- Walmart's drone delivery spreads its wings to 100 more stores - is yours one?
- Meta Ray-Bans for 20% off is a great deal on one of my favorite products
- Control content chaos without compromising security
- Apple Mail freezing after updating to iOS 18.5? Here's a fix you can try
- Scattered Spider Uses Tech Vendor Impersonation to Target Helpdesks
Booking.com Customers Scammed in Novel Social Engineering Campaign
Booking.com customers are being targeted by a novel social engineering campaign, which is “paying serious dividends” for cybercriminals, according to new research by Secureworks.
The researchers said the campaign, which they believe has been running for at least a year, begins by deploying the Vidar infostealer to gain access partner hotels’ Booking.com credentials. This information is then used to send phishing emails to Booking.com customers and trick them into handing over their payment details, in many cases leading to money being stolen.
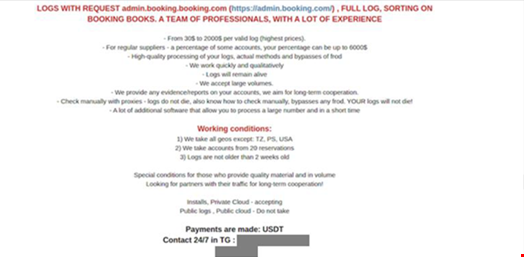
The scam is proving so fruitful that sales of Booking.com portal credentials are commanding sale prices of up to $2000 in two cybercrime forums, according to the researchers.
How the Scam Works
In an October 2023 attack investigated by Secureworks, the threat actor initially emailed a member of the hotel’s operations staff requesting help to find an ID document they claimed to have lost. The message did not include an attachment or malicious links.
With no reason to be suspicious, the employee responded to the email and requested additional information to help them assist the fake customer.
Later that week, the threat actor emailed back, identifying the ID as a passport and stating that they strongly believed they had left it at the hotel. They included a link to a Google Drive URL that purportedly hosted photos of the passport and the guest’s check-in details.
When the hotel employee clicked on the link, a ZIP archive was downloaded to the computer’s desktop. This was identified by Microsoft Defender as the Vidar Infostealer, which executed on the device following multiple failed attempts.
Analyzing the contents of the file, Secureworks observed that this Vidar sample was configured to only steal passwords.
Public reports show that almost identical emails containing a Google Drive URL were sent to other victims of this campaign.
A day after the malware was executed, a hotel employee observed that multiple messages had been sent to upcoming guests from the hotel’s Booking.com account. A few hours later, customers started complaining that money had been taken from their accounts. This suggests the attacker deployed Vidar to steal the hotel’s Booking.com credentials and use them to access the account.
Secureworks said this activity is part of a broader campaign that started at least a year ago, observing that customers of multiple properties received email or in-app messages from Booking.com requesting confirmation of payment details for upcoming stays. These messages contained malicious URLs for inputting these details, and the attackers used this information to withdraw money from the victims’ accounts.
The researchers believe the threat actors stole credentials to the admin.booking.com property management portal directly from the properties, enabling them to send legitimate looking messages via the official app and email address, noreply@booking.com.
A Disturbing Twist
In a variation on this Booking.com campaign, it has been reported that an attacker socially-engineered a hotel in Scotland under the guise of a guest with a sick child.
Jude McCorry, CEO of Cyber Fraud Centre Scotland, said the scam began with the threat actor calling the hotel to say they were planning to stay at the property with a child with serious allergies, and would send a document with full details for simplicity. The receptionist immediately opened the document on receipt, which released the malware and enabled the attacker to access all booking.com bookings.
All the guests were then messaged with demands to pay the full amount for bookings on behalf of the hotel.
McCorry noted that this example shows that some cybercriminals are willing to go to any level to increase the chances of their scam working. “While using social engineering in this way isn’t necessarily new, using the front of a sick child is a low even for these criminals, but doing what we do, nothing surprises us.
“We feel for the victims who fall for this – the victim here was the receptionist who was going above and beyond to look after who she thought was a future guest who needed additional attention,” she outlined.
An Effective Campaign
Rafe Pilling, director of threat intelligence for Secureworks Counter Threat Unit, explained that the scam has a high success rate as it targets genuine Booking.com customers and appears to come from a trusted source.
“It’s social engineering at its best. Firstly, targeting hotel employees who want to help their customers so will act swiftly. And then targeting holidays, one of the biggest investments people make. When an email comes through from a trusted supplier requiring action or a holiday will be cancelled, it’s understandable that someone might respond without pausing to think,” he commented.
Additionally, the Secureworks report noted that the language in the emails “was a better standard of English than average phishing emails.”
Pilling added that as the attack chain so targeted and on such a large scale, it is a difficult scam to close down because it relies on partner hotels having effective controls in place as well as employees and customers being really aware of phishing threats.
“The research demonstrates the whole ‘kill chain’ of threat activity. From the demand for Booking.com credentials, to sales of the Vidar infostealer, to the complaints from victims,” he noted.
Speaking to Infosecurity, Pilling said that Secureworks has observed threat actors discussing targeting other third-party booking services on criminal forums, “Airbnb being another example where there is interest in credentials.”
How to Tackle this Campaign
Secureworks set out the following advice for organizations in the hospitality sector and customers who use Booking.com services to protect themselves against this scam.
Hospitality organizations:
- Make employees aware of this campaign and the signs in incoming emails
- Implement multi-factor authentication (MFA) on Booking.com accounts
- Use available controls to review and restrict access to systems
Customers:
- Be wary of emails or app messages requesting payment details, even if they appear to be from a legitimate source
- If anything feels off anytime you are asked to put your username and password, or credit card information, into a form, contact the business via another route to validate the request

