- This E Ink tablet that runs on Android is irreplaceable when I'm traveling
- Why the LG G4 OLED is one of my favorite TVs for picture quality - even in 2025
- Why the Oura Ring 4 is still the best smart ring on the market - and I've tested dozens of them
- Coffee with the Council Podcast: Passwords Versus Passkeys: A Discussion with the FIDO Alliance
- New WordPress Malware Masquerades as Plugin
Microsoft’s February 2022 Patch Tuesday Addresses 48 CVEs (CVE-2022-21989)

Microsoft addresses 48 CVEs in its February 2022 Patch Tuesday release, including one zero-day vulnerability that was publicly disclosed, but not exploited in the wild.
- 0Critical
- 48Important
- 0Moderate
- 0Low
Microsoft patched 48 CVEs in the February 2022 Patch Tuesday release, with all 48 rated as important and none rated as critical.
This month’s update includes patches for:
- Azure Data Explorer
- Kestrel Web Server
- Microsoft Dynamics
- Microsoft Dynamics GP
- Microsoft Edge (Chromium-based)
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft OneDrive
- Microsoft Teams
- Microsoft Windows Codecs Library
- Power BI
- Roaming Security Rights Management Services
- Role: DNS Server
- Role: Windows Hyper-V
- SQL Server
- Visual Studio Code
- Windows Common Log File System Driver
- Windows DWM Core Library
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows Named Pipe File System
- Windows Print Spooler Components
- Windows Remote Access Connection Manager
- Windows Remote Procedure Call Runtime
- Windows User Account Profile
- Windows Win32K
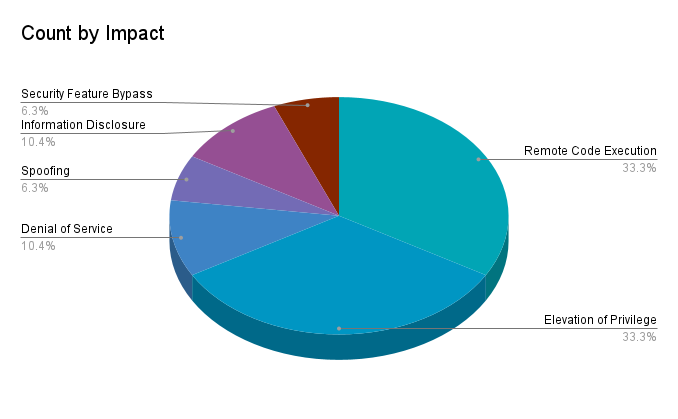
Remote code execution (RCE) vulnerabilities and elevation of privilege (EoP) both accounted for 33.3% of the vulnerabilities patched this month.
CVE-2022-21989 | Windows Kernel Elevation of Privilege Vulnerability
CVE-2022-21989 is an EoP vulnerability in the Windows Kernel and the only zero-day vulnerability addressed this month. According to Microsoft’s Exploitability Index rating, this vulnerability is more likely to be exploited, however it has not been actively exploited at the time this blog was published. The advisory does note that an attacker needs to take additional actions prior to exploitation of this vulnerability, which is evident by the “High” rating for “Attack Complexity” in the CVSSv3 score of 7.8.
CVE-2022-22005 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2022-22005 is a RCE vulnerability in Microsoft SharePoint Server with a CVSSv3 score of 8.8. Microsoft rates this as “exploitation more likely,” however at this time no public proof-of-concept appears to exist. In order to exploit this vulnerability, an attacker would need to be authenticated and have the ability to create pages in SharePoint.
CVE-2022-21999, CVE-2022-22718, CVE-2022-22717 and CVE-2022-21997 and | Windows Print Spooler Elevation of Privilege Vulnerability
CVE-2022-21999, CVE-2022-22718, CVE-2022-22717 and CVE-2022-21997 are EoP vulnerabilities in Windows Print Spooler. CVE-2022-21999 and CVE-2022-22718 received CVSSv3 scores of 7.8 and were rated Exploitation More Likely. CVE-2022-22717 (CVSSv3 7.0) and CVE-2022-21997 (CVSSv3 7.1) were rated Less Likely. Discovery of CVE-2022-21999 was credited to Xuefeng Li and Zhiniang Peng of Sangfor at the Tianfu Cup. These are the same researchers who disclosed CVE-2021-34527, kicking off the PrintNightmare saga in June 2021. CVE-2022-21997 was disclosed by Bo Wu and CVE-2022-22717 was credited to Thibault Van Geluwe de Berlaere with Mandiant. As researchers continue to focus their time on discovering flaws in Print Spooler, it is likely that attackers are as well, therefore organizations should apply these updates urgently.
CVE-2022-21996 | Win32k Elevation of Privilege Vulnerability
CVE-2022-21996 is an EoP vulnerability in Microsoft’s Win32k, a core kernel-side driver used in Windows. This vulnerability received a CVSSv3 score of 7.8 and is more likely to be exploited according to Microsoft. This vulnerability is similar to another EoP flaw from January’s Patch Tuesday release, CVE-2022-21882. CVE-2022-21882 has been actively exploited in the wild by threat actors and the Cybersecurity and Infrastructure Security Agency has added the vulnerability to it’s Known Exploited Vulnerabilities Catalog, requiring federal agencies to remediate the vulnerability by February 18. Interestingly enough, CVE-2022-21882 is a patch bypass for another vulnerability, CVE-2021-1732 according to RyeLv, one of the researchers credited with reporting the vulnerability to Microsoft.
CVE-2022-22715 | Named Pipe File System Elevation of Privilege Vulnerability
CVE-2022-22715 is an EoP vulnerability in the Named Pipe File System. It is rated as Exploitation More Likely. To exploit this flaw, an attacker would need to have established a presence on the vulnerable system in order to run a specially crafted application. Successful exploitation would allow an attacker to run processes with elevated privileges. The vulnerability is credited to researchers at Kunlun Lab, who participated in the Tianfu Cup, China’s biggest hacking competition.
Tenable Solutions
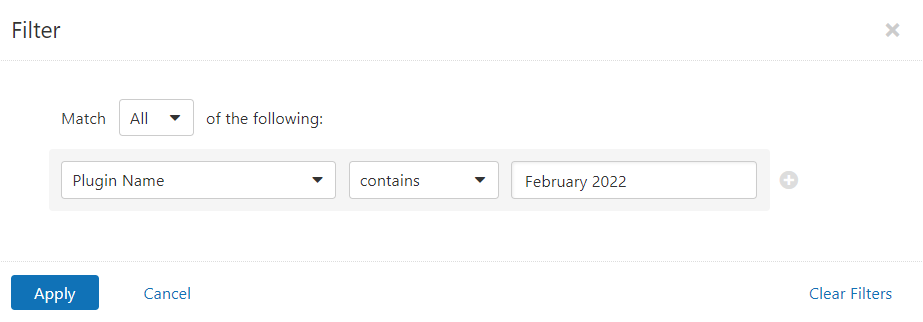
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains February 2022.
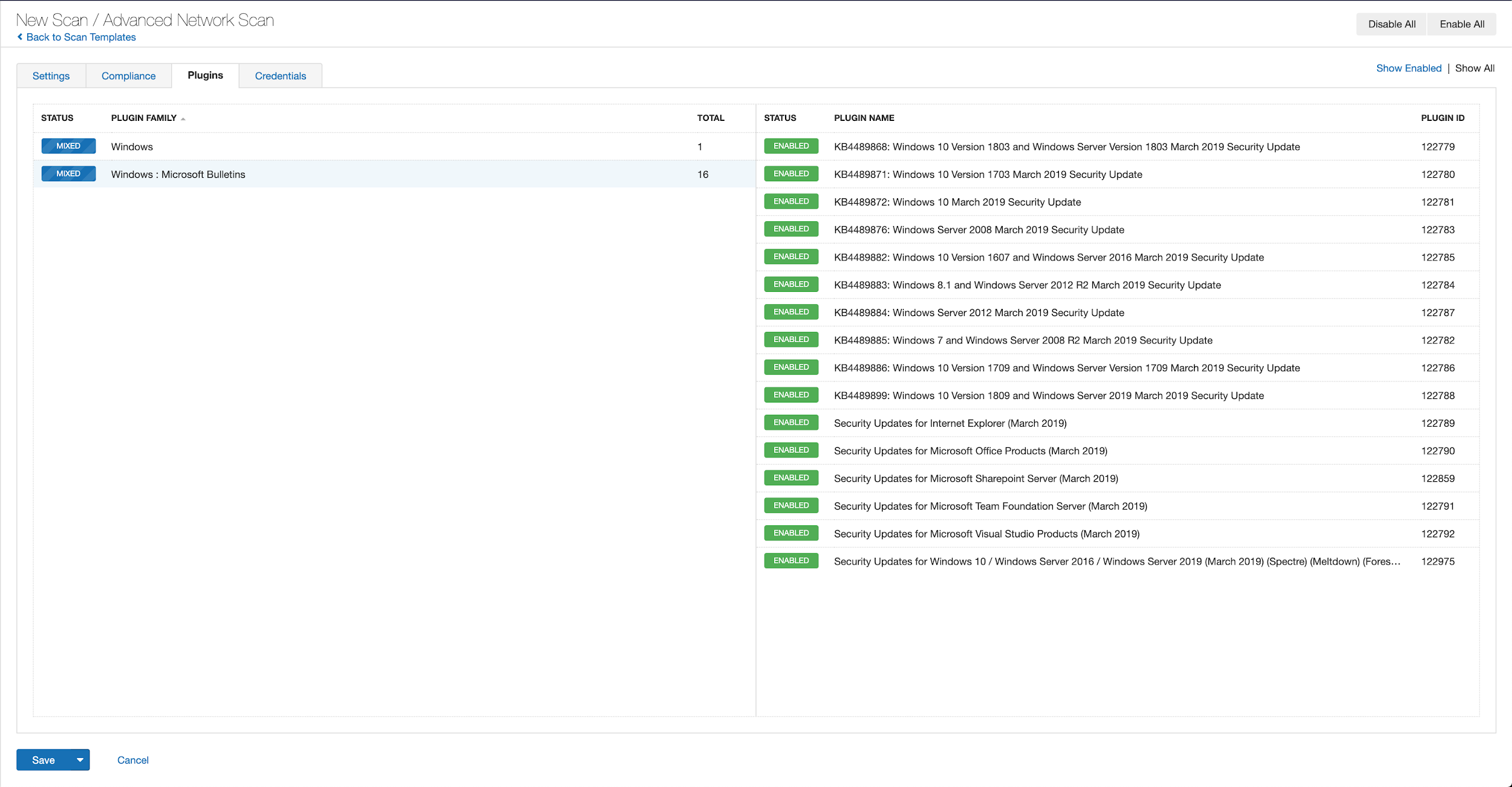
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s February 2022 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.

