- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
New Bumblebee malware replaces Conti’s BazarLoader in cyberattacks

A newly discovered malware loader called Bumblebee is likely the latest development of the Conti syndicate, designed to replace the BazarLoader backdoor used to deliver ransomware payloads.
The emergence of Bumblebee in phishing campaigns in March coincides with a drop in using BazarLoader for delivering file-encrypting malware, researchers say.
BazarLoader is the work of the TrickBot botnet developers, who provided access to victim networks for ransomware attacks. The TrickBot gang is now working for the Conti syndicate.
In a report in March on a threat actor tracked as ‘Exotic Lily’ that provided initial access for Conti and Diavol ransomware operations, Google’s Threat Analysis Group says that the actor started to drop Bumblebee, instead of the regular BazarLoader malware, to deliver Cobalt Strike.
Bumblebee delivery methods
Eli Salem, lead threat hunter and malware reverse engineer at Cybereason says that the deployment techniques for Bumblebee are the same as for BazarLoader and IcedID, both seen in the past deploying Conti ransomware.
Proofpoint confirms Salem’s finding, saying that they’ve observed phishing campaigns where “Bumblebee [was] used by multiple crimeware threat actors previously observed delivering BazaLoader and IcedID.”
“Threat actors using Bumblebee are associated with malware payloads that have been linked to follow-on ransomware campaigns” – Proofpoint
The company also notes that “several threat actors that typically use BazaLoader in malware campaigns have transitioned to Bumblebee” to drop shellcode and the Cobalt Strike, Sliver, and Meterpreter frameworks designed for red team security assessment.
At the same time, BazaLoader has been missing from Proofpoint’s data since February.
In a report today, Proofpoint says that it observed multiple email campaigns distributing Bumblebee within ISO attachments that contained shortcut and DLL files.
One campaign leveraged a DocuSign document lure that led to a ZIP archive with a malicious ISO container hosted on Microsoft’s OneDrive cloud storage service.
The researchers say that the malicious email also included an HTML attachment that appeared as an email to an unpaid invoice, Proofpoint says.
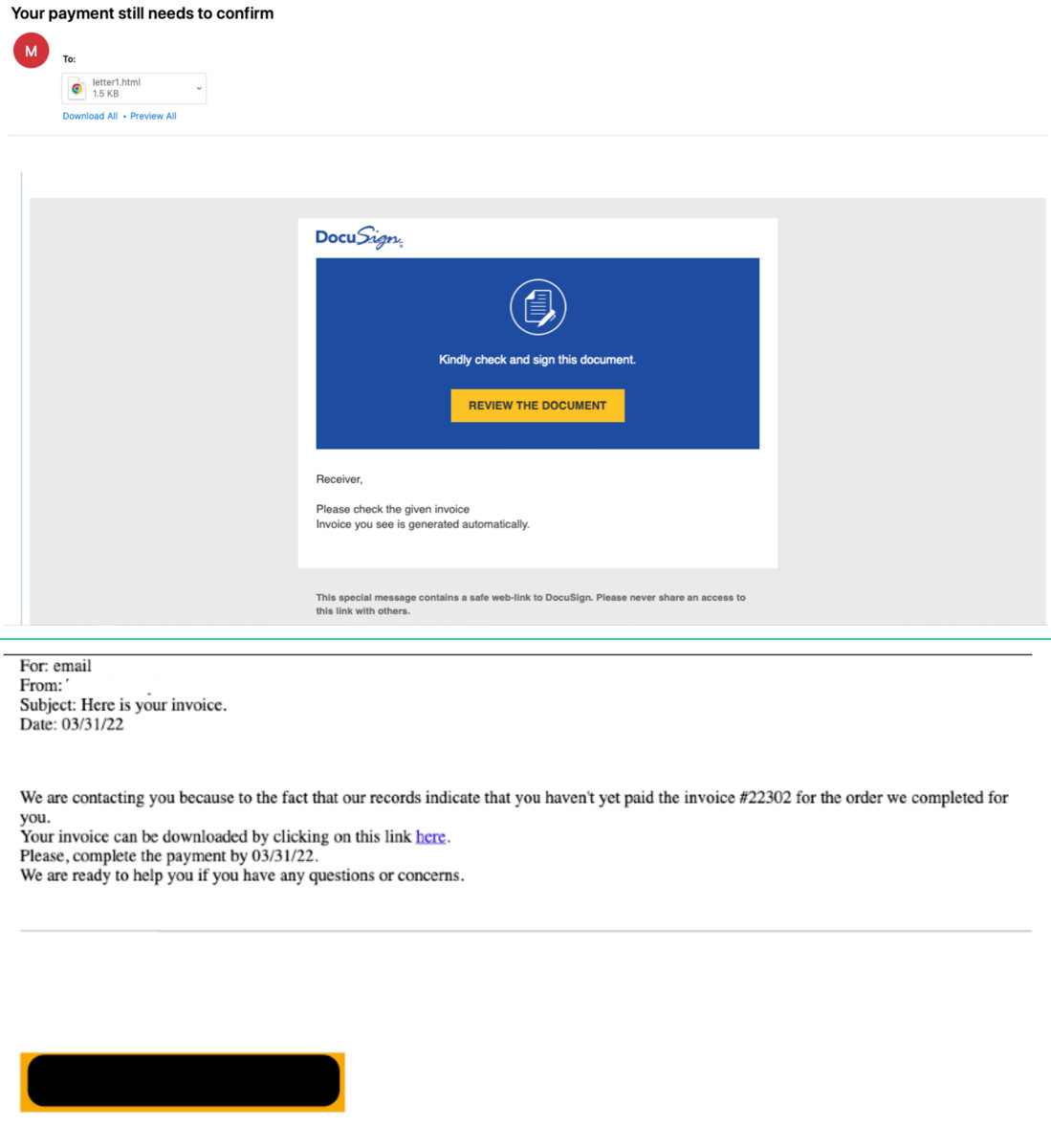
The URL embedded in the HTML file used a redirect service that relies on the Prometheus TDS (traffic distribution service) that filters downloads based on the victim’s timezone and cookies. The final destination was also the malicious ISO hosted on OneDrive.
Proofpoint researchers attributed this campaign with high confidence to the cybercriminal group TA579. Proofpoint has tracked TA579 since August 2021. This actor frequently delivered BazaLoader and IcedID in past campaigns
In March, Proofpoint observed a campaign that delivered Bumblebee through contact forms on a target’s website. The messages claimed that the website used stolen images and included a link that ultimately delivered an ISO file containing the malware.
Proofpoint attributes this campaign to another threat actor that the company tracks as TA578 since May 2020 and uses email campaigns to deliver malware like Ursnif, IcedID, KPOT Stealer, Buer Loader, and BazaLoader, as well as Cobalt Strike.
The researchers detected another campaign in April that hijacked email threads to deliver the Bumblebee malware loader in replies to the target with an archived ISO attachment.
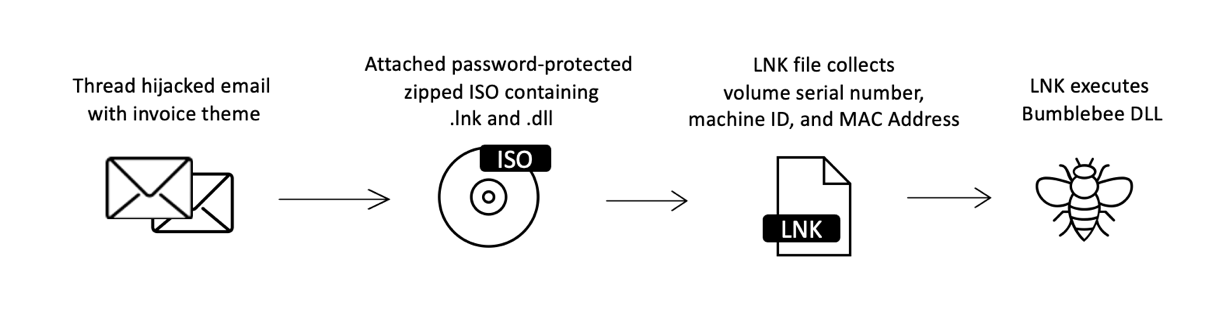
Although it has not found undeniable evidence, Proofpoint believes that the threat actors deploying Bumblebee are initial network access brokers working with ransomware actors.
Highly-complex malware
Researchers agree that Bumblebee is a “new, highly sophisticated malware loader” that integrates intricate elaborate evasion techniques and anti-analysis tricks that include complex anti-virtualization methods.
In a technical analysis on Thursday, Eli Salem shows that Bumblebee’s authors used the entire anti-analysis code from the publicly available al-khaser PoC ‘malware’ application.
Salem’s code examination revealed that the malware searches for multiple tools for dynamic and static analysis, it tries to detect “any kind of virtualization environment” by looking for their processes, and by checking registry keys and file paths.
The researcher notes that one of the most interesting things he found in Bumblebee’s core loader component is the presence of two 32/64-bit DLL files called RapportGP.dll, a name used by the Trusteer’s Rapport security software for protecting sensitive data like credentials.
In its separate technical analysis, Proofpoint found that the Bumblebee loader supports the following commands:
- Shi: shellcode injection
- Dij: DLL injection in the memory of other processes
- Dex: Download executable
- Sdl: uninstall loader
- Ins: enable persistence via a scheduled task for a Visual Basic Script that loads Bumblebee
Bumblebee uses TrickBot code
Malware researchers at cybersecurity companies Proofpoint and Cybereason analyzed Bumblebee and noticed similarities with the TrickBot malware in code, delivery methods, and dropped payloads.
Salem established a connection between Bumblebee to TrickBot after seeing that both malware pieces rely on the same installation mechanism for the hooks.
The similarities go even further, as Bumblebee uses the same evasion technique for RapportGP.DLL as TrickBot for its web-inject module.
Additionally, both malware pieces try to use the LoadLibrary and get the address of the function they want to hook, the researcher found.
Salem says that while there isn’t sufficient evidence to say that Bumblebee and TrickBot have the same author it is plausible to assume that Bumblebee’s developer has the source code for TrickBot’s web-inject module.
Rapid malware development
Bumblebee is actively developed, gaining new capabilities with each update. The most recent one Proofpoint observed is from April 19 and it supports multiple command and control (C2) servers.
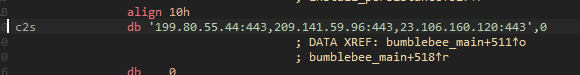
However, Proofpoint says that the most significant development is the addition of an encryption layer via the RC4 stream cipher for network communications, which uses a hardcoded key to encrypt requests and decrypt responses from the C2.
Another modification appeared on April 22 when researchers noticed that Bumblebee integrated a thread that checks for common tools used by malware analysts against a hardcoded list.
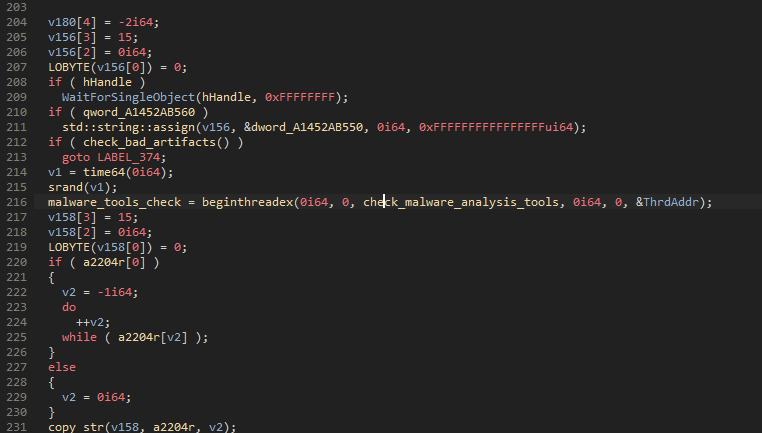
Proofpoint believes that Bumblebee is a multifunctional tool that can be used for initial access to victim networks to later deploy other payloads such as ransomware.
Sherrod DeGrippo, Vice President of Threat Research and Detection at Proofpoint, says that “the malware is quite sophisticated, and demonstrates being in ongoing, active development introducing new methods of evading detection.”
The reports [1, 2] from Cybereason’s Eli Salem and Proofpoint came one day apart and include a detailed technical analysis of Bumblebee malware’s most significant aspects.

