- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Google Cloud's Cybersecurity Predictions of 2024 and Look Back at 2023

Generative AI can be used by attackers, but security professionals shouldn’t lose sleep over it, according to a Google Cloud threat intelligence analyst. Find out why.
Google Cloud’s team recently spoke about the most notable cybersecurity threats of 2023 — multi-faceted extortion and zero-day exploitation — and predicted more zero-day attacks in 2024, during two public, virtual sessions. Plus, Google predicts that both attackers and defenders will continue to use generative AI. However, generative AI probably won’t create its own malware in 2024.
Jump to:
Two most notable cybersecurity threats of 2023
The two most notable cybersecurity threats of 2023, according to Google Cloud’s Luke McNamara, principal trust and safety analyst, were multi-faceted extortion (also known as double extortion) and zero-day exploitation.
Multi-faceted exploitation
Multi-faceted exploitation includes ransomware and data theft, although the number of ransomware attacks tracked by Google Cloud fell in 2023. The most common ransomware families used in multi-faceted exploitation attacks were LockBit, Clop and ALPHV.
Most ransomware attacks initially stemmed from stolen credentials. Brute force attacks and phishing were the next most common initial infection vectors for ransomware.
SEE: Know the warning signs if someone else has accessed your Google account. (TechRepublic)
Attackers increasingly put stolen credentials up for sale on data leak sites, McNamara said. “This past quarter (Q3 2023) we saw the highest number of postings to DLS sites since we started tracking this in 2020,” McNamara said.
Many attackers are industry-agnostic, but “Quarter over quarter, manufacturing seems to be particularly hit and impacted disproportionately,” McNamara said. “That’s where we’re seeing a lot of the activity in terms of volume.”
Zero-day exploitation
Zero-day exploitation is defined by Google Cloud as vulnerabilities with no known patches that threat actors are actively exploiting. In 2023, Google Cloud Security tracked 89 such attacks (Figure A), surpassing the previous high of 2021.
Figure A
Many zero-day threats are nation-state affiliated or sponsored. The second most common motivation among threat actors using zero-day threats is to acquire money.
SEE: What the Cisco Talos Year in Review report revealed (TechRepublic)
Google Cloud’s 2024 cybersecurity forecast
Andrew Kopcienski, principal threat intelligence analyst at Google’s Mandiant Communication Center, talked about nation-state threat actors, zero-day attacks, movement between cloud environments and credential theft during his presentation about cyber threats in 2024. In particular, China and Russia are focusing on zero-day attacks, he said.
“We fully expect to see a lot more zero day use in 2024 by not just nation-state sponsored attackers but cyber criminals as well,” said Kopcienski. “Zero days are one of the best methods attackers have to remain undetected once they get into a network.”
China-sponsored threat actors
China-sponsored actors have focused on developing capabilities in finding and using zero days and botnets to remain undetected, Kopcienski said. Google Cloud expects China’s cyber threat efforts to focus on high-tech fields like chip development.
Russian-sponsored espionage
Russian espionage focused on Ukraine has been a problem, he said. Google Cloud found Russia has conducted campaigns outside Ukraine as well, but those mostly focus on gaining strategic information regarding Ukraine, Kopcienski said. Russian-sponsored attackers use “living off the land” attacks that do not require malware; instead, they abuse native capabilities, and their traffic looks like native traffic. Google Cloud expects more attacks from Russian-backed actors in 2024, mostly focused on victims inside Ukraine or related to Ukraine.
North Korean-sponsored threat actors
Google Cloud also looked closely at nation-state actors associated with North Korea.
“They have developed a scrappy capability to launch software supply chain attacks,” Kopcienski said.
North Korea was the first known nation-state actor to use “cascading” software supply chain attacks, which piggybacked off each other. Many of these attacks are about stealing cryptocurrency or companies conducting cryptocurrency operations. Google Cloud expects to see North Korea-affiliated threat actors’ attacks broaden in 2024.
Credential theft and extortion
Another concern for 2024 is extortion. “Credential theft (Figure B) is the name of the game … that has become the most drastic and most popular measure a lot of these attackers are using,” Kopcienski said.
Figure B
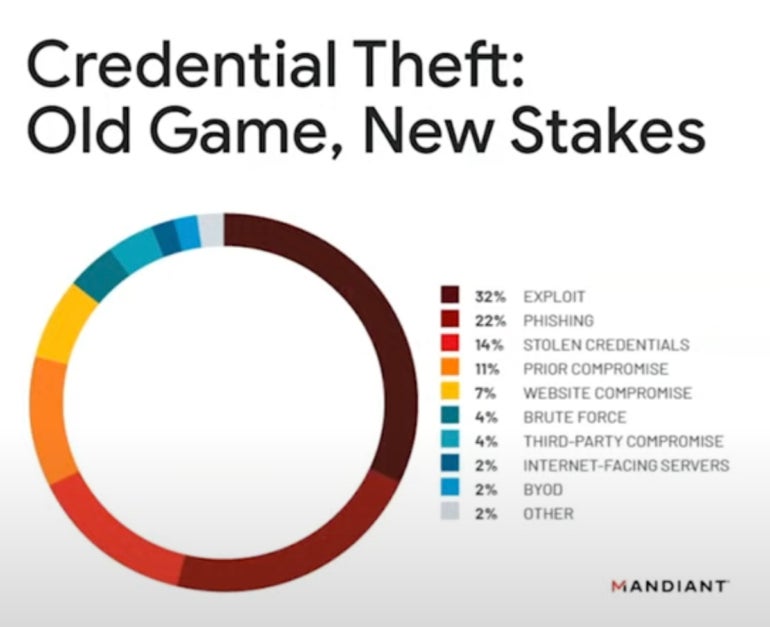
“Into 2024, we expect to see a focus on data leak sites, especially by extortion actors,” he said.
Movement between cloud environments
Attackers in 2024 may use tactics, techniques and procedures that allow them to travel across different cloud environments, likely due to the increasing use of cloud and hybrid environments.
How generative AI has and will affect cybersecurity in 2023 and 2024
Attackers can use generative AI to create text, voice messages and imagery, and Google Cloud expects this to become more common.
“AI is enabling particular kinds of malicious attackers, mostly in disinformation campaigns. We are very concerned going into next year about the impact of disinformation that has been augmented by AI, especially when it comes to the 2024 election,” said Kopcienski.
In 2023, generative AI has been used by attackers and defenders. In 2024, AI may be used to increase the scale of attacks, such as by adopting AI in call centers running ransomware negotiations.
Generative AI might be able to create malware at some point in the future, but Kopcuenski said not to expect that to happen as soon as 2024. He recommends cybersecurity professionals “remain grounded” and not lose sleep when it comes to generative AI. Many of its threats are “hypothetical,” he said.
“There’s a lot of hype and disinformation out there already about what AI can and can’t do. … (AI is) not an overwhelming revolution in terms of the threats being posed,” he said.

