- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Enable workplace transformation with SASE in four use cases

By: Gabriel Gomane, Sr Product Marketing Manager, HPE Aruba Networking.
The advent of digital transformation has brought about a complete overhaul in the workplace and revolutionized the way we access applications. This transformation can be attributed to four pivotal factors: the emergence of hybrid working, the migration of business applications to the cloud, the rapid proliferation of IoT devices, and the growing concerns surrounding cybersecurity risks.
To enable this transformation, organizations can deploy SASE and tailor their SASE journey to align with their specific security and business goals. They can start their SASE journey by securing remote workers with ZTNA or they can begin by addressing application performance issues in branches with SD-WAN. There are no right or wrong choices, but it’s rather a matter of prioritizing specific use cases.
Start your SASE journey based on business and security goals.
Before everything moved to the cloud, applications were hosted in corporate data centers. The workplace was easier to manage but it had its own challenges: branch offices connected to the data center through MPLS. It was costly, it had a limited bandwidth, and it was difficult to spin up new branch offices. Additionally, when a branch user wanted to access a cloud application, traffic was backhauled to the data center, severely impacting application performance.
Remote workers used to connect to the headquarters through a VPN connection. The downside of VPN is that once connected, users could access any resources in the organization, regardless of their role in the business.
IoT devices were not as many as they are today. However, they posed a significant security risk due to the lack of proper management and the inability to run a security agent, making them vulnerable to potential breaches.
Nowadays, the workplace has totally changed. Most of the applications have moved to the cloud and it is no longer viable to route the cloud application traffic to the data center for security inspection. Employees have become hybrid workers and connect from anywhere accessing sensitive data from untrusted links and from any device. The number of IoT devices have exploded increasing the attack surface and cybersecurity risks.
Here are four critical use cases that enable the transformation of the workplace with SASE.
Use Case 1: Enforce least privilege access to applications with ZTNA
Contrary to VPN, ZTNA (Zero Trust Network Access) enforces least privilege access and segments the network at the application level based on identity, so that users only access the resources they need. It protects data from cyberthreats by masking private resources from the internet, keeping users off the network. With ZTNA, remote workers can connect from anywhere, on any device and over any network.
With agentless ZTNA, organizations also seamlessly onboard third-party users in their network. There’s no need to install a ZTNA agent in laptops, third party users simply log in to a ZTNA web portal with their own credentials. Once authenticated, they can conveniently access the specific applications they require, while other applications or services remain inaccessible to them.
Additionally, with VPN, organizations only had few VPN concentrator geo-locations, creating long backhauls, leading to a poor user experience. Advanced ZTNA solutions provide hundreds of Points of Presence (PoPs), ensuring least latency and enhanced quality of experience.
Use Case 2: Protect against web-based threats with SWG
To protect organizations against web-based threats such as malware, ransomware, phishing and other cyber security risks, a Secure Web Gateway solution (SWG) sits between the user and a website to intercept web traffic.
It performs several security inspections including URL filtering, malicious code detection and web access control. The solution establishes policies that restrict access to specific categories of websites, including adult content, gambling platforms, and sites known to pose significant risks. By enforcing these policies, organizations can maintain a secure and productive browsing environment for their users, while mitigating potential legal, reputational, and security risks.
Real-time threat detection is a critical component of SWG. By continuously monitoring web traffic, the solution can promptly identify and alert organizations to potential security incidents. This proactive approach allows quick responses to mitigate risks and minimize the impact of any potential threats.
Use Case 3: Eliminate data exfiltration with CASB
More sensitive data are now hosted outside the enterprise security perimeter. This data resides in cloud applications, whether they are officially sanctioned or unsanctioned. For example, software developers can put sensitive code in GitHub, or employees can put unauthorized data in Dropbox. This change poses significant challenges for organizations in terms of data security and protection.
Cloud Access Security Broker (CASB) plays a vital role in identifying and detecting sensitive data in cloud applications. It monitors user activity in granular details – what applications have been accessed, when it was accessed, the files that have been downloaded – to prevent data loss and protect the organization against data exfiltration.
Additionally, CASB enables organizations to enforce robust security policies such as authentication and Single Sign On (SSO), and prevents users from using cloud applications that are not authorized by the organization, significantly reducing shadow IT.
Use Case 4: Modernize network in branch offices with SD-WAN
To connect branch offices to the data center, an SD-WAN solution can combine multiple links such as MPLS, Internet and 5G, optimizing network performance. Advanced SD-WAN solutions also use techniques such as Path Conditioning, to overcome the adverse effects of dropped and out-of-order packets that are common with broadband internet and MPLS connections. This provides a private-line-like performance over internet links, enabling organizations to reduce MPLS dependency and quickly spin up new branches.
An advanced SD-WAN can also intelligently steer the traffic to the cloud, based on first-packet identification, avoiding the need to backhaul the traffic to the data center. The traffic from trusted applications, such as Microsoft 365 or RingCentral, is sent directly to the cloud, while other traffic is sent to cloud security services (SSE – Security Service Edge) or to the data center depending on security policies.
Virtual instances of SD-WAN solutions can even be deployed in cloud service providers such as AWS, MS Azure and Google Cloud establishing a resilient connection from the branch office to the cloud. Not only does the connection is optimized, but also it creates an end-to-end segmentation ensuring that users only access cloud applications consistent with their role.
To protect organizations from unsecure IoT devices, advanced secure SD-WANs include next-generation firewall capabilities, enabling IT teams to segment the traffic based on role and identity, isolating the IoT traffic from mission-critical applications. Other firewall features include IDS/IPS and DDoS protection, so that organizations can seamlessly replace branch firewalls, reducing hardware footprint in branch locations.
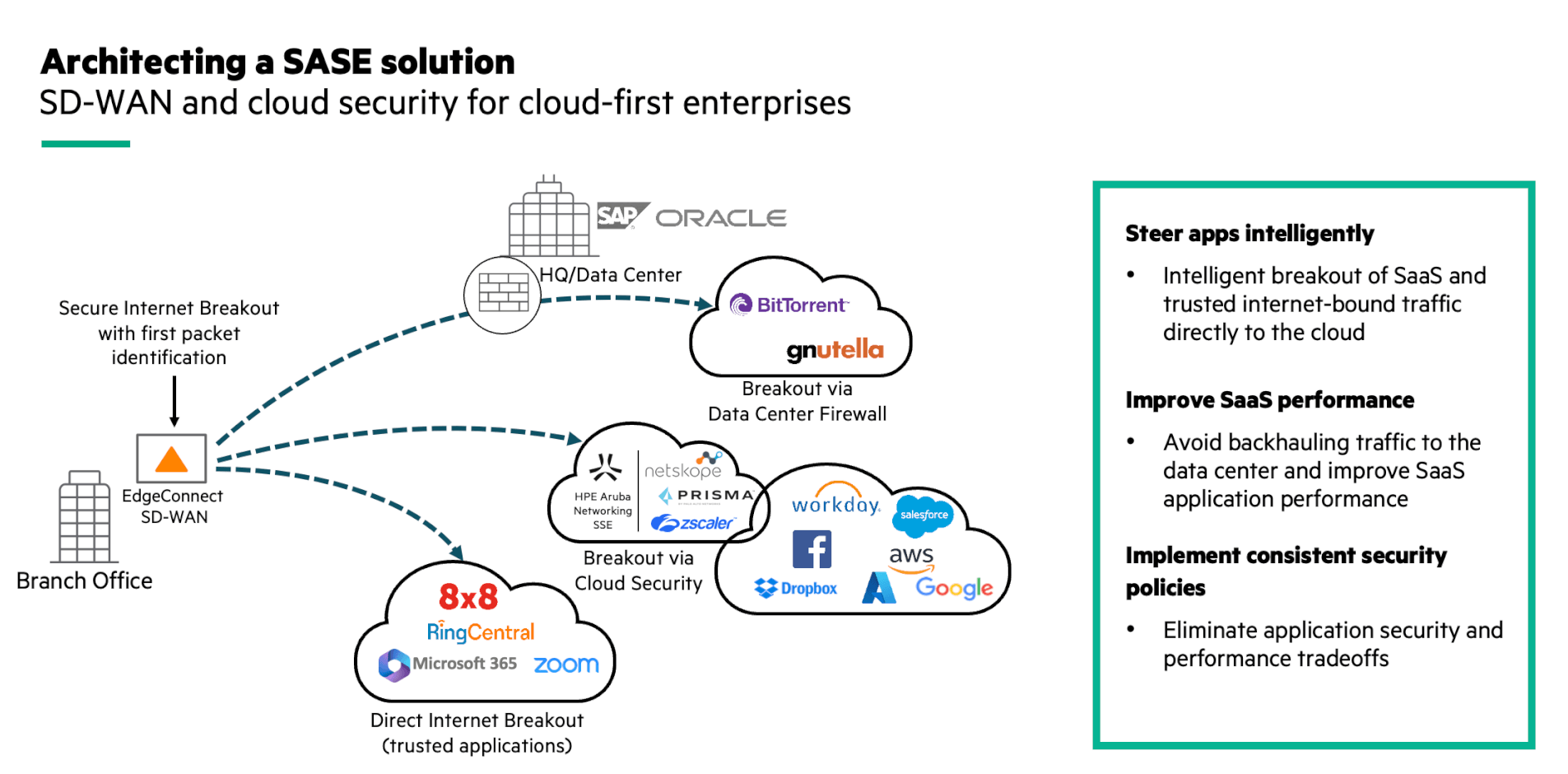
Intelligently steer traffic to the cloud with EdgeConnect SD-WAN.
To summarize, SASE allows organizations to implement a cloud architecture and seamlessly enable hybrid working. With HPE Aruba Networking SASE, users and third-party users can securely connect from anywhere with agent and agentless ZTNA, they are protected against web-based threats with SWG, and sensitive data are securely monitored to prevent data exfiltration with CASB. EdgeConnect SD-WAN provides reliable and business-driven connectivity in branch offices. Additionally, with an embedded next-generation firewall and routing capabilities, organizations can replace legacy routers and firewall, and isolate the unsecure IoT traffic from mission-critical applications. Security policies are managed centrally from a single interface, so that configurations and updates are immediately pushed to remote and branch users.
If you want to learn more, please visit our webpage about HPE Aruba Networking Edge-to-Cloud security solutions.
Other resources:
Copyright © 2023 IDG Communications, Inc.

