- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Attacks Abound in Tricky Threat Terrain: 2021 Annual Cybersecurity Report

The digital transformations that had enabled many enterprises to stay afloat amid the Covid-19 health crisis also brought about major upheavals in cybersecurity, the impact of which was still widely felt in 2021. Trend Micro detected and blocked more than 94 billion threats over the course of last year, keeping pace with malicious actors who were intent on abusing any weak spots in the security postures of organizations around the world. In our annual cybersecurity report, “Navigating New Frontiers,” we look back at 2021 in terms of the most significant security issues and trends that shaped the year’s threat landscape.
Ransomware actors become more deliberate in targeting critical industries
From years of tracking ransomware activities, we have observed how ransomware operators have evolved from deploying quantity-based tactics to deliberately picking more profitable victims. Modern ransomware usually dedicates more time and effort to planning and reconnaissance, making for debilitating attacks that are tailored to the specific systems of targets.
Likely because of the important roles they had played amid the pandemic, organizations in the government, banking, and healthcare industries bore the brunt of ransomware attacks in 2021, although we observed a 21% year-on-year decrease in overall ransomware detections. But this decline does not necessarily mean that there were fewer ransomware attacks. Rather, it could be the result of our detection and blocking of more malware tools that were often used by ransomware actors, including the Cobalt Strike beacon CoBeacon, the trojan Trickbot, and the information stealer BazarLoader. That we blocked larger numbers of these affiliate tools, whose presence is an early indicator of infection, might have prevented ransomware actors from escalating their operations to full-scale attacks.
Figure 1. The top three industries in terms of ransomware file detections in 2020 and 2021
Source: Trend Micro™ Smart Protection Network™
Malicious actors zero in on misconfigurations in cloud environments
More companies turned to the cloud to continue and expand their businesses, but the inherent complexity of setting up cloud infrastructures drove malicious actors to move quickly and take advantage of misconfigurations in these environments. Notably, a role-based access control misconfiguration in Kubernetes enabled the threat actor group TeamTNT to compromise almost 50,000 IP addresses in the US and China as part of a large-scale credential theft campaign last year. Also in 2021, TeamTNT used misconfigured servers as an attack vector to pilfer metadata from cloud service providers.
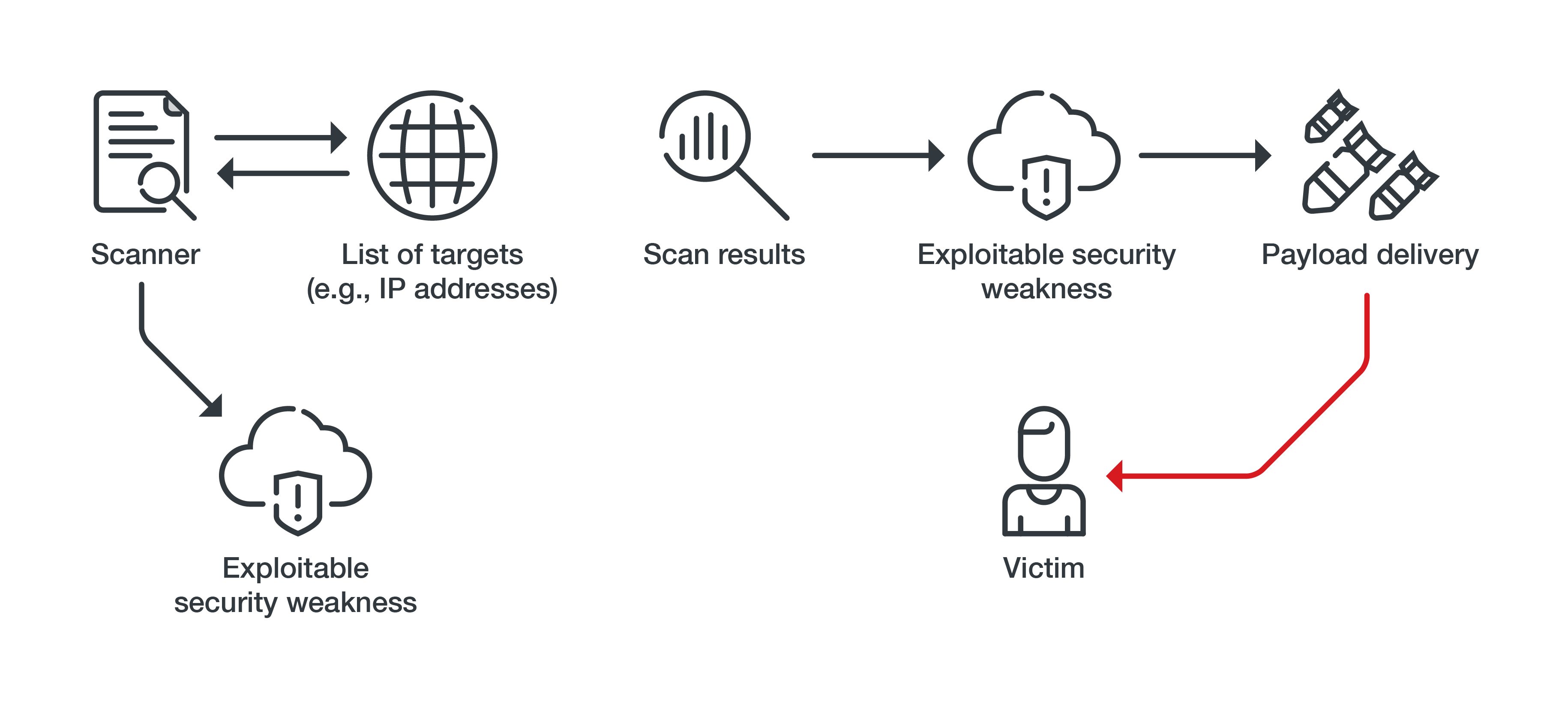
Figure 2. TeamTNT’s attack chain
Email-based attacks evolve into a more complex threat
In 2021, Trend Micro Cloud App Security found and blocked more than 25 million email threats. Phishing attempts, in particular, nearly doubled from 2020’s number. Of these, 62% were from spam emails while the rest consisted of credential-phishing attempts. Organizations in finance, healthcare, and education experienced the bulk of phishing attempts.
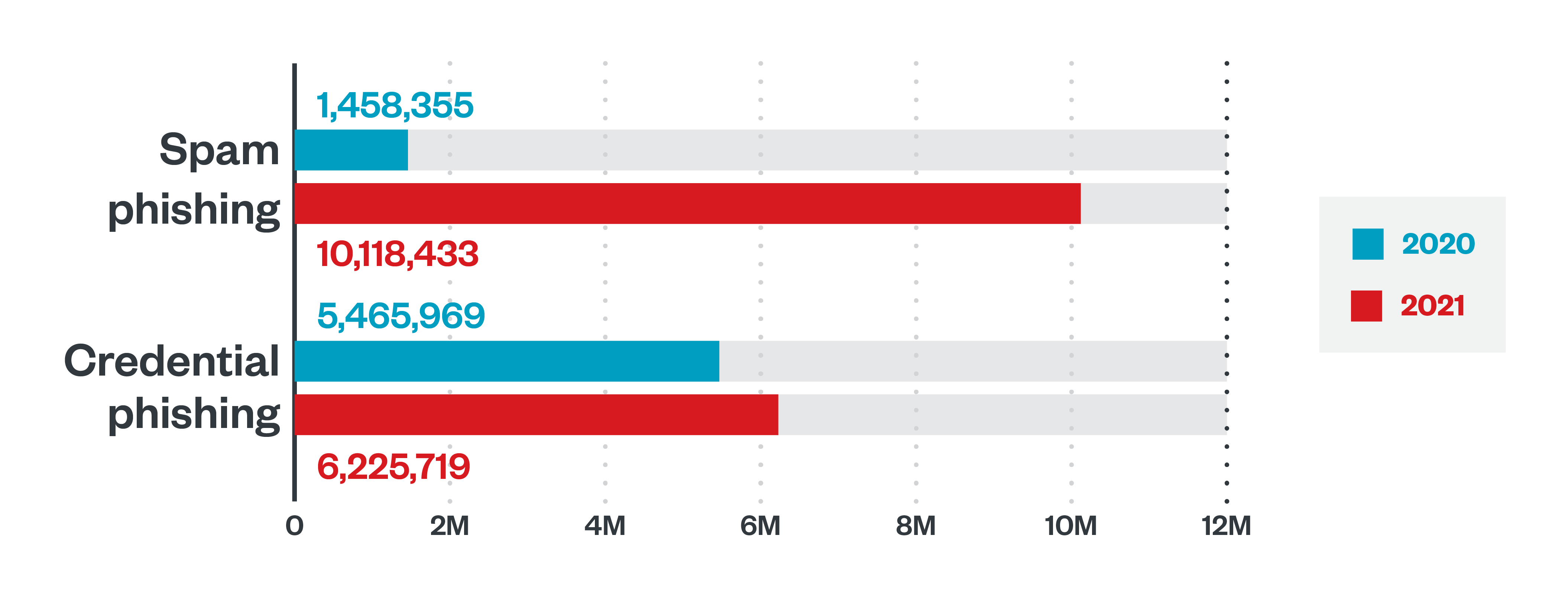
Figure 3. A comparison of the detections of spam phishing and credential-phishing attempts in 2020 and 2021
Source: Trend Micro Cloud App Security
We observed a dip in attempts at business email compromise (BEC) in 2021, but this could be because of an increase in more sophisticated BEC emails that were capable of avoiding antispam rules. We were able to stay on top of this development, however, as Trend Micro Cloud App Security used authorship analysis to detect and block a greater proportion as well as a greater number of these BEC attempts in 2021 than in 2020.
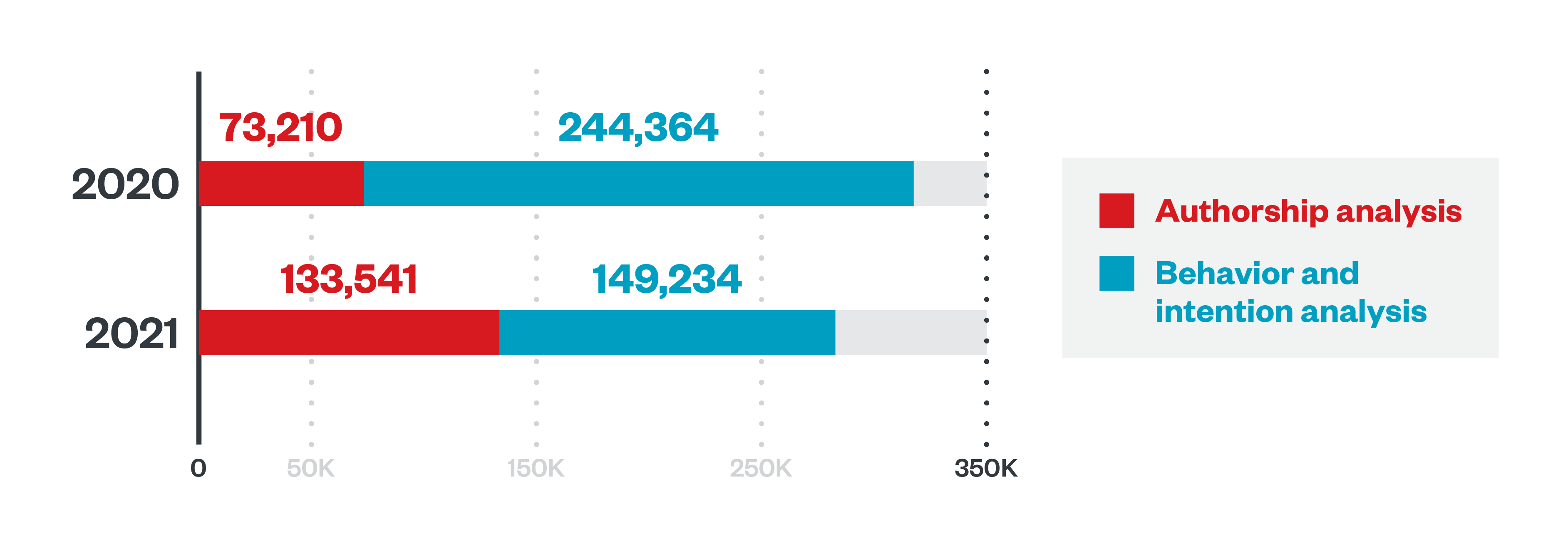
Figure 4. A comparison of the proportions of BEC attempts blocked based on authorship analysis and BEC attempts blocked based on behavior and intention analysis in 2020 and 2021
Source: Trend Micro Cloud App Security
Email was also the preferred entry point of opportunistic actors looking to exploit developments in the ongoing pandemic. We detected over 8 million Covid-19-related threats throughout 2021, mostly in the US and Germany. The majority of these threats were made up of emails, which is consistent with the upward trend of phishing attempts levied against the vaccine cold chain. The consistent news coverage surrounding the health crisis likely supplied malicious actors with new themes for their email lures.
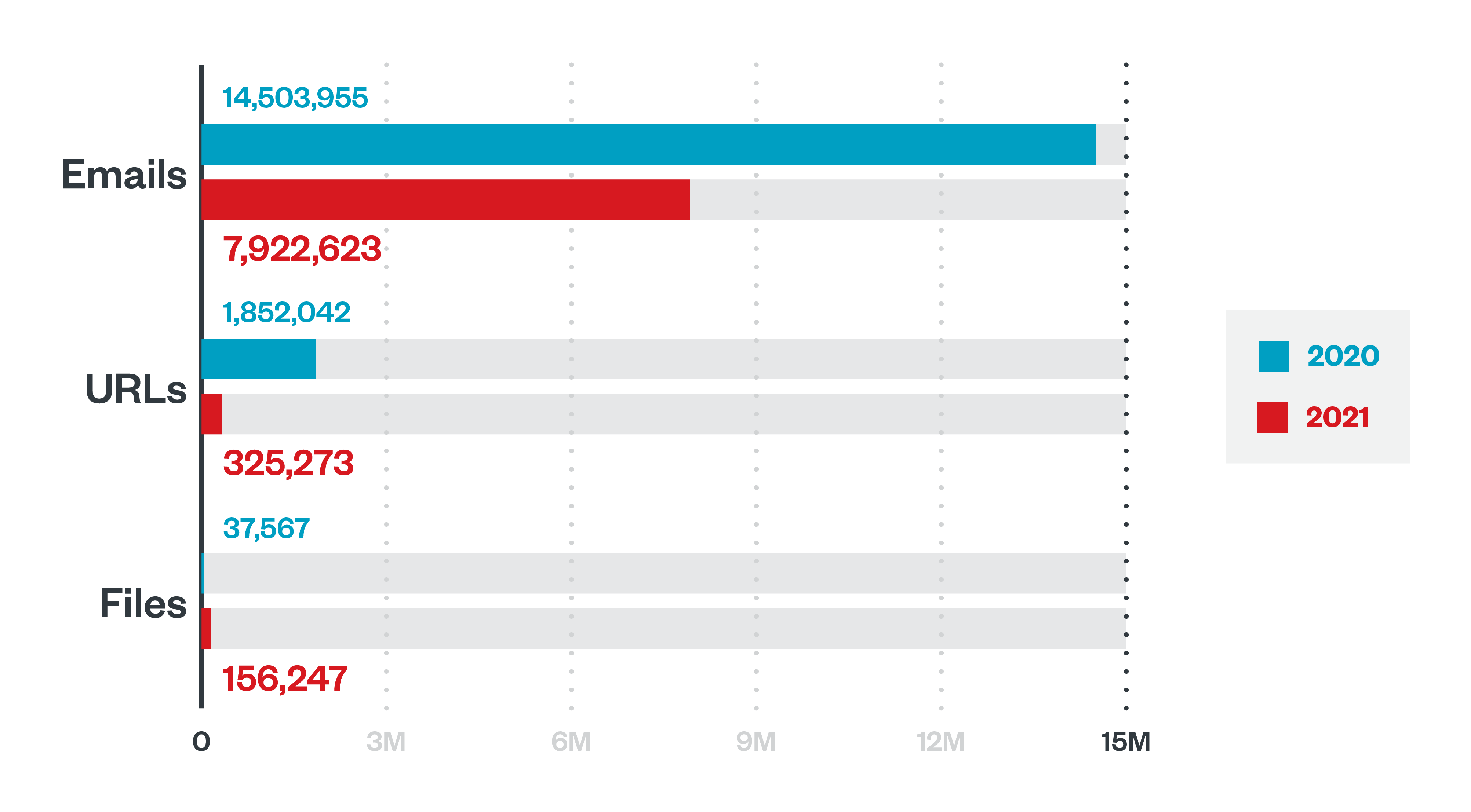
Figure 5. A comparison of the detections of Covid-19-related threats consisting of malicious emails, URLs, and files in 2020 and 2021
Source: Trend Micro Cloud App Security
Exploits of vulnerabilities both old and new run rampant
In 2021, Trend Micro™ Zero Day Initiative™ (ZDI) published advisories for 1,604 vulnerabilities, a 10% increase from the previous year. Alongside newly found ones, however, malicious actors continued to exploit previously disclosed flaws in their attacks. They carried on with abusing legacy vulnerabilities despite the availability of patches addressing these flaws, and a demand for these persisted in the cybercriminal underground, where almost 25% of vulnerabilities sold were at least three years old.
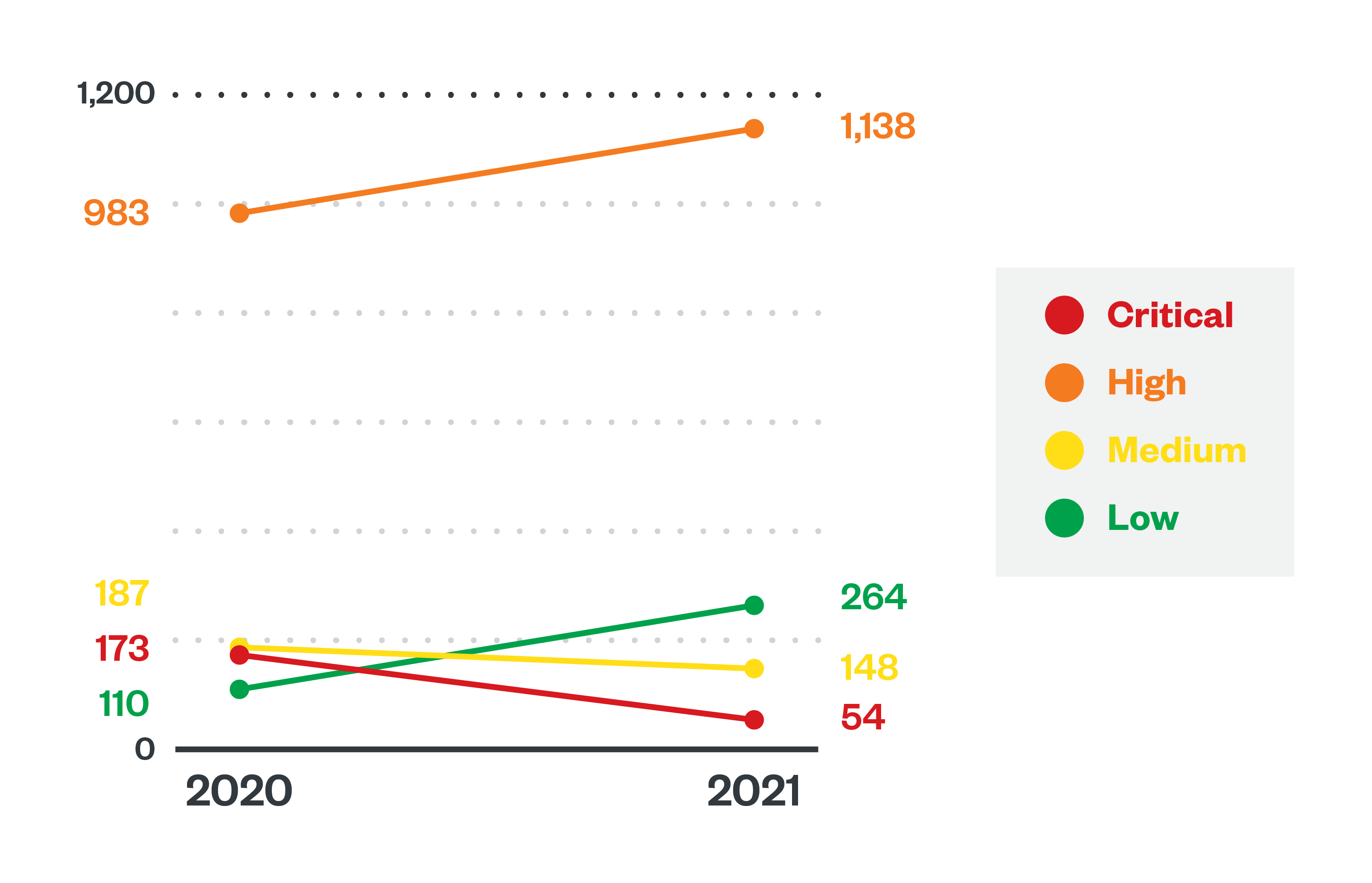
Figure 6. A comparison of the proportions of Common Vulnerability Scoring System (CVSS) ratings among vulnerabilities disclosed by Trend Micro’s ZDI program in 2020 and 2021
Source: Trend Micro™ Zero Day Initiative™
Unpatched systems remained a liability for organizations, as evidenced by Log4Shell (CVE-2021-44228), a high-severity vulnerability in Apache Log4j that was first reported privately to Apache in November 2021. A patch for it was made available a month later, but that did not stop malicious actors from exploiting it in various ransomware, data theft, and cryptocurrency-mining attacks.
Similarly, even though patches for them had been released, the Microsoft Exchange Server vulnerabilities ProxyLogon (CVE-2021-26855) and ProxyShell (CVE-2021-34473 and CVE-2021-34523) were still successfully exploited by malicious actors. The cybercriminals behind the Squirrelwaffle loader, for example, used ProxyLogon and ProxyShell in hijacking their victims’ email accounts.
Enterprises need multilayered defense to keep thorny threats at bay
As their attack surfaces expand or otherwise evolve, enterprises across the globe are compelled to explore unfamiliar security terrain, where they will need high-quality data from a unified view of their entire digital ecosystems to anticipate, assess, and mitigate risks. Read our annual cybersecurity report, “Navigating New Frontiers,” to learn more about the noteworthy security stories of 2021 and obtain valuable insights that can help enterprises fend off latent, emergent, and current threats.

