- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Is The Cloud Leaving You Exposed?

Exploring the public cloud and addressing its unanticipated security challenges
By Chuck Slate, Lead Architect, Attivo Networks, Inc.
On a traditional network, user accounts are the main identity type and, therefore, the primary security focus. In the public cloud, the concept of identity is extended to any object with entitlements (permissions) to another object. This includes “non-human” identities like applications, containers, virtual machines, and other object types that have historically played the role of a resource only.
A core benefit of the public cloud is that it offers managed services such as database, DNS, and storage services. Managed services free admins from the responsibility of having to build and maintain substantial pieces of the cloud infrastructure for themselves. Instead, they define a database table, for example, and grant access to the applications that need it. (In such a scenario, the applications function as non-human identities vis-à-vis the managed database because they have permissions to read or write to the managed database’s table.)
The sheer volume of cloud identities and entitlements resulting from new concepts like non-human identities and managed services can leave cloud security professionals overwhelmed and often blind to the full extent of their exposure.
The Wild West of Identities and Entitlements
What might amount to hundreds of identities on a traditional network could translate into thousands in the public cloud. That increase in the number of identities exacerbates existing security challenges. For example, “privilege creep” is the idea that identities accumulate access to more resources than they need over time. This situation has historically been a common problem on traditional networks. Because the public cloud has that many more identities, privilege creep is that much more probable and dangerous in the public cloud. The public cloud has also seen an increase in the number of relationships between objects and, consequently, the number of entitlements. On a traditional network, for example, a user may have access to an endpoint. In the public cloud, that same user may have access to a virtual machine, which may, in turn, have access to an application, which may then have access to an API, a database, and a storage bucket.
The public cloud also introduces a unique set of identity-specific obstacles. For example, many corporations have a multiple-cloud strategy, and using multiple accounts within a single cloud platform is standard. As a result, there is no native way to assess an enterprise-wide security posture or view assets across platforms from a single management console. Moreover, organizations routinely sync identities from their local Active Directory with the public cloud to provide single sign-on services for seamless access to local and cloud resources alike. To understand the risk associated with Active Directory and public cloud integration, one needs only to consider the SolarWinds breach, which started with an on-premises compromise and led to the exfiltration of public cloud data.
The larger the public cloud footprint, the harder it is to track the set of cloud identities and their relationships with other cloud objects. Without proper visibility, accurate risk assessment and mitigation is an uphill battle.
A New Frontier
Developers did not design traditional IGA and PAM solutions for the public cloud, so they struggle to address its unique security challenges. Existing CSPM, CWPP, and CASB tools address specific aspects of cloud infrastructure security, but they generally lack identity-centric analysis and access controls. Manual methods to ensure a least-privilege approach to cloud security do not scale in an environment with large quantities of identities and entitlements.
Existing security paradigms do not inherently address the needs of cloud identity security, and a new segment of the security market has recently emerged in response to this blind spot. Industry analysts have created new acronyms to describe it, including Cloud Infrastructure and Entitlements Management (CIEM, pronounced “Kim”) and Cloud Permissions Management (CPM).
The common goals among the solutions in this budding sector can be summarized as follows:
- Discover all cloud identities, cloud resources, and the entitlements between them
- Support multiple cloud accounts and multiple cloud platforms in a consistent fashion
- Provide graphical analysis of the relationships cloud objects have with each other
- Highlight risky privileges and entitlement changes to critical cloud assets
- Enable clear and straightforward action to mitigate risk and reduce exposures
More to Cloud Security Than Just the Cloud
Most offerings in this nascent space focus exclusively on managing identities and entitlements in the cloud itself. As previously mentioned, however, the SolarWinds breach is an excellent example of an identity attack that exploited and manipulated both on-premises and cloud identities alike. In the end, cloud-specific visibility is only one piece of the larger security puzzle.
An attacker compromising a workstation on a traditional network, for example, can exploit its user credentials to access Active Directory and its resources.
When Active Directory credentials have been synchronized with the public cloud, that same attack has many more vectors available and can therefore do that much more damage.
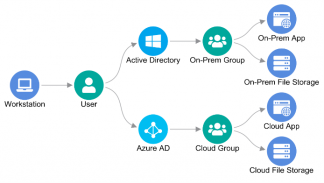
A Comprehensive Approach
Installing a cybersecurity solution that performs analysis on public cloud identities and entitlements alone is like buying a home security solution that only puts a camera on the front door. In both cases, the solution cannot achieve its intended goal because it does not have the visibility it needs to adequately assess and mitigate risk for all possible attack paths.
For comprehensive protection, a solution must have a focus on identities and entitlements across the board. Specifically, it must be able to:
- Intake and analyze identities and entitlements from endpoints
- Intake and analyze identities and entitlements from Active Directory
- Intake and analyze identities and entitlements from multiple public cloud platforms and accounts
- Correlate the analysis results across the data sources and display them in a complementary fashion on a single pane of glass
As corporations continue to move to the public cloud, they must adopt a technology that provides a thorough analysis of their cloud identities and entitlements. That technology must, in turn, be part of a more extensive solution that monitors and protects identities and entitlements throughout the entire enterprise.
About the Author
 Chuck Slate holds the role of Lead Architect at Attivo Networks. Chuck has over 25 years of experience building security solutions with expertise in computer networking and UI/UX design and development. Chuck earned his master’s degree in Computer Science from Boston University. Chuck Slate can be reached online at (chuck.slate@attivonetworks.com, https://www.linkedin.com/in/chuck-slate/ and at our company website http://www.attivonetworks.com
Chuck Slate holds the role of Lead Architect at Attivo Networks. Chuck has over 25 years of experience building security solutions with expertise in computer networking and UI/UX design and development. Chuck earned his master’s degree in Computer Science from Boston University. Chuck Slate can be reached online at (chuck.slate@attivonetworks.com, https://www.linkedin.com/in/chuck-slate/ and at our company website http://www.attivonetworks.com

