- These are my top 15 favorite Memorial Day lawn and outdoor deals right now
- My favorite Memorial Day TV deals 2025: Save up to $5,000 on big-screen TVs
- I'm a laptop expert, and these are the Memorial Day laptop deals I'd grab this weekend
- I'm an audio expert and these are the Memorial Day headphone deals I'd recommend to my friends and family
- I'm a health tech expert and these are the Memorial Day sales fitness enthusiasts should pick up
Attackers Use Fake CAPTCHAs to Deploy Lumma Stealer RAT
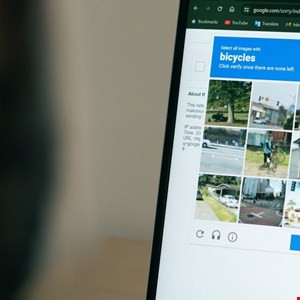
HP’s latest Threat Insights Report has revealed a surge in malicious CAPTCHA campaigns, where users are tricked into running PowerShell commands that install the Lumma Stealer remote access trojan (RAT).
The campaigns show that attackers are capitalizing on growing click tolerance, whereby users are now accustomed to jumping through hoops to authenticate themselves online, according to HP.
Users were directed to attacker-controlled sites and prompted to complete a range of fake authentication challenges. This resulted in them running a malicious PowerShell command on their PC that ultimately installed the Lumma Stealer RAT.
Dr Ian Pratt, Global Head of Security for Personal Systems at HP, said, “Multi-step authentication is now the norm, which is increasing our ‘click tolerance.’ The research shows users will take multiple steps along an infection chain, really underscoring the shortcomings of cyber awareness training.”
“Organizations are in an arms race with attackers – one that AI will only accelerate. To combat increasingly unpredictable threats, organizations should focus on shrinking their attack surface by isolating risky actions – such as clicking on things that could harm them. That way, they don’t need to predict the next attack; they’re already protected,” Pratt added.
The firm’s report found that at least 11% of email threats identified by HP Sure Click bypassed one or more email gateway scanners.
It also noted that executables were the most popular malware delivery type (43%), followed by archive files (32%).
RATs Distributed in Multiple Campaigns
A second campaign identified by HP saw attackers spreading an open source RAT, XenoRAT, with advanced surveillance features such as microphone and webcam capture.
Using social engineering techniques to convince users to enable macros in Word and Excel documents, attackers could control devices, exfiltrate data and log keystrokes – showing that Word and Excel still present a risk for malware deployment.
HP also found threat actors leveraging Scalable Vector Graphics (SVG) images to deliver malicious JavaScript, bypassing traditional detection mechanisms.
By default, web browsers render these images, triggering the embedded code. This technique facilitates the deployment of seven payloads, including RATs and infostealers, offering attackers redundancy and diverse monetization avenues.
As part of the infection chain, the attackers also used obfuscated Python scripts to install the malware. Python’s popularity – which is being further boosted by rising interest in AI and data science – means it is an increasingly attractive language for attackers to write malware, as its interpreter is widely installed.
Data for the Threat Insights Report was gathered from consenting HP Wolf Security customers from October-December 2024.
Image credit: lilgrapher / Shutterstock.com

