- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Detecting Exploitation of Local Vulnerabilities Through Trend Micro Vision One and Cloud One

Exploits & Vulnerabilities
We provide a guide to detecting Dirty Pipe, a Linux kernel vulnerability tracked as CVE-2022-0847.
Read time: ( words)
This blog provides threat analysts a guide to detecting an arbitrary file overwrite vulnerability in Linux Kernel, also known as Dirty Pipe. Dirty Pipe is a local privilege escalation vulnerability that is tracked as CVE-2022-0847. It has a CVSS score of 7.8 and was discovered by IONOS software developer Max Kellermann.
This vulnerability exists in Linux kernel and exploits the flaw in Linux Kernel memory management in the way pipe page caches are merged and overwrites other page caches. The vulnerability is easy to exploit and allows a low-privileged user to escalate to root privilege on the host. There have also been various public proof-of-concept exploits.
Attackers can abuse this flaw to write to pages in the page cache of read-only files. They can also execute their code to escalate their privileges on the system.
The following sections outline how to detect the abuse of this vulnerability using Trend Micro Vision One™ and Trend Micro Cloud One™.
Trend Micro Cloud One™ – Workload Security
Modules
1. Log Inspection
Through this module, we can tap into the authentication-related events on the host.
Upon the execution of the proof of concept, we can deduce suspicious activity based on observations on “/var/log/auth.log”. Successful exploitation can create the following system logs that can be used for detection. It should be noted, however, there are also cases where the exploitation of this vulnerability does not leave any trace in the logs.
2. Antimalware
This module detects the exploitation of this vulnerability in real-time using behavior monitoring.
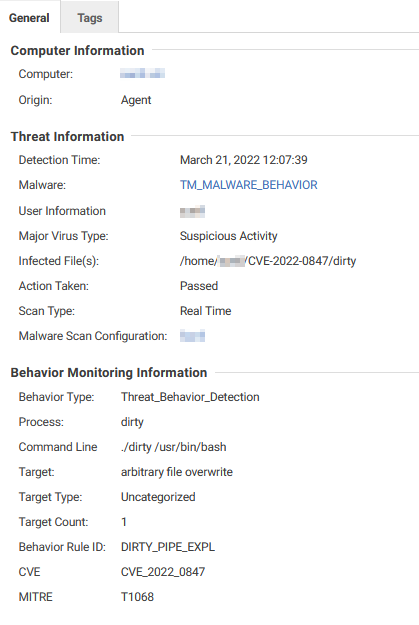
3. Activity monitoring
The module can detect process, file, and network activities on endpoints running Workload Security. In this case, we will examine the file activity since there is no network component to this attack scenario.
Trend Micro Vision One
Workload Security’s correlation of telemetry and detections provides an initial security context that allows security teams to track and monitor the threats that might abuse CVE-2022-0847. In the next section, Trend Micro Vision One provides more information on the paths and events that occur in real time.
Observed Attack Techniques (OATs)
OATs are generated from individual events that provide security value. To investigate the possible exploitation attempts using this vulnerability, analysts can look for these OAT IDs from many other helper OAT triggers that indicate suspicious activities on the affected host.
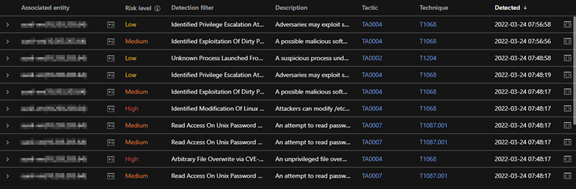
The following OAT IDs can be used while threat hunting:
- F5005: Identified Privilege Escalation AttemptF011: Identified Modification of Linux Passwd File
- F5025: Identified Exploitation of Dirty Pipe Vulnerability
- F2745: Unknown Process Launched From TMP Directory
- F5012: Arbitrary File Overwrite via CVE-2022-0847
Trend Micro Vision One Workbench app
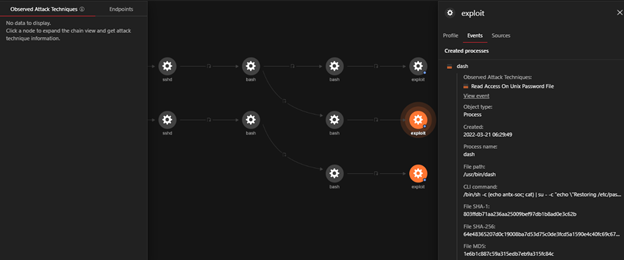
The Trend Micro Vision One Workbench app helps analysts see significant correlated events intelligently based on occurrences throughout the entire fleet of workloads. The left side of the diagram shows the summarized sequence of events happening one after another. Analysts can view the different fields of interest that are considered important and provide security value on the right. The app allows security teams to see the compromised assets and isolate those that can be potentially affected while patching procedures are ongoing.
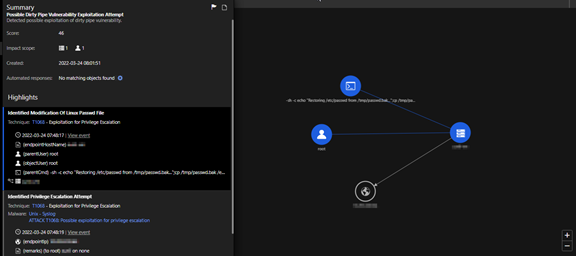
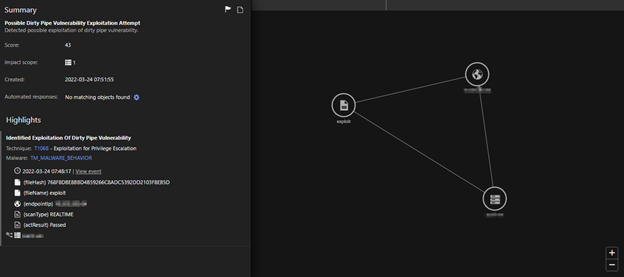
Root cause analysis
“Execution Profile” is a feature in Vision One that generates graphs for defenders. We can expand for fields like “processCmd” and “objectCmd” from the search app or the threat-hunting app to look for different activities being observed in a given period; such activities are process creation, file creation, and inbound and outbound network activity, among others. The following operations can be observed when this vulnerability is being exploited.
a. “/etc/passwd” file overwrite
Conclusion
Security teams that seek to prevent threat actors from exploiting the Dirty Pipe vulnerability must note the following points:
- Incident responders can search for the following string in the “/var/log/auth.log”: “(to root) <user> on none”. Any user in the system will be able to detect possible exploitation.
- Malicious actors that have established a foothold in an enterprise’s system through cryptomining, malware infection, or cyberespionage can exploit this vulnerability as their means of intrusion enables access to root privileges.
- There are many ways to exploit this vulnerability without leaving a trace in the auth.log. We advise security teams to apply the necessary patches as soon as possible, and to enable all applicable solutions for detecting and blocking abuse.
Security solutions that provide comprehensive protection for your system can keep this and other threats at bay:
Trend Micro Vision One helps security teams gain an overall view of attempts in ongoing campaigns by providing them a correlated view of multiple layers such as email, endpoints, servers, and cloud workloads. Security teams can gain a broader perspective and a better understanding of attack attempts and detect suspicious behavior that would otherwise seem benign when viewed from a single layer alone..
Trend Micro Cloud One – Workload Security helps defend systems against vulnerability exploits, malware, and unauthorized change. It can protect a variety of environments such as virtual, physical, cloud, and containers. Using advanced techniques like machine learning (ML) and virtual patching, the solution can automatically secure new and existing workloads both against known and new threats.
MITRE ATT&CK
| Technique | ID |
| Exploitation for Privilege Escalation | T1068 |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

