- Finally, Bluetooth trackers for Android users that work better than AirTags (and are cheaper)
- Your Samsung Galaxy Watch is about to get a big upgrade for free - try 4 cool new features now
- Cisco Customer Achievement Award Winners Recognized at Cisco Live San Diego 2025
- Your TV's USB port is criminally underrated: 5 features you're not using enough
- T-Mobile will give you a Samsung Galaxy S25 Plus for free - how to qualify for the deal
DevSecOps Practices for a Secure Cloud
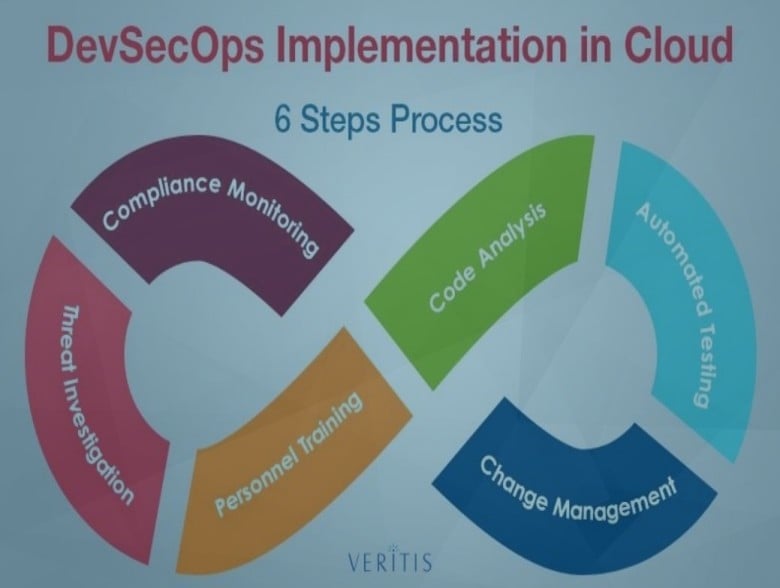
How to start ahead of the curve?
By Vishakha Sadhwani, Customer Engineer, Google Cloud
In today’s rapidly evolving technological landscape, a strong cultural practice like DevSecOps is essential. It empowers engineering teams to collaborate effectively, optimize workflows, ensure security and compliance, and confidently embrace AI innovation. But what exactly does this DevSecOps jargon mean?
TL;DR – DevSecOps is a set of practices and culture that standardizes and automates security processes and tools throughout software development and operations.
The impact of DevSecOps is significant. According to the State of Software Security Report (Cyentia Institute & Veracode) – Organizations with the most active DevSecOps programs fix vulnerabilities more than 11.5 times faster than average.
What role does it play?
With transformative technologies constantly emerging, software development trends can present complex challenges for businesses seeking to innovate quickly. Digital security, encompassing both applications and their underlying platforms, is a growing concern for organizations of all sizes; further requiring to navigate strict regulatory requirements for user data protection, compliance with data privacy standards, and safeguarding sensitive information. Balancing these security needs with the pressure to innovate rapidly can lead to friction.
Source: https://www.veritis.com/blog/devsecops-solution-to-cloud-security-challenge/
Cloud-native environments provide the flexibility essential for agile development and deployment, accelerating the development lifecycle. By integrating DevSecOps practices, organizations adopt a holistic life cycle approach where development, operations, security, and business stakeholders collaborate from the outset. This means embedding security into every stage of the software development lifecycle (SDLC), ensuring a secure and efficient development process.
Goals of DevSecOps
Enhanced Collaboration
DevSecOps aims to break down organizational silos, fostering cooperation between development, operations, and security teams. This involves shared tools, processes, and a culture of shared responsibility. By working together, teams across specializations can proactively identify risks and address them swiftly.
How does it improve Security and Agility?
Developers can detect vulnerabilities and security issues early in the development process, enabling them to ship code quickly without sacrificing security. DevOps professionals manage policies seamlessly and integrate multiple tools, reducing duplicate efforts and ensuring consistency. Security teams focus on automating workflows to detect and prevent risks proactively
Shift Security to the left
The concept of “shift-left” security involves prioritizing security as early as possible within the development lifecycle. Treat security with the same importance as quality and business requirements throughout the CI/CD DevOps process.
Given the significant shortage of security professionals – GitHub estimates developers outnumber them 500 to 1, organizations must embrace ‘shift-left’ security strategies to remain competitive.
This approach avoids the bottlenecks and potential delays caused by traditional SDLC processes where security testing often occurred right before a product’s release.
The cloud has significantly enabled “shift-left” security, offering tooling and automation for the following:
- Artifact Scanning: Integrate scanning of container images, IaC templates, and other artifacts directly into CI/CD workflows.
- Continuous Security Testing: Ensure artifact security during build and deployment phases with tools like:
- SAST (Static Application Security Testing): Analyzes source code for vulnerabilities.
- DAST (Dynamic Application Security Testing): Simulates attacks against running applications.
- SCA (Software Composition Analysis): Checks for vulnerable dependencies.
- Secure Supply Chain: Protect the supply chain through vulnerability scanning and dependency checks.
- Production Monitoring: Continuously monitor production environments for risks, enabling rapid remediation through collaboration between security, development, and DevOps teams.
Foster Operational Efficiency
DevSecOps aims to streamline operations for high-quality code deployment, leading to cost savings and reduced defects. Cloud automation enables scalable, rapid resource provisioning while minimizing the potential for human error, ensuring consistent and predictable infrastructure deployment.
While automated tools effectively identify security issues and best-practice violations, they are most powerful when integrated into robust DevSecOps processes and workflows. This approach drives continuous operational efficiency, codifies institutional knowledge, fosters team collaboration, reduces future risks, and minimizes security alerts.
The key principle: Automate Everything. This includes:
- Infrastructure as Code (IaC): Automate infrastructure provisioning using core IaC tools like Terraform.
- Proactive Detection and Identification: Leverage automated cloud security tools for comprehensive detection and identification of potential risks.
- Automated Response: Integrate security tools to enable an automated, proactive response to security incidents
Continuous Improvement
DevSecOps extends security practices beyond deployment, emphasizing continuous monitoring of security posture and involving both development and operations teams in incident response. This approach creates a feedback loop, fostering a culture of continuous learning and optimization. Here’s how to implement it:
- Use findings to refine processes: Leverage insights from testing, monitoring, and security incidents to improve processes and reduce future risks.
- Define metrics: Track key security metrics to measure improvement over time, ensuring accountability and visibility into the success of DevSecOps initiatives.
- Proactive risk identification: Employ threat modeling techniques to proactively identify potential threats, allowing for mitigation strategies before vulnerabilities are exploited
Start your Journey Right Away with DevSecOps
The value and benefits of this practice will position your organization for immediate and future success on any cloud platform. You can immediately get started by:
- Bringing Security into your DevOps pipeline: Workshops for infrastructure and security engineers to develop, validate, and enforce security guardrails in shifting left
- Implement Infrastructure as Code: Training Security Engineering teams around the fundamentals and operational watchpoints of using IaC tooling to manage resources on cloud.
- Security Automation: Train Security Engineering in cloud automation to maintain security posture (through prevention, detection and remediation)
- Recommendations: Identify opportunities for enhancement, improve coordination amongst teams, the implementation of deeper security controls and alerts and more.
Please note the opinions stated here are my own, not those of my company.
About the Author
 Vishakha is a Customer Engineer at Google Cloud, helping businesses across industries – including finance, AI/ML startups, retail, and cybersecurity – achieve transformative results through cloud automation and secure deployments. With a focus on designing and building large-scale cloud solutions for digital-native customers, she leverages her 7+ years of experience with various cloud providers and open-source tools. Committed to knowledge sharing, Vishakha actively mentors newcomers in cloud technology. Connect with her on LinkedIn (https://www.linkedin.com/in/vsadhwani/) to know more!
Vishakha is a Customer Engineer at Google Cloud, helping businesses across industries – including finance, AI/ML startups, retail, and cybersecurity – achieve transformative results through cloud automation and secure deployments. With a focus on designing and building large-scale cloud solutions for digital-native customers, she leverages her 7+ years of experience with various cloud providers and open-source tools. Committed to knowledge sharing, Vishakha actively mentors newcomers in cloud technology. Connect with her on LinkedIn (https://www.linkedin.com/in/vsadhwani/) to know more!
Disclaimer : The views expressed in this article are solely the author’s and do not represent those of their employer.

