- This Lenovo ThinkPad is my top pick for remote work - and it's nearly 50% off now
- I invested in this 3-in-1 robot vacuum, and it's paying off for my home
- I've tested the Meta Ray-Bans for months, and these 5 features still amaze me
- My new favorite iPhone portable charger has a magnetic superpower - and it's cheap
- This is the best space-saving smart heater I've ever used - and now it's on sale
Chinese Attack Tool Gains Gmail Access
Cybercrime
,
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
Campaign Targets Tibetan Organizations
Proofpoint reports that Chinese state-sponsored hackers are using a new customized malicious Mozilla Firefox browser extension that facilitates access and control of victims’ Gmail accounts. So far, the hackers are targeting Tibetan organizations.
See Also: Top 50 Security Threats
The FriarFox extension apparently is linked to the advanced persistent threat group TA413, Proofpoint says. Earlier this year, the group was observed delivering Scanbox and Sepulcher malware to Tibetan organizations, the security firm says.
The extension, which gives hackers access to a user’s Gmail account and FireFox browser data, could be deployed by others, the Proofpoint researchers say.
“The APT group is aligned with the Chinese state with strategic objectives associated with espionage and civil dissident surveillance that includes the Tibetan Diaspora,” Proofpoint reports.
Phishing Campaign
Researchers detected a phishing email in late January targeting several Tibetan organizations. The email impersonated the “Tibetan Women’s Association” in the “from” field, and the email subject was “Inside Tibet and from the Tibetan exile community,” according to Proofpoint.
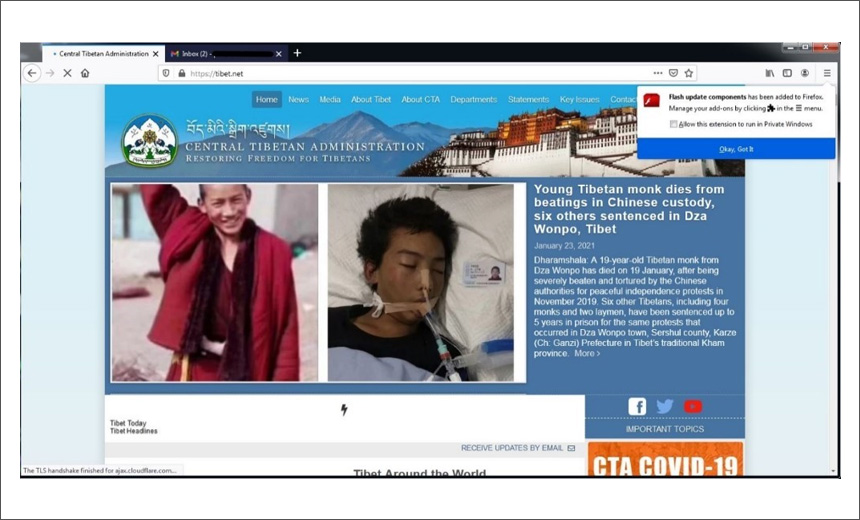
The phishing email was delivered from a known TA413 Gmail account that impersonates the Bureau of His Holiness the Dalai Lama in India. The email contained a malicious URL that impersonated YouTube: hxxps://you-tube[.]tv/.
If the recipient clicks on the malicious link, it directs them to a fake “Adobe Flash Player Update” landing page that executes several JavaScript files, which profile the victim’s system and determines where to deliver the malicious FireFox Browser extension.
The installation and delivery of the FriarFox browser extension depends on the victim’s browsing state. “Threat actors appear to be targeting users that are utilizing a Firefox Browser and are utilizing Gmail in that browser. The user must access the URL from a FireFox browser to receive the browser extension,” the Proofpoint report notes.
Researchers say that to download the malicious file, a victim must be logged in to a Gmail account. When the victim accesses the you-tube[.]tv URL with a non-FireFox browser and no Gmail session, the Adobe Flash Player landing page is temporarily displayed at you-tube[.]tv before redirecting to a legitimate youtube[.]com login page that attempts to access an active domain cookie in use on the site.
“Actors may be attempting to leverage this domain cookie to access the user’s Gmail account in the instance that a GSuite federated login session is used to log in to the user’s YouTube account. This user is not served the FriarFox browser extension,” the researchers note.
If the victim accesses the you-tube[.]tv URL with a FireFox browser and is logged in to Gmail, they are served the FriarFox extension from hxxps://you-tube[.]tv/download.php and then are prompted to allow the download of software from the site. They are also required to add the browser extension named “Flash update components” by approving the extension’s permissions.
“If the user clicks ‘add’ the browser redirects to the benign webpage hxxps://Tibet[.]net and the message ‘Flash update components has been added to Firefox’ will appear in the upper right corner of the browser,” Proofpoint states.
Scanbox Malware
After the successful installation of the FriarFox browser extension, hackers gain access to the victim’s Gmail account and FireFox browser data. FriarFox also contacts the hackers’ command-and-control server to retrieve the PHP and JS-based payload Scanbox, which helps them to access Gmail.
Scanbox is a PHP and JavaScript-based reconnaissance framework that dates to 2014. Its use of PHP and JS enables a file-less malware approach when targeting victims’ hosts.
While APT TA413 is using the malicious extension to access Gmail accounts and spy on vulnerable Tibetan dissident populations, Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, says that other hackers could use this technique to target organizations.
”The complex delivery method of the FriarFox browser extension grants this APT actor near total access to the Gmail accounts of their victims, which is especially troubling as email accounts really are among the highest value assets when it comes to human intelligence,” DeGrippo notes.
The malware enables hackers to search, archive and read emails; receive Gmail notifications; alter FireFox browser audio and visual alert features for the FriarFox extension, label emails, marks emails as spam, delete messages, refresh inboxes, forward emails, perform function searches, delete messages from Gmail trash and send email from compromised accounts.
By obtaining FireFox browser access, based on granted browser permissions, hackers can access user data, display notifications, read and modify privacy settings and access browser tabs.
Cloud-Based Email a Favorite Target
Proofpoint previously reported on Sepulcher malware and its links to the Lucky Cat and Exile Rat malware campaigns that targeted Tibetan organizations (see: Chinese Hackers Use Fresh Trojan for Espionage).
APT groups have an insatiable hunger for access to cloud-based email accounts, DeGrippo says.
“We’ve observed access technique diversification on the high end with the SolarWinds supply chain attack and on the low end with this new FriarFox browser plugin,” she says. “Malicious browser plugins aren’t new, but they are an often-forgotten attack surface in many enterprises, and it was surprising to see an APT actor aligned with the Chinese state use this method.”

