- How to Use AI in Cyber Deception
- How To Privacy-Proof the Coming AI Wave
- Why the Even Realities G1 are the smart glasses to beat in 2025 - and I've tested several pairs
- VPN-ready routers may be a smartest way to connect to Wi-Fi now. I put one to the test
- 4 surprise products we could see at Samsung Unpacked 2025 - and are worth getting excited about
BBC, British Airways, Boots hit with hackers’ ultimatum after suffering MOVEit supply-chain attack

British Airways, BBC and Boots have all been served an ultimatum after they were hit with a supply-chain attack by the ransomware group Clop. In a post made available on their dark web portal, the cybercrime group warned the affected organizations to get in touch by June 14th or risk exposing their stolen data to the public domain. The data are believed to contain personal information, including names, bank details, addresses and national insurance numbers.
Also affected by this security incident are the U.K. payroll services provider Zellis, Dublin-based Aer Lingus, the University of Rochester and the Nova Scotia government.
Confirming this attack, Zellis, whose customers include Jaguar Land Rover, Harrods and Dyson, reassured their clients the breach did not affect other critical components of their IT ecosystem.
“We can confirm that a small number of our customers have been impacted by this global issue, and we are actively working to support them. All Zellis-owned software is unaffected, and there are no associated incidents or compromises to any other part of our I.T. estate,” Zellis noted in a statement.
“We have been informed that we are one of the companies impacted by Zellis’s cybersecurity incident which occurred via one of their third-party suppliers called MOVEit,” British Airways told Sky News.
Jump to:
How did this supply-chain attack happen?
Clop exploited an SQL injection vulnerability (CVE-2023-34362) in the popular business software MOVEit and accessed its servers. MOVEit software is designed to move sensitive files securely and is popular around the world, with most of its customers in the U.S. and Europe.
Last week, the U.S. Cybersecurity & Infrastructure Security Agency warned that hackers had found a vulnerability in the MOVEit Transfer tool and urged users around the world to seek ways to protect their sensitive information against a possible supply-chain attack.
Who is the Clop ransomware group, and what is their demand?
Clop is a Russian-based ransomware crew that has been fingered in many data breaches targeting top business organizations worldwide. In February 2023, Clop claimed responsibility for a supply-chain attack that affected more than 130 organizations, including data belonging to CHS Healthcare patients. The group also had a hand in the Accellion File Transfer Appliance data breach in 2020, which impacted around 100 organizations, including Shell, Kroger and the Australian Securities and Investments Commission. In another major attack reported by The Daily Mail, the group was responsible for dumping sensitive medical records of NHS patients on the dark web after the NHS refused to succumb to their £3 million ransom demand.
Following this recent attack, the group took to their dark web portal to call out companies that use MOVEit for business file transfers: “Dear Companies who use MOVEit, chance is that we download a lot of your data as part of exceptional exploit.” The statement continues by requesting users of MOVEit software to get in touch with the group using the provided email addresses. By contacting them, users will receive a chat URL that can be used on an anonymized browser network to initiate negotiations. Clop emphasizes this must be done by June 14th; otherwise, the ransomware group will publish the names of those who fail to comply.
The rising tide of supply-chain attacks
In recent years, supply-chain attacks have become a growing concern in the cybersecurity landscape. The attacks on SolarWinds, Log4j and Codecov are notable ones. Supply-chain attacks are especially attractive to cybercriminals because they offer multiple rewards for a single breach.
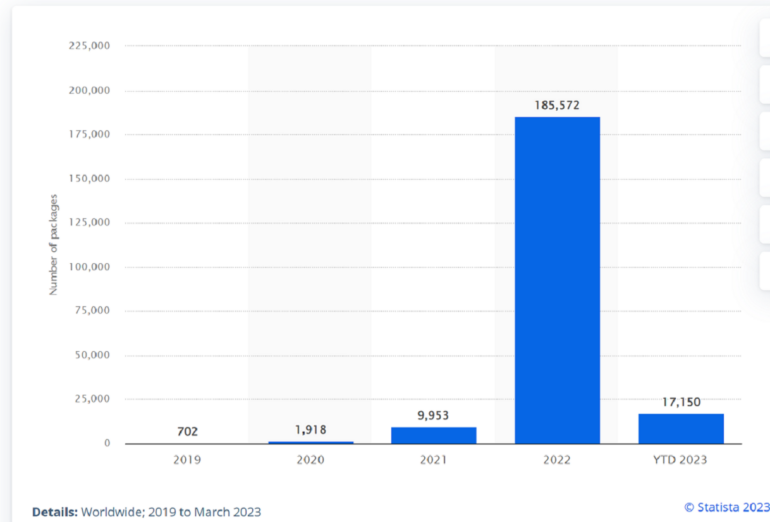
In a recent software supply-chain attacks report, Statista noted the global incidence of software packages impacted by supply-chain attacks had a significant surge between 2019 and 2022, escalating from 702 to 185,572 (Figure A). Furthermore, from January to March 2023, supply chain cyberattacks affected about 17,150 software packages.
Figure A
What organizations can do to mitigate cyberattacks
Given the growing rate of supply-chain attacks, organizations are advised to adopt best practices to help them stay safe. Below is a breakdown of some of the best practices your organization can adopt.
Implement a zero-trust architecture
A zero-trust architecture is designed to operate under the assumption that all network activities are potentially malicious. It adopts a strict approach where every connection request must meet a set of rigorous policies before being granted access to organizational resources.
At its core, a ZTA relies on three key components — a Policy Engine, a Policy Administrator and a Policy Enforcement Point — that work together to serve as the decision-making system, evaluating network traffic based on the rules defined by the Trust Algorithm. By implementing a ZTA, organizations can establish a robust security framework that assumes no inherent trust and verifies each network activity against a set of predefined policies before granting access to valuable resources.
Deploy honeytokens
Honeytokens serve as detection mechanisms that notify organizations of suspicious actions within their network. These deceptive resources mimic valuable data, tricking attackers into believing they have accessed valuable assets. Honeytokens can be in the form of fake database data, email addresses, and executable files. Once attackers interact with these decoy resources, an alert is triggered, notifying the targeted organization of the attempted breach.
By using honeytokens, organizations gain early indications of potential data breaches and gain insights into the specific methods employed by the attackers. With this valuable information, organizations can identify the targeted resources and implement tailored incident response strategies to counter each cyberattack technique effectively.
SEE: Download this security incident response policy from TechRepublic Premium
Conduct regular third-party risk assessments
Sometimes third-party software vendors do not take cybersecurity as seriously as the organizations they serve. This can be counterproductive for organizations that put security above all things. Therefore, organizations should ensure their third-party software suppliers are also purging themselves of every exploitable security vulnerability. They should also assess vendors’ risk assessment reports conducted by a reputable Governance, Risk and Compliance organization. This helps to expose each vendor’s security posture, providing further information on vulnerabilities that should be remediated.
SEE: Download this security risk assessment checklist from TechRepublic Premium
Automate third-party attack surface monitoring
An organization’s attack surface encompasses vulnerabilities, pathways and methods that hackers can exploit to gain unauthorized network access, compromise sensitive data or execute cyberattacks. This attack surface makes the third-party threat landscape more complex. But with an automated attack surface monitoring solution, these complexities can be reduced, thereby making it easier to catch hidden vulnerabilities.Risk management solutions that can help automate third-party attack surface monitoring include OneTrust, Venminder, BitSight and UpGuard.
Apply due diligence when choosing third-party vendors and have strong contractual agreements
Implement a robust due diligence process when selecting third-party vendors or partners. This includes evaluating the vendor’s security controls, policies and practices. Depending on the industry, organizations should check if the vendor meets certain security requirements, such as ISO 27001, NIST SP 800-171 and PCI DSS. This will reveal their commitment to information security standards.
In addition to applying due diligence when choosing a software supplier, organizations should establish solid contractual agreements with their third-party vendors or partners. Clearly outline the security requirements, data protection obligations and consequences for non-compliance. Include provisions for regular audits and assessments to ensure ongoing compliance.

