- 7 Linux distros you should avoid until you've mastered the command line
- 5 ways to use the Linux terminal on your Android phone - including my favorite
- A few secretive AI companies could crush free society, researchers warn
- Key Cybersecurity Considerations for 2025
- Make the Most of Your Holiday Cybersecurity Awareness Efforts
Improve Cloud Security With MITRE ATT&CK Enterprise Cloud Framework Support From CloudHealth Secure State – Cloud Blog – VMware

Between ransomware, cryptocurrency mining operations, and data breaches, threats to the modern cloud-native applications and workloads that enterprises use are undoubtedly on the rise. Meanwhile, attacker groups are becoming more effective and dangerous, leaving many organizations stuck between a rock and a hard place when it comes to cybersecurity.
According to many practitioners, one of the greatest challenges in cybersecurity is the lack of mutual understanding between the many hats and roles within the field: when a compliance officer talks about a vulnerability, they usually refer to one of many backlog entries over the infrastructure they govern. On the other hand, when a Red Team member talks about a vulnerability, they usually have something specific in mind that they think can be exploited and used as part of a larger attack.
These, and other differences in perspective often run deeper than terminology and reflect the underdefined nature of cybersecurity – it’s a goal, not a process; a destination without a roadmap; a disparate landscape of partial solutions that do one thing well (at most), while remaining oblivious of the larger context.
This is where the original MITRE ATT&CK Enterprise Matrix comes into play – it was designed from the ground up to be the common language of the offender’s playbook, the lingua franca of host compromise tactics. Only one problem – it covers traditional infrastructure, rather than cloud-based deployments. Did I say it covers? I meant to say used to cover, because in 2019, the MITRE corporation released the Cloud Matrix, which is solely focused on cloud attack vectors.
At CloudHealth Secure State, we’re very interested in all tools for cloud security, and we couldn’t pass up this opportunity to further empower our customers to improve their cloud security posture. So in March 2021, we released support for the MITRE ATT&CK Enterprise Cloud Matrix as a compliance framework. With that in mind, let’s take a look at three ways you can leverage the Enterprise Cloud matrix to improve your cloud security posture.
Mapping the unknown unknowns
One of the leading principles of law from Roman times says, “ignorance of law excuses no one.” Cloud security should look to adopt a similar moto: “what you don’t know, could very well get you breached.” Recent examples are ample, such as the barrage of software supply chain attacks.
This is the most fundamental and underrated benefit, provided by the Enterprise Cloud Matrix – a structured map of areas, relevant to cloud security and a perfect starting place to discover one’s blind spots. While not as flashy or advanced as the rest of this list, reducing the “unknown unknowns” earns our first mention because of its extreme importance in the fast-moving world of cloud security.
Here’s how to get started with the MITRE ATT&CK Enterprise Cloud Matrix using CloudHealth Secure State:
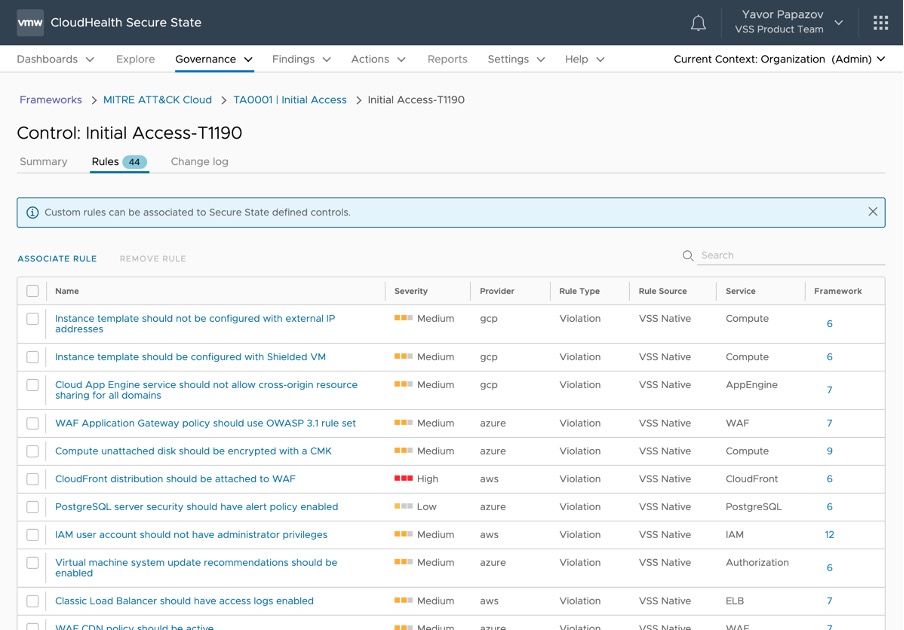
Go to the Governance tab in the CloudHealth Secure State platform and select Compliance. Move to the second page and click on the framework name, “MITRE ATT&CK Cloud.” The screen above is how the result should look, with a listing of all tactics included in the MITRE ATT&CK Enterprise Cloud Matrix. Every tactic has an ID starting with TA and followed by a number and name, such as TA0001 and “Initial Access.” Clicking on any of the tactics will reveal the techniques that are used within this tactic.
One of the techniques within the Initial Access (TA0001) tactic is T1190, or Exploit Public-Facing Application. Within Secure State, selecting a particular technique will reveal all rules mapped to this technique. This functionality allows risk filtering based on the MITRE mapping and thus, enables prioritizing defense against chosen tactics and techniques.
Using a common language with your SOC and Red/Blue teams
This is the big one – when the benefits of the MITRE ATT&CK Enterprise Cloud Matrix are discussed, the “Common Security Language” point is always mentioned, due to the immense utility it provides. Let’s take some time to map out how this works in practice.
Say your SOC identifies an active campaign, currently targeting cloud infrastructure by trying to exploit a public-facing application (or TA0001 > T1190 in Cloud Matrix terms). Due to the distributed nature of cloud security responsibilities (SOC, Red/Blue/Purple Teams, DevSecOps, etc.) it’s often essential to ensure all responsible parties are up to date and informed on all gathered threat intelligence.
Without MITRE, you’re likely to spend a significant amount of time and effort communicating the exact nature of the tactic and technique(s) the attackers are using. However, thanks to MITRE, you can (correctly!) summarize the entire ordeal with “Attacker group is using T1190 to breach our cloud presence” and the rest of the room can know exactly what the problem is. Not only that, but due to the inherent sequential nature of the Matrix’ tactics, you generally know where the attacker might redirect their efforts. In this case, the relevant Tactic is “Initial Access” and it’s a strong indication that the attacker has no other means of access to your infrastructure. This means that if the T1190 technique is successful, the attacker will move to TA0002 – “Execution.” But if it fails, the focus will be on other techniques that provide Initial Access, such as T1078 (Valid accounts) or T1199 (Trusted relationship).
That’s all well and good, but where does CloudHealth Secure State come in? Glad you asked. All of CloudHealth Secure State’s rules are mapped to the MITRE ATT&CK Enterprise Cloud Matrix’ relevant tactics and techniques, so that you can easily answer questions like, “What are the most severe rules that map to this technique?”
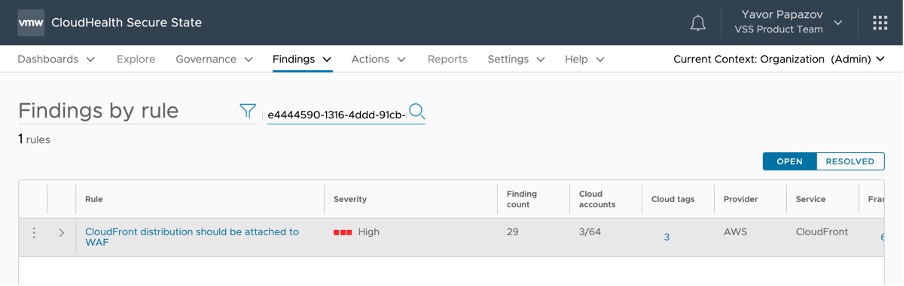
In our case, one of the severe rules identified is “CloudFront distribution should be attached to WAF,” so it makes sense to check this rule (Rule ID e4444590-1316-4ddd-91cb-541c5c054820) and its findings (Findings > Findings by rule, then search by Rule ID) and forward the findings to their respective owner. Following this process will not only help to improve your general cloud security posture, but more pertinently, improve your ability to defend against “Exploit Public-Facing Application (T1190).”
Taking a data-driven approach to cloud security resource prioritization
It’s been said that “data is the currency of the future,” and as it turns out, using MITRE can help us leverage this currency. Continuing our example from the previous point, a natural direction to generalize (and eventually automate) this process would be to track statistics over time about which parts of the cloud infrastructure are under the most pressure from attackers, including which tactics and techniques the attackers are using.
Through the shared, cross-team understanding of MITRE, it’s possible to correlate the threat data with CloudHealth Secure State findings for relevant Enterprise Cloud Matrix techniques. This mapping can provide value in at least two directions:
1) provide a natural roadmap or prioritization of cloud security areas of interest, and
2) reveal trends between attackers’ interest in your organization as a target and your cloud security posture, as measured by Secure State findings.
Using and operationalizing this approach could then provide insight into the “hot spots” of your cloud security posture that could use extra defensive resources.
Final thoughts
The addition of the MITRE ATT&CK Enterprise Cloud Matrix to the list of supported frameworks in CloudHealth Secure State benefits our customers in multiple ways. The shared understanding of the framework enables and empowers cross-team and cross-role collaboration and can help establish or augment data-driven processes for prioritization of cloud security effort, thus improving the efficiency and effectiveness of your investments.
To learn more about how CloudHealth Secure State helps global organizations improve their cloud security posture, we recommend you check out the following resources, or feel free to get in touch with our team directly. One of our cloud security experts would be happy to walk you through the platform and answer any questions you may have.

