- I tested a Pixel Tablet without any Google apps, and it's more private than even my iPad
- My search for the best MacBook docking station is over. This one can power it all
- This $500 Motorola proves you don't need to spend more on flagship phones
- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
- I replaced my Linux system with this $200 Windows mini PC - and it left me impressed
All-New Ransomware Coverage Opens Up the Path to Recovery

Our all-new ransomware coverage is now available, ready to help just in case—all backed by expert advice to help you find the quickest and best possible path to recovery.
Ransomware coverage from McAfee can reimburse you up to $25,0000 for losses resulting from a ransomware threat, including financial losses and ransom fees. You’ll find this ransomware coverage included with our McAfee+ Ultimate plan.
As well as eligibility for ransomware reimbursement, our team of experts can help you:
- Determine the severity of a ransomware attack.
- Learn what immediate action steps you can take.
- Determine if a ransom should be paid or if alternative options exist.
- Facilitate the ransom payment when, and if, necessary.
However, it’s important to realize that ransomware is unlike any other attack. When ransomware locks someone out of their device or encrypts their data and files so they can’t use them, a demand is usually made for money. Sometimes, paying the ransom results in the device being made accessible again or the files being decrypted. Yet like any ransom case, this result is not always guaranteed. There are plenty of cases where people pay the ransom but never get their data or access to their devices back.
Again, our coverage includes guidance from our expert advisers to help walk you through your options should the worst happen to you. You won’t be in it alone—particularly as you look to recover from what can be a complicated attack.
What is ransomware?
As the name implies, ransomware is a type of malware that holds your device or information for ransom. It may lock your computer or smartphone entirely or it may you out of your files by encrypting them so that you can’t access them. Whether it’s a hacker or a cybercrime organization behind the attack, the bad actor involved holds the key to unlock those files—and promises to do so. For a price. And as mentioned above, sometimes that doesn’t happen, even if you pay.
Ransomware can infect your devices several different ways:
- Malware sites, where bad actors direct you to the site with the aim of having you download the malware package or by uploading it to you through your browser without your knowledge.
- Phishing attacks, whether via an email, direct message, text, or any other form of electronic message, bad actors will embed either links or attachments that can lead to ransomware ending up on your device.
- Network or device compromise, which may include a bad actor taking advantage of a security loophole or simply accessing the network or device with a stolen or hacked password.
A brief history of ransomware
Ransomware has seen quite the evolution over the years. Its origins date back to the late 1980s, where malware-loaded floppy disks were sent to users who installed them under false pretenses. There the malware would lie in wait until the user rebooted their computer for the 90th time and presented with a digital ransom note.
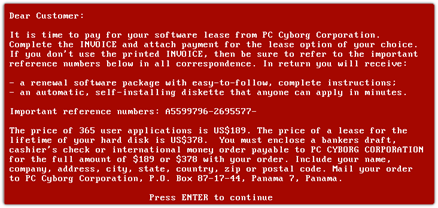
From there, ransomware attacks on individuals became more sophisticated, and more lucrative, with the advent of the internet and the millions of everyday users who flocked to it. Using phishing emails, malware downloads from phony sites, and compromised software and networks, hackers rapidly expanded their ransomware reach.
However, yet more lucrative for hackers and organized cybercriminals were public and private organizations. Shifting their attacks to so-called “big game” targets, hackers and organized cybercriminals have used ransomware to extort money from hospitals, city governments, financial institutions, and key energy infrastructure companies, to name just a few. Seeing further opportunity, ransomware attackers then began targeting smaller and mid-sized businesses as well. While the ransom demands account for lower amounts, these organizations often lack dedicated cybersecurity teams and the protections that come along with them, making these organizations easier to victimize.
Meanwhile, the body of malicious code and attack packages used to launch ransomware attacks has only grown. As a result, small-time hackers and hacking groups can find the tools they need to conduct an attack for sale or for lease as a service (Ransomware as a Service, or RaaS). In effect, these bad actors can simply access a dark web marketplace and figuratively pull a ready-to-deploy attack off the shelf.
As a result, ransomware remains a concern for individuals, even as businesses and governmental bodies of all sizes deal with its threat.
Protecting yourself from ransomware attacks
What makes ransomware so damaging is just how much effort it can take to undo. Setting aside the sophisticated attacks on businesses and governments for a moment, even those “off-the-shelf” attacks that some hackers will launch against individuals go beyond the average user’s ability to undo. For example, there are some known attacks with known methods of decrypting the data, however, that requires knowing specifically which attack was used. Attempting to undo the encryption with the wrong solution can potentially encrypt that data even more.
So without question, the best defense against ransomware is prevention. Comprehensive online protection software gives you the tools you need to help avoid becoming a ransomware victim. A few include:
- Safe surfing features that steer you clear of malicious downloads, attachments, and websites.
- Strong antivirus that detects and neutralizes the latest malware threats with the latest virus definitions.
- Vulnerability scanners that help keep your device and its apps up to date with the latest security measures.
- A firewall that helps prevent intruders from accessing the devices on your home network—and the files on them.
Moreover, you can protect yourself further by backing up your files and data. A cloud storage solution,121cwdv 1765ujb n4yh that’s secured with a strong and unique password, offers one path. Likewise, you can back up your files on an external disk or drive, making sure to keep it disconnected from your network and stored in a safe place.
Also as mentioned in the bullets above, keep your operating system and apps current with the latest updates. Beyond making improvements in your operating system and apps, updates often also address security issues that hackers often use to compromise devices and apps.
Lastly, stay alert. Keep an eye out for sketchy links, attachments, websites, and messages. Bad actors will pull all kinds of phishing tricks to lure you their way, places where they try to compromise you, your devices, and data.
Taken together, the combination of online protection software and a few preventative steps can greatly reduce the chance that you’ll fall victim to ransomware. From there, you also have the assurance of our ransomware coverage, ready to get on the path to recovery, just in case.
The post All-New Ransomware Coverage Opens Up the Path to Recovery appeared first on McAfee Blog.

