- I ditched my daily driver Bose headphones for the XM6 - and I'm hesitant to go back
- This Lenovo ThinkPad is my top pick for remote work - and it's nearly 50% off now
- I invested in this 3-in-1 robot vacuum, and it's paying off for my home
- I've tested the Meta Ray-Bans for months, and these 5 features still amaze me
- My new favorite iPhone portable charger has a magnetic superpower - and it's cheap
Qbot malware now uses Windows MSDT zero-day in phishing attacks

A critical Windows zero-day vulnerability, known as Follina and still waiting for an official fix from Microsoft, is now being actively exploited in ongoing phishing attacks to infect recipients with Qbot malware.
Proofpoint first reported Monday that the same zero-day was used in phishing targeting US and EU government agencies.
Last week, the enterprise security firm also revealed that the Chinese TA413 hacking group is exploiting the bug in attacks targeting the Tibetan diaspora.
As Proofpoint security researchers shared today, the TA570 Qbot affiliate has now begun using malicious Microsoft Office .docx documents to abuse the Follina CVE-2022-30190 security flaw and infect recipients with Qbot.
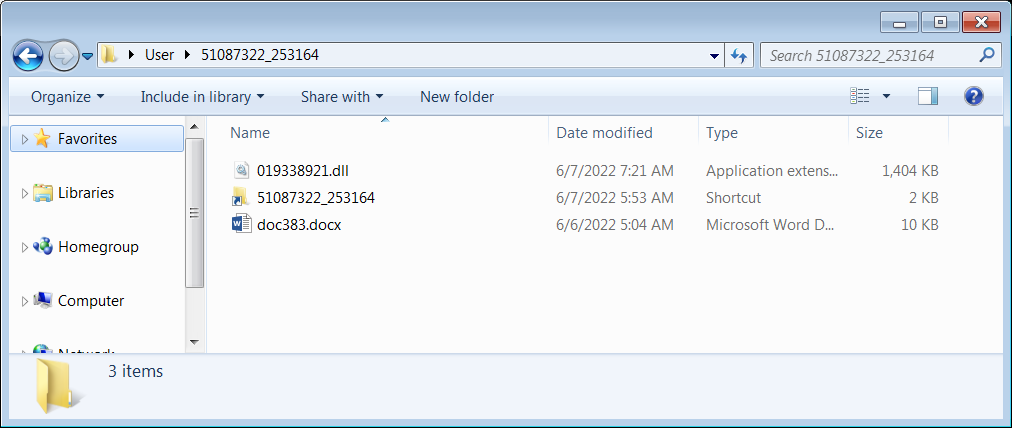
The attackers use hijacked email thread messages with HTML attachments which will download ZIP archives containing IMG files. Inside the IMG, the targets will find DLL, Word, and shortcut files.
While the shortcut file directly loads the Qbot DLL file already present in the IMG disk image, the blank .docx document will reach out to an external server to load an HTML file that exploits the Follina flaw to run PowerShell code which downloads and executes a different Qbot DLL payload.
A collection of indicators of compromise linked to this campaign by malware analyst ExecuteMalware can be found here.
The tactics used in this phishing campaign match previous reports describing how the TA570 has previously used email thread hijacking to push malicious attachments.
TA570’s decision to use two different methods to infect potential victims hints at the cybercrime threat actor likely running an A/B testing campaign to assess which tactic would get them the best results for their “efforts.”
This is one of the few times Qbot affiliates have tried to switch their attack methods this year, first turning to an older trick known as Squiblydoo in February to spread the malware via Microsoft Office documents using regsvr32.exe.
In April, after Microsoft started rolling out a VBA macro autoblock feature to Office for Windows users, the threat actors stopped using Microsoft Office docs with malicious macros and switched to password-protected ZIP archive attachments with malicious MSI Windows Installer packages.
Proofpoint saw #TA570 exploiting CVE-2022-30190 to deliver #Qbot malware. Actor uses thread hijacked messages with HTML attachments which, if opened, drop a zip archive.
— Threat Insight (@threatinsight) June 7, 2022
What is Qbot?
Qbot (aka Qakbot, Quakbot, and Pinkslipbot) is a modular Windows banking trojan with worming capabilities for infecting more devices on compromised networks via network share exploits and highly aggressive brute-force attacks against Active Directory admin accounts.
This information stealer malware has been used since at least 2007 to harvest banking credentials, personal info, and financial data, as well as to backdoor compromised computers and deploy Cobalt Strike beacons.
Ransomware affiliates linked to multiple Ransomware as a Service (RaaS) operations (including REvil, PwndLocker, Egregor, ProLock, and MegaCortex) have also used Qbot for initial access into corporate networks.
Microsoft has published a report in December 2021 regarding the versatility of Qbot attacks that makes it harder to accurately evaluate the scope of its infections.
The DFIR Report also recently shed light on Qbot light-speed attacks where the malware is able to steal sensitive user data (including Windows credentials and emails) within roughly 30 minutes after the initial infection.

