- Half of Firms Suffer Two Supply Chain Incidents in Past Year
- Data strategy e qualità del dato: come gettare le basi per implementare l’AI
- INE Security Alert: $16.6 Billion in Cyber Losses Underscore Critical Need for Advanced Security Training
- From help desk to AI harmony: Redefining IT support in the age of intelligent automation
- F5 grabs agentic AI startup Fletch to bolster security platform
DLL sideloading and CVE attacks show diversity of threat landscape

Threat watchers have spotted new cybersecurity exploits illustrating the protean nature of hacks as malware groups adapt and find new opportunities in dynamic link libraries and common vulnerabilities and exposures.
Security firms Bitdefender and Arctic Wolf are among those who have their eyes on new offensive maneuvers. One of these, dubbed S1deload Stealer, is a sideloader exploit using social channels like Facebook and YouTube as vectors, per Bitdefender.
Jump to:
Sideloading using link libraries as decoys
Bitdefender said S1deload Stealer infects systems through sideloading techniques affecting DLL’s, shared code libraries used by virtually every operating system. The target vectors are social channels via a legitimate executable file in the guise of explicit content.
SEE: IBM: Most ransomware blocked last year, but cyberattacks are moving faster (TechRepublic)
The sideloading technique is used to hide malicious code in the form of a DLL loaded by a legitimate digitally signed process, according to Martin Zugec, technical solutions director at Bitdefender. Zugec noted that DLL sideloading abuses legitimate applications by wearing “sheep’s clothing” of legitimate DLL files for Windows or other platforms.
“We call it ‘sideloading’ because while Microsoft or another OS is running, the exploit is executing malicious code on the side,” said Zugec (Figure A).
Figure A
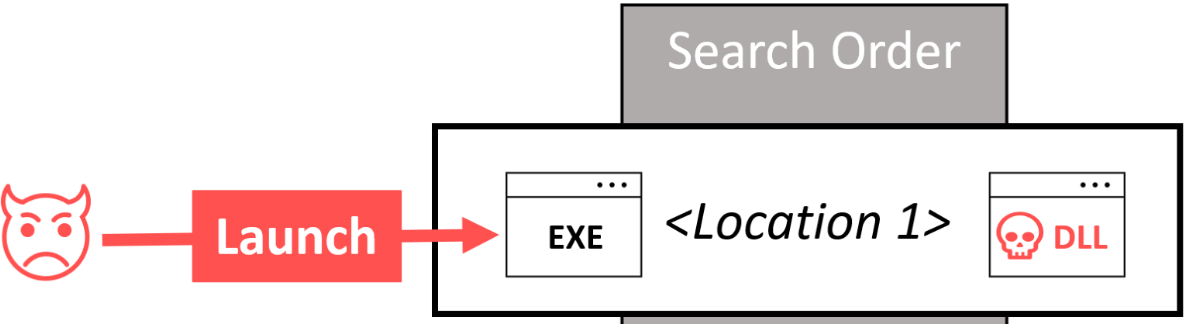
Zugec said Bitdefender has seen a large spike in the use of this tactic “due to the fact that DLL sideloading allows the threat actors to stay hidden. Many endpoint security solutions are going to see that the DLL files are executable, signed, for example, by Microsoft or by any big name company known to be trusted. But, this trusted library is going to load malicious code.”
S1deloader exploits social media for nefarious outcomes
In a white paper, Bitdefender reports that, once installed, S1deload Stealer performs several malicious functions including credential stealing, identifying social media admins, artificial content boosting, cryptomining, and further propagation through user follower lists.
Other functions of S1deload Stealer include:
- Using a legitimate, digitally-signed executable that inadvertently loads malicious code if clicked.
- Infecting systems, as sideloading helps get past system defenses. Additionally, the executable leads to an actual image folder to lower user suspicion of malware.
- Stealing user credentials.
- Emulating human behavior to artificially boost videos and other content engagement.
- Assessing the value of individual accounts, such as for identifying corporate social media admins.
- Mining for BEAM cryptocurrency.
- Propagating the malicious link to the user’s followers.
Zugec was quick to point out that the companies, whose executables are used for sideloading, are typically not to blame.
SEE: Security awareness and training policy (TechRepublic Premium)
“We see a difference between active sideloading, where the software is vulnerable and should be fixed, and passive sideloading, where the threat actor is going to take an executable from one of these big companies,” Zugec said, noting that in the latter case, the executables may have been developed a decade ago.
According to Zugec, the actors “create an offline copy of it, put the malicious library next to it and execute it. Even if the executable was patched a decade ago, threat actors can still use it today to maliciously and silently hide the code.”
Attacks aiming for unresolved vulnerabilities on the rise
The CVE exploits observed by Bitdefender and Arctic Wolf feature attacks on publicly disclosed security flaws. According to cyber insurance and security firm Coalition, which monitors CVE exploit availability using sources such as GitHub and Exploit-DB, the time to exploit for most CVE’s is within 90 days of public disclosure — ample time for vulnerability vendors or threat actors themselves to jimmy a digital window into a network. In its first-ever Cyber Threat Index, Coalition said the majority of CVEs were exploited within the first 30 days.
In the report, the company predicted:
- There will be in excess of 1,900 new CVEs per month in 2023, including 270 high-severity and 155 critical-severity vulnerabilities — a 13% increase in average monthly CVEs from published 2022 levels.
- 94% of organizations scanned in the last year have at least one unencrypted service exposed to the internet.
- On average, in 2022, verified exploits were published on Exploit-DB after 30 days of CVE, and the firm found evidence of potential exploits in GitHub repositories 58 days after disclosure.
New proof-of-concept CVE puts organizations using ManageEngine at risk
Bitdefender unearthed a weaponized proof-of-concept exploitation code targeting CVE-2022-47966, exploiting a remote code execution vulnerability. The targets are organizations using ManageEngine, a popular IT management suite.
Bitdefender Labs is investigating an incident it flagged in ManageEngine ServiceDesk software, which, because it lets an attacker execute remote code on unpatched servers, can be used to install espionage tools and malware.
The firm’s analysts reported seeing global attacks on this CVE deploying Netcat.exe, Colbalt Strike Beacon and Buhti ransomware to access, do espionage and deliver malware.
“Based on our analysis, 2,000 to 4,000 servers accessible from the internet are running one of the vulnerable products,” said Bitdefender, which noted that not all servers can be exploited with the code provided in the proof of concept. “But, we urge all businesses running these vulnerable versions to patch immediately.”
Lorenz group uses VoIP vulnerability to execute RAM capture
Arctic Wolf just issued its own report detailing a series of brazen repeat-attack exploits by the notorious Lorenz ransomware group exploiting a CVE in a Mitel MiVoice VoIP appliance.
The company noted the attackers were leveraging a compromised VPN account to regain access to the victim’s environment and execute Magnet RAM Capture. This is a free tool that law enforcement and forensic teams use to capture the physical memory of a victim’s device — on a Mitel Digital Voicemail system running Microsoft Windows Server 2016 (Figure B).
Figure B

The attackers used Magnet RAM Capture to bypass the victim’s endpoint detection and response. Arctic Wolf Labs said it has informed Magnet Forensics about the known abuse of its tool by the Lorenz group.
Daniel Thanos, vice president and head of Arctic Wolf Labs, said that with the rapid increase in cybercrime, organizations must ensure they continue to staff cybersecurity talent that can stay on top of new shifts in threat actor tactics, techniques and procedures.
“Threat actors have proven that they will rapidly adopt new exploits, evasion methods and find new legitimate tools to abuse in their attacks to blend into normal host and network activity,” Thanos said. “Our new research on Lorenz ransomware abusing the legitimate Magnet RAM Capture forensics utility is another example of this.”

