- I replaced my $3,500 Sony camera with a 200MP Android phone - and can't go back
- 6 things I did immediately after installing iOS 18.5 on my iPhone - and why you should too
- My favorite 3-in-1 MagSafe charger for travel is smaller than a cookie (and it's on sale)
- 8 ways Google's Gemini AI assistant is getting more powerful and helpful
- Coffee with the Council Podcast: Introducing the New India-South Asia Regional Engagement Board
Biggest Cyber Trend in 2022

You Can’t Fix Stupid
By Guy Rosefelt, CPO, Sangfor Technologies
Stop me if you have heard this one: a customer is working late at night, has been a long day, and is very tired. The customer needs to clear a few remaining emails including one from the CEO. Without thinking about it, the customer opens the email from the CEO, barely skims it, and opens the attached Word document. Just as the Word doc opens, the customer realizes the email looks a bit odd and then it hits, it is a phishing email. Laptop infected.
Sound familiar? That just happened to my customer yesterday. And he knows better but was tired and on autopilot. We spent an hour online trying to figure out how bad the infection was and if he should wipe out his system and reimage since he had just done a full backup the week before. We decided to err on the side of caution and wipe and restore.
The moral of the story is anti-phishing will never be 100% successful. The best security products are only ninety-nine point something successful, but even at that rate with the number of emails received in an organization daily, a few are going to get through. And someone will click on one. My customer is normally very diligent, but he slipped. Worse, there are a few employees in every company that does not really check to see if emails are suspicious and will open them anyway.
Why am I rehashing this old trope? Because Barracuda Networks reported a 521% increase in phishing emails using the COVID-19 Omicron variant to entice victims between October 2021 and January 2022. People looking for home testing kits were prime targets and easy prey. Webroot reported a 440% increase in May 2021. And more will keep coming.
“So, Guy,” you may ask, “how can you save us from phishing?” Well, I cannot, and no one else can either. What we need to do is bite the bullet and shift our strategy from trying to block everything to assuming we are already compromised, breached, hacked, etc. Once you start from that viewpoint, it does not matter that you cannot fix stupid, you just have to deal with the aftermath. Your focus is now on threat hunting, looking for signs of compromise. Do you have tools that can watch low and slow network behavior that are indications of stealth scanning? Can you identify regular bursty encrypted traffic being sent someplace out on the internet that might be data being exfiltrated? Can you track system resource utilization for signs of crypto mining or other malicious behavior?
What makes looking for these kinds of behavior difficult is they are all AI-based. That’s right, attackers have learned to weaponize artificial intelligence (AI) into advanced persistent threats (APTs) and other malware payloads. The malicious software installed has become so much smarter than you think. It will look for specific targets, domains, even countries before it decides to activate. It can hide inside legitimate processes running in memory, evading security scans. In fact, it can disable security software running on systems without you knowing about it.
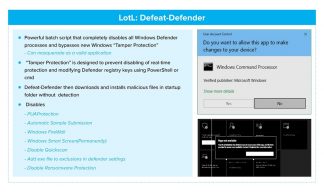
There is a powerful batch script available now called Defeat-Defender that can shut down all Windows Defender processes silently. The best part is Defeat-Defender can masquerade as a legitimate process, evading the new Windows Tamper Protection functionality. All from opening an infected Word document.
I see heads shaking in despair and a few of you getting ready to jump out of your office windows (you realize some of your work in the basement…). But there is a strategy that can help you through this dark and difficult time. You need to do 4 extremely simple and painless things:
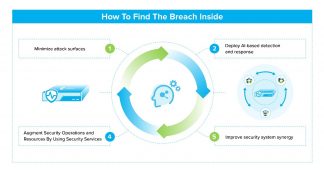
- Look for and minimize attack surfaces
Conduct external and internal attack surface assessments to find ways for the attacking malware to breach. Look for signs that those surfaces were exploited. Then work to close those holes.
- Deploy AI-based detection and response
You need to use AI to combat AI, but not just any AI. Security tools that employ broad-based AI will not find the signs of stealthy activity or APTs. Purpose-built AI models designed to identify very specific behaviors are needed, such as looking for enormous amounts of abnormal DNS requests going to malicious domains or finding short periods of bursty HTTPS traffic during off-hours; both are indications of data exfiltration.
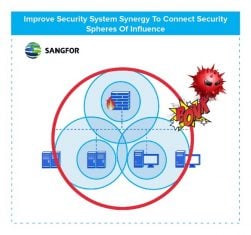
- Improve security system synergy
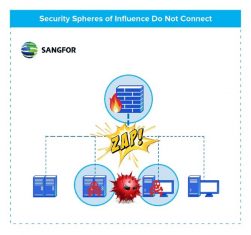
All security products have a sphere of influence covering their own security domain. But the domains do not overlap causing gaps that AI-enabled APTs can exploit. Having security products share data in real-time and coordinate responses can close those gaps.
- Augment security operations and resources by using security services
Face it, you do not have enough time, staff, or resources to go into threat hunting mode. And if you are breached and under attack, can you really do incident response (IR)? Even the security teams in the largest organizations are resource-limited. Leverage your VAR or security vendor to provide resources to backfill your team, help conduct assessments and IR, and do managed detection and response. Think of it as a home security monitoring service available 24 hours a day; that is there when the breach occurs during off-hours.
It isn’t possible to block everything 100% and combating stupid makes it even harder. Since you can’t fix stupid, these 4 things can minimize and contain the damage caused. More importantly, thinking like an attacker will help you find signs if you were attacked and close off any holes and vulnerabilities that attackers will use.
About the Author
 Guy Rosefelt, Chief Product Officer, Sangfor Technologies. Guy is Chief Product Officer for Sangfor Technologies. He has over 20 years of experience (though some say it is one year’s experience twenty times) in the application and network security, kicking it off with 10 years in the U.S. Air Force, reaching the rank of captain. After his time in the USAF building the first fiber to the desktop LAN and other things you would find in Tom Clancy novels, Guy worked at NGAF, SIEM, WAF, and CASB startups as well as big-name brands like Imperva and Citrix. He has spoken at numerous conferences around the world and in people’s living rooms, written articles about the coming Internet Apocalypse, and even managed to occasionally lead teams that designed and built security stuff. Guy is thrilled to be in his current position at Sangfor — partly because he was promised there would always be Coke Zero in the breakroom. His favorite cake is German Chocolate.
Guy Rosefelt, Chief Product Officer, Sangfor Technologies. Guy is Chief Product Officer for Sangfor Technologies. He has over 20 years of experience (though some say it is one year’s experience twenty times) in the application and network security, kicking it off with 10 years in the U.S. Air Force, reaching the rank of captain. After his time in the USAF building the first fiber to the desktop LAN and other things you would find in Tom Clancy novels, Guy worked at NGAF, SIEM, WAF, and CASB startups as well as big-name brands like Imperva and Citrix. He has spoken at numerous conferences around the world and in people’s living rooms, written articles about the coming Internet Apocalypse, and even managed to occasionally lead teams that designed and built security stuff. Guy is thrilled to be in his current position at Sangfor — partly because he was promised there would always be Coke Zero in the breakroom. His favorite cake is German Chocolate.
Guy can be reached online at guy.rosefelt@sangfor.com or on Twitter at @otto38dd and at our company website https://www.sangfor.com/en .
FAIR USE NOTICE: Under the “fair use” act, another author may make limited use of the original author’s work without asking permission. Pursuant to 17 U.S. Code § 107, certain uses of copyrighted material “for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.” As a matter of policy, fair use is based on the belief that the public is entitled to freely use portions of copyrighted materials for purposes of commentary and criticism. The fair use privilege is perhaps the most significant limitation on a copyright owner’s exclusive rights. Cyber Defense Media Group is a news reporting company, reporting cyber news, events, information and much more at no charge at our website Cyber Defense Magazine. All images and reporting are done exclusively under the Fair Use of the US copyright act.

