- Intel appears stuck between ‘a rock and a hard place’
- “언론은 몰려오고, 내부는 혼돈에 빠지고”···CISO가 직접 겪고 깨달은 보안 사고 교훈 8가지
- AI의 상상과 실사 영화의 콜라보···구글, 단편 영화 앤세스트라 제작 과정 공개
- Select Prime members can get Kindle Unlimited for 3 months at no cost - here's how
- Modernization means putting developers in the driver’s seat
Threat Intelligence: Cyber and Electromagnetic Activities (CEMA) with Software-Defined Radio (SDR)

By Brendon McHugh, FAE & Technical Writer, Per Vices
Under the umbrella term Cyber and Electromagnetic Activities (CEMA), a number of military operations must be synchronized and coordinated. This includes cyberspace offensive and defensive operations, electronic warfare (EW) attacks, EW protection, and EW support, as well as spectrum monitoring and management operation. To maintain strategic advantages and ensure mission success, multi-operational domains in space, air, land, and maritime all need to be coordinated. Adversaries continue to seek new opportunities to exploit the domains of the cyber and the electromagnetic spectrum and the associated infrastructure, particularly as there is a proliferation of embedded electronics on the battlefield.
In this article, we first discuss CEMA and explain the inner workings of the organization’s various operations and objectives, as well as challenges often encountered. Following this, we discuss how software-defined radio (SDR) is paramount to the present and future CEMA operations, as they are able to assist with various cyberspace, EW, and spectrum monitoring capabilities and solve many of the challenges outlined.
Fundamentals of Cyber and Electromagnetic Activities (CEMA)
Broadly speaking, CEMA consists of cyberspace operations (CO), electronic warfare (EW), and spectrum management operations (SMO), as shown in Figure 1 below. CEMA operations are used by military forces to seize, preserve, and exploit dominance over hostile adversaries in both cyberspace and the electromagnetic spectrum (EMS). Along with this, CEMA is used for denying and degrading adversary use of their own CEMA capabilities and thereby protecting the CEMA organization and related systems.
Figure 1: CEMA operations (adopted from https://irp.fas.org/doddir/army/fm3-38.pdf)
The key to the entire CEMA operation is integration and synchronization. Integration is the arrangement of various military forces and their respective capabilities in order to create a force that operates by engaging as a whole– that is integration of space, maritime, land, and air forces. Just as important is synchronization. This consists of the arrangement of military actions in time, space, and purpose to produce maximum combat capability and power at a decisive place and time.
The purpose of CEMA is to provide military forces with capabilities to increase spectrum awareness, situational awareness, and overall survivability. Examples of enhanced capabilities by EW include the use of expendables such as flares (i.e. redirecting heat-seeking missiles), electronic countermeasures against radio-controlled improvised explosive devices (IEDs), and jamming to disable an enemy’s equipment or capability. On the other hand, SMO can be used for mitigating electromagnetic interference in systems from the friendly use of EW. Lastly, CO ensures the secure and uninterrupted flow of data and information that allows military forces to respond rapidly to a changing battlefield and synchronize with other joint capabilities.
Cyberspace Operations and Challenges
Cyberspace is a worldwide information environment consisting of interdependent networks of information technology (IT) infrastructures and local data/traffic users, including the Internet, telecommunications networks, computer systems, and embedded processors and controllers– both wireless and wired. High-performance software-defined radios (SDR) also fall into this category, which is essentially a device that incorporates all the preceding technologies in one box.
Within CEMA, cyberspace operations (CO) consist of three functions: offensive cyberspace operations (OCO), defensive cyberspace operations (DCO), and Department of Defence (DoD) information network operations (DODIN). Important for OCO operations is conducting cyberspace attacks. These consist of actions that create various direct denial effects in cyberspace (for example, degradation, disruption, or destruction) and manipulation that leads to denial of service that is hidden or that manifests in the physical domain of a network.
Unique to cyberspace is how interrelated it is to the space domain, primarily because of how satellites play a critical role in military telecommunications and networks, particularly for the vast number of PNT (position, navigation, and timing) requirements. Moreover, the relationship between cyberspace and the space domain (i.e. military-band satellite communications) activities within the electronic magnetic spectrum (EMS) greatly expands and complicates the operational framework, recasting a concentrated physical battlefield into a global battlefield. For example, computer viruses or malware executed in cyberspace may reach their intended target, but also blindly strike and wreak havoc on subsystems relied upon by other allied forces around the world. These interrelationships are important considerations when planning for CEMA on a global scale.
Numerous challenges within the cyberspace domain exist, particularly when it comes to exploiting network protocol stacks. Often communications are based on the Open System Interconnection (OSI) model, where often the internet protocol (IP) is combined with Transmission Control Protocol (TCP) to form TCP/IP. This system is designed for packet exchange of critical data/information between CEMA operations but is one of the causes of flooding and other attacks.
Electronic Warfare and Challenges
EW is an activity that is integrated into operations through CEMA and consists primarily of three functions: electronic attack (EA), electronic protection (EP), and electronic warfare support (EWS). Figure 2 shows the general functions of EW. These EW functions are carried out and applied from the air, land, sea, space, and cyberspace by manned (i.e. surveillance aircraft) and unmanned (i.e. drones), or unattended systems (i.e. autonomous UAVs/sensors).
EW capabilities are now becoming important for how a battle is fought and won, as these capabilities are becoming increasingly important for how commanders shape operational environments to their advantage. For example, commanders may order that EW be used to establish favorable conditions for cyberspace operations (CO) by stimulating adversary networked sensors, denying wireless networks, or other related actions.
Other examples of offensive EA include jamming enemy radar or electronic command and control (C2) systems. Using electronic deception to confuse enemy intelligence, surveillance, and reconnaissance systems. Using directed-energy weapons to disable an enemy’s equipment or capability.
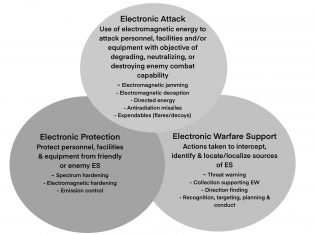
Figure 2: EW functionality (Adopted from https://irp.fas.org/doddir/army/fm3-38.pdf)
Spectrum management is often classified as part of electronic protection as well. Swift coordination is required for such tasks as deconfliction of spectrum resources allocated to different aspects of military forces. For instance, spectrum managers are often involved directly in planning EW operations to ensure that there’s no electromagnetic interference during an EW attack mission.
Finally, the US Department of the Army1 states that “electronic warfare support (EWS) is a division of electronic warfare involving actions tasked by, or under the direct control of, an operational commander to search for, intercept, identify, and locate or localize sources of intentional and unintentional radiated electromagnetic energy for the purpose of immediate threat recognition, targeting, planning, and conduct of future operations.” In other words, this involves the geolocation of RF emitter sources and establishing a plan of attack.
With the advance in computing and RF technologies, has come a number of challenges with detecting adversary emitter sources. This includes the ability of fast frequency hopping techniques to avoid detection of enemy transmission, various beam focusing/steering technologies, as well as the design of hard-to-detect waveforms that last in very short durations.
Spectrum Management and Challenges
The importance of the electromagnetic spectrum (EMS) and its relationship to the operational capabilities of the military is the focus of the electromagnetic spectrum operations (EMSO). Generally, the EMSO overlaps largely with electronic warfare (EW) and signals intelligence (SIGINT) operations. Within the EMSO organization are the interrelated functions of spectrum management, frequency band assignment, host-nation coordination, and various policies enabling planning, management, and execution of operations within the electromagnetic operational environment for all phases of a mission. Ultimately, the EMSO and its spectrum managers are responsible for coordinating EMS access among civil, joint, and multinational partners throughout the operational environment.
As discussed, the spectrum manager plays an integral part in all EW planning, who are able to inform commanders of spectrum conflicts initiated by friendly systems for personnel protection, enemy exploitation, or enemy denial. The advent of common user “jammers” has made this awareness and planning critical for the spectrum manager. Moreover, the spectrum manager coordinates with satellite managers to maintain awareness of frequency channels being used by satellite communications systems during uplink/downlinking. Thus, it is largely in the hands of the satellite manager to generate and process satellite access requests for all very high frequency (VHF), ultra-high frequency (UHF), super high frequency (SHF), and extremely high frequency (EHF) satellite systems which are important for military communications.
As mentioned, there is a lot of overlap between EW and EMSO. For instance, when the EMSO detects an adversary signal of interest, such as a radar jammer, EW can proceed to geolocate the enemy emission source. Then a plan of EA can occur, where EMSO processes an access request to use anti-radiation missiles to suppress the enemy radar jammer (these weapons use radiated energy emitted from a target as the mechanism for guidance onto the target).
Challenges in the management of the spectrum are often down to it being extremely contested and congested on the battlefield. This includes adversaries who aggressively launch electronic attacks and cyber technologies that erode the ability to use the spectrum for military operations, combined with the global wireless broadband and commercial satellite industry continuously attempting to reallocate spectrum from defense and satisfy consumer demands for greater mobility and data connectivity. Thus the challenges faced by all RF technologies used in military missions– from radar to satellite to tactical radios– will be to ensure efficiency, adaptability, and flexibility in using spectrum resources.
Putting it all together: Software Defined Radio (SDR) for CEMA
High-performance software-defined radio (SDR) is a technology that is at the heart of CEMA operations. This device generally consists of a radio front-end (RFE) and digital back end. The RFE is responsible for the actual tuning of RF frequencies used in transmit (Tx) and receive (Rx) functionalities. The RFE terminates at SMA connectors which can be connected to various antenna systems for communications between satellites, maritime vessels, aircraft, drone/UAV control systems, radar, and various other CEMA operations. On the other end, the digital back end, often with an embedded field-programmable array (FPGA) consists of a means to conduct various DSP as well as packetize RF data into transportable Ethernet packets over networks in cyberspace.
Size, weight, and power (SWaP) are also important characteristics of SDRs used in various applications in CEMA. Fortunately, these SDR devices can be tailored to suit the requirements of various operations. For instance, an SDR used in a satellite payload has very different requirements than an SDR used in a radar system.
The software part of an SDR stems from its ability to be reconfigured for tuning to center frequencies, analyzing different bandwidths, modulating/demodulating signals and data, and generating and transmitting new waveforms. These features help to solve challenges related to EW and EMSO, whereby the contested and congested spectrum can be navigated using the flexibility and adaptability inherent to SDR.
SDRs are also able to solve many of the issues encountered in cyberspace operations. For starters, issues related to cyberspace attacks, such as flooding or replay attacks, can be mitigated with various security features embedded into the SDRs FPGA used for de-framing packets. This can include multi-factor authentication algorithms, cryptographic schemes and a means to alert of various attacks.
Mitigation of spectrum management challenges is also possible with SDR. This includes evaluating and mitigating electromagnetic environmental effects, managing frequency records, and databases, deconflicting frequencies, frequency interference resolution, allotting frequencies, and EW coordination to ensure EM-dependent systems operate as intended. SDRs are often combined with storage solutions on a battlefield in order to be part of the CEMA network or cloud infrastructure.
Particularly important for processing signal data to determine timing, location (i.e. direction finding), or other RF emitter source information. Through an SDR’s high-performance radio front end (RFE), these systems are able to detect weak signals in a crowded spectrum (by having high instantaneous bandwidth, exceptional noise figures, and excellent dynamic range in the receiver chains). Moreover, elusive enemy signals using frequency hopping spread spectrum (FHSS) can be detected when using the highest instantaneous bandwidth SDRs, such as Per Vices Cyan, as shown in Figure 3. Swept mode operation or having a high instantaneous bandwidth ensures that enemy emitters will not fall out of band when using FHSS.
SDRs also provide timestamped data that make it possible for algorithms used in direction finding, particularly those related to time-difference of arrival (TDOA). As well, when using other direction-finding techniques, such as phase difference or interferometric measurements, high-performance SDRs have highly phase-coherent channels to ensure these measurements are possible.

Figure 3: Cyan SDR with the highest instantaneous bandwidth
Conclusion
CEMA is a continuously evolving means to integrate and synchronize the various operations in cyberspace, EW as well as spectrum management. SDR is fast becoming an integral part of these operations, due to its ability to combat a number of challenges related to CEMA.
Per Vices has extensive experience in developing, building, and integrating SDR for CEMA operations. To find out how we can help you on your next project, contact solutions@pervices.com.
References:
- Cyber Electromagnetic Activities, Department of the Army Headquarters (2014). https://irp.fas.org/doddir/army/fm3-38.pdf
About the Author
 Brendon McHugh is the Field Application Engineer and Technical Writer at Per Vices Corporation. Per Vices has extensive experience in developing, building, and integrating software-defined radios for CEMA operations. Brendon is responsible for assisting current and prospective clients in configuring the right SDR solutions for their unique needs, and possesses a degree in Theoretical and Mathematical Physics from the University of Toronto.
Brendon McHugh is the Field Application Engineer and Technical Writer at Per Vices Corporation. Per Vices has extensive experience in developing, building, and integrating software-defined radios for CEMA operations. Brendon is responsible for assisting current and prospective clients in configuring the right SDR solutions for their unique needs, and possesses a degree in Theoretical and Mathematical Physics from the University of Toronto.
Brendon can be reached online at solutions@pervices.com and at our company website https://www.pervices.com/
FAIR USE NOTICE: Under the “fair use” act, another author may make limited use of the original author’s work without asking permission. Pursuant to 17 U.S. Code § 107, certain uses of copyrighted material “for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.” As a matter of policy, fair use is based on the belief that the public is entitled to freely use portions of copyrighted materials for purposes of commentary and criticism. The fair use privilege is perhaps the most significant limitation on a copyright owner’s exclusive rights. Cyber Defense Media Group is a news reporting company, reporting cyber news, events, information and much more at no charge at our website Cyber Defense Magazine. All images and reporting are done exclusively under the Fair Use of the US copyright act.

