab, and garmin working with Trend Micro Zero Day Initiative. One can only speculate why these researchers were examining Paint all at once, unless more information becomes available. Paint 3D wasn’t able to provide any insights either.
Beats us.
— Paint 3D Edu. (@Paint3Dedu) June 8, 2021
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains June 2021.
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
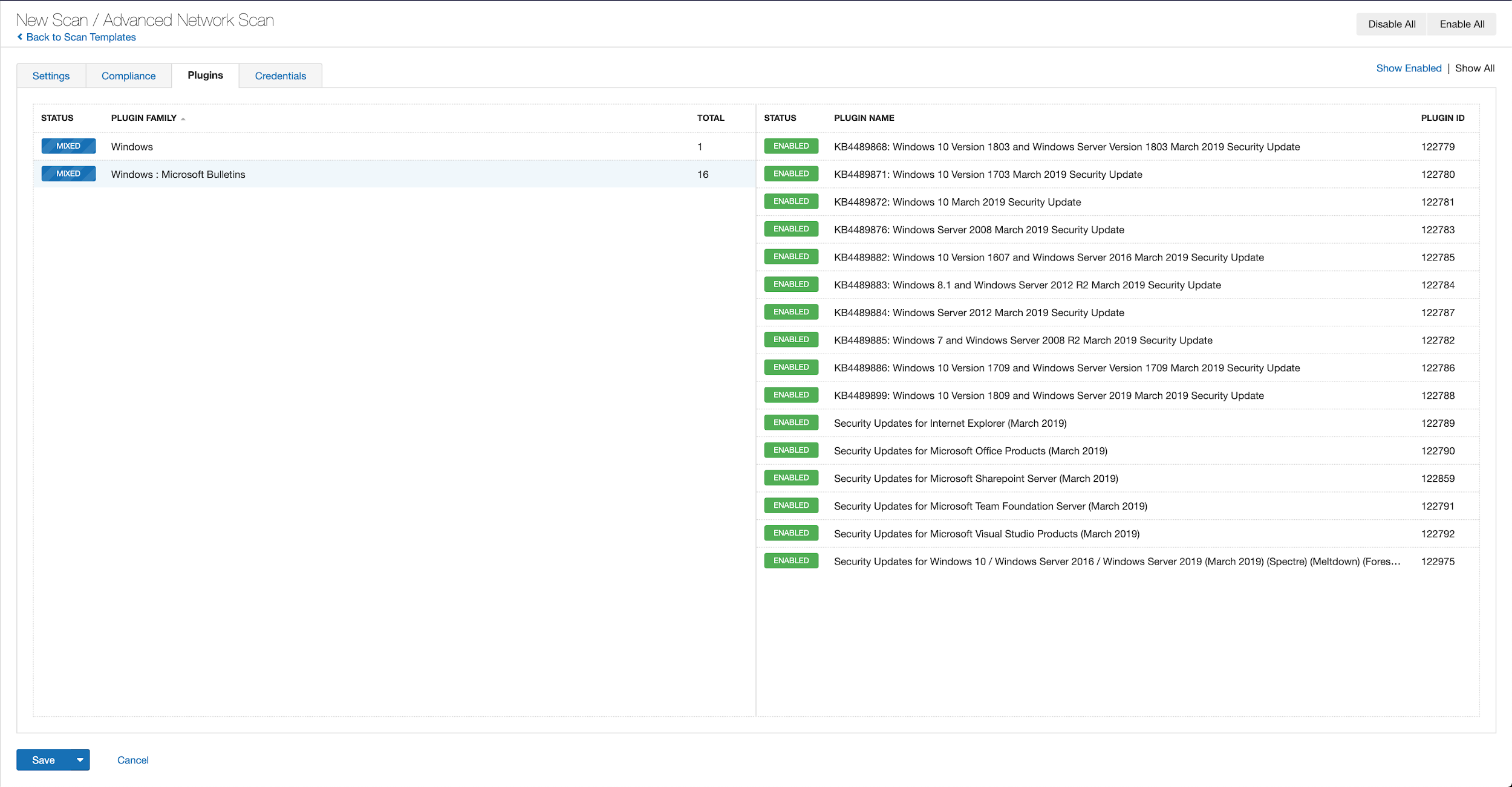
A list of all the plugins released for Tenable’s June 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.

