- T-Mobile will give you a Samsung Galaxy S25 Plus for free - how to qualify for the deal
- AI-Ready Optics Transceivers Partner Enablement Campaign
- Request for Comments: PCI Key Management Operations (KMO) v1.0 Standard
- This 5-in-1 travel charger is the only one I'll need this summer (and it's full of power)
- You can turn your Google Search into a podcast now - here's how
Technical Support Scams – What to look out for | McAfee Blog

Authored by Oliver Devane
Technical Support Scams have been targeting computer users for many years. Their goal is to make victims believe they have issues needing to be fixed, and then charge exorbitant fees, which unfortunately some victims pay. This blog post covers a number of example actions, that scammers will go through when they are performing their scams. Our goal is to educate consumers on the signs to look out for, and what to do if they believe they are being scammed.
Advertising – The Lure
For a tech support scammer to reach their victims, they need to first find them (or be found by them). One technique we see includes scammers creating Twitter or other social media accounts that post messages claiming to be from the official technical support site. For example, a Twitter account will post a tweet with the hashtags #McAfee and #McAfeeLogin to drive traffic to the tweet and make victims believe the links are legitimate and safe to click.
Scammers behind tech support scams can create very convincing websites which mimic the official ones.
Some fraudulent websites use the McAfee logo or other company logos to try trick individuals. They often invite clicking on a ‘LOGIN’ or ‘ACTIVATE’ link with a similar color scheme to official sites to appear legitimate.
These sites may then ask the victim to enter their real username, password, and phone number. Upon entering these details, websites will usually show an error message to make the victim believe there is an issue with their account.
The error message will usually contain a link that upon clicking will load a chat box where the scammers will initiate a conversation with the victim. At this point, the scammers will have the phone number and email address associated with the victim. They will use this to contact them and make them believe they are an official technical support employee.
Gaining Access
The scammer’s next objective is often to gain access to the victim’s computer. They do this so that they can trick the victim into believing there is an issue with their computer and that they need their support services to fix it.
The scammers will do this by either asking the victim to enter a URL that will result in the download of a remote access tool or by providing them with a link in the chat window if they are still speaking to them on the fake support website.
A remote access tool will enable the scammer to take complete control of the victim’s machine. With this, they will be able to remove or install software, access personal data such as documents and cryptocurrency wallets as well as dump passwords from the web browsers so they can then access all the victim’s accounts.
It is vital to not provide remote access to your computer to unknown and unverified individuals, as there could be a big risk to your personal data. Some examples of remote access tools that have legitimate uses but are often used to perpetrate fraud are:
- TeamViewer
- LogMeIn
- AnyDesk
- Aweray (Awesun)
Activity once the connection is established
If the scammers are given access to the victim’s machine, they will often make use of the command filename cmd.exe to perform some visual activity on the computer screen which is done to attempt to trick the individual into believing that some malicious activity is occurring on their computer or network. Most people will be unaware of the filename cmd.exe and the actions being used,and thus will be none the wiser to the scammer’s actions.
Here are some examples we have seen scammers use:
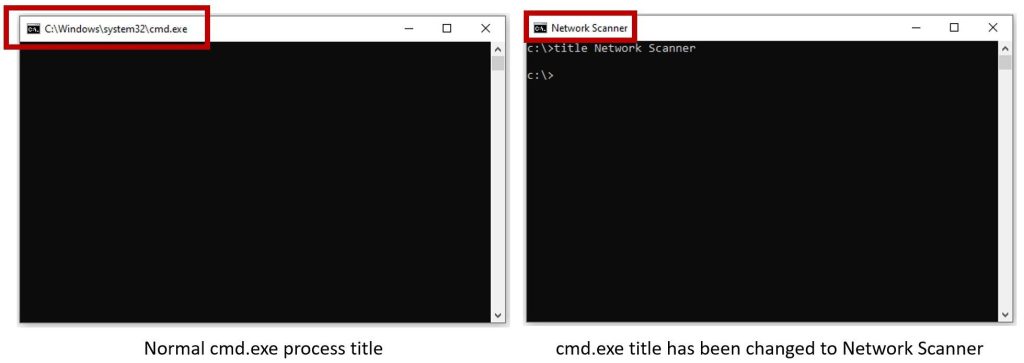
Title
Changing the title of cmd.exe to ‘network scanner’ or ‘file scanner’ to make the victim believe they are running a security tool on their machine.
Directory enumeration
Scammers will make use of standard functions within the cmd.exe file, to make their victims believe they are performing lots of activity. One of these functions is ‘dir’ which will display all the files for a specific directory. For example, if you have a folder called ‘school work’ and have 2 word documents in there, a ‘dir’ query of that folder will appear like this:
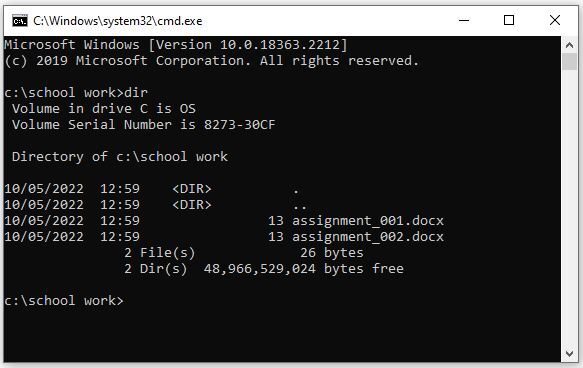
What the scammers will do is make use of ‘dir’ and the title function to make you believe they are scanning your machine. Here is an example of running ‘dir’ on the all the files on a machine with the cmd.exe title set to ‘File Scanner’:
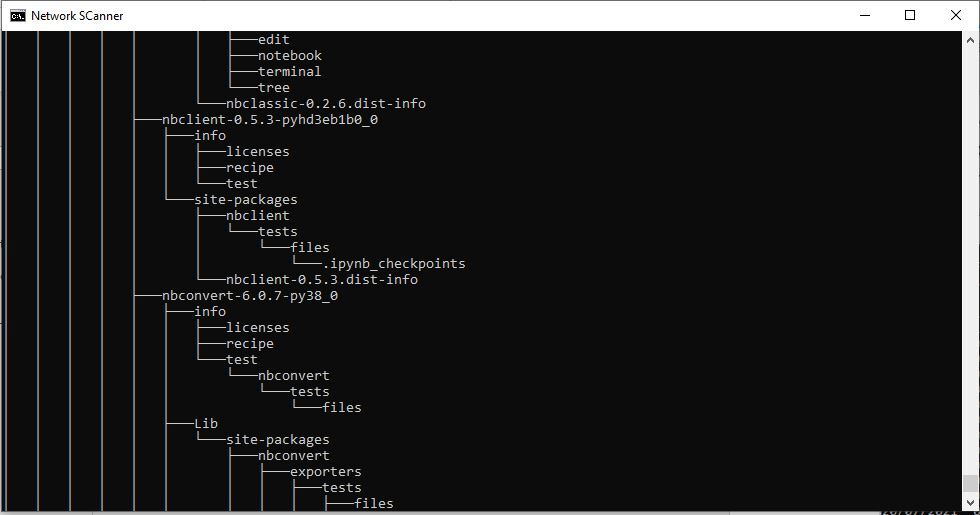
Tree
A similar function to ‘dir’ called ‘tree’ may also be used. The ‘tree’ function will display directory paths and will generate lots of events on the screen:
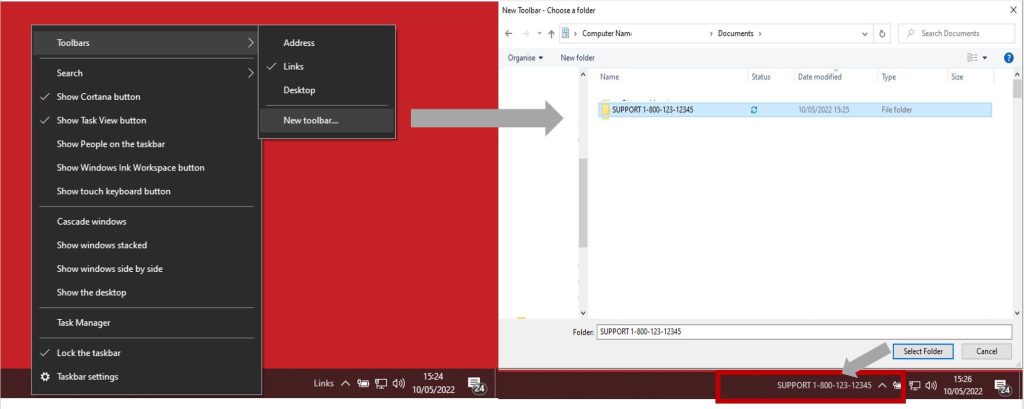
Tech Support Phone Number
Some scammers will also add their phone number to the taskbar of the victim’s machine. They do this by creating a new folder with the phone number as the name and adding it as a toolbar. This is shown in the image below
Software Installation
Scammers may install other software on the victim’s machine or make them believe that they have installed additional software which they will then be charged for.
For example, some scammers may add programs to the desktop of victims which have no purpose, but the scammers insist they are legitimate security tools such as firewalls or network scanners.
Some example filenames are:
- Firewall security.exe
- Network firewall.exe
- Network security.exe
- Email security.exe
- Banking security.exe
Payment
The scammers will usually perform some activity on your machine before asking for payment. This is done to build confidence in their work and make you believe they have done some activity and therefore deserve some sort of payment. Do not be fooled by scammers who have not performed any useful activity. As detailed in the previous sections, be careful not to fall victim to fake social media accounts or websites.
Signs to look out for
This section contains a few signs to look out for which may indicate that you are interacting with a scammer.
Rude/Short
Some scammers will become rude and very short with you if you start questioning what they are doing. They may say that you are not technical and do not understand what is occurring. This would not be the behavior of a legitimate technical support operative.
Leave the computer on
Scammers will encourage you to leave the machine and remote connection on even if you need to go out and leave it unattended. Do not under any circumstances do this as they would then be free to do any activity they wish on your machine and network.
Created files being detected
Some files added to your machine by the scammer may be detected by the AV security software. They may act like this is an error and the file is innocent. If you have initiated a remote connection and the controller creates a file on your machine which is detected by the security software, we recommend ceasing the interaction as detailed below.
What to do
The following steps should be performed if you believe you are being scammed as part of a tech support scam.
Disconnect the machine from the internet
If the machine is connected via a network cable, the easiest way is to unplug it. If the machine is connected via Wi-Fi, there may be a physical switch that can be used to disconnect it. If there is no physical switch, turn off Wi-Fi through the settings or the computer. It can be powered down by pressing the power button.
Hang up
Hang up the phone (or end the chat) and do not answer any more calls from that number. The scammer will try to make you believe that the call is legitimate and ask you to reconnect the remote-control software.
Remove the remote-control software
If the scammer was controlling your machine, the remote-control software will need to be removed. If the computer was powered down, it can be powered back up, but if a popup is shown asking for permission to allow remote access, do not grant it.
The remote software can usually be removed by using the control panel and add/remove programs. To do this, press the Windows key and then perform a search for ‘remove’ and click on ‘Add or remove programs’.
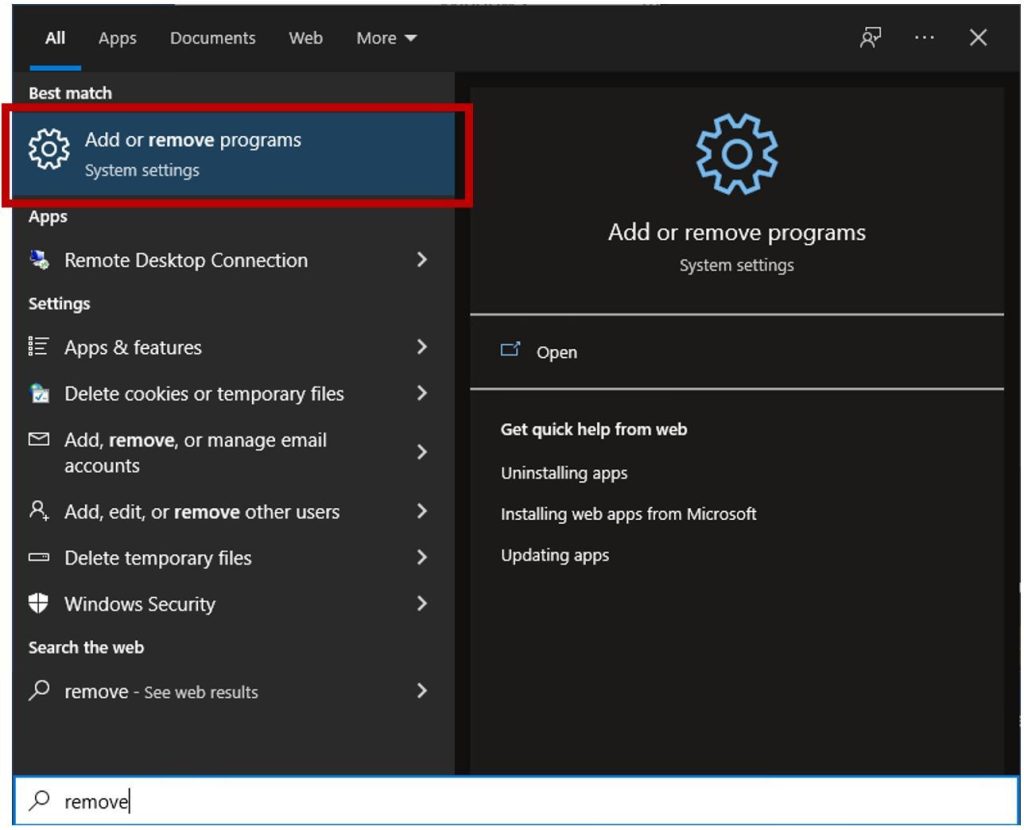
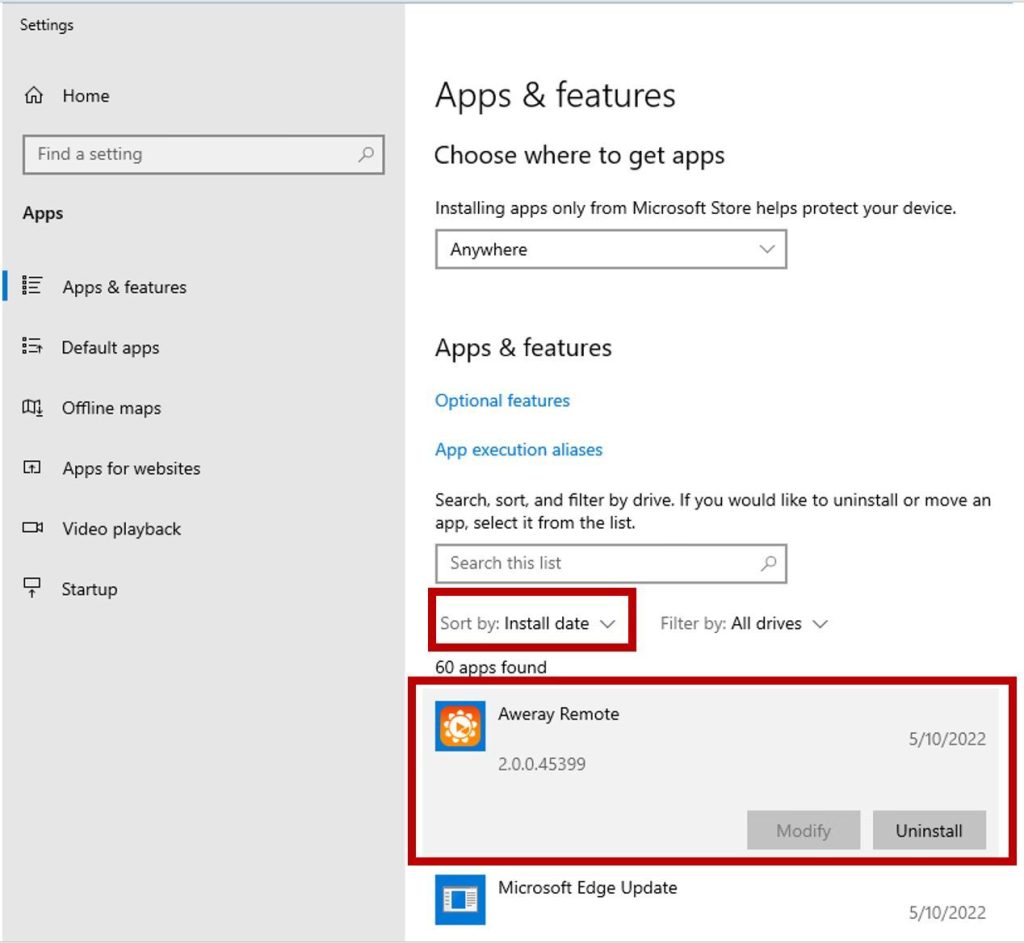
Sort the programs by install date as shown below and then remove the remote software by clicking on the ‘Uninstall’ button. Keep in mind that the software installed on your computer may appear by a different name, but if you look at what was installed on the same day as the scammer initiated the remote control session, you should be able to identify it.
Check the Antivirus Software for any exclusions
Some scammers may add exclusions for the files they create on your computer so that they are not detected by the security software. We recommend checking the exclusions and if any are present which were not added by yourself to remove them.
A guide for McAfee customers is available here
Update Antivirus Software and perform a full scan
After removing any software which was installed, we recommend updating your security software and performing a full scan. This will identify any malicious files created by the scammer such as password stealers and keyloggers.
Change passwords
After performing a full scan, we recommend changing all of your passwords as the scammer may have gathered your credentials while they had access to your computer. It is recommended to do this after performing a full scan as the scammers may have placed a password stealer on the computer and any new passwords you enter may also be stolen.
Conclusion
This blog post contains a number of examples that scammers may use to trick consumers into believing that they may have issues with their devices. If you are experiencing issues with your computer and want to speak to official McAfee support, please reach out via the official channel which is https://service.mcafee.com/.
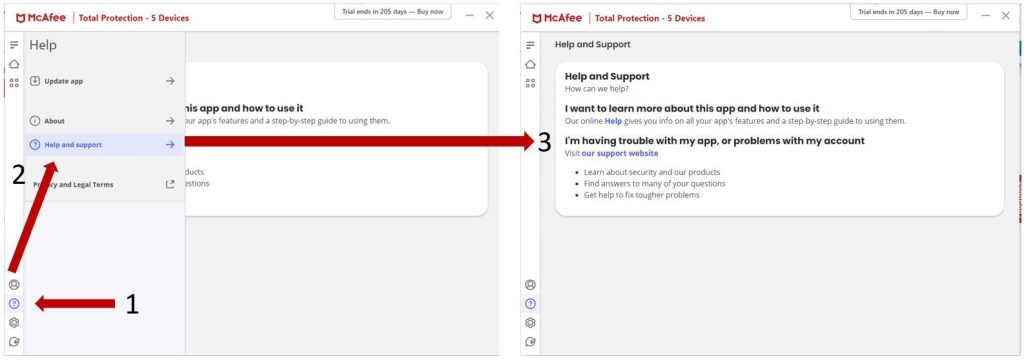
The McAfee support pages can also be accessed directly via the McAfee Total Protection screen as shown below:
McAfee customers utilizing web protection (including McAfee Web Advisor) are protected from known malicious sites.
!function(f,b,e,v,n,t,s)
{if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};
if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version=’2.0′;
n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];
s.parentNode.insertBefore(t,s)}(window, document,’script’,
‘https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘448732493334171’);
fbq(‘track’, ‘PageView’);
!function(f,b,e,v,n,t,s)
{if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};
if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version=’2.0′;
n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];
s.parentNode.insertBefore(t,s)}(window, document,’script’,
‘https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘187610925152304’);
fbq(‘track’, ‘PageView’);
// load Facebook
!function(f,b,e,v,n,t,s){if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};if(!f._fbq)f._fbq=n;
n.push=n;n.loaded=!0;n.version=’2.0′;n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];s.parentNode.insertBefore(t,s)}(window,
document,’script’,’https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘766537420057144’);
fbq(‘track’, “PageView”);
//document.write(‘x3Cnoscript>x3Cimg height=”1″ width=”1″ style=”display:none” src=”https://www.facebook.com/tr?id=766537420057144&ev=PageView&noscript=1″ />x3C/noscript>’);

