- Every dad should build their toolkit with theses 10 DIY gadgets
- Broadcom grows revenues by 20% following VMware purchase, as customers fume about subscription costs
- How global threat actors are weaponizing AI now, according to OpenAI
- The viral Air Purifier Table is my smart home's MVP (and it's on sale for $179)
- Grab the Galaxy S25 Edge for $170 off and get a free Amazon gift card - but act fast
Critical Insight Reports Fewer Cybersecurity Breaches in Health Care, Yet Victim Numbers Are Up in 2023

A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners.
In 2021, a World Economic Forum blog examined the COVID-era spike in health care sector cyber attacks, noting the over 10 million records stolen over the course of a little over a year. The pandemic is over (for now), but the mercury in the cyber thermometer is still rising as recent attacks against such health sector players as Prospect Medical Holdings and HCA Healthcare add to the stack of violated data in 2023.
A new study by cybersecurity firm Critical Insight noted that while the sheer number of breaches against health care facilities is actually down, there is a spike in the number of people who have been affected by attacks as well as an increase in supply chain and third-party targets. Also, attackers are focusing more on extortion, not merely denial of service tactics, according to the study.
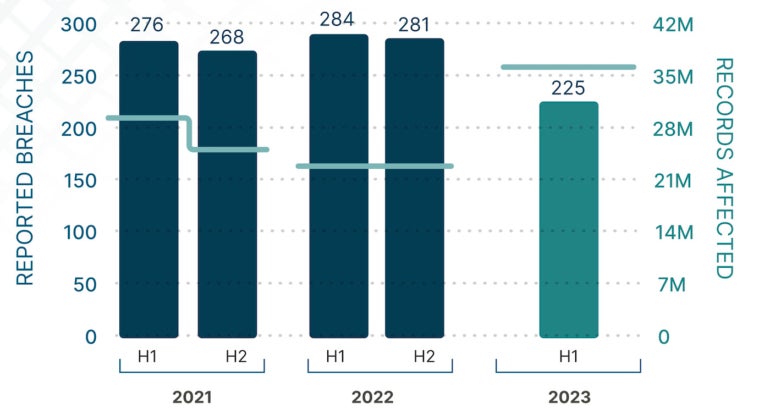
In fact, the new 2023 Healthcare Data Cyber Breach Report shows, paradoxically, that while the year is on track to have the fewest breaches since 2019, individual records compromised are the highest ever in a six-month period (Figure A).
Figure A
Jump to:
Breaches down, but number of individual records compromised, way up
According to the report, based on an analysis of data breaches reported by health care organizations to the U.S. Department of Health and Human Services, total breaches of organizations dropped 15% in the first six months this year, versus the second half of 2022.
However, there was a 31% increase in the number of individual records compromised, affecting 40 million people (74% of the total number of individuals affected in 2022 and the highest number on record for a six month period according to the firm), versus 31 million in the second half of 2022.
Michael Hamilton, CISO of Critical Insight, said attackers looking for bigger ROI with reduced risk explains the shift to bigger targets and a shortening long tail of smaller targets, or those with limited potential. “The changing priorities of the attackers have to do with minimizing their own risk and maximizing their own outcomes. If they can attack one organization and get a better ROI, they will do that. That’s what we are seeing,” he said.
The average number of individuals affected per breach also hit an all-time high of 131,000, reflecting the lower number of breaches and the impact of the large breaches on the overall average.
Among the victim organizations:
- Dental benefits administrator, Managed Care of North America saw 8.9 million individual records compromised.
- PharMerica, a pharmacy services provider, had 5.8 million records exposed in a ransomware attack.
These two breaches were the third- and fourth-largest ever reported, according to Critical Insights.
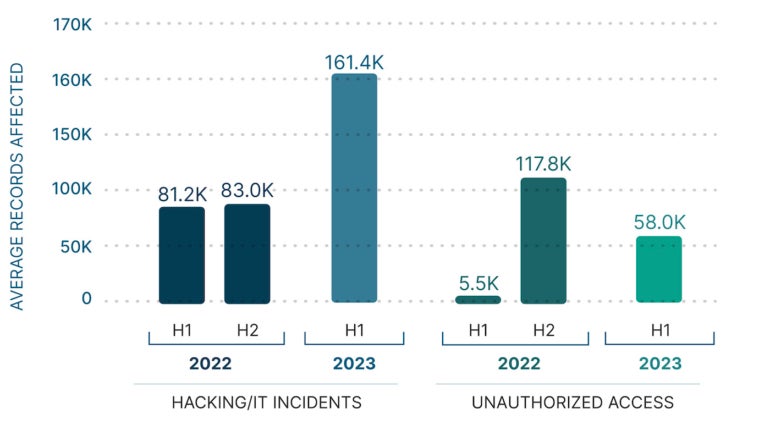
Hacking and IT incidents accounted for 73% of breaches, according to the report, whose authors said attackers’ focus on network server vulnerabilities has partly to do with organizations’ hardening of their email endpoints. According to the report, network server breaches were responsible for 97% of individual records affected, versus only 2% of records compromised by email breaches (Figure B).
Figure B
Third-party vulnerabilities a rising threat vector
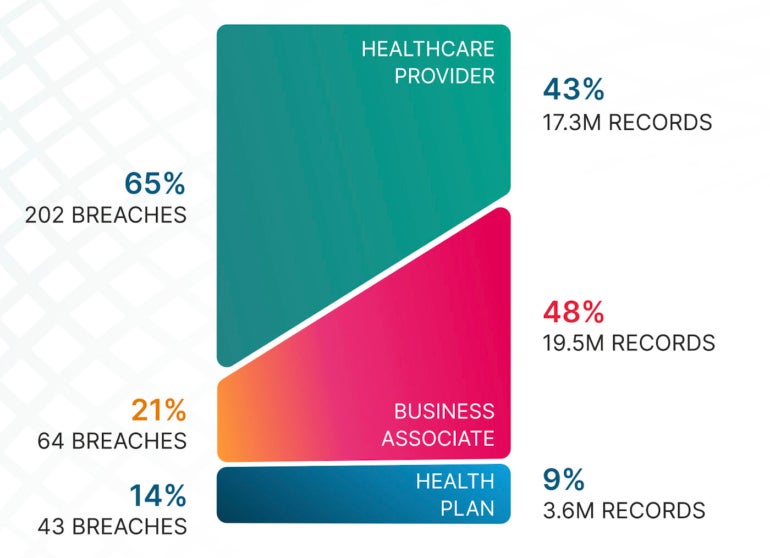
Hackers are also moving laterally to attack third-party organizations. According to the study, attacks against third-party partners were “significantly higher than individuals affected in healthcare provider and health plan-related breaches.” Critical Insight reported that of the 40 million exposed records, 48% were linked to business associates, while 43% were associated with healthcare providers (Figure C).
Figure C
One example cited by Critical Insights of an attack via third-party vulnerabilities was supplementary benefits company NationsBenefits Holdings, which disclosed that a breach originating from its own third-party cybersecurity services provider impacted 3 million individuals in its system.
“Our report found that hackers are increasingly targeting the weakest links and vulnerable points in the supply chain, specifically business associates or third-party companies, that offer services to healthcare organizations emphasizing the importance of effective incident response planning and proactive defense strategies,” said John Delano, Healthcare Cybersecurity Strategist at Critical Insight and VP at Christ’s Health, in a statement.
Hospitals, clinics, physician groups are top targets
The report authors noted that specialty clinics suffered the most hacking and IT incidents, followed by:
- Hospital systems
- Physician groups
- Services and supplies
- Behavioral health
- Outpatient facilities
- Home care service providers
The report also noted that a single successful large-scale attack can skew these findings, noting that only 4% of individuals in the services and supplies category were affected by attacks in 2021, jumping to 19% in the first half of 2022. The PharMerica attack by itself drove that percentage to 42% this year. Similarly, according to the report, the Regal Medical Group attack, affecting 3.4 million individual records, hoisted the physician group microsegment from 4% in the second half of 2022 to 22% in the first half of 2023.
Enzo Clinical Labs reported a breach involving nearly 2.5 million individuals, pushing the diagnostic segment from 3% in the second half of 2022 to 15% in the first half of 2023.
Health organizations should take pulses, including partners’
Critical Insights suggest organizations should:
- Begin with an incident response plan and a NIST-CSF-based risk assessment to build a multi-year strategy.
- Track the cyber hygiene of its critical partners essential to maintaining a more secure environment.
- Place robust focus on safeguarding third-party vendors, business associates, and suppliers from vulnerabilities.
- Ensure support from the board, emphasizing the most critical impact for the investment.

