- The best Mini ITX PC cases of 2025: Expert recommended
- From Copilot to agent - AI is growing up, and CISOs need to be ready
- My favorite Apple Watch for tracking my workouts is 32% off at major retailers
- Discover the Cisco Catalyst Center Fundamentals (CCFND) Training Program
- This robot vacuum's dustbin doubles as a handheld vacuum (and it's on sale)
TeamTNT cybercrime gang expands its arsenal to target thousands of orgs worldwide
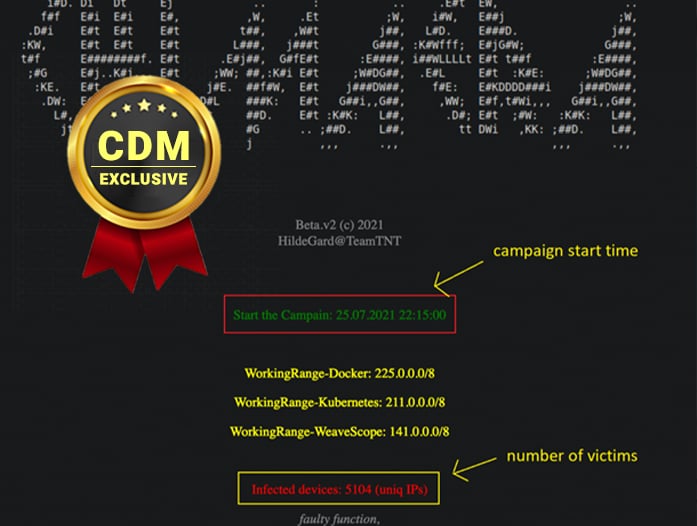
The financially motivated TeamTNT hacking group expanded its arsenal with new tools used to target thousands of victims worldwide.
Researchers from AT&T Alien Labs uncovered a new campaign, tracked as Chimaera, conducted by the TeamTNT group, aimed at organizations worldwide.
Evidence collected by the experts suggests that the campaign began on July 25, 2021, threat actors used a large set of open-source tools in the attacks. Threat actors leverage open-source tools to avoid detection and make hard the attribution of the attacks.
The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and that targets Docker installs. The activity of the TeamTNT group has been detailed by security firm Trend Micro, but in August 2020 experts from Cado Security discovered that that botnet is also able to target misconfigured Kubernetes installations.
In January 2021, the cybercrime gang launched a new campaign targeting Kubernetes environments with the Hildegard malware.
The Chimaera campaign is targeting multiple operating systems ( Windows, different Linux distributions including Alpine (used for containers), AWS, Docker, and Kubernetes) and applications, threat actors used a wide set of shell/batch scripts, new open-source tools, a cryptocurrency miner, the TeamTNT IRC bot, and more.
The campaign was very insidious and as of August 30, 2021, many malware samples used by the attacker still have zero detection rate from AV software. The campaign is responsible for thousands of infections globally in only a couple of months.
A partial list of the tools used by the group includes:
- Masscan and port scanner to search for new infection candidates
- libprocesshider for executing their bot directly from memory
- 7z to decompress downloaded files
- b374k shell which is a php web administrator that can be used to control infected systems
- Lazagne, an open-source tool for multiple web operating systems, which is used to collect stored credentials from numerous applications.
Researchers from Palo Alto Networks, that analyzed the same campaign, reported that the group is also using a cloud penetration testing toolset to target cloud-based apps that is named Peirates.
Experts pointed out that even if the group is expanding its arsenal adding new capabilities, it still focuses on cryptocurrency mining.
“AT&T Alien Labs has discovered new malicious files distributed by the threat actor TeamTNT. As researches have observed of TeamTNT in older campaigns, they are focusing on stealing cloud systems credentials, using infected systems for cryptocurrency mining, and abusing victim’s machines to search and spread to other vulnerable systems.” reads the analysis published by AT&T. “The use of open-source tools like Lazagne allows TeamTNT to stay below the radar for a while, making it more difficult for anti-virus companies to detect.”
Follow me on Twitter: @securityaffairs and Facebook
 Pierluigi Paganini
Pierluigi Paganini
International Editor-in-Chief
Cyber Defense Magazine

