- How global threat actors are weaponizing AI now, according to OpenAI
- The viral Air Purifier Table is my smart home's MVP (and it's on sale for $179)
- Grab the Galaxy S25 Edge for $170 off and get a free Amazon gift card - but act fast
- How I learned to stop worrying and love my health tracker
- I found a free iPhone 16 deal that doesn't require a trade-in (and applies to Pro models, too)
Android Phishing Scam Using Malware-as-a-Service on the Rise in India | McAfee Blog

Authored by ZePeng Chen and Wenfeng Yu
McAfee Mobile Research Team has observed an active scam malware campaign targeting Android users in India. This malware has gone through three stages. The first one is the development stage, from March 2023 to July 2023, during which a couple of applications were created each month. The second is the expansion stage, from August 2023 to October 2023, during which dozens of applications were created each month. The third is the active stage, from September 2023 to the present, during which hundreds of applications were created each month. According to McAfee’s detection telemetry data, this malware has accumulated over 800 applications and has infected more than 3,700 Android devices. The campaign is still ongoing, and the number of infected devices will continue to rise.
Malware developers create phishing pages for scenarios that are easy to deceive, such as electricity bill payments, hospital appointments, and courier package bookings. Developers use different applications to load different phishing pages, which are eventually sold to scammers. In our research, more than 100 unique phishing URLs and more than 100 unique C2 URLs are created in these malicious applications. It means that each scammer can carry out scam activities independently.
Scammers use malware to attack victims. They typically contact victims via phone, text, email, or social applications to inform them that they need to reschedule services. This kind of fraud attack is a typical and effective fraud method. As a result, victims are asked to download a specific app, and submit personal information. There was a report where an Indian woman downloaded malware from a link in WhatsApp and about ₹98,000 was stolen from her. We were not able to confirm if is the same malware, but it is just one example of how these malicious applications can be distributed directly via WhatsApp.
The attack scenario appears credible, many victims do not doubt the scammers’ intentions. Following the instructions provided, they download and installed the app. In the app, victims are induced to submit sensitive information such as personal phone numbers, addresses, bank card numbers, and passwords. Once this information falls into the hands of scammers, they can easily steal funds from the victim’s bank account.
The malware not only steals victims’ bank account information via phishing web pages but also steals SMS messages on victims’ devices. Because of the stolen information, even if the bank account supports OTP authentication, the scammer can transfer all the funds. The malware uses legitimate platforms to deploy phishing pages to make it appear more trustworthy to evade detection.
McAfee Mobile Security detects this threat as Android/SmsSpy. For more information, and to get fully protected, visit McAfee Mobile Security.
Malware-as-a-Service (MaaS)
We discovered that these phishing pages and malware were being sold as a service by a cyber group named ELVIA INFOTECH. A distinct difference between this malware and others is that the apps sold have a valid expiration date. When the expiration date is reached, some application links will redirect to a payment notification page. The notification is clearly to request the purchaser to pay a fee to restore the use of the malware.
Figure 1. Payment notification.
We also discovered that the cybercriminal group was selling malware in a Telegram group. Based on these observations, we believe that ELVIA INFOTECH is a professional cybercriminal organization engaged in the development, maintenance, and sale of malware and phishing websites.
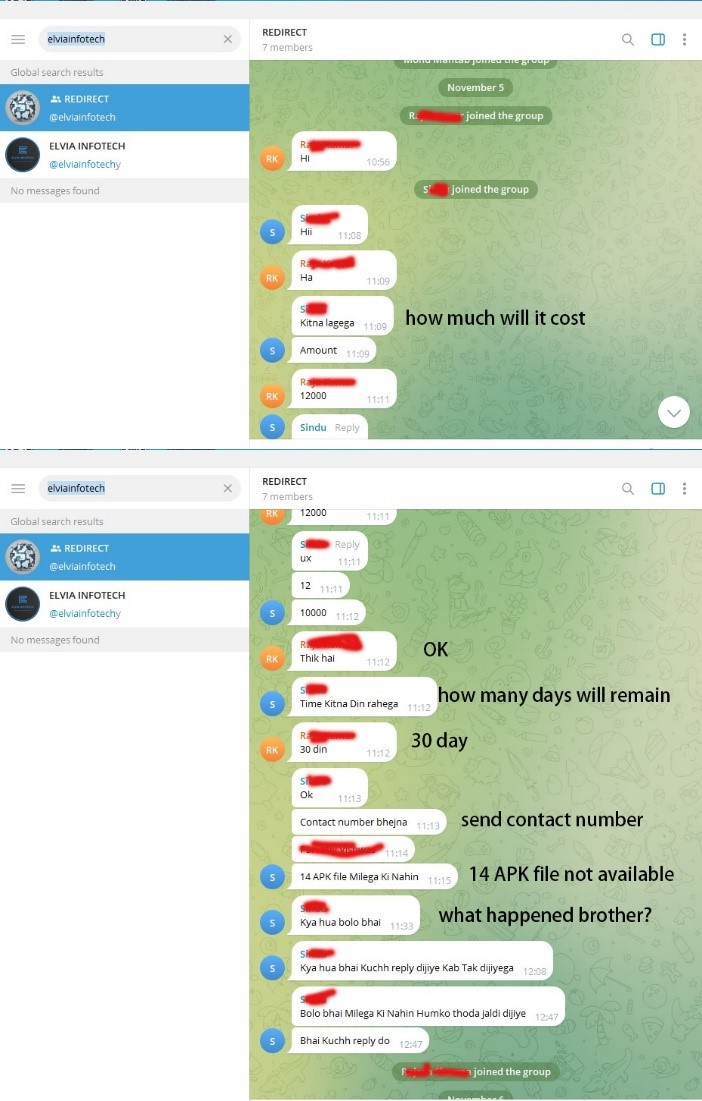
Figure 2. Telegram Group conversation.
Malware Analysis
This malware has been maintained and recently updated, and hundreds of malicious applications were created. They like to use the file names such as “CustomerSupport.apk”, “Mahavitaran Bill Update.apk”, “Appointment Booking.apk”, “Hospital Support.apk”, “Emergency Courier.apk” and the application names such as “Customer Support”, “Blue Dart”, “Hospital Support”,” Emergency Courier” to trick victims, below are some applications’ names and icons.

Figure 3. Some applications’ names and icons
Not only do they pretend to be “Customer Support”, but they also pretend to be popular courier companies like “Blue Dart” in India, but they also target utility companies like “Mahavitaran” (Power Corporation of India).
Once victims click the fake icon, the application will be launched and start to attack victims.
1. Loading Phishing Pages
The phishing page loads once the application is launched. It will disguise itself as a page of various legitimate services, making victims believe that they are visiting a legitimate service website. Here, victims are tricked into providing sensitive information such as name, address, phone number, bank card number, and password. However, once submitted, this information falls into the hands of scammers, allowing them to easily access and control the victim’s bank account.
We found that most of this attack campaign impersonated carrier package delivery companies.

Figure 4. Phishing Pages Load Once App Launches
The malware developers also designed different phishing pages for different applications to deceive victims in different scenarios that exploit electricity bill payments and hospital appointments.
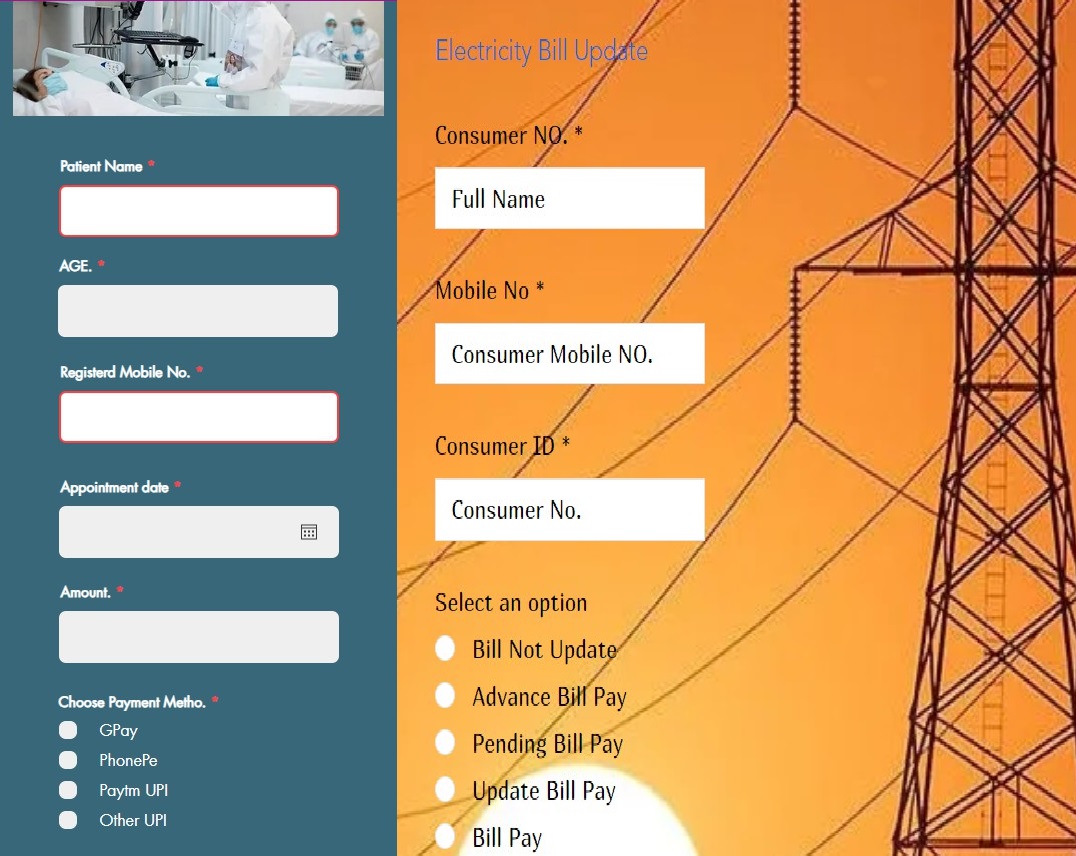
Figure 5. Hospital appointment and Electricity Bill Phishing Pages
2. Stealing One-Time Passwords via SMS message
As a core design of this malware, the application requests permissions to allow it to send and view SMS messages once it launches.
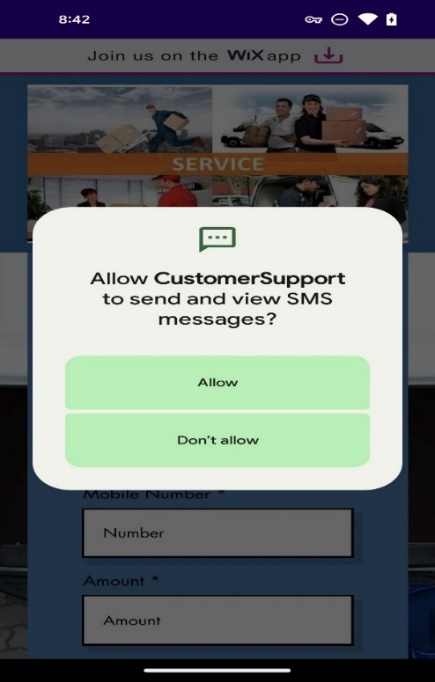
Figure 6. Request SMS permissions.
If victims click the “Allow” button, the malware starts a background service that secretly monitors users’ text messages and forwards them to a number which is from C2 server.
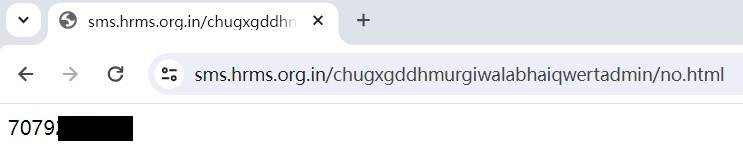
Figure 7. Forward phone number from C2 server
This step is crucial for the scam process, as many banks send a one-time password (OTP) to the customer’s phone for transaction verification. Using this method, the scammers can obtain these OTPs and successfully complete bank transactions.
Conclusion:
This malicious app and the developers behind it have emerged rapidly in India from last year to now, purposefully developing and maintaining malware, and focusing on deploying well-designed phishing websites through legitimate platforms. The group secretly promotes and sells its malware through social media platforms, making the spread of the malware more subtle and difficult to detect. This tactic resulted in an even more severe malware outbreak, posing an ongoing and serious threat to the financial security of Indian users.
Malware campaigns are very persistent and using multiple different applications on different websites can trick many victims into installing these applications and providing their private and personal information, which can then be used to commit fraud. In this environment, ordinary users in India face huge cybersecurity challenges. Therefore, users need to remain vigilant and cautious when dealing with any electronic communications or application download requests that appear legitimate but may contain malware. We strongly recommend users install security software on their devices and always keep it up to date. By using McAfee Mobile Security products, users can further protect their devices and reduce the risks associated with this type of malware, providing a more secure experience.
Indicators of Compromise (IOCs)
SHA256 hash List:
- 092efedd8e2e0c965290154b8a6e2bd5ec19206f43d50d339fa1485f8ff6ccba
- 7b1f692868df9ff463599a486658bcdb862c1cf42e99ec717e289ddb608c8350
- c59214828ed563ecc1fff04efdfd2bff0d15d411639873450d8a63754ce3464c
- b0df37a91b93609b7927edf4c24bfdb19eecae72362066d555278b148c59fe85
- 07ad0811a6dac7435f025e377b02b655c324b7725ab44e36a58bc68b27ce0758
- c8eb4008fa4e0c10397e0fb9debf44ca8cbadc05663f9effbeac2534d9289377
- 1df43794618ef8d8991386f66556292429926cd7f9cf9b1837a08835693feb40
- 5b3d8f85f5637b217e6c97e6b422e6b642ce24d50de4a6f3a6b08c671f1b8207
Phishing URLs:
- hxxps://bijlipayupdate[.]wixsite[.]com/my-site
- hxxps://appointmentservice0[.]wixsite[.]com/onlineappointment
- hxxps://couriers9343[.]wixsite[.]com/courier/
- hxxps://doctorappointment34[.]wixsite[.]com/appointmentbooking
- hxxps://hospitalservice402[.]wixsite[.]com/hospital-in
- hxxps://adn-reg[.]com/website
C2 Server URLs:
- hxxps://forexroyality[.]online/complainf13/My_File[.]txt
- hxxps://adn-reg[.]com/data[.]json
- hxxps://icustomrcore[.]com/chand3/data[.]json
- hxxps://sms[.]hrms[.]org[.]in/chugxgddhmurgiwalabhaiqwertadmin/no[.]html
- hxxps://krishna[.]salaar[.]co[.]in/admindata[.]txt
- hxxps://courier[.]elviainfotech[.]cloud/pages/phone[.]json

