- ServiceNow to acquire Logik.ai to boost CRM portfolio
- Mechanical Orchard taps gen AI for mainframe-to-cloud modernization
- How Bill Gates, the Altair 8800 and BASIC propelled me into the PC revolution
- These wireless headphones are an audiophile's dream - and my new all-time favorite
- 11 Samsung Galaxy phone settings I always change right away - here's why
CVE-2021-1609: Critical Remote Code Execution Vulnerability in Cisco Small Business VPN Routers

Cisco releases patches for Critical vulnerabilities in its line of Small Business VPN Routers.
Background
On August 4, Cisco released several security advisories, including an advisory for two vulnerabilities in a subset of its line of Small Business VPN Routers.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2021-1609 | Web Management Remote Code Execution and Denial of Service Vulnerability | 9.8 |
| CVE-2021-1610 | Web Management Command Injection Vulnerability | 7.2 |
The table below lists which routers in the Small Business line are vulnerable:
| Cisco Small Business Router Model | Status |
|---|---|
| RV340 Dual WAN Gigabit VPN Router | Vulnerable |
| RV340W Dual WAN Gigabit Wireless-AC VPN Router | Vulnerable |
| RV345 Dual WAN Gigabit VPN Router | Vulnerable |
| RV345P Dual WAN Gigabit POE VPN Router | Vulnerable |
| RV160 VPN Router | Not Vulnerable |
| RV160W Wireless-AC VPN Router | Not Vulnerable |
| RV260 VPN Router | Not Vulnerable |
| RV260P VPN Router with PoE | Not Vulnerable |
| RV260W Wireless-AC VPN Router | Not Vulnerable |
Analysis
CVE-2021-1609 is a critical-rated vulnerability in Cisco’s web management interface for Cisco Small Business routers that was assigned a CVSSv3 score of 9.8. According to Cisco, the flaw exists due to improper validation of HTTP requests. A remote, unauthenticated attacker could exploit the vulnerability by sending a specially crafted HTTP request to a vulnerable device, resulting in arbitrary code execution as well as the ability to reload the device, resulting in a denial of service.
CVE-2021-1610 is a high-rated command injection vulnerability in the same web management interface. While both flaws exist due to improper validation of HTTP requests and can be exploited by sending specially crafted HTTP requests, CVE-2021-1610 can only be exploited by an authenticated attacker with root privileges. Successful exploitation would grant an attacker the ability to gain arbitrary command execution on the vulnerable device’s operating system.
Cisco is careful to note that both of these vulnerabilities can be exploited independently of each other, and that some versions of the Small Business VPN Router software may only be affected by one of the two vulnerabilities.
Web management interface default exposure is limited
Cisco’s advisory clarifies that the web management interface for its small business VPN routers is available by default through local area network connections and can’t be disabled. Under this default configuration, a local attacker could potentially gain arbitrary code execution. However, Cisco notes that remote management of these devices is disabled by default.
Example of a remotely accessible Small Business VPN Router login page
Over 8,800 devices publicly accessible
Despite the remote management feature being disabled by default, Tenable’s Security Response Team found over 8,800 devices publicly accessible according to BinaryEdge. The table below lists the publicly accessible devices.
| Affected Device | Publicly Accessible |
|---|---|
| RV340 | 5,679/5,673 |
| RV340W | 684/685 |
| RV345 | 1,845 |
| RV345P | 642 |
| Total | 8,850 |
Cisco VPN routers historically targeted
In January 2019, Cisco published advisories for two different vulnerabilities in its RV320 and RV325 WAN VPN routers. A few days after the advisories were published, proof-of-concept exploit scripts for these flaws were published, which was followed by active scanning for vulnerable devices. Because of this historical precedent, we believe it is important that organizations patch these latest vulnerabilities as soon as possible.
Proof of concept
At the time this blog post was published, there were no proofs-of-concept (PoC) available for either CVE-2021-1609 or CVE-2021-1610.
Solution
Cisco says that firmware version 1.0.03.22 and later fixes these vulnerabilities in the affected versions of its Small Business VPN Routers. Organizations are strongly encouraged to patch these routers as soon as possible.
If patching is not feasible at this time, a way to mitigate the threat of remote exploitation would be to disable the remote management feature on these devices.
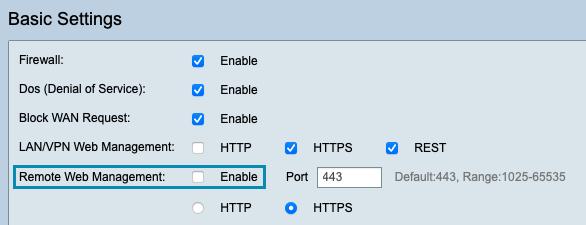
Under the Firewall section, select the Basic Settings menu option then ensure that “Remote Web Management” is unchecked. As mentioned previously, this setting is unchecked — disabled — by default. If it has been enabled, uncheck it and press Apply to update the configuration.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.


