- Google Gemini will let you schedule recurring tasks now, like ChatGPT - here's how
- iOS 26 isn't just about a rebrand and Solarium - here's what else is coming
- Energy Management in the AI Era: Cisco's Digital Transformation Advantage
- Hong Kong’s massive pension project grapples with technical glitches
- Foundation-sec-8b-reasoning: World's First Security Reasoning Model
Microsoft’s October 2021 Patch Tuesday Addresses 74 CVEs (CVE-2021-40449)

- 3Critical
- 70Important
- 0Moderate
- 1Low
Microsoft patched 74 CVEs in the October 2021 Patch Tuesday release, including three rated as critical, 70 rated as important and one rated as low. This is the eighth month in 2021 that Microsoft patched fewer than 100 CVEs.
This month’s update includes patches for:
- .NET Core & Visual Studio
- Active Directory Federation Services
- Console Window Host
- HTTP.sys
- Microsoft DWM Core Library
- Microsoft Dynamics
- Microsoft Dynamics 365 Sales
- Microsoft Edge (Chromium-based)
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Intune
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Windows Codecs Library
- Rich Text Edit Control
- Role: DNS Server
- Role: Windows Active Directory Server
- Role: Windows AD FS Server
- Role: Windows Hyper-V
- System Center
- Visual Studio
- Windows AppContainer
- Windows AppX Deployment Service
- Windows Bind Filter Driver
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows Desktop Bridge
- Windows DirectX
- Windows Event Tracing
- Windows exFAT File System
- Windows Fastfat Driver
- Windows Installer
- Windows Kernel
- Windows MSHTML Platform
- Windows Nearby Sharing
- Windows Network Address Translation (NAT)
- Windows Print Spooler Components
- Windows Remote Procedure Call Runtime
- Windows Storage Spaces Controller
- Windows TCP/IP
- Windows Text Shaping
- Windows Win32K
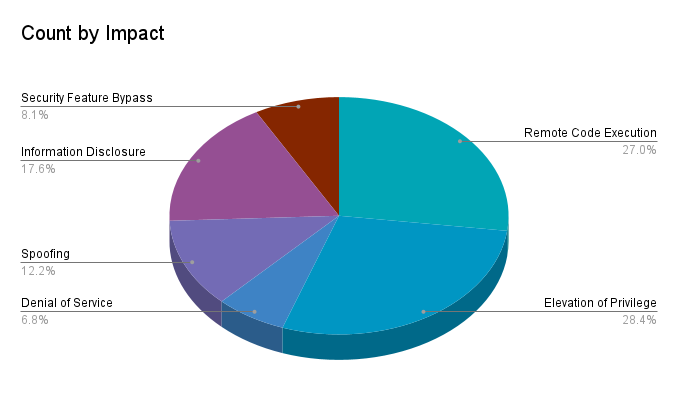
Elevation of privilege (EoP) vulnerabilities accounted for 28.4% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 27%.
CVE-2021-26427 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2021-40449 | Win32k Elevation of Privilege Vulnerability
CVE-2021-40449 is a use-after-free EoP vulnerability in Win32k. The flaw was discovered by researchers at Kaspersky in August and September, who observed it being exploited in the wild as a zero-day in attacks linked to a remote access trojan known as MysterySnail. According to the researchers, the vulnerability is a patch bypass for CVE-2016-3309, a separate EoP vulnerability in the Windows Kernel. EoP vulnerabilities, especially zero-days, are often linked to malware campaigns such as MysterySnail, and they are primarily associated with targeted attacks.
CVE-2021-36970 | Windows Print Spooler Spoofing Vulnerability
CVE-2021-36970 is a spoofing vulnerability in the Windows Print Spooler that received a CVSSv3 score of 8.8 and the designation of “Exploitation More Likely” according to Microsoft’s Exploitability Index. This vulnerability requires that an attacker have access to the same network as a target and user interaction. The advisory lists that a functional exploit does exist for this vulnerability so we may see a PoC circulating in the wild.
Disclosure of this vulnerability is credited to XueFeng Li and Zhiniang Peng of Sangfor who presented their prior work discovering CVE-2021-34527, the vulnerability that originally received the PrintNightmare title, in Windows Print Spooler at Black Hat USA in August. Given the adoption of prior Print Spooler vulnerabilities by attackers, we agree with Microsoft’s assessment that exploitation of this vulnerability is likely.
CVE-2021-40469 | Windows DNS Server Remote Code Execution Vulnerability
CVE-2021-40469 is an RCE vulnerability in Windows DNS Server. This vulnerability affects Windows server installs that have been configured as DNS servers. According to the advisory, this flaw was publicly disclosed, but it was categorized as “Exploitation Less Likely.” It received a CVSSv3 score of 7.2 because an attacker needs a privileged user account in order to exploit this across the network.
CVE-2021-41335 | Windows Kernel Elevation of Privilege Vulnerability
CVE-2021-41335 is an EoP vulnerability in the Windows Kernel which could be used by a low privileged, local attacker to elevate their privileges on an affected system. Microsoft assigned it a CVSSv3 score of 7.8 and rates this as “Exploitation Less Likely,” despite the vulnerability being publicly disclosed. EoP vulnerabilities like this are popular with malicious actors, helping them pivot from a low level user account to a privileged account with access to potentially sensitive data and the ability to execute arbitrary code.
Tenable Solutions
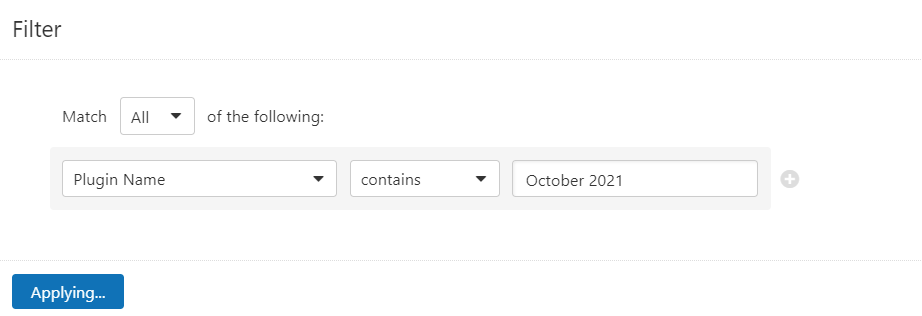
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains October 2021.
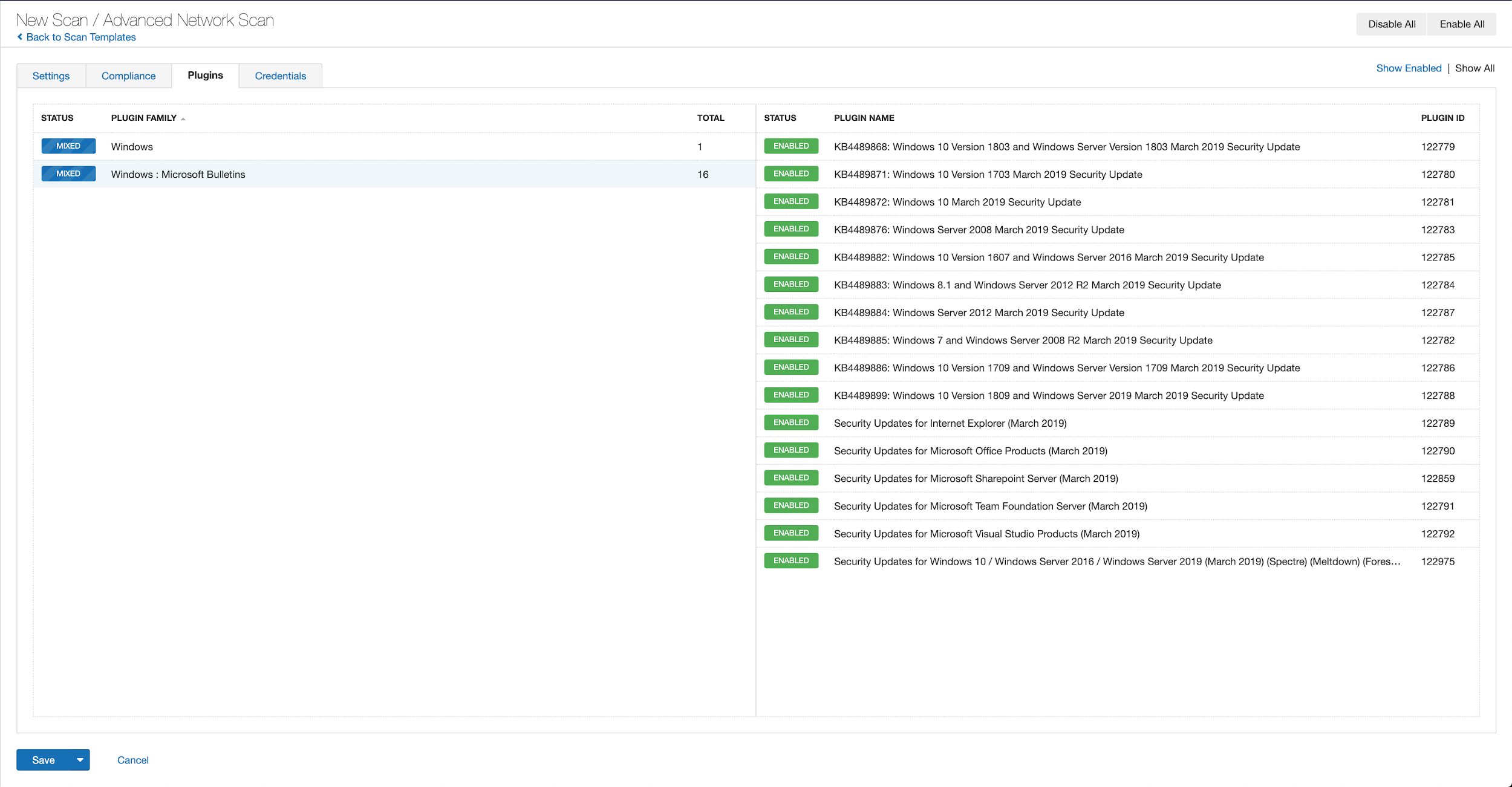
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s October 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.

