- My search for the best MacBook docking station is over. This one can power it all
- This $500 Motorola proves you don't need to spend more on flagship phones
- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
- I replaced my Linux system with this $200 Windows mini PC - and it left me impressed
- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
Five reasons to adopt a single-vendor SASE approach

By: Gabriel Gomane, Senior Product Marketing Manager at HPE Aruba Networking
As organizations are moving to a cloud-centric architecture, where most applications reside in the cloud and the demand for hybrid work environment increases, security must evolve in parallel:
- Legacy VPNs have often provided poor user experience. Additionally, usage of VPNs without granular controls could over-extend network privilege, granting users more access to resources than necessary, increasing security risks.
- Traditional network architectures routed application traffic to the data center for security inspection, which is no longer practical, and impacted application performance since most applications now reside in the cloud.
- With data increasingly hosted in SaaS applications, organizations need to take extra steps to protect their data. Sensitive data can indeed be stored in both sanctioned and unsanctioned cloud applications (or shadow IT), and may travel over unsecured links, leading to potential risk of data loss.
- Employees are vulnerable to web-based threats such as phishing attacks and ransomware when browsing the internet or simply accessing emails.
- The explosion of IoT devices in the recent years have significantly increased the attack surface. However, IoT devices are often built on a simple design and lack sophisticated security mechanisms.
- Finally, organizations must comply with regulatory mandates such as HIPAA or GDPR but often lack the essentials tools and comprehensive reports needed to demonstrate compliance.
SASE, Secure Access Service Edge, helps tackle these challenges by combining SD-WAN with SSE (Security Service Edge).
SASE combines advanced WAN edge capabilities with Security Service Edge (SSE)
- SD-WAN leverages network virtualization to combine multiple links such as MPLS, Internet and 5G, reduce costs and improve application performance. It also eliminates the need to backhaul SaaS traffic to the data center, based on intelligent steering.
- SSE (Security Service Edge) includes advanced cloud-delivered security services. These include ZTNA (Zero Trust Network Access), SWG (Secure Web Gateway) and CASB (Cloud Access Security Broker). ZTNA enforces least privilege access at the application level based on identity, ensuring that users and third-party users only access the resources they need. SWG safeguards against web-based threats like ransomware and phishing by monitoring all web traffic through URL and content filtering. CASB identifies sensitive data, prevents data loss, and detects shadow IT.
Organizations can choose between a single-vendor SASE approach and a multi-vendor SASE approach. While a multi-vendor approach allows for selecting best-of-breed solutions for specific aspect of SASE, some organizations prefer the simplicity and the ease of deployment of a single-vendor SASE solution, as well as the single point of contact for support, and the simpler licensing.
In fact, Gartner predicts that by 2025, 50% of SD-WAN purchases will be part of a single-vendor SASE offering, up from less than 10% in 2021[1].
Five key trends explain the preference for a single-vendor SASE solution:
1. Cloud-native architecture and scalability
A single-vendor SASE solution is designed with a cloud-native architecture, leveraging the scalability and agility of cloud computing. This architecture enables organizations to dynamically allocate resources based on traffic demand, enabling a more efficient and adaptable network.
Additionally, achieving a global network presence through geographically distributed Point of Presence (PoPs) is essential to ensure consistent performance and low latency, regardless of user location. A single-vendor SASE simplifies the management of these points of presence, eliminating the need for multiple points of presence required by a multi-vendor SASE approach.
2. Unified policy management and granular control
Contrary to a multi-vendor SASE approach, a single-vendor SASE solution enables IT administrators to manage all security policies from a single interface. This interface encompasses policies related to SWG, CASB, DLP and ZTNA. This approach streamlines operations, reduces complexity, and helps organizations to deploy and enforce consistent policies effectively. Additionally, this approach provides organizations with a faster response to security threats, enabling the adjustment of security policies in real-time across the entire fabric during security incidents. Importantly, this approach also enables IT administrators to enforce granular access control based on users, identity, and devices.
3. Centralized UI, comprehensive dashboards
Beyond unified policy management, a single-vendor SASE solution provides IT teams with the ability to manage all network and security operations in a centralized user interface. It offers an enhanced visibility into network traffic, security events and policy enforcement, supporting better threat detection and incident response. Additionally, it enhances reporting capabilities, providing organizations with the means to demonstrate compliance with regulatory requirements and industry standards.
4. Combined SASE capabilities
With a single-vendor SASE solution, organizations can easily combine multiple SASE capabilities to enhance their security posture. For example, SWG and CASB can be combined with DLP to monitor user activities and protect sensitive data from leaking out to the Internet and SaaS applications. Also, SWG and CASB use SSL decryption to analyze HTTPS traffic. By using a single-vendor SASE solution, SSL inspection is performed only once, improving performance, and reducing complexity. Furthermore, by combining SWG and CASB with ZTNA, organizations can enforce even more granular controls over web access, allowing or denying access to specific websites or cloud applications based on user identity.
5. Universal Zero Trust Access
Universal Zero Trust Access represents a fundamental shift in the approach to network security. It allows users and devices to securely access resources from any location, whether they are in the office, working remotely or on the go. Central to this approach is the principle of least-privilege access, which segments traffic based on identity and role, ensuring that users and devices only access the resources essential to their tasks, reducing the attack surface. Additionally, private resources can be masked from the internet, keeping users off the network. Third-party contractors can easily access the network with an agentless ZTNA solution, eliminating the need to install a security agent on their device.
As a user connects to the corporate network, the integration of NAC (Network Access Control) with ZTNA becomes instrumental. NAC verifies the security posture of devices through health checks before granting network access. These health assessments on specific devices ensure that they adhere to corporate anti-virus, anti-spyware and firewall policies, enabling organizations to grant access to users and devices based on their inherent risk.
In branch offices, SD-WAN plays a pivotal role in connecting branch users to the headquarters. It intelligently steers traffic to the cloud while eliminating the need to backhaul traffic to the data center. Advanced SD-WAN solutions can even provide built-in next-generation firewall capabilities, with IDS/IPS and fine-grained segmentation, to enforce Zero Trust access. As a new user or device connects to the corporate network and registers, SD-WAN—coupled with Network Access Control—propagates security policy information and any updates related to the user, device type, role and security posture to the entire network, to enforce role-based segmentation across the LAN and the WAN. Additionally, because IoT devices are agentless, it is not possible to run a third-party VPN or ZTNA client on them. This approach helps secure IoT devices by segmenting the network based on identity from other traffic while ensuring users and IoT devices reach destination consistent with their role in the business.
In conclusion, the adoption of a single-vendor SASE approach presents organizations with a robust strategy to address the multiple challenges of modern network security. By seamlessly integrating SD-WAN and SSE components, organizations can effectively secure their network, accelerate deployment, simplify adoption, and thrive in an ever-evolving digital landscape.
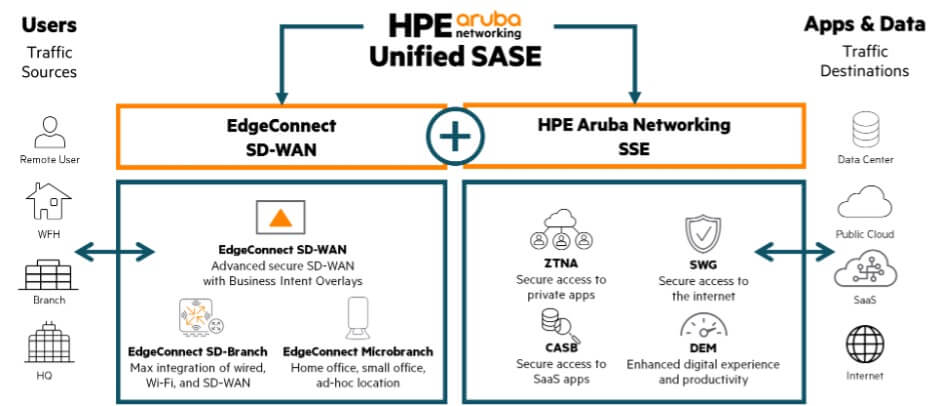
HPE Aruba Networking’s unified SASE platform
HPE Aruba Networking’s unified SASE combines EdgeConnect SD-WAN with HPE Aruba Networking SSE. HPE Aruba Networking SSE provides advanced security functions, such as ZTNA, SWG, CASB as well as DEM (Digital Experience Monitoring).
EdgeConnect SD-WAN is a secure SD-WAN solution with a built-in next-generation firewall that seamlessly integrates with HPE Aruba Networking SSE. HPE (Aruba) has been named a leader in the 2023 Gartner® Magic Quadrant™ for SD-WAN for the sixth consecutive year. This follows the strong results announced from the IDC MarketScape for the worldwide SD-WAN infrastructure 2023 vendor assessment, in which HPE Aruba Networking was placed as a leader.
To learn more, please visit our webpage on unified SASE.
And for more information on how to use SASE and Zero Trust Security to help your users stay safe online, visit our Cybersecurity Awareness Month resource hub.
Other resources:
[1] 2022 Strategic Roadmap for SASE Convergence, Gartner, June 2022

