- Forget Ring - Arlo's flagship battery-powered security camera is still on sale for $120
- These might be one of my favorite exercise earbuds -- and they're still on sale
- If Musk wants AI for the world, why not open-source all the Grok models?
- xAI's Grok 3 is better than expected. How to try it for free (before you subscribe)
- EXL Code Harbor streamlines platform migration, data governance, and workflow assessment
Benefits of Cloud Automation
Workload Security
Learn more about how cloud automation can simplify security controls, policies, and scans.
Read time: ( words)
Related articles in the Cloud Migration series:
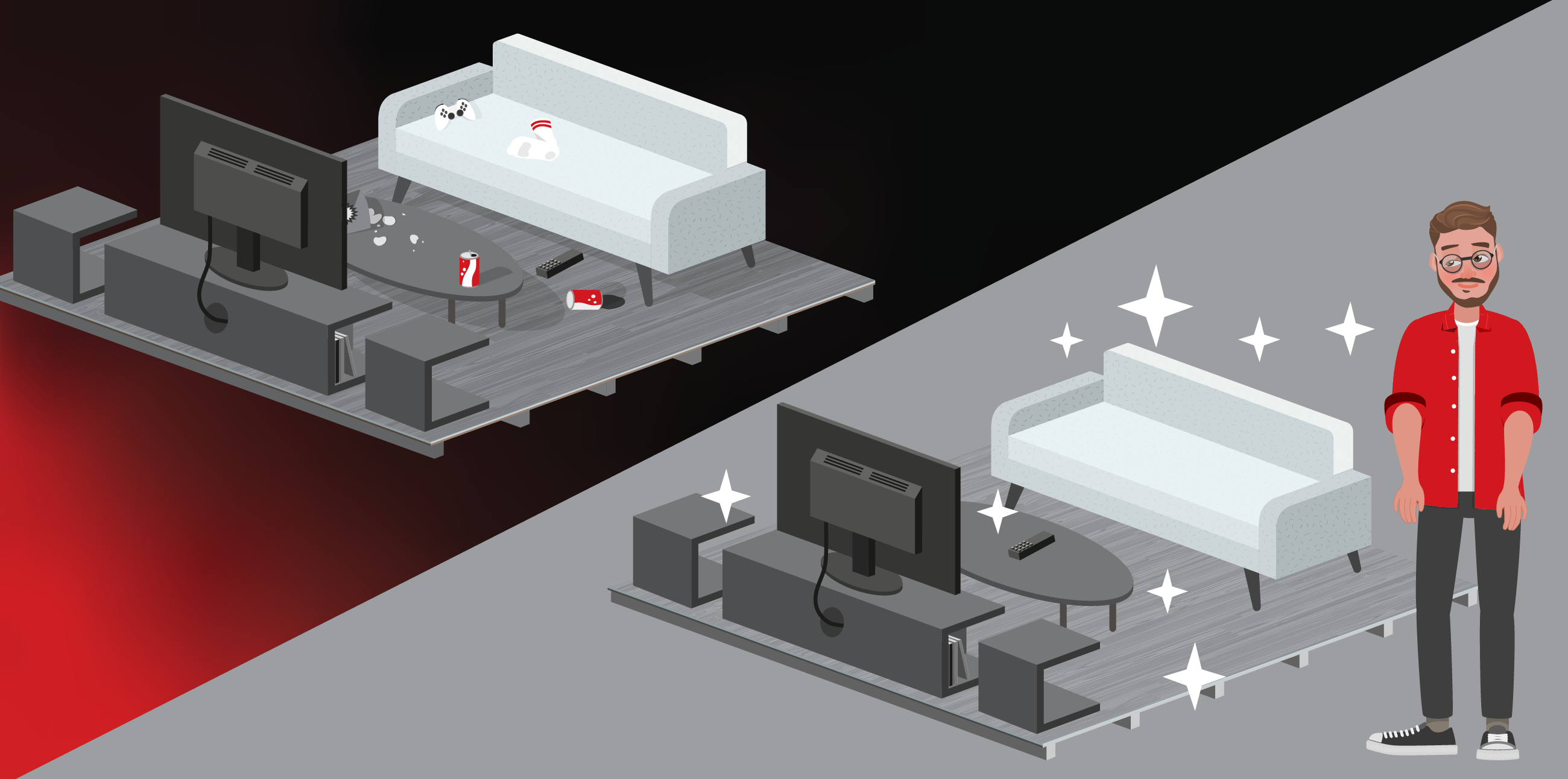
Automation is the bedrock to innovation. It allows people to work smarter, not harder. Think of inventions like the dishwasher, laundry machines, and the robotic vacuum. All of these automate chores that are mundane, tedious, and time-consuming. You can think of cloud automation in the same way. It simplifies many processes, including some related to security, allowing you to shift your focus away from manually deploying protection for new infrastructure and creating more time for business transformation projects.
The importance of automation is reflected by its demand from security leaders. According to a study by Fegue, 95% of the IT, cloud, and security professionals surveyed said that security automation would enable them to be more efficient and make cloud-based data security more effective.
Let’s dive into the benefits of cloud automation, specific use cases, and how to select the right tool for your cloud migration journey:
Benefits of cloud security automationBesides the basic fact that automation simplifies security by eliminating manual tasks, freeing you to focus on innovating, here’s how cloud automation can help you get ahead:
- Minimizes misconfigurations: Human error remains the #1 cause of cloud misconfigurations. Cloud automation eliminates the guesswork and human errors that can compromise your infrastructure.
- More resilient: Just like insurance for your home, a back-up process for your data is a necessity. By automating that process, you minimize recovery time and can limit the impact of a breach.
- Supports both security and development teams: Ensure security from the very beginning of the build process throughout deployment by integrating automated scans and testing from the moment code is committed to the repository.
- Accelerates compliance: Manual compliance audits are a costly time sink when DevOps teams need to be as agile as possible. With cloud automation you can scan continuously and enforce security policies throughout the development process, ensuring you demonstrate compliance without compromising build time.
Cloud automation use cases
There are many ways to incorporate automation into your cloud migration journey—so where should you start? Here are a couple suggestions:
Manage permissions
Secure user permissions are the first line of defense against data breaches, just as locked doors and windows deter would-be burglars. But manually authorizing, tracking, and deprovisioning access can be difficult considering the sheer amount of your dispersed cloud resources. Cloud automation tools can streamline this process by allowing you to create permissions based on roles, enable multi-factor authentication (MFA), and require regular password rotation. You can even identify overly permissive user and service accounts using cloud automation.
Infrastructure as code
Think of the difference between manually building security infrastructure and using infrastructure as code (IaC) like a weekend handyman building a house from the ground up versus a professional builder. The handyman could learn along the way and hopefully build something secure, but this will waste a lot of time, resources, and money. A builder comes in with a plan and the resources to lay a strong foundation. Similarly, IaC quickly establishes the strong foundation for developers to build upon, instead of the time-consuming alternative of manually building and configuring the infrastructure.
Virtual patching
There’s no such thing as being 100% secure. Sooner or later, something will slip through the cracks. When it does, automated identification and remediation will limit the impact to ensure you remain compliant. Virtual patching can be automatically applied to known and unknown vulnerabilities on affected servers and endpoints before the vendor patch is released. This saves you from countless hours—and potential system downtime—spent trying to manually locate and patch everything yourself.
Choose your fighter: Cloud automation tools
As we’ve reiterated throughout this series, a cybersecurity platform solution is ideal, but these solutions are not all equal. Your tool of choice should be able to handle the specific use cases we listed (permissions, IaC, and remediation) as well as:
- Discovery of workloads and cloud infrastructure across all the major cloud service providers (CSPs), including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform™.
- Continuous scanning and monitoring of IaC templates, instances, applications, cloud file storage, cloud networks, and everything in between for vulnerabilities, malware, and compliance risks. Yes, we already mentioned compliance scanning in this article, but it’s so important it deserves mentioning (at least) twice. Automated scanning should also generate relevant reports, logs, and alerts, so anything unusual can be quickly brought to your attention.
- Detection and remediation of known and unknown vulnerabilities or risks to minimize disruption to workflows.
- Integration with your existing tool set for automated security deployment, policy configuration and management, health checks, incident response, and more.
Next steps
Cloud automation is the key to a smooth and efficient cloud migration. Think of automation like the electricity in your home. Without power your dishwasher, laundry machines, and robotic vacuums are useless. After you’ve put your security strategy together, incorporating cloud automation allows it to go from paper to practice.
Trend Cloud One™ is a security services platform compromised of eight solutions. Each solution is purpose-built for cloud builders to simplify their security approach while providing cutting-edge protection. Here’s a look at how our solutions check all the boxes:
- Discovery of workloads and cloud infrastructure: Trend Cloud One is optimized for DevOps thanks to strong API integration with Microsoft Azure, AWS, and Google Cloud. Workload Security automatically protects new and existing workloads across your mixed environment of virtual, physical, cloud, and containers.
- Continuous scanning and monitoring:
- Trend Cloud One provides continuous security, compliance, and governance checks against nearly 1,000 configuration best practices and nearly 100 services from major CSPs. Check IaC templates thanks to CloudFormation Template Scanning and run preconfigured or customized reports with an endless combination of filters.
- Trend Cloud One provides automated malware scanning whenever new files are uploaded to block known bad files and protect against malware variants. By scanning files of all sizes and types, DevOps teams’ workflows remain uninterrupted and secure.
- Detection and remediation: Trend Cloud One deploys without disruption or need to rearchitect and immediately inspects ingress and egress traffic. It also includes virtual patching and post-compromise detection and disruption, so you’re secured against all phases of the attack life cycle.
- Integration with your existing tool set: Thanks to powerful APIs, all eight solutions integrate seamlessly with your favorite communication, deployment, orchestration, cloud storage, and other tools from major CSPs.
- Managing permissions: Automatically ensure your AWS Identity Access and Management (IAM) policies are enforced thanks to many IAM configuration checks.
- Infrastructure as a code: Ensure your IaC templates are secure and compliant via automated scans against industry best practices.
Simplify your cloud migration journey by experiencing the benefits of automation with a free 30-day trial of Trend Cloud One.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk


