10 tips for protecting your cloud data and accounts

As more organizations migrate to the cloud, cybercriminals are taking advantage of the vulnerabilities in online apps, says Netskope.
Image: danijelala, Getty Images/iStockPhoto
The quest for digital transformation has been driving more organizations to move their data and other resources to the cloud. The coronavirus pandemic and the abrupt shift to remote work have put these cloud migration initiatives in even higher gear. But this quick transition has naturally caught the eye of cybercriminals who are exploiting any weaknesses in cloud-based access to deploy malware.
SEE: 6 enterprise security software options to keep your organization safe (TechRepublic)
Released Wednesday by security software provider Netskope, the new “Cloud and Threat Report” looks at the vulnerabilities among cloud apps and offers 10 tips for organizations to better protect their online assets.
The average number of cloud apps in use among enterprise companies rose by 20% last year, and cloud activity now accounts for 53% of secure web gateway traffic, Netskope said. However, this greater reliance on the cloud carries with it certain risks. Organizations with 500 to 2,000 employees now use on average around 690 distinct cloud apps each month, 97% of which are considered shadow IT apps adopted by various departments and users.
The percentage of all malware being delivered via a cloud app rose to 61% in 2020 from 48% the previous year, according to the report. Cybercriminals tend to favor apps that are popular among enterprise users. As one example, the GuLoader Trojan downloader has used Microsoft OneDrive and Google Drive to deliver its malicious payloads.
Among the apps analyzed in the report, almost 50% carry a “Poor” Cloud Confidence Index (CCI) rating from Netskope. Based on more than 50 different attributes in the areas of security, privacy, financial viability and other measures, the low score indicates apps that should be avoided by enterprise customers. The top five apps to which enterprise users upload data and that garnered a poor rating are: 1) Yahoo Mail; 2) ILovePdf; 3) PDF to PNG; 4) PDF2Go.com; and 5) AOL Mail.
Cybercriminals are also increasingly hiding Trojans in Microsoft Office documents to kick off ransomware campaigns and other types of attacks. At the end of 2020, malicious Office documents accounted for 27% of all malware downloads detected by Netskope, up from 17% at the start of the year.
Another type of security risk occurs when remote workers store sensitive data in personal apps. Some 83% of users tap into personal versions of cloud apps on company-managed devices to which they upload an average of 20 files each month.
The top corporate apps from which users copy data to personal instances are: 1) Microsoft OneDrive; 2) Box; 3) Google Gmail; 4) Microsoft SharePoint; and 5) Google Drive. The top personal apps to which they copy that sensitive data are: 1) Microsoft OneDrive; 2) Google Drive; 3) Google Gmail; 4) iCloud; and 5) WeTransfer. Popular types of files that get copied this way are PDFs, Microsoft Office documents, source code files, images and zip files.
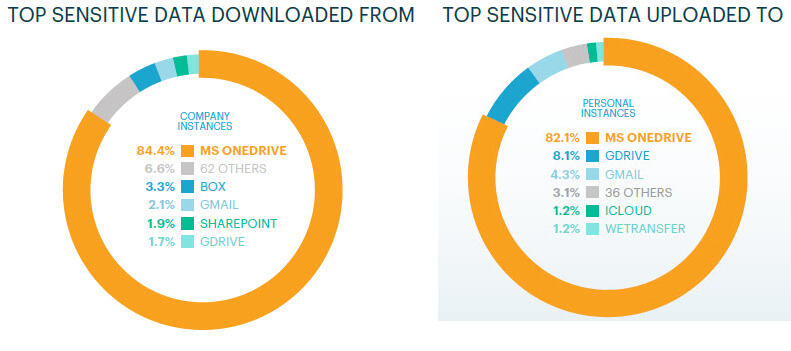
Image: Netskope
The credentials for cloud apps are a tempting target for cyberattacks, with 36% of all phishing campaigns in last year’s third quarter aiming to capture such credentials. Further, more attackers are using cloud apps to launch their phishing attacks as a way to circumvent traditional security measures.
To protect your organization from some of the security threats of cloud apps and services, Netskope offers the following 10 tips:
- Use strong authentication and access controls (e.g., SSO, MFA, etc.) for both managed and unmanaged apps.
- Use adaptive access controls based on the user, app, instance, device, location, data and destination to selectively grant access to specific activities.
- Employ Zero Trust network access to private apps in data centers and public cloud services to reduce the exposure of apps and limit their lateral network movement.
- Continuously assess the security of public cloud services to detect misconfigurations and publicly exposed data.
- Analyze managed and unmanaged cloud apps for suspicious user traffic.
- Selectively and safely enable cloud apps based on a third-party risk assessment.
- Coach users on safe behavior to protect themselves and company data. For example, if a user wants to use an app that has a poor risk rating, advise them of safer alternatives with higher risk ratings.
- Set up granular policy controls for data protection including data movement to and from apps, instances, users, websites, devices and locations.
- Use cloud data protection (DLP) to safeguard sensitive data from internal and external threats.
- Analyze the behavior of security anomalies, events and alerts.


