- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Attack Surface Management 2022 Midyear Review Part 1

Privacy & Risks
In our 2022 midyear roundup, we examine the most significant trends and incidents that influenced the cybersecurity landscape in the first half of the year.
Read time: ( words)
The digital age is an exciting time for businesses as it offers the opportunity to be more efficient and effective with how things are done. Many companies have taken this opportunity by adopting new technologies that allow them not only to improve their operations but also to create a better culture within those organizations.
However, the digital transformation has also created a wider attack surface that encompasses more areas, including email inboxes and IoT devices. In this three-part series, we examine the most significant trends and incidents that influenced the cybersecurity landscape in the first half of the year based on our 2022 midyear roundup report.
The Growing Attack Surface
In a study conducted in partnership with Sapio Research, we surveyed 6,297 IT security decision-makers from 29 countries about their thoughts on the risks brought about by the growing attack surface.
The majority of respondents were concerned about their increasing attack surface. When asked to describe how they felt, many (73%) described it as constantly evolving and messy while another 43 percent argued that the problem is out of control with no end in sight for growth.
The results show an alarming lack of understanding when it comes to digital risks.
Cyber risk is a difficult topic to address, with many organizations unsure of how best they should proceed. Thirty-seven percent of the organizations also claimed to have the least insight into cloud assets. Thirty-five percent said the same of their insights into networks. In addition, there were also blind spots for the end-user information as well (32%).
Threat Actors and Sophisticated Attack Tools
One of the prominent APT groups from early 2022 was a threat actor called “Earth Lusca.” This group has been active since mid-2021 and conducts cyber espionage campaigns targeting organizations around the world by using spear phishing lures, watering holes tactics which are common among other actors in their arsenal along with more sophisticated malware such as Cobalt Strike or Shadowpad. They also use these VPSs for command control architecture where it deploys Winnti infections amongst others.
Malware also seems to stay for good.
Malware has been around for quite some time now and it’s not going anywhere any time soon. In fact, older malware is still popular among cybercriminals who recognize its effectiveness in attack campaigns despite increased security measures put up by organizations against such threats.
In our 2022 Security Predictions, we mentioned that malicious actors turn towards commodity botnet or other tools when attempting new techniques; this turned out exactly as expected with Emotet being offered through a malware-as-a-service (MaaS) scheme, precisely because they knew there would be demand due to its success over the recent months.
Another attack group that has continued to plague 2022 is Conti. It is one of the prominent threat actors that became involved early in the Russia-Ukraine War and announced its support for the Russian government just a day after the war started. The group then softened its stance following criticism over attacks launched against individuals or groups who are victims themselves.
The Stormers ransomware gang also announced its support for Russia and declared that it would target Ukrainian government institutions as part of its plans.
New Players and Lucrative Monetization Method
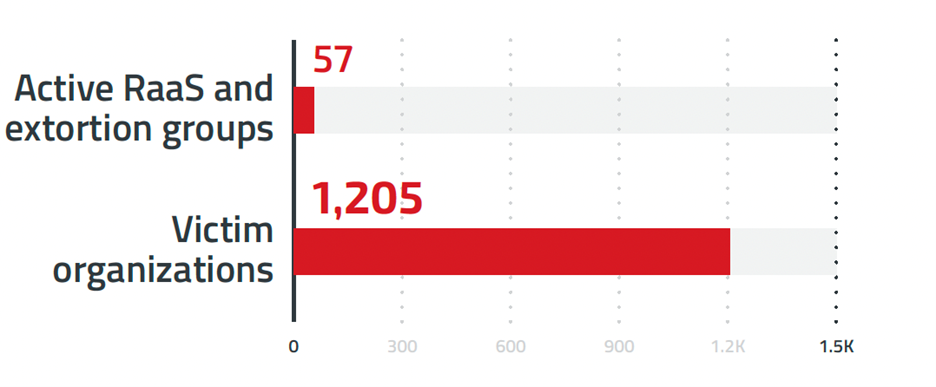
The RaaS model has provided hackers with access to tools and infrastructure that would not be available otherwise. Affiliates are also responsible for infections, as well as split ransomware payments between developers, giving them an additional opportunity in the evolution of malware and other techniques.
With over 50 active RaaS and extortion groups, 1,200 organizations were victimized by ransomware in the first half of this year alone.
The malware landscape is changing rapidly, and with that comes an increase in new types. Lockbit, Conti and Black Cat were major players during the first half of 2022 while other methods saw notable increases in other ransomware families.
Linux: A Prime Target
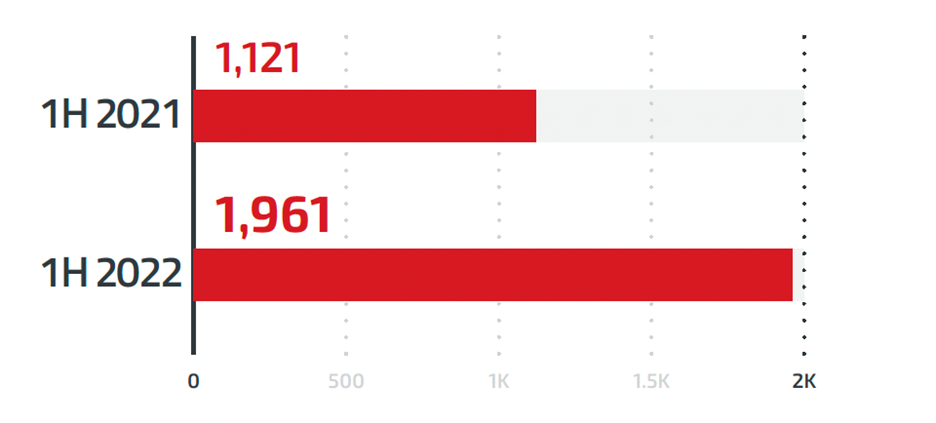
Linux systems present a juicy target for malicious actors who want to expand their reach and target specific types of infrastructure, such as servers and embedded systems where Linux is expected grow over the next few years.
We observed 75% more ransomware attacks targeting this system during the first half of 2022 compared with last year’s first half. It lends evidence to our assumption about a focused effort by cybercriminals on this platform at least until 2024 when it will be increasingly difficult due to new security measures put into place following WannaCry 2 & NotPetya outbreaks.
LockBit’s operators announced a new variant of their product in October 2021. This Linux-based ESXi Locker, version 1.0, targets servers through advanced encryption standard (AES) and elliptic curve cryptography, making it nearly impossible for hackers to access data on these machines without the correct key.
LockBit Linux-ESXi Locker version 1.0 and Cheerscrypt deviate from the typical double extortion scheme used by many other ransomware variants, but it still has a notable potential impact since ESXI servers are widely used in enterprises for server virtualization. These servers host important data within an organization’s critical infrastructure that could lead to damage if successfully attacked or corrupted.
The first half of the year has seen a rise in both ransomware and other notable vulnerabilities. In part two, we’ll discuss these threats with an eye toward their impacts on your organization’s security posture as well as how you can best protect yourself from them going forward.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

