99.2% of US government Android users are running outdated OS versions

Some versions of Android in use by government employees go all the way back to 2017’s Android 8, and that’s a huge cybersecurity problem.
Tero Vesalainen, Getty Images/iStockphoto
Android, the most popular mobile operating system in the world, runs on plenty of devices used by U.S. government workers, but only 0.08% of those devices are running the latest version of Android, a report finds.
Mobile security firm Lookout is behind the report, which looked at over 200 million mobile devices being used by U.S. federal and state government workers between January 2019 and December 2020. It found that the COVID-19 pandemic triggered a massive shift to mobile device use for government employees, which makes the security statistics it uncovered even more concerning.
SEE: Identity theft protection policy (TechRepublic Premium)
“The rate at which [government employee] devices are exposed to mobile phishing, app threats, device and network threats is increasing,” Lookout said. Phishing attacks may be a matter of training users to avoid falling for tricks, but other attacks against government devices attempting to leverage known vulnerabilities, and older versions of Android are rife with them.
The breakdown in Android versions among government devices is alarming, as is the number of CVE vulnerabilities they contain (Figure A).
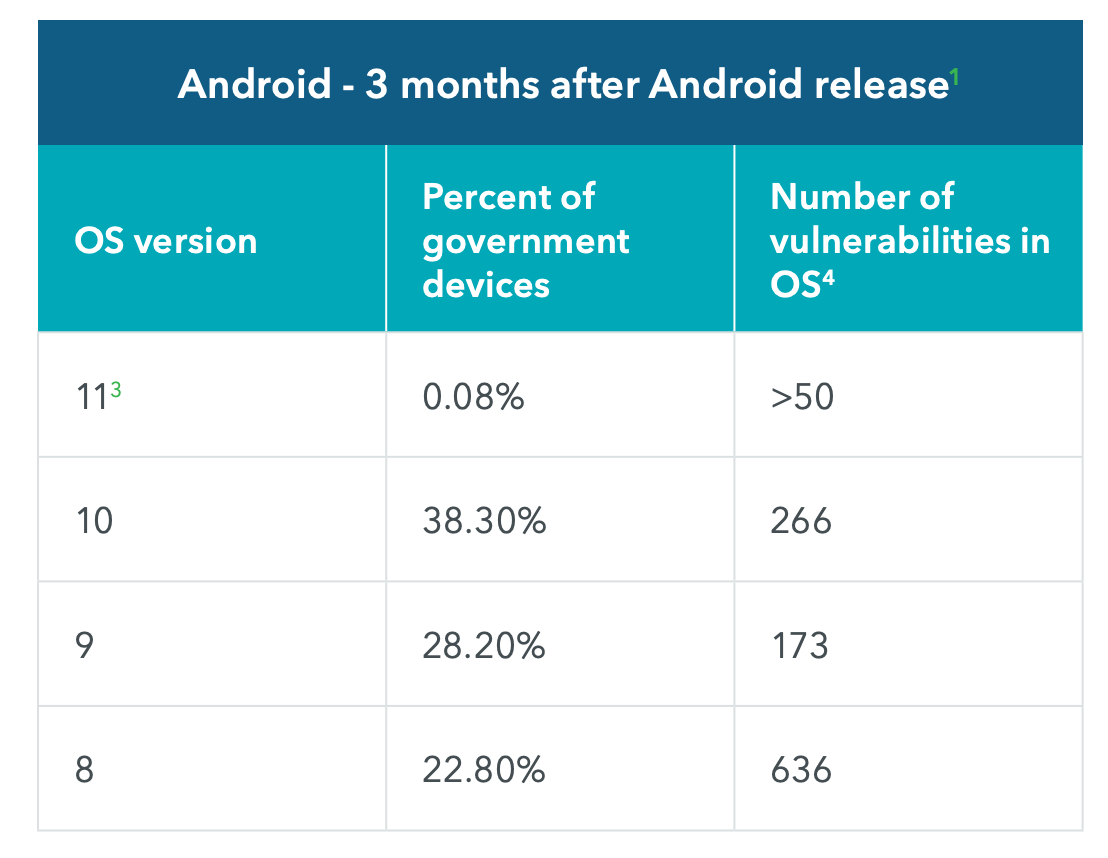
Figure A: The breakdown of Android OS versions being used by U.S. government employees.
Image: Lookout
The fact that nearly a quarter of government employees are running Android 8, which has over 636 known vulnerabilities, makes it a serious security risk. The report notes that the second half of 2020 saw a huge spike in malicious app activity: In the fourth quarter alone there was a 20-times increase in year-over-year malicious app encounters on government devices. Vulnerabilities found on government devices included:
- Connections to servers in foreign countries,
- Access to device file systems,
- Camera/microphone access,
- Excessive permissions that allow apps to see data from other apps on a device.
In contrast to Android devices, iOS users in the government sector show a high rate of adoption of the latest iOS version, with 67.8% on iOS 14. “Government agencies or departments may choose to delay updates until their proprietary apps have been tested. This delay creates a vulnerability window during which a threat actor could use a mobile device to gain access to the
organization’s infrastructure and steal data,” the report notes.
A second bright spot in the report is the contrast between managed and BYOD devices used by government employees: On the federal side, 91.34% of mobile devices are government- managed, and at the state and local level 75.69% are managed.
Unmanaged personal devices are more convenient for employees, but the report points out that the tradeoff is additional exposure to phishing attacks. Only 2.66% of federally-managed mobile devices are exposed to phishing attacks, versus 16.62% of federally-used unmanaged devices. At the state and local level those numbers are 6.18% for managed and 11.02% for unmanaged.
Counterintuitively, state and local employees are exposed to phishing attacks more often, despite the numbers for unmanaged devices being lower. “This is because these departments have a higher proportion of BYOD employees who have unrestricted use of their devices. As a result, these employees are exposed to phishing sites at a higher rate,” the report said.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
To maximize mobile device security, Lookout makes the following recommendations:
- Keep mobile systems up-to-date. This may mean accelerating the testing of proprietary apps, but it’s a necessary change of priority.
- Make sure mobile vulnerability and patch management capabilities are part of your operation.
- Require users to install updates on mobile devices whenever they’re available.
- Implement an approved device list for BYOD devices.
- Train employees to recognize phishing attacks, but don’t stop at desktop attacks: Be sure to include recognizing phishing on mobile devices as well.


