- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Takeaways from The Oldsmar Water Attack & What Security Leaders Can Do About It

With Real Examples & Screenshots of Cyber Attacks on Water & Wastewater Facilities
By Michael Yehoshua, VP of Global Marketing, SCADAfence
Over the last few months, cybersecurity journalists and the ICS security community have been discussing the Oldsmar Florida water system cyber-attack and other similar attacks on water infrastructure, almost ad nauseam. While many people have been talking about this “news” topic, we’ve actually been treating this issue with many of our customers over the past few years. In this article, I will explain what we’ve learned from this cyberattack, but most importantly, I will share how we’ve been busy solving these issues over the last few years with actual examples from our range of industrial cybersecurity products.
The Oldsmar Water Facility Attack
Back in February 5th, a hacker gained access into the water treatment system of Oldsmar, Florida, and hijacked the plant’s operational controls. He was able to temporarily drive up the sodium hydroxide content in the water to poisonous levels. The Oldsmar facility is the primary source of drinking water for the city’s 15,000 residents. Luckily, a plant operator was able to return the water to normal levels. The incident has nonetheless launched many conversations about the state of security in global critical infrastructure.
But that wasn’t the whole story.
A security advisory released in March by the state of Massachusetts’s Department of Environmental Protection, referred to additional unsafe practices or behaviors at the Oldsmar water treatment plant that significantly increased the risk further. Like many other facilities of its kind, Oldsmar uses a SCADA (Supervisory Control And Data Acquisition) system that allows staff to monitor and control conditions within the facility. At the same time, the staff was using TeamViewer, a fairly common remote access program, which can be used to monitor and control systems within the SCADA network. Sadly, cybersecurity was not a priority for the facility, as is the case occasionally with critical infrastructure. Not only was the Oldsmar facility using Windows 7 – an outdated software that is no longer supported by Microsoft, but all of their employees shared the same password to access TeamViewer. Additionally, the facility was connected directly to the internet without any type of firewall protection installed.
The Current Situation with Water Systems
In the United States alone, there are about 54,000 distinct drinking water systems. The vast majority of those systems serve less than 50,000 residents. They mainly rely on some type of remote access to monitor and/or administer their facilities. Many of their facilities are also unattended, underfunded, and do not have someone watching the IT operations 24/7. Finally, many facilities have not separated their OT (operational technology) networks from their safety systems that are in place in order to detect intrusions or potentially dangerous changes by threat actors.
While the attempt was spotted and taken care of by a plant operator before it could do any damage, it raises questions about how serious a threat this sort of terrorist or nation-state action could be in the future.
Why Don’t We See More Stories Like This On The News?
So, despite how easy it is to find ways to remotely interact with such OT networks, we aren’t seeing more incidents like the one in Oldsmar making the news. One reason may be that these facilities don’t have to disclose such events right when they happen. Additionally, many companies, especially in the public sector want to avoid bad publicity and do what they can to avoid their company name smeared in cyber-attack news headlines. We’ve seen many companies, especially publicly traded companies lose stock value and brand trust after a cyberattack.
But the main reason you don’t see more of these attacks on the news is that SCADAfence protects many of these critical infrastructure facilities.
Over the last seven years, SCADAfence has been working with many critical infrastructure organizations, including water & wastewater facilities to keep their OT networks safe. We do this by providing them with full network visibility, we accurately detect any anomalous behavior and malicious activities – including anomalies that originate in remote access. We were ready for 2020 before remote access security was required (due to the lockdowns) and it’s been paying off dividends. Here is a case study of the City of Hutchinson, Kansas.
Here’s How SCADAfence Secures Water Treatment Facilities
Let me show you a few key examples, (with actual screenshots) of how we have prevented identical attacks over the last seven years for our customers.
- With the SCADAfence Platform’s continuous network monitoring we have been easily been able to detect any remote access into OT networks, specifically, detailed alerts for TeamViewer connections in OT networks.
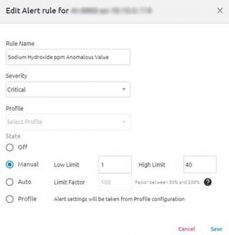
- We also immediately alert on value level changes, once they pass a certain threshold to prevent unauthorized changes or process manipulation. The platform is also so flexible that users can create specific firewall-like rules for variables such as this one: “Sodium Hydroxide ppm Anomalous Value” alert. This will raise an alert in case the value of Sodium Hydroxide in the water exceeds the max value of (for example) 40 ppm (parts per million) or goes below 1 ppm.
- The SCADAfence Platform also provides visual exposure maps that can spot malicious activities – weeks, or even months in advance. At another similar incident (that didn’t hit the news), we monitored a water treatment facility during normal operations. As you can see in the screenshot below, there was no connectivity between the remote access group and the DMZ group.
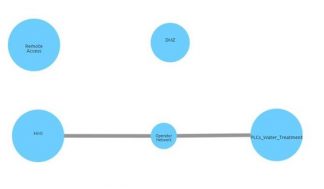
During an attack on the facility, the security team was immediately able to see new connections forming from the remote access group to the DMZ group and from the DMZ to the operator network group (see below). As soon as that alert was issued, the security team was notified of that change and the remote access connection was disconnected, stopping the attackers immediately.
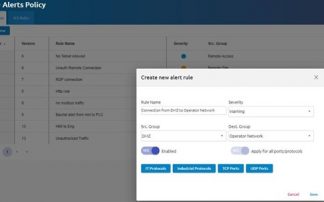
- It’s really easy to set automated rules that will alert in case there is connectivity between specific network groups. In this case, we set an alert if there is a connection from the DMZ to the operator network and a similar rule in case there is a connection from the remote access to the DMZ group.
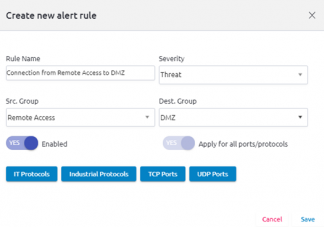
- This incident at Oldsmar, highlights what we’ve been saying for years. Remote access in OT networks provides a big risk. And the thing is, remote access is not going away.
The SCADAfence platform also provides security staff with the correlation between their users and their activities while performing remote work.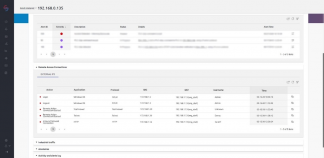
In addition to alerts on anomalous or unauthorized actions in the OT network, the SCADAfence Platform provides security teams with the association details – including the user name, the originating workstation, and the application to provide a holistic view into remote access activities, hop-to-hop.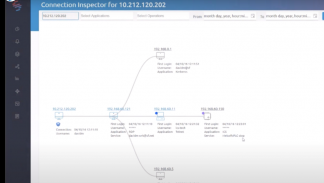
- This also ties into the issue of compliance with industrial standards. SCADAfence offers a governance portal that enables operators to define compliance enforcement policies, and continuously monitor compliance enforcement status for most ICS standards, frameworks, and regulations.
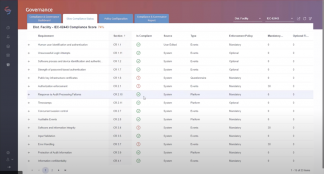
Don’t Be Scared, Be Prepared
Many water & wastewater utilities are already using continuous network monitoring and remote access technologies to get visibility into their OT networks and keep their critical infrastructure networks secure.
With this holistic approach, of network monitoring, anomaly detection, remote access visibility, and compliance, many water & wastewater are already reducing 95% of their risk level of future attacks.
The best part is that these solutions are all agentless, are not intrusive, and can perform superhuman tasks at a fraction of the cost of one human worker.
If your organization is looking into securing their industrial networks, the experts at SCADAfence are seasoned veterans in this space and can show you how it’s done.
To learn more about these products and see short product demos, click here: https://l.scadafence.com/demo
About the Author
 Michael brings 15 years of marketing creativity and out-of-the-box thinking to SCADAfence. Before joining the team, Michael was the Director of Marketing at TrapX Security, where he was famous for thought leadership and for turning a small, declining startup into a successful, profitable world-leading vendor in their vertical. Prior to that, Michael was the VP of Marketing at AMC and rebuilt their entire marketing architecture, bringing in strong revenue figures that the firm has’t seen in decades. Michael studied at Harvard Business School, at Bar Ilan University for his MBA & Lander College for his BS degrees in Marketing and Business Management.
Michael brings 15 years of marketing creativity and out-of-the-box thinking to SCADAfence. Before joining the team, Michael was the Director of Marketing at TrapX Security, where he was famous for thought leadership and for turning a small, declining startup into a successful, profitable world-leading vendor in their vertical. Prior to that, Michael was the VP of Marketing at AMC and rebuilt their entire marketing architecture, bringing in strong revenue figures that the firm has’t seen in decades. Michael studied at Harvard Business School, at Bar Ilan University for his MBA & Lander College for his BS degrees in Marketing and Business Management.
Michael can be reached online at (marketing@scadafence.com, https://www.linkedin.com/in/michael-yehoshua/) and at our company website https://www.scadafence.com/

