- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
New VPN risk report finds nearly half of enterprises attacked via VPN vulnerabilities

Virtual private networks (VPNs) have long provided remote access for enterprises. However, after a year full of high-profile exploits of severe and zero-day VPN vulnerabilities, including ones requiring emergency CISA directives to disconnect VPN services, enterprises are reconsidering. Many are rethinking workforce connectivity strategies and moving to zero trust architecture as a secure VPN alternative.
In fact, 91% of enterprises are concerned that VPNs will compromise their security.
Released today, the Zscaler ThreatLabz 2024 VPN Risk Report sheds light on critical VPN trends and explores solutions to secure remote users. Cybersecurity Insiders and Zscaler surveyed 647 IT professionals and cybersecurity experts on the shifting security, management, and user experience challenges of VPN technologies. These include the risks VPNs may present to an organization’s security posture around lateral movement, third-party access, and vulnerability to attacks like ransomware.
Overall, the findings paint a clear picture. Enterprises show stark concerns around the security risks of VPN solutions, even as they reach a strong consensus around zero trust strategies and make concrete plans to adopt zero trust network access (ZTNA). Organizations also agree hosting VPN infrastructure in the cloud is against the principles of zero trust and does not provide the same level of security or user experience as ZTNA.
Download the Zscaler ThreatLabz 2024 VPN Risk Report to uncover enterprise perspectives and expert guidance around the risks of VPN.
Key findings
- VPN attacks are on the rise. 56% of organizations experienced one or more VPN-related cyberattacks in the last year—up from 45% the year before. This highlights the growing frequency and sophistication of attacks targeting VPNs.
- The vast majority are shifting to zero trust. 78% of organizations plan to implement zero trust strategies in the next 12 months. Meanwhile, 62% of enterprises agree that VPNs are anti-zero trust.
- Most have doubts about VPN security. 91% of respondents expressed concerns about VPNs compromising their IT security environment. Recent breaches illustrate the risks of maintaining outdated or unpatched VPN infrastructures.
- VPNs are no match for ransomware, malware, and DDoS. Respondents identified ransomware (42%), malware (35%), and DDoS attacks (30%) as the top threats exploiting VPN vulnerabilities, underscoring the breadth of risks organizations face due to inherent weaknesses in traditional VPN architectures.
- The risk of lateral movement can’t be ignored. 53% of enterprises breached via VPN vulnerabilities say threat actors moved laterally, demonstrating containment failures at the initial point of compromise that underscores the risks of traditional, flat networks.
- Almost everyone has concerns about third-party risk. Since VPNs provide full network access, 92% of respondents are concerned about third parties with VPN access serving as potential backdoors into their networks.
Rising VPN attacks, CVEs, and enterprise concerns
Overall, a staggering 56% of organizations reported cyberattacks that exploited VPN vulnerabilities within the past year, marking a significant increase from the previous year (45%). Even more concerning, 41% of organizations reported experiencing two or more VPN-related attacks, highlighting the existence of severe security gaps that need immediate attention.
Zscaler
Figure 1: Enterprises that have experienced an attack that targeted VPN vulnerabilities in the past year.
This rise in VPN-related attacks is not without context. In the past year, we’ve seen a string of zero-day and high-severity VPN vulnerabilities come to light. This trend has revealed that, from an architectural point of view, VPN-based networks are vulnerable to a single point of failure that allows threat actors to move laterally on the network, discover crown jewel applications, and steal sensitive data.
Indeed, most survey respondents who experienced VPN-related breaches reported that attackers moved laterally on their networks.
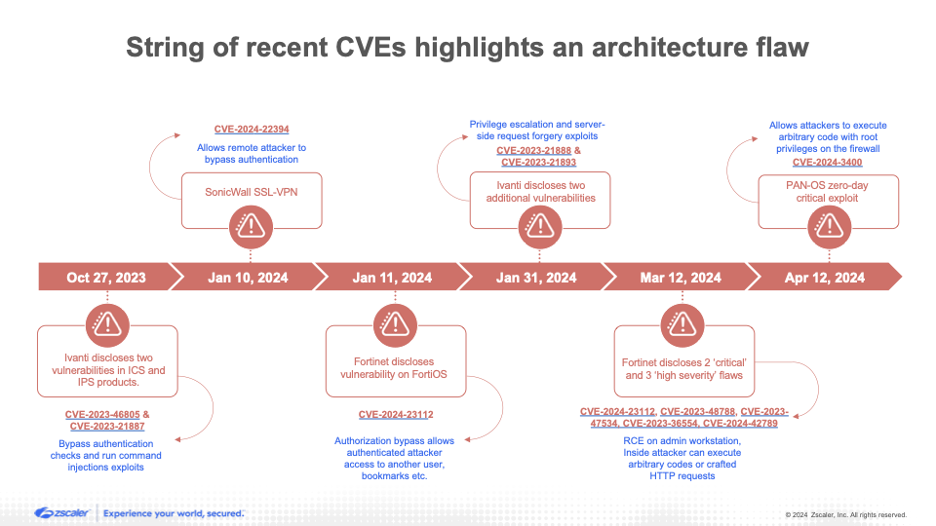
Zscaler
Figure 2: A string of high-profile CVEs impacting VPN in the last year.
Enterprise trust in the security of VPNs is low. Overall, 91% of companies have concerns that VPNs may jeopardize the security of their environments.
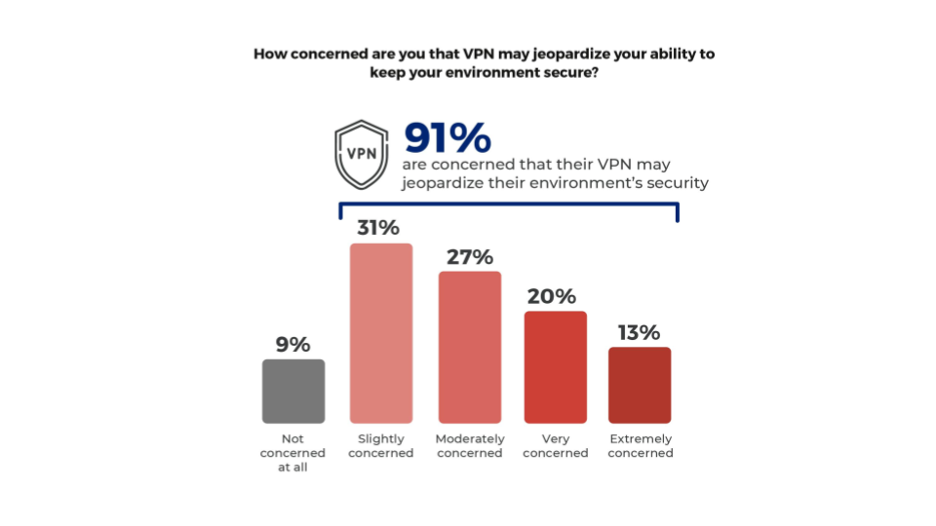
Zscaler
Figure 3: Enterprise concerns that VPN may jeopardize the security of their environment.
Growth in Zero Trust adoption
In parallel with, or because of, the security concerns of VPN, enterprises show a strong consensus around the adoption of zero trust strategies for secure connectivity. In fact, 62% of enterprises see VPN technology as incompatible with zero trust strategies.

Zscaler
Figure 4: Enterprise views on VPN as compatible with zero trust strategies.
Meanwhile, enterprises are actively adopting zero trust strategies as enthusiasm for VPN wanes. On the whole, 78% of enterprises plan to implement zero trust strategies within the next 12 months, while 31% are actively implementing zero trust strategies today.
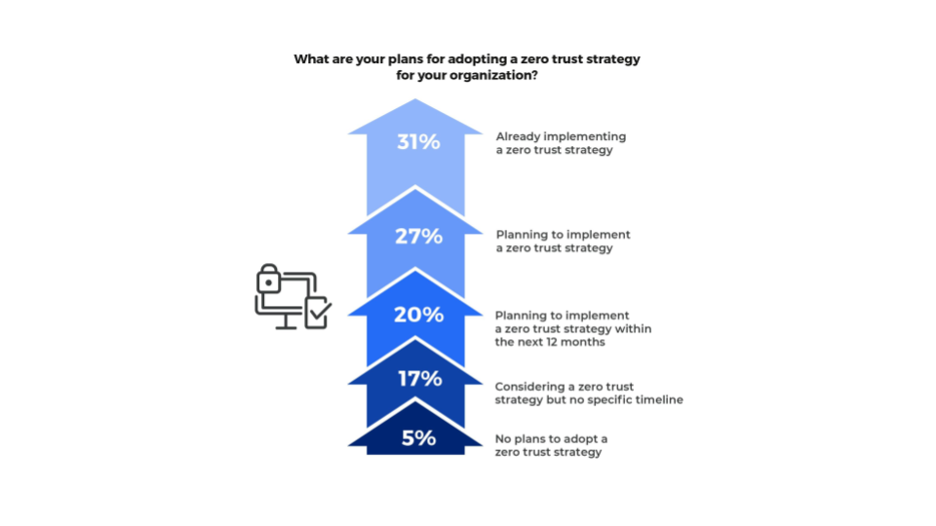
Zscaler
Figure 5: Enterprise adoption of zero trust strategies.
As the number of high-profile security vulnerabilities associated with VPNs continues to rise, businesses should anticipate a corresponding rise in security incidents related to VPNs. As a result, enterprises will increasingly look to ZTNA as a replacement for VPN and a way to fundamentally improve their security posture.
Our ZTNA solution, Zscaler Private Access (ZPA) provides comprehensive security for users connecting to private applications regardless of their location, from any device. With ZPA, applications are hidden from internet exposure, making it difficult for attackers to find and target them. Our inline traffic inspection detects malicious activities to prevent compromise and data exfiltration. ZPA is able to limit the blast radius with AI-powered user-to-app segmentation and integrated deception.
For the full report insights, including best-practice guidance on mitigating VPN risks and predictions for 2024 and beyond, download your copy of the Zscaler ThreatLabz 2024 VPN Risk Report with Cybersecurity Insiders today.

