- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
US Agencies and FireEye were hacked with a supply chain attack on SolarWinds Software – Cyber Defense Magazine

Hackers broke into the networks of federal agencies and FireEye by compromising SolarWinds’ Orion Network Management Products.
The cyber espionage group has tampered with updates released by IT company SolarWinds, which provides its products to government agencies, military, and intelligence offices, two people familiar with the matter told the Reuters agency.
Nation-state actors, allegedly Russia-linked hacked, have compromised the networks of several US government agencies, including the US Treasury, the Commerce Department’s National Telecommunications and Information Administration (NTIA). The hack allowed the threat actors to spy on the internal email traffic.
“Hackers believed to be working for Russia have been monitoring internal email traffic at the U.S. Treasury and Commerce departments, according to people familiar with the matter, adding they feared the hacks uncovered so far may be the tip of the iceberg.” reported the Reuters.
A report published by the Washington Post, citing unnamed sources, attributes the attacks to APT29 or Cozy Bear, the Russia-linked APT that’s believed to have recently compromised the top cybersecurity firm FireEye.
The Cybersecurity and Infrastructure Security Agency (CISA) immediately issued Emergency Directive 21-01, in response to the compromise involving SolarWinds Orion products that are currently being exploited by malicious threat actors. The US agency is calling on all federal civilian agencies to review their networks for indicators of compromise power down SolarWinds Orion products immediately.
“The compromise of SolarWinds’ Orion Network Management Products poses unacceptable risks to the security of federal networks,” said Brandon Wales, acting director of the US Cybersecurity and Infrastructure Security Agency (CISA), which has released an emergency directive, urging federal civilian agencies to review their networks for suspicious activity and disconnect or power down SolarWinds Orion products immediately.
At the time of this writing, it is still unclear the extent of the hack, but the situation could be dramatic due to the popularity of SolarWinds’ networking and security products. Threat actors carried out a highly-sophisticated supply chain attack.
SolarWinds’ networking and security products are currently used by more than 300,000 customers worldwide, including government agencies, military offices, major US telecommunications companies, education institutions, and Fortune 500 companies.
The Pentagon, State Department, NASA, National Security Agency (NSA), Postal Service, NOAA, Department of Justice, and the Office of the President of the United States use SolarWinds solutions.
FireEye is investigating the supply chain attack, it already confirmed that a threat actor tracked as UNC2452 had used a trojanized SolarWinds Orion business software updates to distribute a backdoor tracked as SUNBURST.
According to the experts, the campaign may have begun as early as Spring 2020 and is still ongoing.
The attacks are the work of a highly-skilled threat actor and the operation was conducted with significant operational security, FireEye explained.
“SolarWinds.Orion.Core.BusinessLayer.dll is a SolarWinds digitally-signed component of the Orion software framework that contains a backdoor that communicates via HTTP to third party servers. We are tracking the trojanized version of this SolarWinds Orion plug-in as SUNBURST.” reads the analysis published by FireEye.
“After an initial dormant period of up to two weeks, it retrieves and executes commands, called “Jobs”, that include the ability to transfer files, execute files, profile the system, reboot the machine, and disable system services. The malware masquerades its network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files allowing it to blend in with legitimate SolarWinds activity. The backdoor uses multiple obfuscated blocklists to identify forensic and anti-virus tools running as processes, services, and drivers.”
FireEye published the indicators of compromise (IoCs) and attack signatures for SUNBURST here.
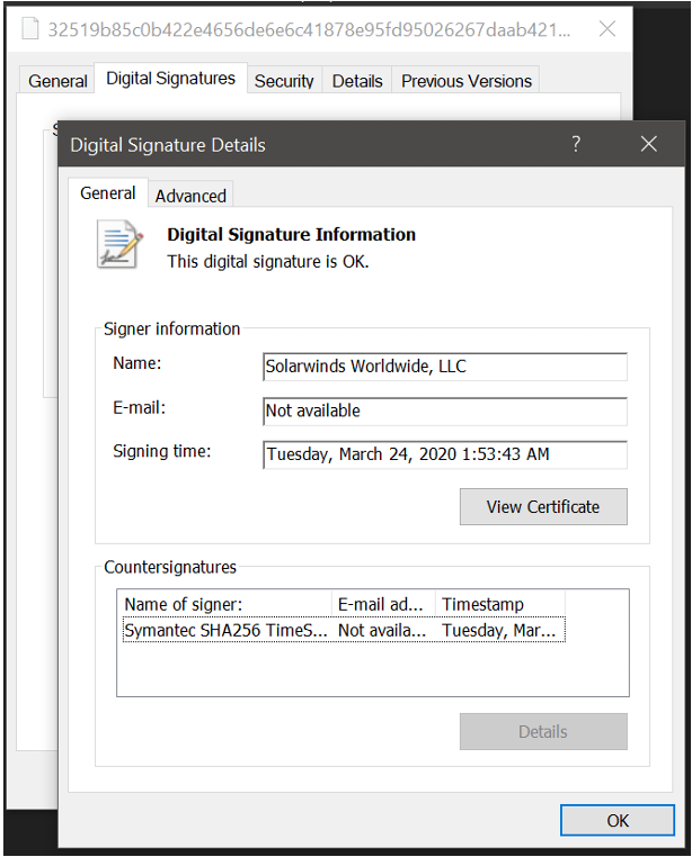
FireEye discovered multiple weaponized updates that were digitally signed between March and May 2020 and posted to the SolarWinds updates website.
The tainted version of SolarWinds Orion plug-in masqueraded network traffic as the Orion Improvement Program (OIP) protocol, it communicates via HTTP to C2 to retrieve and execute malicious commands, dubbed “Jobs.” The backdoor supports multiple features, including file transferring, executing files, disabling system services, and gathering system info.
The attackers used VPN servers in the same country as the victim to obfuscate the IP addresses and evade detection.
Microsoft also carried out its separate analysis and confirmed that the hackers mounted a supply chain attack on SolarWinds, the experts tracked the backdoor as”Solorigate,”
In a security advisory published by SolarWinds, the company confirmed the supply chain attack, the threat actors compromised versions 2019.4 through 2020.2.1 of the SolarWinds Orion Platform software that was released between March and June 2020. The vendor recommendss users to upgrade to Orion Platform release 2020.2.1 HF 1 immediately.
SolarWinds reported the security breach to the authorities and is still investigating the attack with the support of FireEye and the FBI. The company will release the 2020.2.1 HF 2 update on December 15 to replace the compromised component and implements security enhancements.