- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Oil and Gas Cybersecurity: Recommendations Part 3

Cyber Threats
In the final part of our series, we look at the APT33 case study and several recommendations from our expert team.
August 15, 2022
Read time: ( words)
The oil and gas industry continues to be a prime target for threat actors who want to disrupt the operation and wreak havoc. In part two, we discussed various threats that can affect an oil and gas company, including ransomware, DNS tunneling, and zero-day exploits. For the final installment of the series, we’ll investigate the APT33 case study—a group generally considered to be responsible for many spear-phishing campaigns targeting the oil industry and its supply chain. We’ll also lay out several recommendations to better strengthen the cybersecurity framework of oil and gas companies.
APT33: a case study
The group APT33 is known to target the oil supply chain, the aviation industry, and military and defense companies. Our team observed that the group has had some limited success in infecting targets related to oil, the U.S. military, and U.S. national security. In 2019, we found that the group infected a U.S. company providing support services to national security.
APT33 has also compromised oil companies in Europe and Asia. A large oil company with a presence in the U.K. and India had concrete APT33-related infections in the fall of 2018. Some of the IP addresses of the oil company communicated with the C&C server times-sync.com, which hosted a so-called Powerton C&C server from October to December 2018, and then again in 2019. A computer server in India owned by a European oil company communicated with a Powerton C&C server used by APT33 for at least three weeks in November and December 2019. We also observed that a large U.K.-based company offering specialized services to oil refineries and petrochemical installations was likely compromised by APT33 in the fall of 2018.
APT33’s best-known infection technique has been using social engineering through emails. It has been using the same type of lure for several years: a spear-phishing email containing a job opening offer that may look quite legitimate. There have been campaigns involving job openings in the oil and aviation industries.
The email contains a link to a malicious .hta file, which would attempt to download a PowerShell script. This would then download additional malware from APT33 so that the group could gain persistence in the target network. Table 1 lists some of the campaigns we were able to recover from data based on feedback from the Trend Micro™ Smart Protection Network™ infrastructure. The company names in the campaigns are not necessarily targets in the campaign, but they are usually part of the social lure used in the campaigns.
The job opening social engineering lures are used for a reason: Some of the targets actually get legitimate email notifications about job openings for the same companies used in the spear-phishing emails. This means that APT33 has some knowledge of what their targets are receiving from legitimate sources.
APT33 is known to be related to the destructive malware called StoneDrill and is possibly related to attacks involving Shamoon, although we don’t have solid evidence for the latter.
Besides the relatively aggressive attacks of APT33 on the supply chain, we found that APT33 has been using several C&C domains, listed in Table 2, for small botnets composed of about a dozen bots each. It appears that APT33 has taken special care to make tracking more difficult.
The C&C domains are hosted on cloud-hosted proxies. These proxies relay URL requests from the infected bots to back-ends at shared web servers that may host thousands of legitimate domains. These back-ends are protected with special software that detects unusual probing from researchers. The back-ends report bot data back to a dedicated aggregator and bot control server on a dedicated IP address. The APT33 actors connect to these aggregators via a private VPN with exit nodes that are changed frequently. Using these VPN connections, the APT33 actors issue commands and retrieve data from the bots.
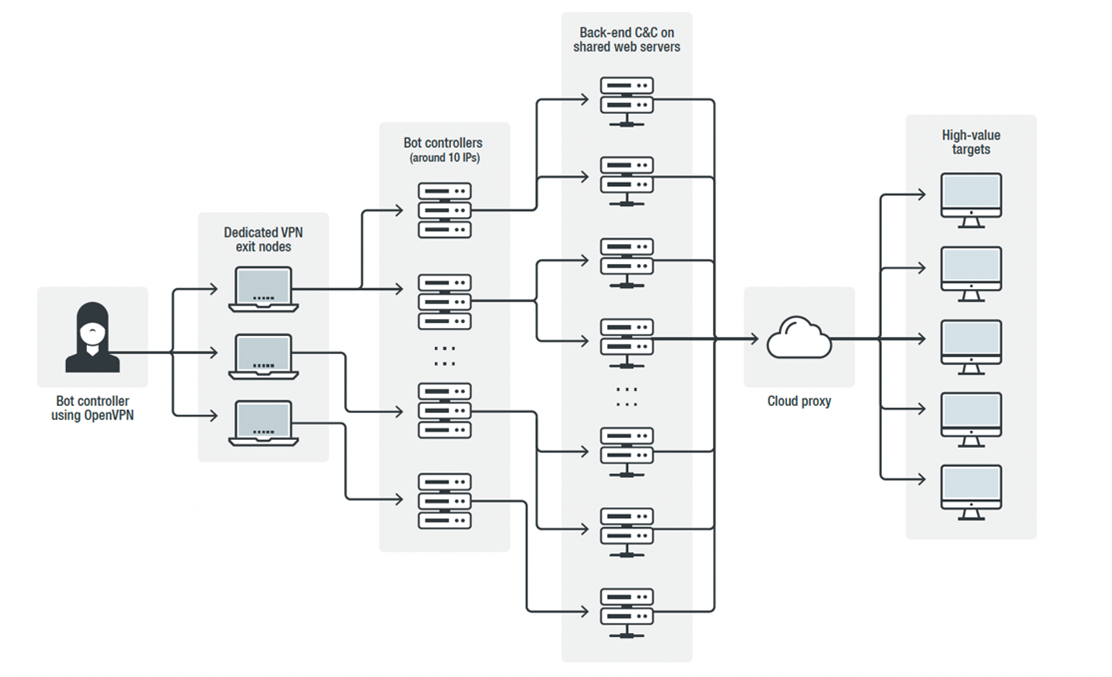
Regarding APT33, we were able to track private VPN exit nodes for more than a year. We could cross relate the exit nodes with admin connections to servers controlled by APT33. It appears that these private VPN exit nodes are also used for reconnaissance of networks that are relevant to the supply chain of the oil industry. More concretely, we witnessed IP addresses that we believe are under the control of APT33 doing reconnaissance on the networks of an oil exploration company in the Middle East, an oil company in the U.S., and military hospitals in the Middle East.
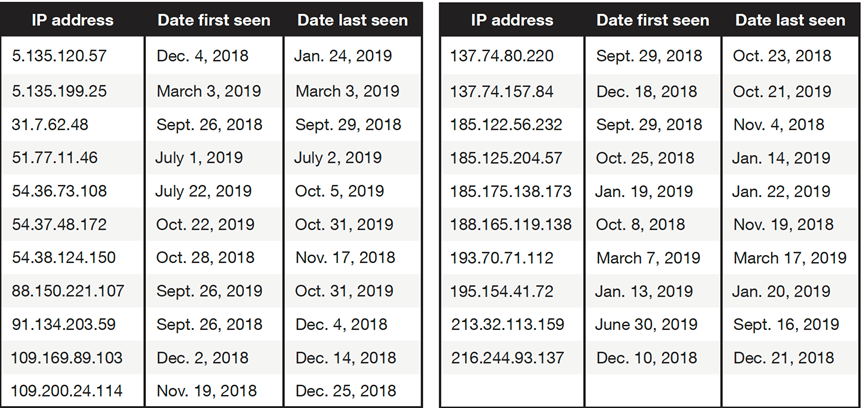
Table 2 shows a list of IP addresses that have been used by APT33. The IP addresses are likely to have been used for a longer time than the time frames indicated in the table. The data can be used to determine whether an organization was on the radar of APT33 for, say, reconnaissance or concrete compromises.
Security recommendations
Here are several general tips that may help companies in the oil and gas industry combat threat actors:
- Perform data integrity checks
While there may not be an immediate need for encrypting all data communications in an oil and gas company, there is some merit in taking steps to ensure data integrity. For example, regarding the information from the different sensors at oil production sites, the risk of tampering with oil production can be reduced by at least making sure that all data communication is signed. This can greatly decrease the risk of man-in-the-middle attacks where sensor values could be changed or where a third party could alter commands or inject commands without authorization. - Implement DNSSEC
We have noticed that many oil and gas companies don’t have Domain Name System Security Extensions (DNSSEC) implemented. DNSSEC means digitally signing the DNS records of a domain name at the authoritative nameserver with a private key. DNS resolvers can check whether DNS records are properly signed. - Lock down domain names
Domain names can potentially be taken over by a malicious actor, for example, through an unauthorized change in the DNS settings. To prevent this, it is important to use only a DNS service provider that requires two-factor authentication for any changes in the DNS settings of the domains of an organization. - Monitor SSL certificates
For the protection of a brand name and for early warnings of possible upcoming attacks, it is important to monitor newly created SSL certificates that have certain keywords in the Common Name field. - Look out for business email compromise
Protection against business email compromise (BEC) is possible through spam filtering, user training for spotting suspicious emails, and AI techniques that will recognize the writing styles of individuals in the company. - Require at least two-factor authentication for webmail
A webmail hostname might get DNS-hijacked or hacked because of a vulnerability in the webmail software. And webmail can also be attacked with credential-phishing attacks; a well-prepared credential-phishing attack can be quite convincing. The risk of using webmail can be greatly reduced by requiring two-factor authentication (preferably with a physical key) and corporate VPNs for webmail access. - Hold employee training sessions for security awareness
It is important to have regular training sessions for all employees. These sessions may include awareness training on credential phishing, spear phishing, social media use, data management, privacy policies, protecting intellectual property, and physical security. - Monitor for data leaks
Watermarks make it easier to find leaked documents since the company can constantly monitor for these specific marks. Some companies specialize in finding leaked data and compromised credentials; through active monitoring for leaks, potential damage to the company can be mitigated earlier. - Keep VPN software up to date
Several weaknesses in VPN software were found in recent years.36, 37 For various reasons, some companies do not update their VPN software immediately after patches become available. This is particularly dangerous since APT actors start to probe for vulnerable VPN servers (including those of oil companies) as soon as a vulnerability becomes public. - Review the security settings of cloud services
Cloud services can boost efficiency and reduce cost, but companies sometimes forget to effectively use all security measures offered by cloud services. Some services help companies with cloud infrastructure security.
To learn more about digital threats that the oil and gas industry face, download our comprehend research here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

