- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Top 5 DevOps Resource Center Articles of 2021
Cloud Native
We look back on the 5 most popular DevOps Resource Center articles in 2021 to help you build at your best in 2022.
Read time: ( words)
2021 Cloud Security Roundup
2021 was yet again an active year for security and development teams. And as Apache Log4Shell dominates the news, the need for effective, proactive cybersecurity continues to grow. Like ESPN’s Top 100 Plays of the Year, we decided to look back on our most popular topics in 2021 help you build securely (and quickly) in the new year.
How to use Rancher in Kubernetes
This popular blog walks you through deploying Rancher to manage your Kubernetes clusters. We also test out a helm-based deployment to create your very own private helm chart repo and integrate Trend Micro Cloud One™ – Container Security to scan images and files before they’re allowed in the cluster. Check out how to simplify container security with Rancher in Kubernetes.
5 Best Practices for Keeping Amazon S3 Buckets Secure
Fun fact: More than 3 trillion objects are stored in Amazon S3. It’s not a mystery as to why—it’s inexpensive and scalable, a dream come true. Although the product is secure, don’t forget your end of the Shared Responsibility Model; you are responsible for configuring the buckets and ensuring the objects being stored as secure. This blog runs you through 5 best practices to prevent breaches. Pro tip: they can all be automated with the right security platform.
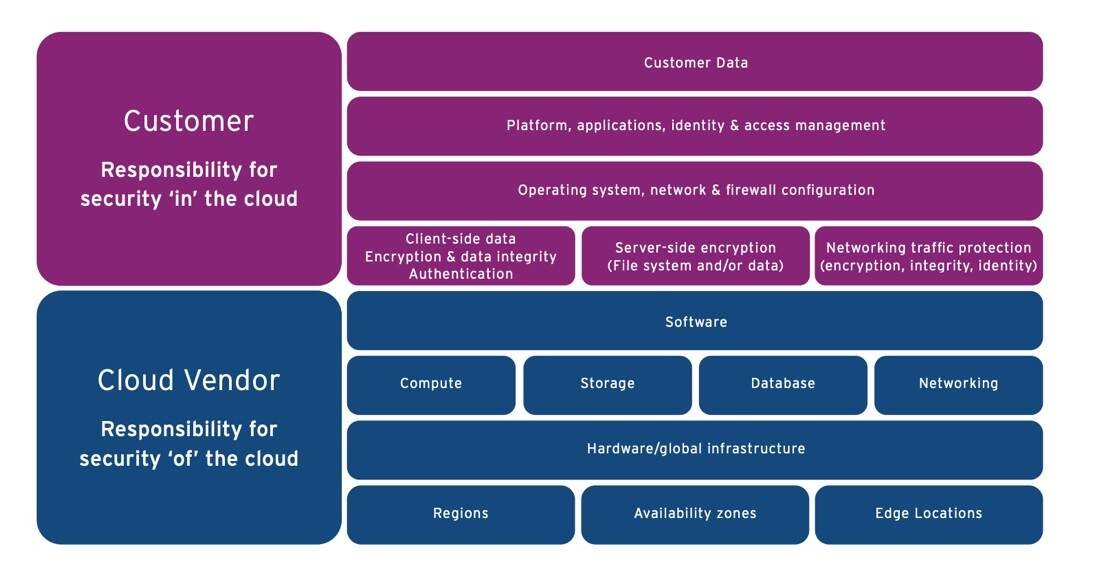
Securing your journey to the cloud continued to be a hot topic in 2021, as organizations struggled with navigating the challenges of securing a perimeter-less, multi-cloud environment. We discussed the main security benefits of undertaking cloud migration, and best practices for a secure move.
A Guide to the Well-Architected Framework
The Well-Architected Framework is the holy grail of designing and building a secure cloud environment. This series dives deep into the 5 pillars and examine the best practices and design principles to help you leverage the cloud in a more efficient, secure, and cost-effective manner. You can also explore related articles for more in-depth how-tos for each pillar.
12 Azure & AWS IAM Security Best Practices
Just like National Security Agency (NSA) doesn’t give out Gold Codes to anyone who asks, you shouldn’t grant access to your valuable resources without proper verification. Don’t forget to manage that access as well. Like the NSA changes its codes every day, make sure you revaluate access and dormant accounts that can be used to dump credentials. Explore our blog for all 12 best practices to keep your apps secure.
What’s next for 2022?
Cybersecurity continues to evolve, and it seems like every day there’s a new product, terminology, or tool popping up. Rest assured, having a strong grasp on the basics of cloud security is always critical. Here are some best practices to take into 2022:
- Leverage validated resources like AWS and Azure Well-Architected frameworks as well as common compliance guidelines like the NIST Cybersecurity Framework and the CIS Controls
- Automate as much as possible. Human error is the #1 cause of cloud misconfigurations (which are the #1 cause of data breaches). Use automation to streamline compliance and configuration checks as well as scanning for open source code flaws and malware in files and images
- Minimize the use of point-products to increase visibility. This helps security teams gatekeep your CI/CD pipelines so you can build quickly and securely. A platform with broad third-party integrations (no rip and replace) is a great way to enhance visibility and consolidate all those automated scans and checks we mentioned
Want more resources to help you prepare for 2022? Check out our 2022 cybersecurity predictions for DevSecOps blog.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk


