- Learn with Cisco at Cisco Live 2025 in San Diego
- This Eufy robot vacuum has a built-in handheld vac - and just hit its lowest price
- I highly recommend this Lenovo laptop, and it's nearly 50% off
- Disney+ and Hulu now offer prizes, freebies, and other perks to keep you subscribed
- This new YouTube Shorts feature lets you circle to search videos more easily
A Deep Dive into the Evolution of Ransomware Part 1

Ransomware
This 3-part blog series takes an in-depth look at the evolution of ransomware business models, from the early stages to current trends.
Read time: ( words)
Ransomware has become a notorious and damaging form of malware, inflicting financial losses on enterprises, governments, healthcare organizations and core infrastructure. Ransomware has been a very profitable activity for malicious actors. However, we want to investigate what would cause changes in this business model—both in the far future and near future.
Our team conducted comprehensive research to understand the future of ransomware. We studied various scenarios, from focusing on risk assessment and avoiding capture by authorities, to exploring more financially advantageous opportunities cybercriminals may come across in their operations.
It appears that geopolitical events such as Russia’s 2022 invasion of Ukraine can be triggers for this change along with proactive defence strategies employed by authorities’ network hardening tools, arrests against criminal gangs and cryptocurrency regulations designed to reduce money laundering risks. We believe these conditions will help create an environment where malicious activity associated with ransomware is now less attractive to cybercriminals.
The ransomware evolution
Fake virus
Before mapping out what the future brings for ransomware and its implication for cybersecurity, it’s vital to look back at its evolution over the years.
In the past decade, ransomware attacks have become an increasingly common threat in the digital world. To understand these malicious tactics better, we can look to earlier forms of ransom-requesting malware such as “Fake Antivirus” software and “Locker” malware. Both methods involve hijacking a computer system’s data while attempting to persuade users into paying up with various scare tactics.
However, Fake AV was particularly successful from 2005 – 2010 due to its ability to convince many people that their computers were infected even when they weren’t. This eventually led it to gain press attention which subsequently caused its effectiveness (and popularity) among hackers to decline significantly over time.
Locker malware
By 2010, Locker malware had become a prevalent threat. Rather than usual viruses that are designed to disrupt computers, this malicious code enabled attackers to completely lock users out until they paid money in exchange for access and often posed as a “fine” from fake law enforcement agencies. However, due to its high-profile coverage and exposure by the media, victims soon became aware of these ruses.
Encrypting ransomware
Ransomware attacks have become an all-too-common occurrence since 2015, targeting users’ files with a powerful encryption algorithm and demanding payment to unlock them. This type of attack is particularly effective; once the computer system has been infected, victims are helplessly entrapped. As such, ransomware poses a serious threat to individuals and organizations alike.
The wave of ransomware attacks that swept across the world using Bitcoin payments has allowed attackers to evade law enforcement and receive payment more easily. Common perpetrators included CryLock and Dharma/Crysis who initially employed mass-mailed downloads or links attached to email messages as their main vector for delivering malware – a method often able to bypass anti-spam filters in its indiscriminate spread.
Modern ransomware
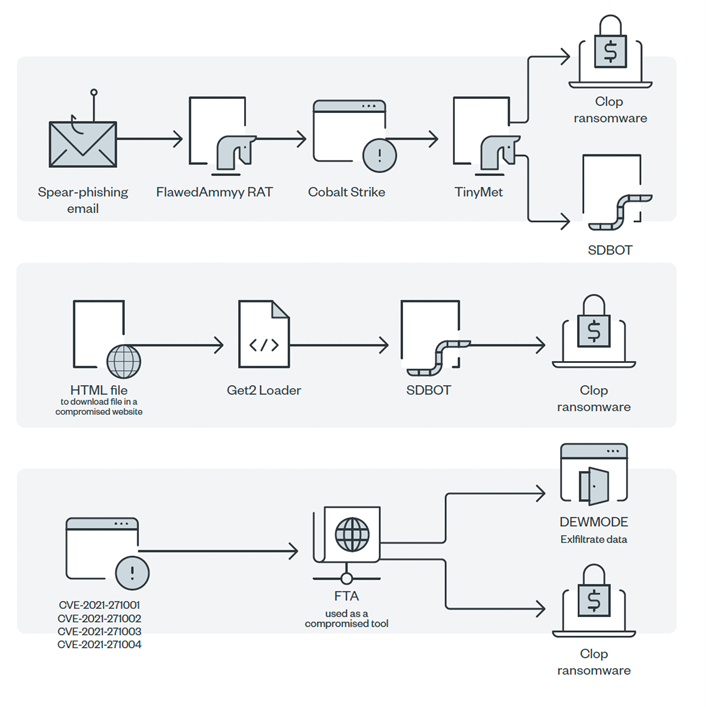
As ransomware continues to evolve, intruders have become increasingly targeted in their attacks. In 2019, newer versions of this malicious software infiltrated the network via hacking or other means. After assessing for valuable data, they moved laterally within it to gain administrative privileges before encrypting that information and asking for a ransom payment. Among the most well-documented variants are Conti, Clop & LockBit.
Ransomware attacks have evolved into sophisticated strategies, combining encryption with additional tactics to persuade victims to pay. Tactics range from publishing data bit by bit in an attempt to increase pressure on targets through more aggressive measures, making these threats all the harder for organisations and individuals alike to protect against.
When it comes to extortion, criminals don’t just settle for a basic demand. In recent years, ransomware attacks have evolved from double-extortion threats of data disclosure into triple and quadruple extortions using additional pressure points such as the threat of distributed denial of service (DDoS) attacks on networks or harassing victims through social media platforms like clients and suppliers. The ultimate goal remains: financial gain via ransom payments at any cost.
Key underground services that enable ransomware
Ransomware has become an integral part of a sophisticated criminal ecosystem. Several actors may play key roles in the ransomware process, from pre- to post-attack. These phases are critical for successful implementation – understanding them is essential to protecting yourself against potentially devastating attacks.
Some underground phases that enable ransomware:
- Initial access
Gaining access to a network is frequently done through malicious email campaigns which contain backdoors, targeting enterprises with specific social engineering techniques and exploiting vulnerabilities in internet-facing systems. Additionally, some ransomware actors purchase initial access from sellers of specialized services or gain it themselves. - Lateral movement and privilege escalation
In this phase, an attacker tries to penetrate deeper into the victim’s network and tries to get elevated privileges with standard or custom hacking tools. - Sensitive data exfiltration
When the lateral movement phase is a success, the attacker is likely to get their hands on private data and will try to exfiltrate it. In addition, the stolen data is analyzed to determine the ransom amount and whether the company has cyber insurance. - Backup systems’ disruption
The attacker tries to lower the chances of the victim’s capability to potentially restore systems from backups by disrupting the backup processes and systems. - Ransomware payload deployment
In this phase, an attacker deploys ransomware that can lead to serious problems for the victim: data files are encrypted and IT systems become unusable. - Extortion
The attacker extorts the victim. Two ways are particularly harmful: the victim gets a decryption key for the encrypted data only after paying a ransom, or the threat actor threatens to release stolen data if the victim does not pay a ransom.
In part two, we’ll discuss triggers that may cause ransomware actors to shift business models that could prompt them to start a ransomware revolution.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

